The role of technology in modern terrorism
Technology is a foundation of modern society, it governs its dynamics, and therefore, it is normal that also the terrorism will benefit from it.
We are living a very difficult period, the terrorism is threatening the society and cultures on a global scale, and differently from the past, it has reached a global dimension.

What should you learn next?
We are facing a global alert. Intelligence and law enforcement agencies worldwide are warning about possible terrorist attacks in the major cities.
Parigi, Istanbul, Jakarta are last locations in order of time where the terrorist threat has demonstrated its strength, where terrorists have hit the defenseless population with a military strategy.
The modern terrorism is instantaneous and unpredictable, a global threat that hit its targets, but that at same time hits a wide audience thanks to the technology, it is bringing the terror into our homes.
The cyberspace is an environment without boundaries, a privileged place where terrorists find resources, make propaganda activities and from which it is possible to launch the attacks against enemies everywhere in the world.
Social media is an essential element of modern terrorism; these powerful platforms allow terrorists to communicate, to make propaganda and recruit new sympathizers.
Every terrorist attack is similar to a dramatic representation, in which the Internet is the stage.
"Terrorist attacks are often carefully choreographed to attract the attention of the electronic media and the international press. Terrorism is aimed at the people watching, not at the actual victims. Terrorism is a theater," wrote Brian Jenkins, an International Terrorism expert.
Figure 1 - ISIS images spread through social media
Although members of the Islamic state use new technologies with great skill, many other terrorist groups use the Internet and its resources every day.
Many other groups are active on the web, including Hamas (the Islamic Resistance Movement), the Lebanese Hezbollah (Party of God), the Egyptian Al-Gama'a at Islamiyah, the Popular Democratic Liberation Front Party in Turkey (DHKP / C), the Kurdish Workers' Party (PKK), the Zapatista National Liberation Army (ELNZ), the Islamic Movement of Uzbekistan (IMU) the Mujahedin, and the Chechens.
Surfing on the Web it is quite easy to find material spread by groups of terrorists, a study titled "Terrorism in Cyberspace: The Next Generation" conducted by the Prof. Gabriel Weimann demonstrated a significant increase in the presence of terrorists in the Internet since 1998.
The experts explained that in 1998 the number of websites containing terrorist material was 12, in 2003 he counted 2,650 websites and in September 2015 the total number has reached 9,800.
The data leaves no doubts; terrorist organizations are looking with increasing interest to the Internet, let me also add that a growing number of radical organizations are also exploiting darknets, a circumstance that greatly increases the number of sites currently operated by terrorist organizations.
What are the advantages in the use of the Internet?
The Internet offers a simple access to a global stage, every terrorist could instantly reach large masses or targets specific groups of individuals. Under specific circumstances, the resources of the Internet could offer anonymity to the user, a great advantage for a terrorist organization that wants to spread their message while remaining undetected.
The internet is cheap; a group of terrorists could arrange efficient propaganda campaigns without economic effort.
But the aspect that most of all makes the Internet a privileged instrument for terrorist groups is that it is interactive. For the first time in the history, groups like the Islamic State could interact with their sympathizers and with their targets.
The strength of terrorist attacks today is the amplification effect obtained through social media, terrorists hit their targets and at the same time use the technology to make propaganda e spread fear among wide audience worldwide.
The Internet, and generally speaking technology, could be exploited by terrorist organizations for several purposes including:
- Propaganda
- Psychological warfare
- Recruitment and mobilization
- Fundraising
- Data Mining, information gathering
- Secure communications
- Cyber attacks
- Software distribution (e.g., mobile app)
- Buying false documents
- Training
The Internet propaganda is probably the most common use of technology by terrorist organizations. Groups like the ISIS demonstrated a great mastery of the technology and a deep knowledge of the techniques of communication.
Each video is carefully prepared, and its programming is meticulous and aims to reach the largest number of individuals.
Terrorists use the new social platforms like Facebook, Twitter and media services such as YouTube. Their language is direct, young, and it can reach a specific audience by using images with a high emotional impact.
The online propaganda is multi-lingual. It reaches not only Arab people and is easily accessible to young people.
The amplification effect is obtained through easy dissemination of content, sympathizers and media outlets allow easy sharing of the terrorist messages through emails, messaging and mobile apps.
Figure 2 - ISIS Video Message
The chain of communication leading massacres and executions directly into our homes is extremely short, a few tools (i.e. A smartphone, a camera and a laptop) and the free Internet network are the pillars of the new strategy of terror.
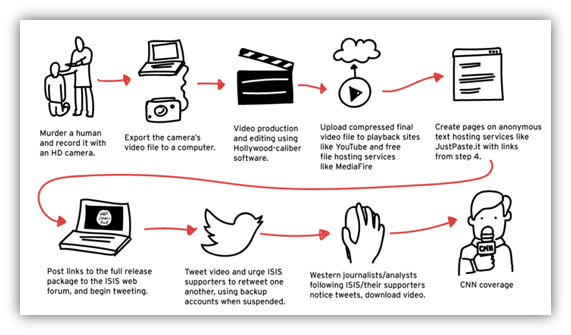
Figure 3 - Chain of Terrorist propaganda (Gawker.com)
One of the phenomena worries the intelligence agencies most of all is the narrowcasting; that consists in the dissemination of information to a narrow audience. The narrowcasting targets specific segments of the public, contextualizing the practice to the terrorism, the propaganda content could be crafted to reach teenagers.
Security experts have uncovered a number of websites offering pro-jihad content designed using a 'comic-style' and high impact Videos and Animations.
On the Internet, it is also possible to find infographics and computer "games," both media content types very popular among young people.
Figure 4 - ISIS infographic
Social media is a privileged instrument of propaganda; this means that analyzing them it is possible to follow the events and their geographic location.
To give you a better idea of this concept, let's consider a study conducted by the threat intelligence firm Recorded Future that analyzed the tweets sharing content related to the IS and its operations until February 2015.
The results reported in the following table shows a significant absolute increase in Saudi Arabia and Egypt, the countries where the IS aroused the greatest interest.
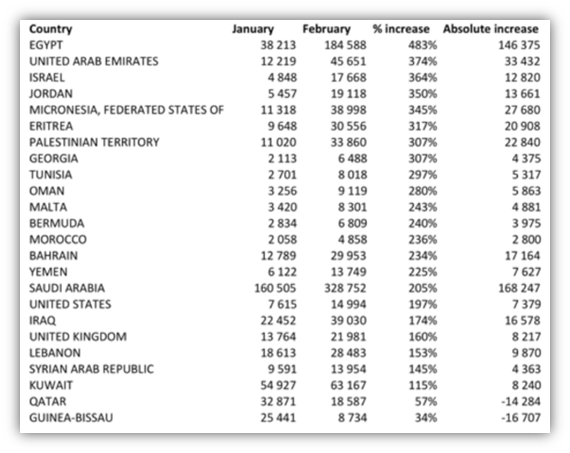
Figure 5. Tweets related to Islamic State (Feb. 2015 - Source Recorded Future)
Social media platforms and forums are used by terrorist organizations to share propaganda and training material.
On the Internet, it is possible to find any training material, including manuals for the preparation of chemical weapons and bombs. Experts have also discovered documents containing the instructions for kidnappings and techniques of torture. Once again, the technology assumes a crucial role for terrorists that also share manuals for optimizing the use of social media and communication platforms avoiding monitoring operated by Intelligence agencies.
In December, alleged members of the Islamic State launched a new cyber war magazine for jihadists titled Kybernetiq that instructs militants about technology.
The magazine aims to instruct jihadist on how to participate in the cyber war against the Western infidels. The members of the ISIS consider technology a crucial instrument in the fight against its opponents, and the Kybernetiq magazine explains it.
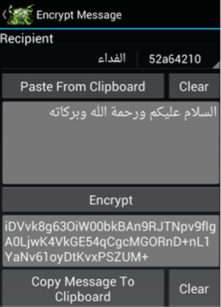
One of the articles in the first number titled "Digital Brand" states explained the importance to use encryption to protect communications avoiding any modification of the well-known enciphering algorithm. Each modification may compromise the robustness of the algorithm, for this reason, the author of the post incentives the use of secure end-to-end encryption systems such as the GNU Privacy Guard (GnuPG)-encryption program.
"as a brother in Islam, I feel obliged in this post-Snowden era to strongly discourage crypto-programs with a mujahid branding. This includes programs like Asrar al-Mujahideen, Amn al-Mujahid, Asrar al-Ghurabaa and various mobile applications."
The articles included in the Kybernetiq magazine illustrates the ISIS members the programs to protect their anonymity avoiding eavesdropping and how to use them. A specific session was written to explain how intelligence agencies use metadata to track terrorists. Under a section titled "Metadata can kill", author of the magazine clearly warned of surveillance which is undertaken by intelligence agencies like the US National Security Agency (NSA).

Figure 6 - Kybernetiq Magazine (ISIS)
The Internet is a mine for terrorists, it includes precious information that could be used by terrorist to attack specific targets. The analysis of Open Sources allows attackers to collect data on targets and allow terrorists to conduct a passive reconnaissance.
Many web services could be used to obtain information related to a specific place that terrorists intend to attack. Google Maps could give attackers aerial photo of the location of the attack; these pictures could reveal the presence of supervisory staff, checkpoints, fence, entry points and much more.
This information could be crossed with data obtained by querying other services, like worldc.am, that could provide the attacker with images took by Instagram users in a specific location.
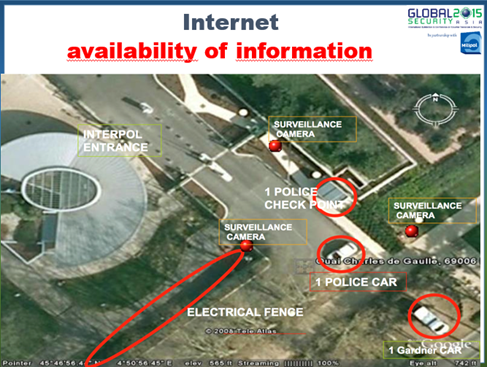
Figure 7 - Information Gathering from Google Maps
Another aspect related the use of technology made by a terrorist organization is the communication. Modern terrorists make a large use of mobile applications and other solutions for secure communications.
In May 2014, web intelligence firm Recorded Future published an interesting research on the use of encryption made by Al-Qaeda after the Snowden leaks. The study reported that members of Al-Qaeda were developing a series of new encryption software in response to NSA surveillance.
Since 2007, Al-Qaeda groups have developed the encryption software Mujahideen Secrets used to protect online and cellular communications, but according to the report of the intelligence, the militants were using different new encryption tools and communication channels (New services like mobile, instant messaging).
The below tools were designed starting from the Mujahideen Secrets tool used by terrorists of Al-Qaeda:
- Tashfeer al-Jawwal, a mobile encryption platform developed by the Global Islamic Media Front (GIMF) and released in September 2013.
- Asrar al-Ghurabaa, another alternative encryption program developed by the Islamic State of Iraq and Al-Sham and released in November 2013, around the same time the group broke away from the main Al-Qaeda following a power struggle.
- Amn al-Mujahid, an encryption software program developed by Al-Fajr TechnicalCommittee which is a mainstream Al-Qaeda organization and released in December 2013.
In a second report published by Recorded Future in collaboration with experts at ReversingLabs is explained that groups belonging to Al-Qaeda's media arms were showing a growing interest in mobile technology and that Android is the preferred platform for these groups due to the large availability and affordability of Android phones in their countries.
Since the first report provided by the Recorded Future firm, the group Al-Fajr released a new Android encryption app in June 2014 while GIMF also released a new version of their Android app.
Figura 8 - Android Mobile App developed by Terrorists
According to the analysts, there is a strict correlation between Snowden leaks and the increased pace of innovation in encryption technology by Al-Qaeda.
"Take your precautions, especially in the midst of the rapidly developing news about the cooperation of global companies with the international intelligence agencies, in the detection of data exchanged over smartphones." is reported on the Tashfeer al-Jawwal download page.
As Al-Qaeda has launched new software products and modules, are they using new crypto algorithms invented by themselves ("home-brew") or adopting new algorithms available to the public?
Based on the analysis of the Recorded experts conducted through the reverse engineering of the encryption application used by the member of Al-Qaeda, the groups aren't using home-brew encryption.
Returning to the present day, according to the Christian Science Monitor, the Ghost Security Group the ISIS has developed an Android mobile app used by members of the terror organization.
The Ghost Security Group is the notorious group of cyber experts in counter-terrorism networks that are involved in a series of initiatives against the ISIS radical group online.
The Android app discovered by the experts is spread through hidden channels in popular messaging apps like Telegram. The ISIS members have developed the app as an alternative communication channel; the mobile application is reportedly used to spread propaganda and share information on the operations of the group.
"They want to create a broadcast capability that is more secure than just leveraging Twitter and Facebook," Ghost Security Group chief operating officer Michael Smith II told the Christian Science Monitor. "Increasingly what you will see is the focus on developing means to control the distribution of their materials on a global scale."
In January 2016, experts from the Ghost Security Group discovered new Android App for encrypted communication that integrates other mobile applications specifically developed to share propaganda content and recruiting material.
Last month, security and intelligence experts, including Ghost Security, noticed that social media accounts used by members of the IS started sharing the address of a website hosting an Android app dubbed Amaq Agency app.
The Amaq Agency is linked to the Islamic State and spread messages in support of the activities of the radical group, including the recent California shootings.
The Amaq Agency app was advertised through Telegram groups and Twitter.

Figure 9 - Amaq Agency App
"The application's primary purpose is for propaganda distribution. Using the app you are able to follow the most recent news and video clips." Ghost Security told Defense One.
Members of the IS were sharing the Alrawi.apk, a new executable that also implements "encrypted communications features although rudimentary to Telegram or other more-company created ones."
The members of groups of terrorists in many cases also use mobile application available on the market, and that implements end-to-end encryption, including popular messaging chat like Telegram or Signal.
The scenarios we are exploring demonstrate the great interest of modern terrorism in technology, the Internet is becoming a point of attraction for members of terrorist organizations and wannabe terrorists.
Another worrying aspect related to the strict link between technology and terrorism is the possibility of acquiring counterfeit documents that could be used by militants to move across the Europe.
On the internet, and in particular in the cybercriminal underground, there are many black markets where it is possible to acquire any kind of illegal product and services, including fake documents.
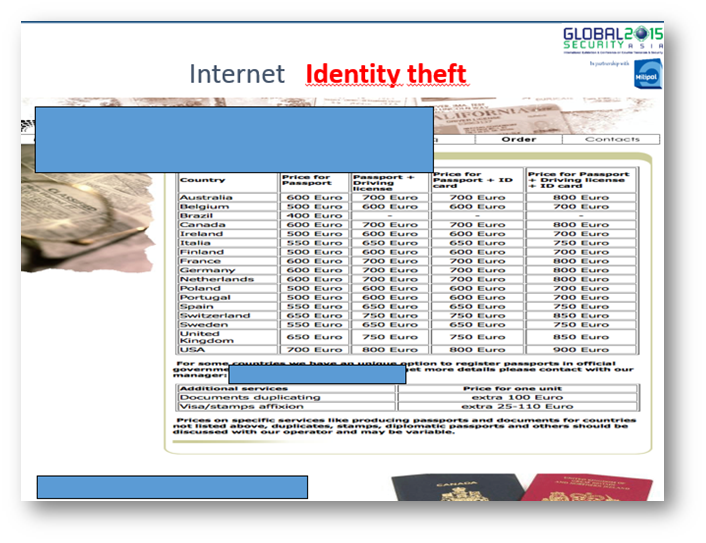
Figure 10 - Black market offering fake documents
Pseudo-anonymity offered by darknet makes the dark web an ideal environment for various activities such as:
- Propaganda
- Purchasing weapons
- Purchasing stolen card data
- Counterfeit documents
- Recruiting
- Download Mobile Apps used for secure communications
- Purchase of malicious code
- Fund-raising
- Doxing
Dealing with terrorist groups, many experts fear their hacking capabilities, part of the security community considers the ISIS a serious menace to the security of Western critical infrastructure.
The availability of tool and exploits in the criminal underground makes it easy for terrorists to hit computer networks and infrastructure worldwide. The IS has the offensive capabilities to hit its adversaries; this is the opinion of many cyber security experts, including the popular Mikko Hypponen.
"The Islamic State is the first extremist group that has a credible offensive cyber capability," said F-Secure Chief Research Officer Hyppönen, speaking last week at the Wall Street Journal's WSJDLive conference in Laguna Beach, Calif. "Clearly, this situation isn't getting better. It's getting worse."
A terrorist could attack a critical infrastructure to sabotage, or computer systems to steal sensitive data to use in other attacks.
The use of cyber weapons is a novelty in the terrorism landscape; it is a concrete risk with some advantages including
- The pre-attack phase is stealth, the organization of a cyber attack present low risks respect conventional terrorist attacks.
- The use of a zero-day vulnerability provides a real advantage to the attackers that minimize the risks of failure of operations and maximize the efficiency of the cyber weapon. Zero-day exploits could be acquired in the criminal underground and could be used in targeted attacks.
- The costs of a cyber weapon are very cheap compared to the one related a conventional weapon (explosive, weapons, vehicles for the commandos, etc.).
- The choice of cyber weapon allows the terrorists to remain under the radar until the attacks.
- Cyber weapon could have similar effects of a terrorist attack.
What are the objectives of cyber weapons?
The list is very long and includes almost every strategic infrastructure of a country such as Industrial control systems, communications networks, and defense systems.
Despite groups of terrorists haven't the time and the knowledge necessary for the design of a new cyber weapon, there is the concrete risk that threat actors in the wild can conduct a reverse engineering of the code of other nation-state malware circulating over the Internet.
The ISIS is trying to recruit hackers and experts to involve them in his hacking campaigns.
Members of the ISIS are willing to pay Indian hackers to hack into government websites and gain access to sensitive documents. The terrorists promise up to $10,000 for every successfully cyber attack, and in the Indian underground community, there are a lot of talented hackers that could offer their services to the IS.
Intelligence analysts are already observing a massive campaign through social media operated by members of the IS, over 30,000 youngsters have reportedly been in contact with members of the organization.
The Daesh is focusing its recruiting activity on the Indian hacking community; many hackers are based out of various parts of South India, including Kashmir, Maharashtra, and Rajasthan.
"Indian handlers are now creating local content to spread their propaganda in Hindi, Tamil, Gujarati, Urdu and other vernacular languages on cyberspace. In the past, Bangla has also been used to spread ISIS' hate propaganda, targeting vulnerable youths in Bangladesh and India." continues the post published by the DailyMail.
Intelligence agencies have already arrested twelve suspects in India that were in contact with terrorists in Syria and were planning an attack ahead of Republic Day.
"The work of Indian handlers is to identify people who tweet or share pro- ISIS and anti-West posts. Such users are potential ISIS sympathizers. Such people are contacted by ISIS members on social media and engaged in religious conversations. After assessing their mindset, pro-ISIS content and videos are shared. If they show interest, they are enrolled into the terror outfit." a senior officer of a central security agency.
The terrorist groups are largely investing in technology, according to footage obtained by Sky News, the members of the Islamic State have sophisticated surface-to-air missiles in their arsenal. Members of the Islamic State are reportedly developing surface-to-air missiles that can be used in attacks against airliners and military jets flying over the controlled territories.
The most disconcerting part of the revelation is related to the existence of a secret Research & Development lab in Syria that has also designed hi-tech car bombs. Journalists at Sky News obtained a video footage from the Free Syrian Army fighters that shows workshop equipped with sophisticated toolkits.
The footage provided to Sky News also shows a remote controlled car that can be used in the attacks without a driver. The video shows that the engineers of the Islamic State have designed "driver" mannequins with self-regulating thermostats. The mannequins use the thermostats to produce the heat signature of humans to deceive IR scanners used to a physical measure to protect potential target (i.e. Embassies, government offices).
Intelligence experts believe it is located in the Syrian town of Raqqa, the city considered the nerve center of the caliphate.
Let's close with a look at new trends, security experts fear the possibility of cyber attacks completely managed by isolated cells. These attacks can cause sabotage or the disclosure of sensitive information with serious repercussion on homeland security.
The terrorism is assuming even more a global connotation also thanks new technologies. Terrorism represents one of the main threats to the modern society as confirmed by the experts who gathered for the World Economic Forum 2016.
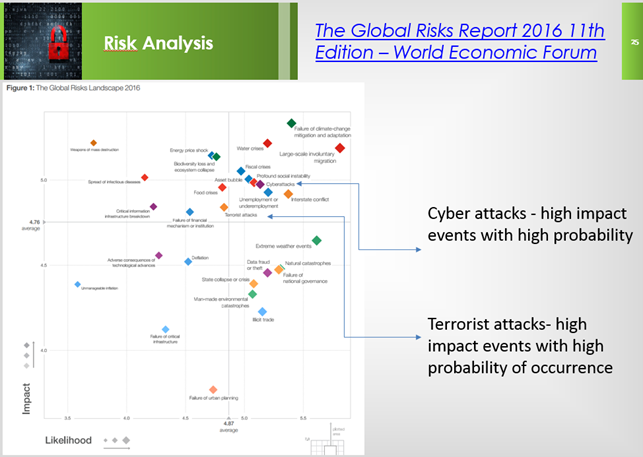
Figure 11 - The Role Of Technology In Modern Terrorism - Pierluigi Paganini

What should you learn next?
If you are interested in my presentation on the topic you can download the slides at the following link.
Slide share - role of technology in modern terriorism
Sources
Papers -Rand
Cyber crime -Security affairs
Isis Mobile - Security affairs
Isis infiltrating indian hacking community
Amaq android app - Security affairs
Kybernetiq magazine cyber - Security affairs
How Isis makes its blood sausage
Al Qaeda encryption technology