VLAN hacking
In Virtual LAN or VLAN is a group of hosts communicate with each other, even thoughthey are in different physical location. Virtual LAN provides location independence to the users, able to save the bandwidth, manage the device, cost effective for the organization are some of the facilities provided by the Virtual LAN.
VLAN is based on Layer 2 "Data link" of the OSI Model. The OSI layers are independent of each other and they communicate with each other. If any one of the layer gets compromised the other layers also fail. The VLAN is on the Data Link layer, which is as vulnerable to attacks as any other layer on the OSI model.

FREE role-guided training plans
Security issues faced by a VLAN
When it comes to VLAN, it is best suited for Traffic management and definitely not for security. Some of the security issues faced by VLAN are given below.
ARP attack
ARP is an Address Resolution Protocol which is designed for a friendly environment. ARP works by associating IP address of Layer 3 with MAC address of Layer 2.
ARP lacks very much when it comes to security, a malicious user is able to use a forged IP address of Layer 3 and MAC address of Layer 2, there is no way to verify those forged details in ARP. The malicious user identifies him as a legitimate user and starts to use resources available on the network. It's even possible to transmit ARP packets to a device in a different VLAN using those forged details.
It even allows the malicious user to perform a Man-in-the-middle ( MiM )attack. A MiM attack is performed when a network device identifies itself as another network device such as default gateway, there is no way to verify those credentials.
Then the attacker starts to send the ARP packets to the targeted victim, those ARP packets cannot be verified by the receiver. The receiver ARP table is filled with the forged details of the ARP packets sent by the attacker. The attacker is then able to gather all the information about the receiver and even tries to resemble as the receiver to other devices in the network. At the end of the attack, the attacker corrects the ARP tables and the network comes back to normal.
Tool which can be used for performing ARP spoofing are Arpspoof, Arpoison, Cain and Abel, and Ettercap, Trapper which was inspired from the famous tool called Cain.
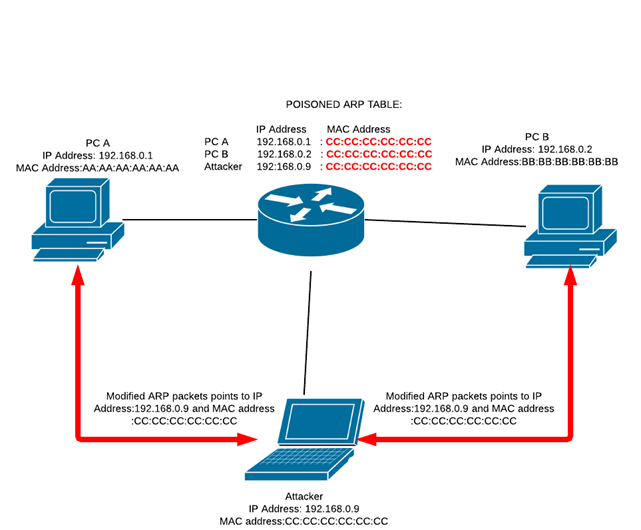
An effective countermeasure to ARP attacks is Dynamic ARP inspection (DAI). DAI is a security feature which validates all the ARP packets in a network. It discards the ARP packets with invalid IP and MAC address.
To enable DAI on a VLAN(DHCP Environment on CISCO)
Enters into the Global Configuration command
Router# configure terminal
Enables DAI on VLAN by using iparp inspection Vlan{vlan_id|vlan_range} from the global configuration table
Router(config)# iparp inspection vlan {vlan_ID |vlan_range}
Finally, Verifies the Configuration
Router(config-if)# do show iparp inspection vlan {vlan_ID |vlan_range} | begin Vlan
MAC flooding attack
MAC flooding attack is one of the common attacks on a VLAN. In a MAC flooding attack, the switch is flooded with packets of different MAC address therefore consuming memory on the switch. During the MAC flooding attack, switch starts to behave like a "hub" where it starts to share the data with all the ports. Thus a malicious user is able to use a Packet sniffer to extract the sensitive data's.
For example, there are 3 workstations WA, WB and WC. When WA tries to send a data to WB it is not viewed by the WC because of switch. Now, a malicious user consider WC, starts a MAC flooding attack on switch with different MAC Address, the memory of switch is filled. Now, the switch starts to behave like a HUB, thus when next time WA tries to send a data to WB, it will be easily viewed by the WC.
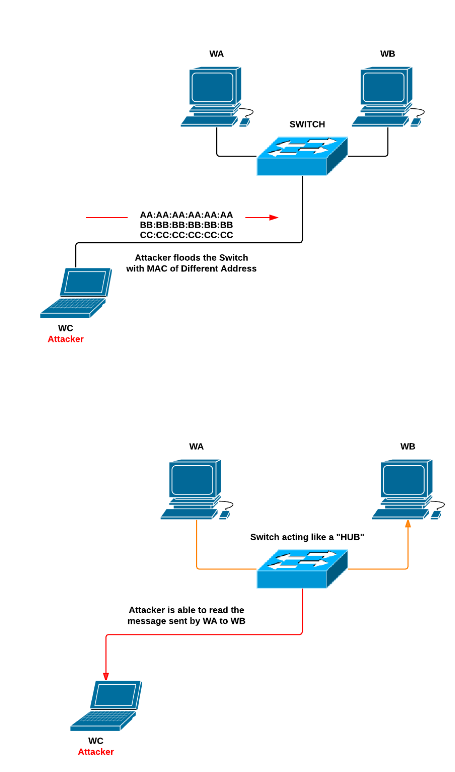
The best way to secure VLAN from MAC flooding attack is through Static Secure MAC address. They need to be manually configured using the command "switchport port-security mac-address mac-address interface ".The other way to secure MAC Flooding is to limit the amount of MAC address received by the port.
DHCP attack
DHCP is Dynamic host configuration protocol which enables a server to automatically assign IP address to a host with other information such as subnet mask and default gateway. There are two types of DHCP attack on VLAN; they are DHCP starvation Attack and DHCP rogue attack.
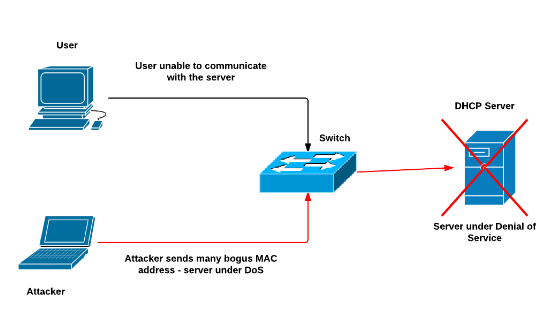
In DHCP starvation attack, a malicious user sends numerous DHCP request with spoofed MAC address. This causes a Denial of Service at DHCP server, thus not allowing an authentic user from using the network. It can be avoided by limiting the number of MAC address.
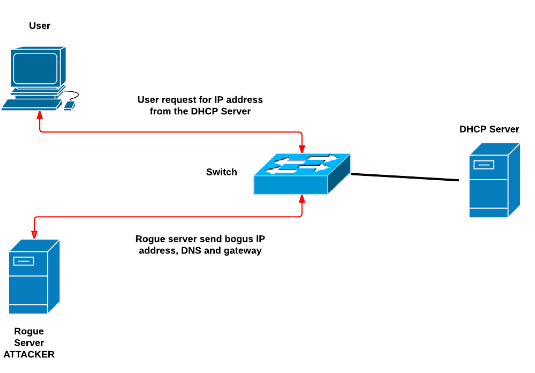
In DHCP rouge attack, a malicious user acts as if he is a DHCP server and provides a reliable user with Wrong gateway, Wrong DNS and Wrong IP. The user will experience numerous problems ranging from connection problem to communication problems with other host. This can be avoided by using a multilayer switch which got a capability to drop the packets.
One of the tools which can be used for these kind of attack is Yersinia which is a network tool designed to take advantage of some weakness in different network protocols. This can be also used for spanning-tree protocol attack.
Spanning-tree protocol attack
When a malicious user sends a STP message with a priority zero value thus making a new root bridge thus compromising the entire network is known as Spanning-Tree Protocol attack. It can be avoided by disabling spanning -tree function to the entire user interface. This can also be done by enabling root guard on CISCO equipment or BPDU guard on user's port to disable Priority Zero value thus the malicious user won't be able to gain the root bridge
To enable Root Guard on CatOS
vega> (enable) set spantree guard root 1/1 Rootguard on port 1/1 is enabled. Warning!! Enabling rootguard may result in a topology change. vega> (enable)
To enable BPDU guard on CatOS
Console> (enable) set spantreeportfastbpdu-guard enable
Spantreeportfastbpdu-guard enabled on this switch.
Console> (enable)
Multicast brute force attack
The multicast brute force attack proceeds when a switch receives a number of multicast frames in rapid succession. This causes the frames to leak into other VLAN instead of containing it on original VLAN. This might also cause a scenario similar to denial of service.
The multicast brute force attack can be stopped by a well-equipped switch which prevents the frames from leaking into other VLAN and therefore containing them in the original VLAN.
Private VLAN attack
A Private VLAN is a feature in Layer 2 which is used to isolate the traffic only at layer2. When a layer 3,device such as a router is connected to a Private VLAN, it supposed to forward all the traffic received by the router to whatever destination it's meant for. Sometimes a malicious user might use it for his advantage.
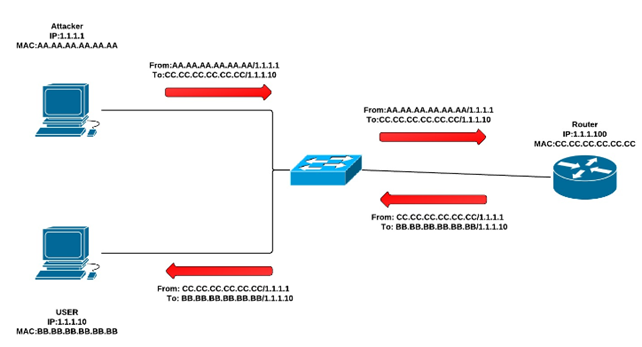
This can be prevented by configuring the VLAN access list.
To define a VLAN access map
# vlan access-mapmap_name [0-65535]
To delete a map sequence from VLAN access map
# no vlan access-mapmap_name 0-65535
To delete the VLAN access map
# no vlan access-mapmap_name
VMPS/VQP attack:
This kind of attack normally happens on Dynamic VLAN Access Ports. This VMPS uses VQP protocol. The disadvantage of VMPS is that it doesn't use authentication for assigning Vlans based on the MAC address and also it is over UDP which further makes it more vulnerable for the attack.
Normally a DOS attack happens in order to join the unauthenticated VLAN.
VLAN hopping attack
VLAN hopping works by sending packets to a port which should not be accessible. Basically, in VLAN hopping attack there are two types
- Switch Spoofing
- Double Tagging
Switch Spoofing
Switch spoofing happens when a malicious user tries to configure a system to spoof itself as a switch by matching itself to 802.1q or ISL. The malicious user is able to spoof the switch with help of (Dynamic Trunk Protocol) DTP signaling.
Double Tagging
Double tagging is a method involves tagging transmitted frames with two 802.1q headers, one of the headers is used for Victim switch and another is used for the attacker's switch.
The simplest way to prevent a VLAN Hopping attack is by disabling Dynamic Trunk protocol (DTP) on all untrusted ports.
For example:
ciscoswitch# conf t
ciscoswitc(config)# int gi1/10
ciscoswitch(config-if)# switchportnonegotiate
From the example "switchportnonegotiate" disables the DTP.
Double-encapsulated 802.1Q
IEEE 802.1Q helps to create smaller network out of large networks. A large network is very slow and consumes lot of bandwidth whereas a smaller network is easier to manage and consumes less bandwidth. So, it's desirable to have a smaller network than a large complex network. IEEE802.1Q was developed as a part of IEEE802.
To use IEEE802.1Q, it's must that we implement Trunk. Suppose Trunk is enabled in IEEE802.1Q, a certain type of attack is performed on 802.1Q. This attack is called Double Encapsulation attack. It adds two tags to the original frame. In IEEE 802.1Q trunk always modify the frame by eliminating the outer tag but the inner tag remains permanently and it becomes the destination.
To prevent Double-Encapsulation in 802.1Q, the native VLAN should not be assigned to any port. We must force traffic on trunk to always carry a tag. To make the trunk to carry a tag, we can use the command "Switch(config)# vlan dot1q tag native". It is a global command to tag the native VLAN.
Random frame stress attack
Random frame stress attack got many types but it's generally a brute force attack performed on several fields. In this type of brute force attack the source address and destination address are kept constant. They are primarily performed to test the switch ability when it encounters abnormalities in inputs and calculations.
Random frame stress attack can be prevented when a Private VLAN or PVLAN is used to separate the host from receiving those unwanted inputs.
Using of Shodan for gathering information:
This is just to find out the online devices using Shodan (http://www.shodanhq.com). Shodan stands for Sentient Hyper-Optimized Data Access Network which is almost similar to a normal search engine except for its results. Shodan grabs the banner of the devices and gives a detail information, thus helping the user while pen testing.
The usage of shodan is simple and easy and also has shodan syntax for making the results more filtered. For example, to find a device or service running in the target, then the syntax would be "service name" hostname: target.com. Similarly we can discover more devices and making the analysis of the target easier and also reducing the time.
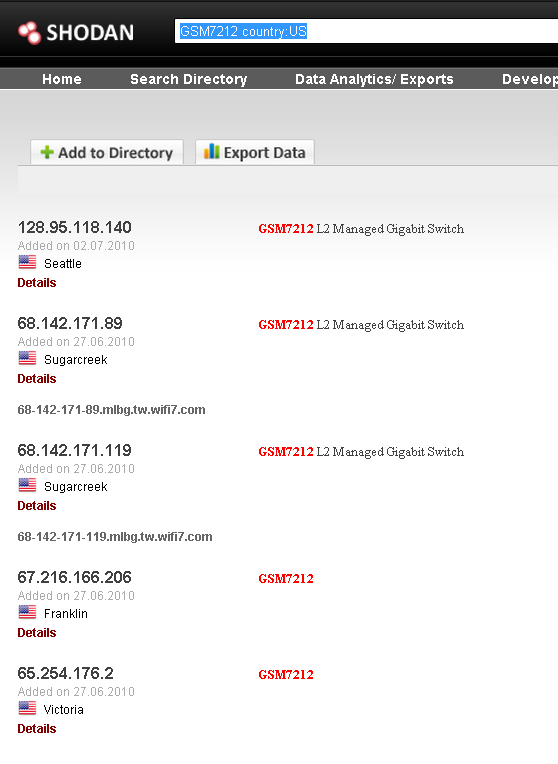
Another example would be finding the L2 devices like for example Netgear GSM7212 L2 switch from a particular country. The image shows the Netgear switch from the country US. Similarly, we can find different devices for information gathering phase.
Conclusion
I hope this helps understand various VLAN attacks and makes the concept simpler. On other hand, attacking a Vlan is tough. And never forget to change the default settings of your devices.
A few points for the administrators would be:
- Manage switches in as secure a manner
- The native VLAN ID should not be used for trunking. Always use a dedicated VLAN ID for all trunk ports.
- Set all user ports to non trunking
- Do configure port-security feature in the switch for more protection. (Note: be careful about configuring the port-security feature.)
- Avoid using VLAN 1
- Deploy port-security where possible for user ports
- Enable BPDU Guard for STP attack mitigation
- Use private VLAN where appropriate to further divide L2 networks
- If VTP is used, use MD5 authentication.
- Unused ports can be disabled.

What should you learn next?









