The Cyber Enemy within: Rise of Insider Threat
Around the world, many countries are spending millions of dollars to protect themselves from cyber crime/fraud. Unfortunately, attackers seem to be succeeding in stealing the information and causing harm to the companies. The insider threat is one of the core reasons for their success.
There are always some security flaws or backdoors that are used to breach and exploit the systems. In many cases, we have witnessed that there was no security management in companies to protect themselves.
In a global survey conducted by Mckinsey, 100 companies were surveyed for cyber risk management maturity across Africa, United States, Europe and the Middle East. According to the survey, a majority lie in 2 – 3 on the scale of 1 – 4.
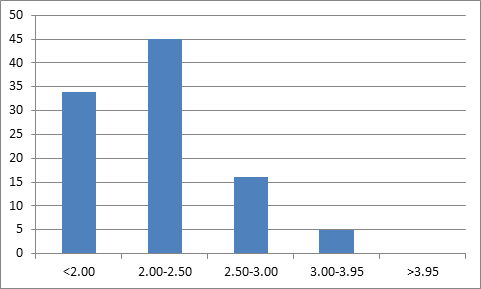
This survey shows that we are not fully prepared for cyber security threats. We must come up with solutions as fast as attackers are working and growing otherwise our personal information will be exposed or sold on Dark Web.
Dark Web is a major security concern, as it provides the complete anonymity to the users. The Dark Web makes it easy for cyber criminals to earn money by selling stolen information. People behind the TOR network usually do criminal activities; it becomes a type of an underground market where anyone can sell or provide any kind of services that may be illegal or seems offensive.
For many years we have seen that to steal money from the bank, robbers came directly with a weapon. But now things have been changed; the attacker hires employees for such a task so that no one generates notice.
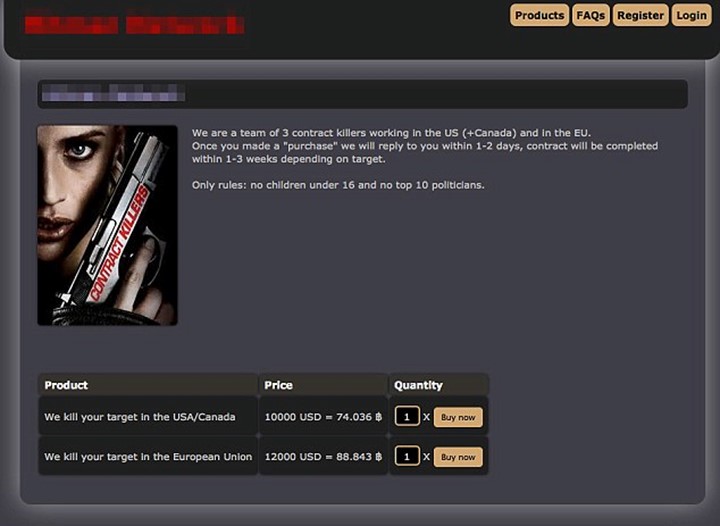
Insiders have become the most critical threat that any organization can have, more crucial than competitors. Insiders are actively recruited by criminals over Dark Web. This platform is mostly preferred to recruit employees from financial institutions, hospitals, government sectors and other organizations for offensive services.
Unsatisfied employees from many companies are selling their services to bad guys to inflict harm on their employers. However, many companies are hiring cyber security specialists and enlisting help from law enforcement forces to monitor and track users on Dark Web that are planning to cause any harm.
According to Krebs on Security, a pharmacy owner meets with federal agents once a week to see if his employees are active on the Dark Net. Back in the old days before Dark Web, maintaining anonymity was a hectic job, but now it has become easy to access the dark web to do criminal activities.
Insiders are the easiest target to perform such tasks to gather information of organization's routine task, and security policies to make any cyber attacks. Although in some cases, they don't even know that they are being used against their organization or in any cyber crime.
Research from IBM revealed that more than 55% of attacks were insider attacks originate from within the company, executed by a person who is in general authorized and trusted to access a company's electronic asset.
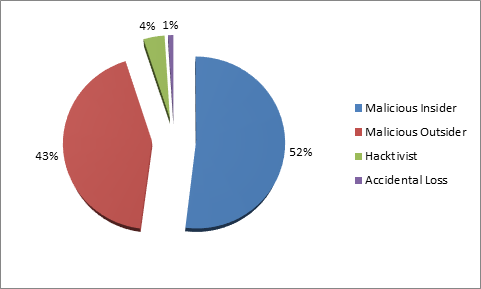
Here, it is most important to distinguish between external and insider cyber attacks. External cyber-attacks are originating from outside the organization that targets employees using spam emails and Phishing pages. Employees become victimized by these types of attacks due to lack of awareness, although the employees themselves do not originate these attacks. While, insider attacks are originated from within the organization. That is, executed by the person who is an authorized and trusted user to access the company's database.
An employee normally becomes disgruntled due to an unmet expectation, dissatisfaction or an unfortunate event like; the insider was expected to be promoted but was evidently passed over.
Many insider attacks have been reported over years. The companies are more affected by internal attacks than external. The numbers of insider attacks are incredibly high, as attackers prefer to launch their attack from inside rather breaking into the sophisticated security system.
Insider threats are more complex to respond to and cannot be addressed by technology alone. A much more non-technical and human-oriented defense approach is required. Securing a company against insider threats has been a difficult process; very often, companies do not even take insiders as a threat because they are focused on stopping external intruders. They assume their employee sincere and loyal.
As technology is evolving, it has become easier for an insider to do such activities over the company's network. A single USB can inject malware into an organization's database that can cause serious failure or complete damage to the information. Other means of connecting to company's electronic media are also crucial and should be prompted to use by network/security administer.
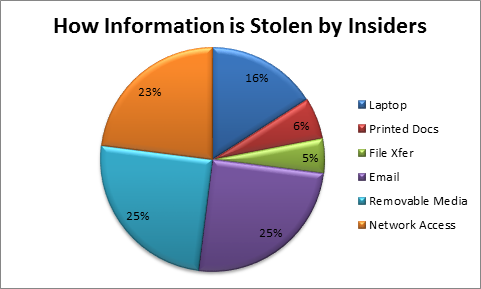
The insider attack involves deletion of data ranges from deleting specific records, and source code that corrupts system functionality that the company and its customers relied on. If we consider an insider as a permanent employee who has authorized access to a company's information systems and electronic assets, then we are already underestimating the risk. Insiders include anyone who has logical access to the company's electronic assets. This can include third-party contractors, visitors, and temporary employees.
In one case, the insider, who had full access to the company's network and systems, was terminated. On the day of the insider's termination, he proceeded to attack the organization remotely. The insider deleted crucial files on servers, deleted backup disks, and numerous records from databases used by other systems. The insider was able to attack the organization because his credentials were still enabled.
How Can an Organization Protect Against Insider Threats?
Implementing full proof countermeasures to eliminate insider threat is impossible. So what can be done to address this insider risk?
There is no doubt that, when the employee is wisely treated and trusted, there are less chances of an employee going rogue and becoming an insider threat. A good way to start is to do as much as possible to manage an employee's complete employment cycle from pre-employment to employment termination.
- The employee should be trained to use system and database securely.
- No biases should be created among employees.
- No privileged access should be given to any temporary employee.
- Credentials must be disabled when an employee terminates.
- In consideration of Cyber risk, the insider must be taken seriously.
- Strict Security policies should be implemented.
- Insider threat program should be created to manage all insider threats related activities.
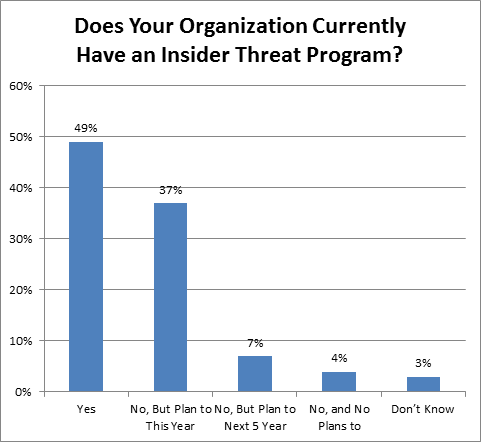
The most important is the insider threat program. The insider threat should be taken seriously as external threats, even are more crucial, and respective management program should be created to overcome and look after employees to prevent these threats before its damage.









