Security features and risks in Google Chrome
Today a web browser has become a very important piece of software in our daily life. It is an application that finds and displays the web pages. Be it via mobile phone or computer browser, we are using it everywhere. When you access some website through your browser, the request goes to the server and then the server provides the content of the requested page. The browser then processes the content sent by the server. The content can be written in any language such as HTML, XML, JavaScript, etc. and can load other elements like Java, Flash, etc. that are required to generate the page.
Browsers have evolved over time and hence are always in the spotlight of the attacker. Web attacks can be performed in many ways. You can be attacked via your web browser through a malicious plugin or through email clients.
In this article, we will look at some features of the Chrome browser and associated risks with those features.
Browser features and security risks
The browser uses various elements (such as JavaScript, Active X, Flash, etc.) to generate the web page. These features are usually enabled by default in the browser. This poses a huge risk because there are multiple vulnerabilities related to these elements present on the Internet.
Plugins
The plugin is the additional piece of software that is plugged into the browser to provide additional functionality. For example, Adobe Flash Player is a plugin used for online videos or games. Plugins are widely used and enable optimal functionality. Owing to wide usage, plugins are the prime target of attackers. A plugin that is not up to date can have serious vulnerabilities like buffer overflow, remote code execution, etc. In many cases, plugins are executed without the user's knowledge and hence pose a great threat to the browser and the system. Anyone can write a plugin and host it on legitimate extension galleries. It can be used as malware once downloaded into your system.
Java
Java is a programming language that can be used to develop various active content for websites. The Java applet can be used to provide interactive and rich features to the application that cannot be provided by HTML alone. JVM (Java Virtual Machine) is used to run the Java application. The applet executes within the JVM. JVM restricts the execution of the applet in a safe environment. However, some implementation of JVM has vulnerabilities that allow the applet to bypass this restriction.
In the past, there were many vulnerabilities reported in Java and it has become a target for client-side attacks. Many security researchers caution users to limit their usage of Java unless it is a business requirement.
1. Type 'chrome://plugins' into the Omnibar.
2. Look for the 'Java' plugin and click the 'Disable' link next to it.
Active X
Active X is a software developed by Microsoft and commonly used in Windows operating systems. Active X is used to enhance the browsing experience by allowing animation on the website.
The developer can give Active X controls a high-level access to computer resources, which makes them dangerous. Therefore, if the user allows Active X controls, it can compromise your system. Some legitimate-looking Active X can have bad code to steal your sensitive information.
Active X controls are commonly used by attackers to install malware, spyware, pop-up ads and can interfere with browser and system performance.
Cookies
Cookies are the files placed on your local machine to store data for specific websites. Cookies may contain Session ID, credentials for accessing the site, user preferences or any other sensitive information related to the specific website. Session cookies are deleted when the browser is closed, and the persistent cookie will remain stored in your local machine. Persistent cookies have greater risk compared with session cookies as they remain stored on the local machine. An attacker with physical access to your machine can access these cookies and obtain the sensitive information.
JavaScript
JavaScript is a programming language. It is used in dynamic web pages to provide functionalities such as form submission, validation, animation, interactivity, etc. JavaScript is embedded in HTML pages where it can interact with the page's document object module (DOM) to perform specified functions.
Features provided by JavaScript and DOM can be abused by attackers by running a malicious script on a web page. Running a malicious script can cause many issues such as stealing user cookies, redirecting the user to another website, installing malware or trojans, deleting system files, defacing the website, etc.
By default, many web browsers enable the support for scripting, which can lead to multiple vulnerabilities like cross-site scripting (XSS), Cross-site request forgery (CSRF), etc.
Browser security features
The most important step is to keep your browser up-to-date with the latest security patches. An older version of the browser can have many severe vulnerabilities that can be exploited remotely. By default, Chrome has the auto-update feature. It can automatically update to the latest version and ask for browser restart when it is done. In case it is not updating automatically, you can either:
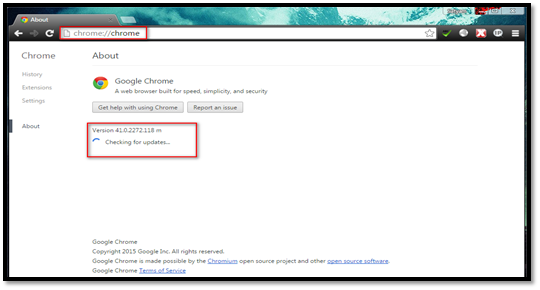
1. Navigate to Chrome menu, which is located at top right corner of the browser, and then select "About Google Chrome".
2. Or you can type "chrome://chrome" in the Omnibox and Chrome will start checking for the update.
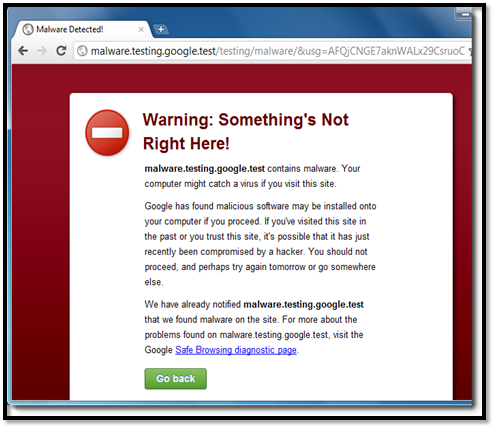
Phishing and malware are the most common and major concerns among most of Internet users. The anti-phishing feature in Chrome checks the visited website against a list of known bad websites that is stored in your computer. If the website you visited matches the list, the browser displays a warning message.
The anti-malware feature prevents user from going to malware-affected websites and downloading malicious content from them. This option is enabled by default in Chrome.
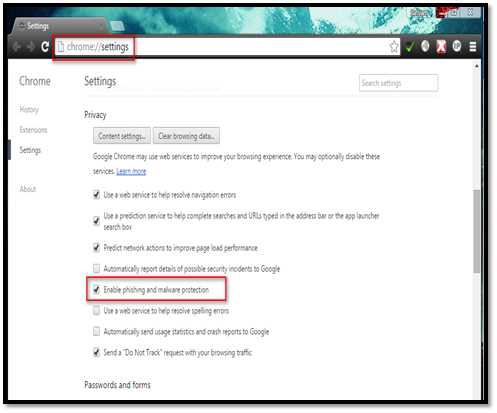
To enable these features, navigate to Settings Privacy. Select the "Enable phishing and malware protection" check box.
Sandboxing enables an additional layer of security in your browser. It is designed to provide a restricted environment around each process of the browser. In Chrome, every application or website you open in the browser is a separate and independent process. For example, if you open 4 different websites each in a different tab, then each tab corresponds to a separate process. Therefore, if one tab crashes due to some bad website having malware, virus, etc., the process in other tabs should remain unaffected and avoid further damage to your computer. Google Chrome by default comes with the sandboxing technique.
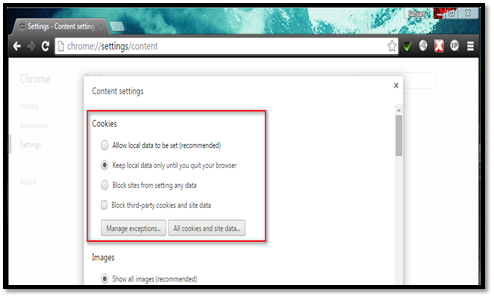
Cookie-related settings can be performed in this feature. Navigate to Settings Privacy Content settings Configure options under the "Cookies" section.
Select the "Keep local data until you quit browser" check box to automatically delete the cookie when you close the browser.
Select the "Block third party cookies and site data" check box to prevent Chrome from accepting a cookie from a third party. A third party can use this cookie to track you online.
The website uses your physical location using Chrome's geolocation features. Based on your physical location, it then shows local or area-specific advertisements to you. The "Location" feature allows you to configure your browser to instruct websites not to track your browsing data.
Navigate to Settings Privacy Content settings Configure options under "Location" section.
Select the "Ask when a site tries to track your physical location" option if you want Chrome to show a pop up asking to allow location tracking whenever a website tries to access your current location.
Select the "Do not allow any site to track your physical location" option to completely disable this location-sharing feature.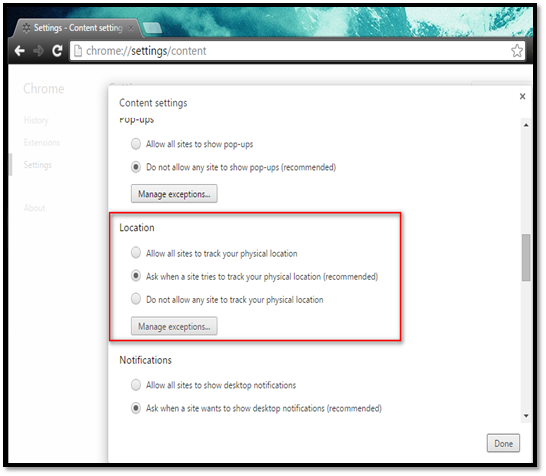
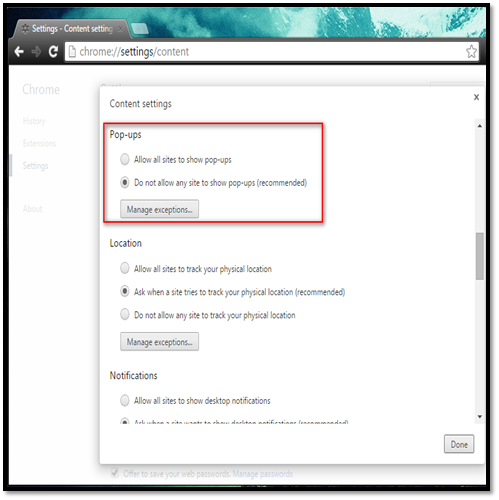
The pop-up blocker is an important security feature that prevents the web browser from opening additional web browser windows or pop-ups without the user's permission. The pop-up windows in most cases are used by websites for showing advertisements to visitors. Malicious websites can use pop-up windows to share/distribute the malicious software.
Navigate to Settings Privacy Content settings Configure options under the "pop-ups" section.
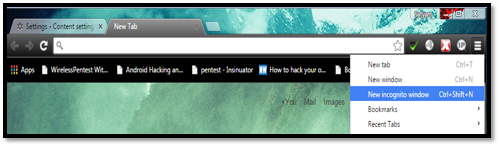
Private Browsing Mode
Keeping privacy in mind, Google has a private browsing mode called "Incognito mode". When you access any website in Incognito mode, the browser will not record any activity such as downloads, passwords, browsing history, cookies, etc. This mode is very useful when you are using a shared system through a public computer or public Wi-Fi places to access the website.
Navigate to settings and then choose "Incognito mode" to launch the private browsing mode.
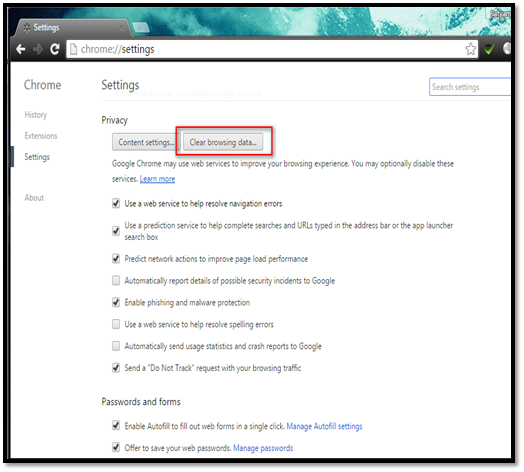
Clear Data
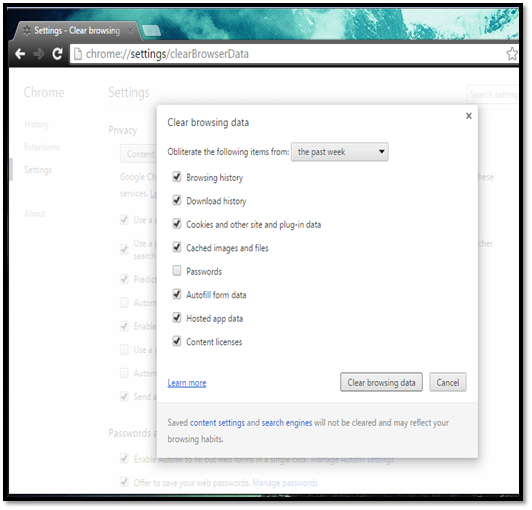
When you use the web browser, it collects the browsing data such as the website visited, cache, password, cookies, etc. to make it easy for the user to re-visit the website later. However, if an attacker gains physical access to your machine, he can easily extract all the above details. As a security best practice, the user should delete all the saved data after browsing in a public or shared computer. The "clear data" feature is used to delete all saved data from the browser.
Navigate to settings and then click the "Clear browsing data" button and select the data to be removed.
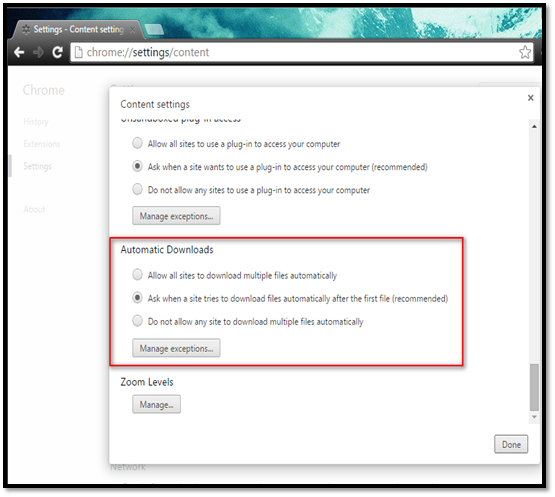
If you visit a malicious web site, it may attempt to download the malicious file on to the local system and execute it. It is better to always know what type of file you are about to download. The automatic download is the feature that allows you to configure the download settings.
Navigate to Settings Privacy Content settings Configure options under "Automatic download" section.
Select the "Ask when a site wants to download a file automatically" option.
This will show a pop up asking to confirm the file download.
Disable the plugins that have not been downloaded from trusted sources. Also, as a security best practice, disable the plugins that you are not using.
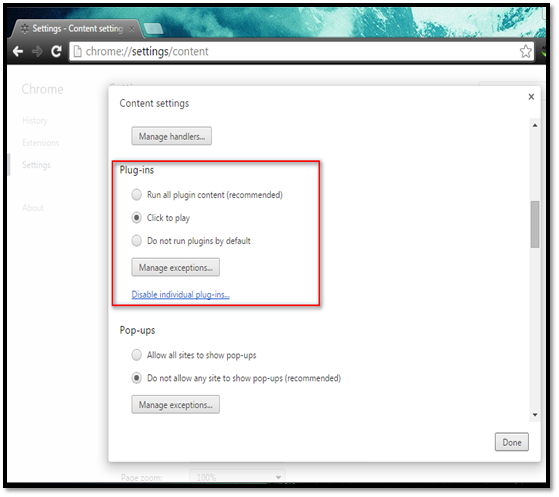
Navigate to settings Privacy Content settings Configure options under the "plugins" section.
The "click to play" option prevents all the plugins like Java, Adobe, etc. from running automatically. When you use this feature the site will ask for permission to run plugins.
You can click the "Manage exceptions…" button to allow some specific site to always run the plugins.
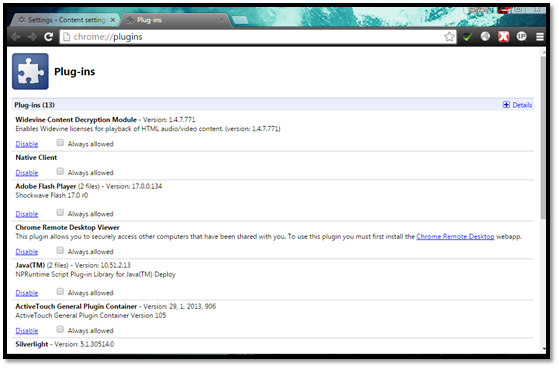
You can disable unwanted plugins by typing "chrome://plugins" in the URL and then select which plugins you want to enable/disable.
Google Chrome uses its internal sandboxing feature to prevent plugins from directly accessing the local system. In some situations, direct access is required.
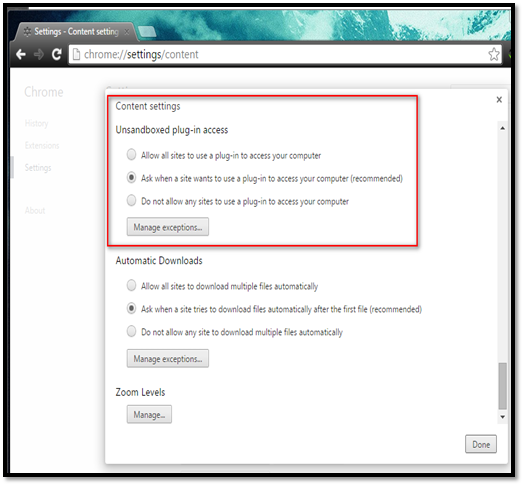
Navigate to Settings Privacy Content settings Configure options under "Unsandboxed plugin access" section.
The "Ask when a site wants to use a plugin access..." option allows Chrome to ask the user before running the plugin in the unsandboxed environment.
The "Do not allow any site to use a plugin..." is a restrictive option that allows Chrome to block all unsandboxed plugin executions.
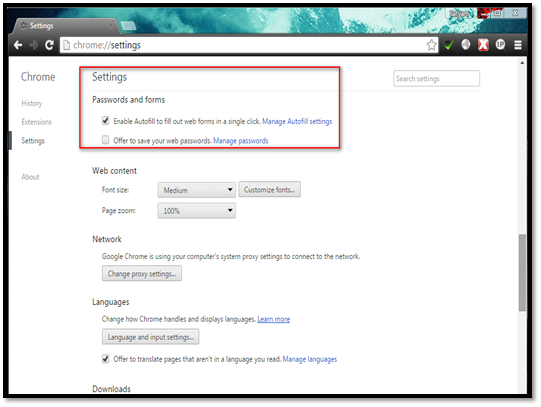
Autofill is the feature used to remember and store user data like e-mail address, phone number, credit card details, etc. so that user don't have to fill it manually again and again. It stores the user credentials also so that user doesn't have to remember the credentials for the specific website.
Though this functionality provides some ease to the user, it also raises threats.
Navigate to settings and configure the options under the "Password and forms" section.
Clear the "Offer to save your web password" check box to prevent Chrome from asking to save the credentials of websites. This is very important as malware can easily store the stored credentials.
Chrome offers an additional security layer by protecting the access to stored passwords with the machine password. This means before accessing the stored passwords, Chrome will ask for the machine password. This is a good security measure but not strong enough. An attacker with machine credentials can access the stored passwords.
Also as a security best practice, never store sensitive information like a credit card number in the browser.
You can clear the "Enable autofill to fill out …" check box to prevent the browser from saving the user data.
Security best practices to be followed for browsers
- Keep the browser updated and patched.
- Install antivirus in your local machine and keep it updated.
- Keep the operating system and application up to date.
- Download content from legitimate sources.
- Use minimal plugins and keep them updated.
- Disable unnecessary browser plugins.
- Block pop-ups.
- Use malware and phishing filters or the safe browsing feature in your browser.
- Change the default configuration of web browsers after installing.
- Avoid using the "remember my password" feature or do not save any sensitive personal information in the browser.
- Configure the setting to delete the cookies on closing the browser.
- Avoid downloading files from untrusted sources.
Conclusion
The browser allows you to connect to the World Wide Web, but it opens your system up to a variety of severe vulnerabilities and attacks. The browser can be an entry point for an attacker into your machine, hence securing your browser is a vital step. Almost every browser and operating system combination is vulnerable. Customizing the browser settings can add an additional level of protection. There are a number of steps that you can take to reduce the probability of getting compromised, all of which require some level of effort and time, and some of which may limit the usefulness of the web in some ways.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!










