Security Categories
1. Introduction
I've been a security enthusiast for years now, and currently I'm working as a security penetration tester. Over the years it has happened that I've heard about a new security method I've never encountered before. When I started doing research about the topic, it was all very interesting, but I've often spend weeks, even months grasping it all in. While studying this new exciting topic I've always come across yet newer security concepts, methods, etc. This process can go on indefinitely, but the question remains: where does it all end?
Well, it really doesn't end anywhere, since there's really too much information out there that can be learned by one individual. Usually it takes quite a few people to cover all the topics regarding information security, but even then there are still new areas none of them are aware about. That's why we really must ask ourselves a different question: What is important to me, what interests me the most, how deep should I go? The answer to those questions depend entirely on the individual and how much time he or she is willing to spend reading and learning new stuff.
In this article we'll try to introduce the most important security areas that are out there and from which we can choose when trying to learn something new. All the categories can also serve as an entry point into a security field, so we can always know where are we currently located. If we're reading an article on THN: The Hacker News and it talks about uploading a shell to a vulnerable website, how does it all fit together, is this part of some more abstract category, or should it be it's own category? We'll describe that in more detail later.
If we can remember our years in university, when we were studying comprehensive subjects, at the end we always ended up with a mindmap, which essentially covered all the concepts of the subject even though it was represented on one A4 paper. When we looked at the generated mindmap, we could always remember all the details about the outlined concepts on the mindmap, no matter how detailed they were – that is assuming that we were studying at all :).
Another great example is the following: Let's say we need to write an exploit about CWD vulnerability in EasyFTP 1.7.0.11 FTP server. There are a couple of ways we can approach such a problem, which we won't describe here. Currently we're only interested in how to categorize the problem we have. After quick examination of the vulnerability, we can categorize it as being a buffer overflow, more precisely a stack overflow. If at that point someone asks us what we're doing, we can answer in two ways. The first way is the following: I'm writing an EasyFTP exploit that can take advantage of the CWD command of the EasyFTP server version 1.7.0.11. The second way: I'm writing a stack-based exploit for some FTP server.
But the answer greatly depends on on who's asking. If we're answering to an experienced penetration tester, the first answer might be more appropriate, but if we're talking to a system admin, the second answer is better. Needless to say, if our wife is asking, we should come up with an entirely different answer.
This article should also be a great reference when trying to get into information security. It should give us a great overview of what's out there.
2. Presenting All the Categories
Over the years I've built a schematic representation of the categories I've worked with, studied, encountered, etc. I've written them down into my notebook, but now it's time to put them into digital form and introduce them to the world. If you're an experienced penetration tester or a security enthusiast then the presented categories will really be nothing new to you, but it's a great reference for other people out there.
The security categories are presented in the picture below:
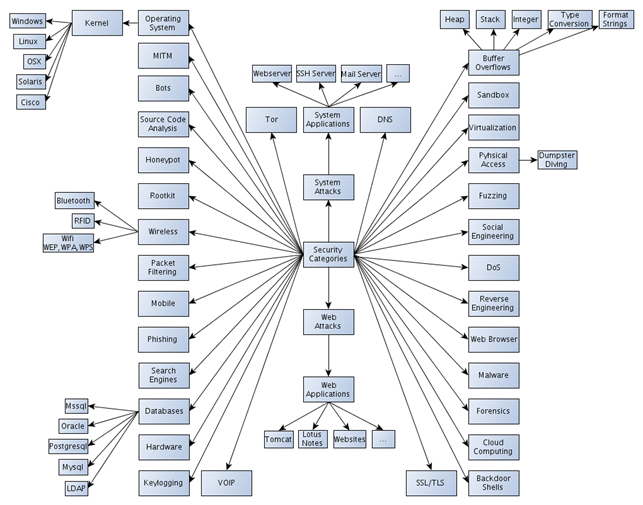
We can see that the picture is quite daunting. It contains a lot of information (maybe too much), but presents what it promises. I guess it's better to describe it very precisely. In the middle of the picture, we can see that most of the applications/programs out there can be divided into:
- Web Applications: Those are the applications can are accessible in our browser, whatever they might be. Usually, those applications are HTTP servers (like Apache, Tomcat, etc), CMS systems (like Joomla, Wordpress, Typo3, Plone, Drupal, etc), or just plain old websites.
- System Applications: Those applications usually run on our desktops, and include Microsoft Word, PDF Reader, web browser, etc.
The rest of the above picture represents different categories of the information security field. They are described in more detail in the rest of the section.
- Operating Systems – Kernel
Numerous vulnerabilities are discovered in operating system security each year.
- MITM (Man In The Middle) Attack
Is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all messages going between the two victims and inject new ones, which is straightforward in many circumstances (for example, an attacker within reception range of an unencrypted Wi-Fi wireless access point, can insert himself as a man-in-the-middle) [MITM].
- Bot
Is a software application that runs automated tasks over the Internet. Typically, a bot performs tasks that are both simple and structurally repetitive, at a much higher rate than would be possible for a human alone. The largest use of a bot is in web spidering, in which an automated script fetches, analyzes and files information from web servers [Bot].
- Source Code Analysis
Is the analysis of computer software that is performed without actually executing programs built from that software. In most cases the analysis is performed on some version of the source code and in the other cases some form of the object code. The term is usually applied to the analysis performed by an automated tool, with human analysis being called program understanding, program comprehension or code review [Source Code Analysis].
- Honeypot
Is a trap set to detect, deflect, or in some manner counteract attempts at unauthorized use of information systems. Generally it consists of a computer, data, or a network site that appears to be part of a network, but is actually isolated and monitored, and which seems to contain information or a resource of value to attackers [Honeypot].
- Rootkit
A rootkit is a stealthy type of malicious software (malware) designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer [Rootkit].
- Wireless
Is a popular technology that allows an electronic device to exchange data wirelessly (using radio waves) over a computer network, including high-speed Internet connections [Wireless].
- Packet Filtering
A packet filter can either be software-based or hardware-based and is used to help keep a network secure. Its primary objective is to control the incoming and outgoing network traffic by analyzing the data packets and determining whether it should be allowed through or not, based on a predetermined rule set [Packet Filter].
- Mobile
A mobile phone is a device that can make and receive telephone calls over a radio link whilst moving around a wide geographic area [Mobile].
- Phishing
Phishing is attempting to acquire information (and sometimes, indirectly, money) such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT administrators are commonly used to lure the unsuspecting public. Phishing emails may contain links to websites that are infected with malware [Phishing].
- Search Engine
A web search engine is designed to search for information on the World Wide Web. The search results are generally presented in a list of results often referred to as search engine results pages (SERPs). The information may consist of web pages, images, information and other types of files. Some search engines also mine data available in databases or open directories. Unlike web directories, which are maintained only by human editors, search engines also maintain real-time information by running an algorithm on a web crawler [Search Engine].
- Database
A database is an organized collection of data, today typically in digital form. The data are typically organized to model relevant aspects of reality, in a way that supports processes requiring this information [Database].
- Hardware
Is the collection of physical elements that comprise a computer system. Computer hardware refers to the physical parts or components of computer such as monitor, keyboard, hard disk, mouse, etc. Refers to objects that you can actually touch, like disks, disk drives, display screens, keyboards, printers, boards, and chips [Hardware].
- Keylogging
Is the action of tracking (or logging) the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored [Keylogging].
- VOIP
VOIP refers to the communication protocols, technologies, methodologies, and transmission techniques involved in the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet [VOIP].
- Buffer Overflow
Is an anomaly where a program, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory [Buffer Overflow].
- Sandbox
Is a security mechanism for separating running programs. It is often used to execute untested code, or untrusted programs from unverified third-parties, suppliers, untrusted users and untrusted websites. Typically it provides a tightly-controlled set of resources for guest programs to run in, such as scratch space on disk and memory. Network access, the ability to inspect the host system or read from input devices are usually disallowed or heavily restricted [Sandbox].
- Virtualization
Is the creation of a virtual version of something, such as a hardware platform, operating system (OS), storage device, or network resources [Virtualization].
- Physical Access
Refers to the ability of people to physically gain access to a computer system [Physical Access].
- Fuzzing
Is a software testing technique, often automated or semi-automated, that involves providing invalid, unexpected, or random data to the inputs of a computer program. The program is then monitored for exceptions such as crashes, or failing built-in code assertions or for finding potential memory leaks [Fuzzing].
- Social Engineering
Is the art of manipulating people into performing actions or divulging confidential information [Social Engineering].
- DoS
Is an attempt to make a machine or network resource unavailable to its intended users [DoS].
- Reverse Engineering
Is the process of analyzing a subject system to create representations of the system at a higher level of abstraction. The purposes of reverse engineering include security auditing, removal of copy protection ("cracking"), circumvention of access restrictions often present in consumer electronics, customization of embedded systems (such as engine management systems), in-house repairs or retrofits, enabling of additional features on low-cost "crippled" hardware (such as some graphics card chip-sets), or even mere satisfaction of curiosity. [Reverse Engineering].
- Web Browser
A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content. Hyperlinks present in resources enable users easily to navigate their browsers to related resources [Web Browser].
- Malware
Is a malicious software used or created by hackers to disrupt computer operation, gather sensitive information, or gain access to private computer systems [Malware].
- Forensics
Is a branch of digital forensic science pertaining to legal evidence found in computers and digital storage media. The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying, preserving, recovering, analyzing and presenting facts and opinions about the information [Forensics].
- Cloud Computing
Is the delivery of computing and storage capacity as a service to a community of end-recipients. End users access cloud-based applications through a web browser or a light-weight desktop or mobile app while the business software and user's data are stored on servers at a remote location [Cloud Computing].
- Backdoor Shell
Is a malicious piece of code that can be uploaded to a site to gain access to files stored on that site. Once it is uploaded, the hacker can use it to edit, delete, or download any files on the site, or upload their own [Backdoor Shell].
- SSL/TLS
Are cryptographic protocols that provide communication security over the Internet [SSL/TLS].
- DNS
Is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. A Domain Name Service resolves queries for these names into IP addresses for the purpose of locating computer services and devices worldwide [DNS].
- Tor
Is a system intended to enable online anonymity. Tor client software directs internet traffic through a worldwide volunteer network of servers to conceal a user's location or usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace Internet activity [Tor].
3. Conclusion
We've presented all the categories, which are by no means complete. I hope you'll try to contribute to the list, which will improve in time. The basic idea is to give context to all the articles in InfoSec Institute and other security-related websites, blogs, books, so we'll instantly be able to tell from which category a certain article originates. That should give us a quick reference what the article is about before reading further.
We should also keep in mind that each of the categories can be further divided into more specialized categories, which should also be presented as a mindmap of a particular category.