How to Ensure HIPAA HITECH Compliance
By now, most people have at least some passing familiarity with HIPAA – the federal rules and regulations that apply to the security and handling of personal information in health records. The Health Insurance Portability and Accountability Act went into effect in 1996, and was designed to achieve quite a few vital goals, including reducing fraud and abuse in the health care system, protecting health information, and giving Americans the ability to transfer and continue health insurance coverage when changing jobs or losing employment. It also mandated industry-wide standards for electronic billing and health care information handling.
The immediate impact of HIPAA is easy to see, but it actually goes far deeper than ensuring that health care providers and physicians handle patient information with care. According to the California Department of Health Care Services, it “requires health care providers and organizations, as well as their business associates, to develop and follow procedures that ensure the confidentiality of protected health information (PHI) when it is transferred, received, handled or shared.” Given that most of this is done electronically these days, technology plays a significant role, and the HIPAA HITECH Act was created specifically to ensure compliance with HIPAA rules in IT environments.
Implementing HIPAA Controls
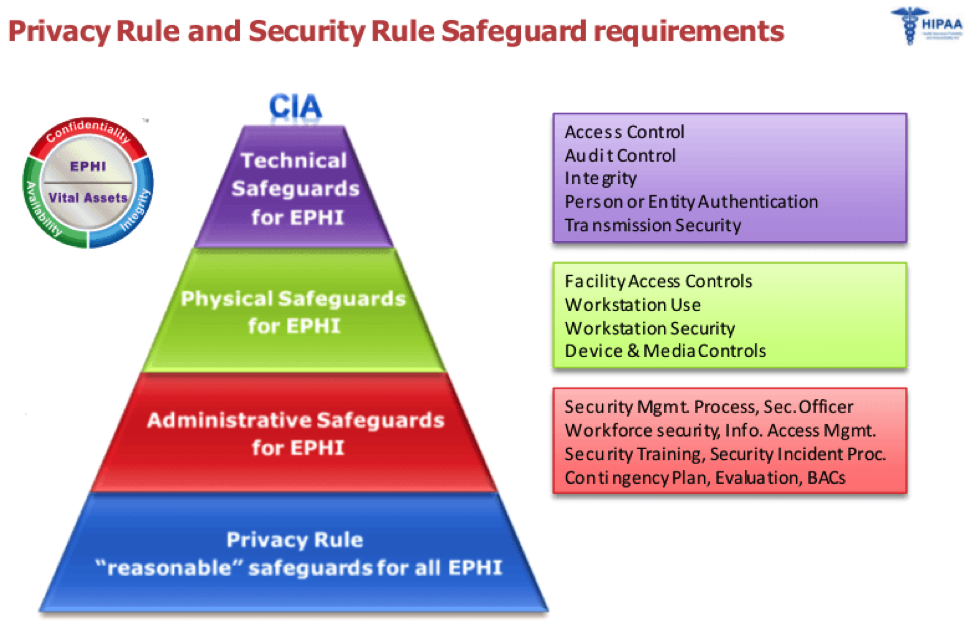
An example of the most common HIPAA/HITECH violations
What Is the HIPAA HITECH Act?
The HITECH Act (Health Information Technology for Economic and Clinical Health Act) expands HIPAA in many ways, and actually broadens its scope. It was introduced as part of the American Recovery and Reinvestment Act of 2009, and was enacted due to the dramatic increase in the adoption and use of electronic health record systems (EHRs) and, thus, the exchange of electronic protected health information (ePHI). Essentially, it requires that health care organizations “apply meaningful use of security technology to ensure the confidentiality, integrity, and availability of protected data.”
In a way, it’s similar to the stipulations in ISO 27001 for personal information and the PCI-DSS requirements for businesses that process, hold or store credit card information. However, rather than dealing with personal information or financial data, the HIPAA HITECH Act deals specifically with how health care organizations and their business partners protect health data.
What Does the HITECH Act Mean for Health Care Businesses and Organizations?
Given the fact that the HITECH Act is aimed solely at electronic storage and transmission of health data, let’s jump straight to the requirements. They’re pretty significant, and the Act doesn’t actually tell health organizations or related businesses how to comply with its rules. It only tells you what must be done, not how to do it. The Act does not stipulate any specific technologies, but focuses on principles that health care organizations and their business partners should follow when making choices in terms of technology, as well as in how those organizations deal with individuals.
Access to Information: First, the HITECH Act mandates that organizations are required to provide a patient, or the patient’s representative, with a copy of their medical records in “a designated record set for as long as the protected health information is maintained in the designated record set.” Essentially, you must provide all patients with access to inspect or retrieve a copy of their information as long as that information is retained. However, not all information is free to be accessed. The circumstances under which specific information (such as psychotherapy notes) still apply.
So, if a patient requests a copy of his or her x-rays after an automobile accident, and the organization has an EHR system in place, the organization must provide those records, and they must be delivered in electronic format (as long as the records are in electronic format). Given the increasing adoption of technology by consumers, it’s logical that more requests will be made for electronic records than for hardcopy records.
Use: The HIPAA and HITECH Acts both stipulate that organizations must have stringent controls in place that deal with how health information is stored, accessed, analyzed and used within an organization. However, HITECH also broadens the scope of the previous definition by extending it to the business associates and partners of health care organizations. These partners are now required to sign a Business Associate Agreement (BAA) with the health care organization. Not having a BAA in place is grounds for investigation and financial penalties. In addition, business associates working with health care organizations must have BAAs in place with their subcontractors, as well.
Repercussions of No BAA: Not ensuring that affiliated organizations and partners have a BAA in place carries the potential for serious repercussions. For instance, a clinic in North Carolina was required to pay $750,000 to settle claims that it worked with a business partner (exchanging patient x-rays) without having a BAA in place.
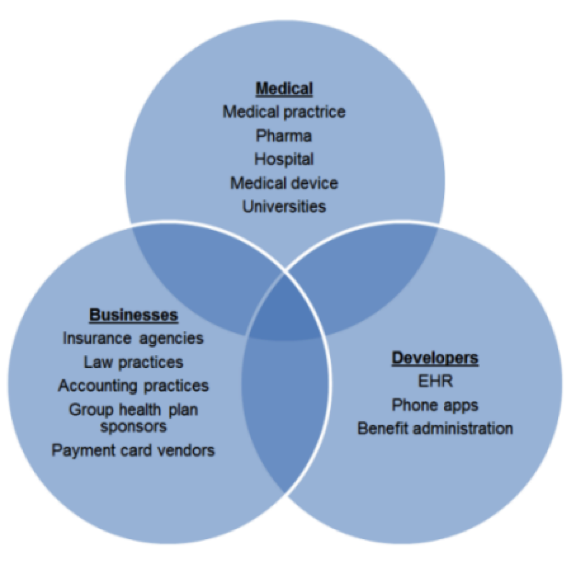
To follow this scenario, if a hospital works with a dialysis clinic but doesn’t have a BAA with that clinic, the hospital is in violation of HITECH rules. If that clinic subcontracts some of its responsibilities to another company and does not have a BAA with them, then both the hospital and the dialysis clinic are in violation of HITECH rules. Of course, this applies to more than just health care providers – it extends to any organization that stores, accesses, analyzes or uses patient medical information and their associates, which can include clearinghouses, insurance companies and an incredible number of other businesses.
There are plenty of other examples of health organizations or their partners being held accountable for errors. For instance, the state of Connecticut sued Health Net (an insurance company) for a breach that affected 1.5 million people (400,000 of which lived in Connecticut). The state received $250,000, and the insurer was on the hook for an additional $375,000 from suits brought by other states. Other similar high-profile cases include the Raleigh Orthopaedic Clinic, and the New York Presbyterian Hospital. Raleigh Orthopaedic Clinic settled with the government for $750,000, and the New York Presbyterian Hospital settled for $4.8 million.
However, don’t be tempted to think that a BAA absolves your organization of any wrongdoing if an audit finds that one of your subcontractors or business associates does not comply with HIPAA/HITECH. A BAA is not proof of compliance and it does not compel compliance, either.
It’s also important to understand that HIPAA penalties are not only assessed in the absence of a BAA. They are being issued for failure to safeguard patient information even in the face of phishing, malware and other outside threats that compromise the security of that information. For example, the University of Washington Medicine experienced a massive data breach in 2013 that compromised the information for approximately 90,000 people after an employee downloaded a phishing email attachment that contained malicious malware. It cost the school $750,000. Partners Healthcare experienced a similar breach due to phishing, but has not yet been fined.
An example of the myriad organizations impacted by HIPAA/HITECH
Notification of Breach: One of the most significant requirements imposed by the HITECH Act is that health organizations (and their business partners by association) are now required to let individuals know when their health information has been compromised by a data breach. And make no mistake, despite the implementation of HITECH Act compliance, many organizations are still experiencing massive data breaches. The five largest breaches of all time, consisting of millions of individuals’ records each, occurred in 2015, years after the HITECH Act went into effect. The Act also requires that in a breach that affects 500 or more patients, the organization must also notify the Department of Health and Human Services, and in some cases, even the local media so that the provider’s name can be publicized (as a penalty).
As an example, if a physician’s office experiences a breach with its EHR system, each patient whose information was breached must be notified. If that breach extends to 500 or more people, the office is required to notify the DHHR.
Penalties for Violation: The DHHR and the OCR (Office of Civil Rights) have instituted some serious penalties for organizations found in violation of HIPAA/HITECH requirements. For example, fines can rise as high as $25,000 per year for just one violation. In the case of wrongful disclosure, fines can reach $250,000 per case. Civil charges can be brought by states on behalf of victims to the tune of up to $1.5 million per year, as well. As of 2016, the OCR has investigated nearly 90,000 HIPAA breaches. However, there have been 126,472 complaints investigated, with 572 of those being referred to the Department of Justice.
So, what’s a health organization to do? There are some vital steps that must be followed to ensure compliance with HIPAA/HITECH mandates.
Steps to Take for HIPAA/HITECH Compliance
To be clear, neither the HIPAA nor the supporting HITECH Act stipulates any specific technologies or software to use in order to comply with regulations. With that being said, there are some specific steps that must be taken to ensure that an organization is in compliance.
Considerations in HIPAA/HITECH compliance
Step 1: Assess your current system and determine if it actually protects patient health information. Stringent security standards must be developed (if they’re not currently in place) and applied across the entire organization. The HITECH Act actually states, “Ensure the confidentiality, integrity and availability of all ePHI created, received, maintained or transmitted.” This is one of the most significant challenges facing organizations, particularly those with semi-public facilities (think hospitals and medical clinics). This rule applies to all electronic devices used in the environment, from PCs at nurses’ stations to cell phones in use by physicians and everything in between. BYOD (bring your own device) policies need to be created and enforced to ensure that safeguards are in place to protect patient information at all times.
Step 2: Analyze the risks and threats to the integrity of patient information within your organization. Based on that analysis, it may be necessary to institute new forms of protection, such as file encryption and transfer method encryption. Something as simple as an unencrypted text message that contains private information can lead to a breach. Again, this can be a serious hurdle, particularly for organizations without expert IT staff or enough resources to allow the IT staff to conduct a thorough analysis.
Step 3: Protect the information in your system from “impermissible uses or disclosures”. Essentially, this means ensuring that only those with a “need to know” have access to that information at any time, and can require the use of employee-specific credentials (login and password), two-factor authentication and other steps. Again, this poses a pretty big challenge to health organizations and related businesses, particularly for larger operations that might employ hundreds, or even thousands of people, all of whom need their own credentials (if they are required to have access to patient information in any way, shape or form).
Step 4: Develop an information protection and use policy that applies to your organization’s entire workforce, and then enforce that policy. It is also vital that you provide ongoing training and education for your staff. This applies to long-term employees, as well as new employees completing the onboarding process. In some ways, this is a simpler step than those that have gone before, but it requires a great deal of insight into the daily operation requirements of your organization, as well as the ways in which health records are used within the organization.
Step 5: Regularly inspect your security solutions and underpinning system, as well as your policies and procedures regarding health data to make sure that they still comply with HIPAA/HITECH requirements. Note that this is a requirement of HIPAA, although HITECH adds on the requirement that you must also undergo third-party auditing. Your ongoing inspections should reveal weaknesses that evolve over time as procedures change, staff members come and go, and even with changing hardware in use within the organization.
Step 6: Document what must be documented. The HITECH Act stipulates that “If an action, activity or assessment is required by the security rule to be documented, maintain a written (which may be electronic) record of the action, activity or assessment.” Make sure that your documentation practices are up to snuff, and that those documents are stored securely and easily accessible to both your organization (on a need to know basis), as well as third-party auditors.
Step 7: Prepare for audits. A significant requirement of the HITECH Act is that all organizations handling patient health information in any manner are subject to third-party auditing. The DHHR and OCR are stepping up their efforts here to a considerable extent, largely in response to the growing number of data breaches.
Conclusion
HIPAA/HITECH Act compliance isn’t simple, and it’s most definitely not straightforward. The language of the Acts alone makes it difficult to determine the requirements that pertain to the various organizations that work with patient health information in different ways. However, compliance is not optional. The government is dramatically stepping up enforcement of HIPAA/HITECH compliance with organizations large and small, and at all levels. Even associates of associates of associates are being scrutinized in the ongoing effort to protect vital health data and prevent it from falling into the wrong hands. If your organization does not comply with HIPAA/HITECH, it is past time that it should.
Sources:
http://www.hipaasurvivalguide.com/hitech-act-summary.php
https://www.qualys.com/solutions/compliance/hipaa-hitech/
http://www.bna.com/nc-clinic-pays-n57982070223/
http://healthitsecurity.com/news/what-are-the-3-key-layers-in-healthcare-data-security
http://www.dhcs.ca.gov/formsandpubs/laws/hipaa/Pages/1.00WhatisHIPAA.aspx
http://www.hitechanswers.net/hitech-act-compliance-hipaa-privacy/
http://www.ct.gov/ag/cwp/view.asp?A=2341&Q=453918
http://www.hhs.gov/hipaa/for-professionals/compliance-enforcement/data/numbers-glance/index.html
Implementing HIPAA Controls