The Internet Underground: Tor Hidden Services
Some people think onion routing or the Tor network is for criminals and people with something to hide. Well, they are half right. The Tor network was designed to give a masked, "semi-safe", passage to those who needed to get information out.
According to its website, "Tor was originally designed, implemented, and deployed as a third-generation onion routing project of the U.S. Naval Research Laboratory. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Today, it is used every day for a wide variety of purposes by normal people, the military, journalists, law enforcement officers, activists, and many others."

FREE role-guided training plans
People use Tor as a way to bypass traffic filters or monitors throughout the Internet. If using a minimum of SSL encryption, this medium has been recognized as being a "safer" way to communicate over the Internet. What most people do not realize is that there is an entire subnet underground out there called "Darknet" or "Deepweb". Others just call the underground Internet Tor network hidden servers. These hidden servers usually have a ".onion" extension and can only be seen using a Tor proxy or TorVPN. The easiest way to get onto the Tor network is with the Tor Browser Bundle (TBB). It is free and very easy to install and then use. All you have to do is go to the torproject.org and download TBB and within minutes you will be connected.
There are legitimate reasons to use Tor, especially for those who are trying to hide their identities from oppressive governmental regimes or reporters trying to minimize leaking the identity of informants. Some will even stay on the proxy network and use services like Tor mail, a web based email service. There are still some anonymity challenges. If you are on the same network, you may still leak the originating IP address and there is a risk of someone capturing your traffic. Some will even go as far as only using HTTPS (SSL encryption) or reverting back to the good old VPN.

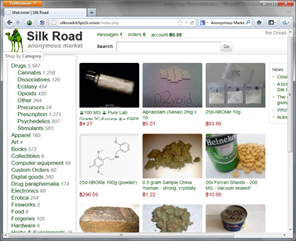
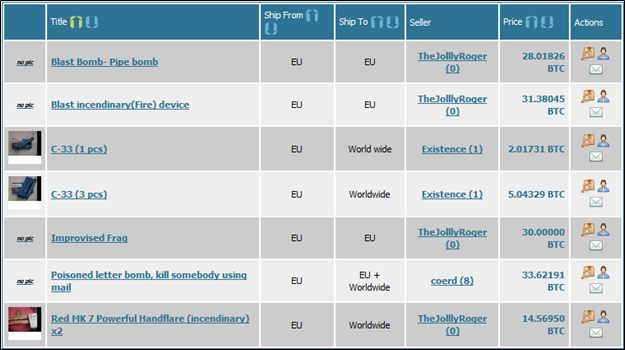
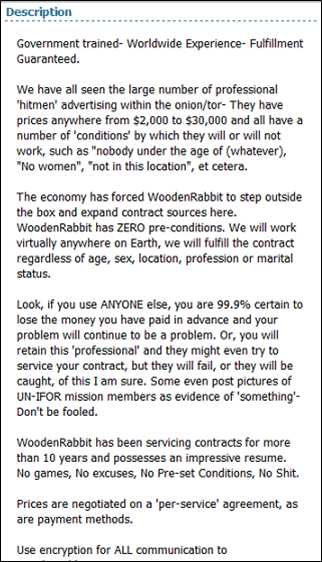
There are darker usages of the hidden servers. There are E-Black Markets all over this network that sell anything from meth to machine guns and services that range from assembling credit card data to assassinations ("you give us a picture; we'll give you an autopsy report!"). Most of the sites trade their goods with an e-currency called Bitcoins, an anonymous electronic commodity that can purchase almost anything.
One of the most popular "secret" sites called "The Silk Road" or SR has almost anything you can think of. SR has evolved over the years and has recently dropped its weapon sales section and created a new site called the Armory. Shortly after, the Armory closed due to the lack of traffic and interest. They have also banned assassination services to minimize attention from showing up on Law Enforcement's radar. They still have plenty of drugs, counterfeit items, and stolen goods though.
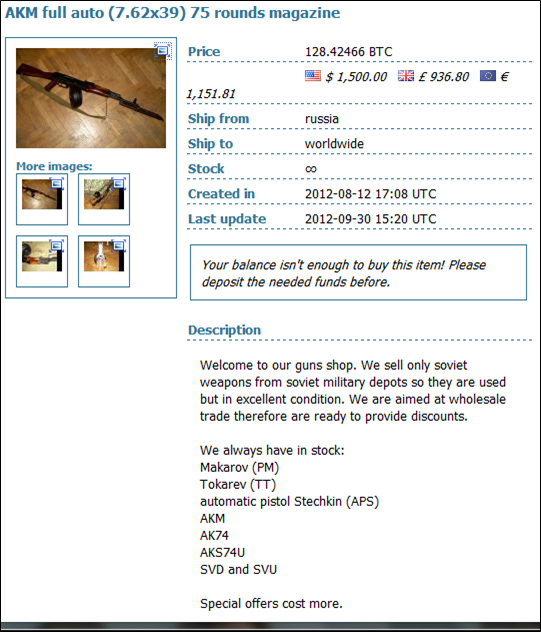
There are still plenty of other sites that focus on arms dealing or unfiltered auction site. Once you are on Tor, the next thing you would have to do to communicate with some of these sites is to get an anonymous Tor based email. This is a web based email that you log into that acts just like a regular email except it only exists in the Tor world. Another popular communications mechanism is TorPM.
Tor Communications
- Tor Mail – http://jhiwjjlqpyawmpjx.onion
E-Black Market sites
- The Silk Road: http://silkroadvb5piz3r.onion/index.php
- Black Market Reloaded: http://5onwnspjvuk7cwvk.onion/index.php
- Zanzibar's underground marketplace: http://okx5b2r76olbriil.onion/
- TorBlackmarket: http://7v2i3bwsaj7cjs34.onion/
- EU Weapons & Ammunition: http://4eiruntyxxbgfv7o.onion/snapbbs/2e76676/
- CC4ALL (Credit Card site): http://qhkt6cqo2dfs2llt.onion/
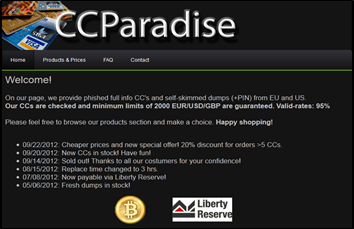
- CC Paradise: http://mxdcyv6gjs3tvt5u.onion/
- C'thulhu ("organized criminal group"): http://iacgq6y2j2nfudy7.onion/
- Assassination Board: http://4eiruntyxxbgfv7o.onion/
- Another hitman: http://2v3o2fpukdlpk5nf.onion/
- Swattingservice (fake bomb threats): http://jd2iqa4yt7vqvu5o.onion/
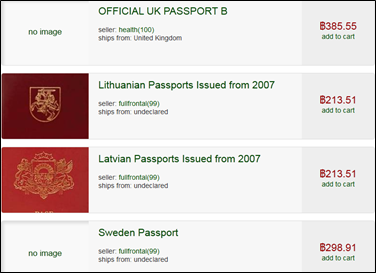
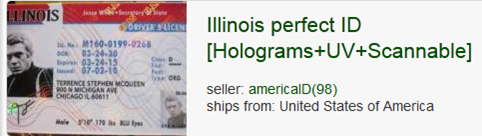
- Onion-ID (fake ID): http://g6lfrbqd3krju3ek.onion/
- Quality Counterfeits: http://i3rg5diydpbxkewu.onion/
Social Network
- mul.tiver.se: http://ofrmtr2fphxkqgz3.onion/
Informational
- LiberaTor (weaponry & training): http://p2uekn2yfvlvpzbu.onion/
- The Hidden Wiki: http://kpvz7ki2v5agwt35.onion/wiki/
Search
- Torch: http://xmh57jrzrnw6insl.onion/
- Torlinks: http://torlinkbgs6aabns.onion/
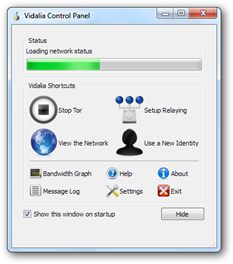
So let's take this step by step.
- Download "Tor Browser Bundle" from torproject.org.
- Double left click on "Start Tor Browser".
- You should then see Vidalia connecting to Tor.
- The Tor Browser should automatically open.
You are now on the "Deepweb."
You can now access ".onion" domains.
- Create a TorMail account on jhiwjjlqpyawmpjx.onion.
- Create a TorPM account on 4eiruntyxxbgfv7o.onion/pm/
- Enjoy a little more anonymity for research.
Disclaimer: do NOT break the law. This was written to explain what the (Darkweb / Deepnet / Tor hidden service) is and what kind of things you may find. It is not an invitation to break the law with no recourse. Just like any network, this one has both good and bad guys. If you break the law, you will get caught. Bad guys have to be lucky EVERY time. Good guys only have to be lucky once.


FREE role-guided training plans









