MITRE ATT&CK™
MITRE ATT&CK™
Learn how advanced persistent threat groups use defense evasion to remain undetected in this walkthrough with Keatron Evans.

February 20, 2023
Bianca Gonzalez
MITRE ATT&CK™
Learn how threat actors use MITRE ATT&CK® persistence techniques to maintain a foothold in an environment. Then try the techniques yourself.

February 13, 2023
Bianca Gonzalez
MITRE ATT&CK™
Learn the techniques the Sandworm APT hacking group used to compromise, pivot from and destroy a server. Then try to do it yourself.

December 6, 2022
Bianca Gonzalez
MITRE ATT&CK™
Learn how threat actors use MITRE ATT&CK® persistence techniques to maintain a foothold in an environment. Then try the techniques yourself.

November 29, 2022
Bianca Gonzalez
MITRE ATT&CK™
Learn how adversaries leverage hardware to pivot into a protected network. Then try it yourself in our cyber range.

November 22, 2022
Bianca Gonzalez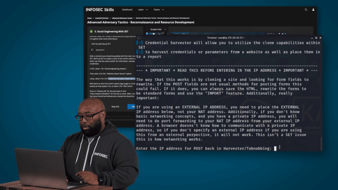
MITRE ATT&CK™
Learn the MITRE ATT&CK® techniques adversaries use for reconnaissance and resource development. Then try it yourself in our cyber range.

November 15, 2022
Bianca Gonzalez
MITRE ATT&CK™
Learn how to effectively use the MITRE ATT&CK matrix and develop your and your security team’s cybersecurity skills.

July 22, 2022
Louis Livingston-Garcia
MITRE ATT&CK™
Learn how to use the MITRE ATT&CK Navigator and showcase this data in formats that can be useful in multiple scenarios.

March 29, 2022
Kurt Ellzey
MITRE ATT&CK™
Introduction CISA has released a list of Risk and Vulnerability Assessments, or RVAs, to the MITRE ATT&CK Framework and have released their findings to

March 11, 2021
Greg Belding
MITRE ATT&CK™
The MITRE ATT&CK framework is a tool developed by the MITRE Corporation. It is designed to provide information about how a cyberattack works and the vari

February 9, 2021
Howard PostonIn this series
- Advanced adversary tactics and defense evasion: Lab and walkthrough
- Privilege escalation via cross-site scripting: Lab and walkthrough
- Executing the Sandworm APT: Lab and walkthrough
- Using persistence to maintain a foothold: Example and walkthrough
- Pivoting and proxychains with MITRE ATT&CK: Example and walkthrough
- Recon and resource development with MITRE ATT&CK: Example and walkthrough
- How to use the MITRE ATT&CK Matrix for Enterprise: Video walkthrough
- How to use MITRE ATT&CK Navigator: A step-by-step guide
- Most common MITRE ATT&CK tactics and techniques: CISA shares most common RVAs
- Using MITRE ATT&CK with cyber threat intelligence
- MITRE ATT&CK framework mitigations: An overview
- MITRE ATT&CK framework techniques, sub-techniques & procedures
- MITRE Shield: An active defense and adversary engagement knowledge base
- 7 Steps of the MITRE ATT&CK®-based Analytics Development Method
- How to Use MITRE ATT&CK® to Map Defenses and Understand Gaps
- Using MITRE ATT&CK®-based analytics for threat detection: 5 principles
- Use cases for implementing the MITRE ATT&CK® framework
- How to Use the MITRE ATT&CK® Framework and the Lockheed Martin Cyber Kill Chain Together
- How to use the MITRE ATT&CK® framework and diamond model of intrusion analysis together
- MITRE ATT&CK® Framework Tactics: An Overview
- MITRE ATT&CK® Framework Matrices: An Overview
- The Ultimate Guide to the MITRE ATT&CK® Framework
- MITRE ATT&CK spotlight: Process injection
- MITRE ATT&CK: System shutdown/reboot
- MITRE ATT&CK: Credential dumping
- MITRE ATT&CK: Endpoint denial of service
- MITRE ATT&CK: Disk content wipe
- MITRE ATT&CK: Disk structure wipe
- MITRE ATT&CK: Supply chain compromise
- MITRE ATT&CK: Shortcut modification
- MITRE ATT&CK: External remote service
- MITRE ATT&CK: Port knocking
- MITRE ATT&CK vulnerability spotlight: Forced authentication
- MITRE ATT&CK vulnerability spotlight: Exploitation for credential access
- MITRE ATT&CK: External remote services
- MITRE ATT&CK: Exploiting a public-facing application
- MITRE ATT&CK: Drive-by compromise
- MITRE ATT&CK vulnerability spotlight: Credentials in registry
- MITRE ATT&CK vulnerability spotlight: Credentials in files
- MITRE ATT&CK vulnerability spotlight: Brute force
- MITRE ATT&CK: Hardware Additions
- MITRE ATT&CK vulnerability spotlight: Bash history
- MITRE ATT&CK vulnerability spotlight: Account manipulation
- MITRE ATT&CK: Replication through removable media
- MITRE ATT&CK: Command-line interface
- MITRE ATT&CK: Network sniffing
- MITRE ATT&CK: Input capture
- MITRE ATT&CK: Audio Capture
- MITRE ATT&CK: Man-in-the-browser
- MITRE ATT&CK: Browser bookmark discovery