How Russia Controls the Internet
Russia and Internet Freedom
The Russian government is increasing its pressure on social media. Many experts maintain that the population is suffering a serious online censorship. The analysts have noted a surge in the use of anonymous web surfing software like Tor. According to data proposed on the Tor Metrics Portal, the number of directly connecting users from Russia passed from 80,000 in June to more than 200,000 in the last week.
It has been estimated that Russian Internet users were 68 million last winter (59% of the adult population), and despite the fact that 200,000 users represent a small fraction of the overall Russian online population, the data show a concerning situation in which Russian netizens are afraid of the monitoring of online activities by the government.
In May, the State Duma discussed a copyright protection bill, still pending, that proposes extrajudicial blacklisting of websites suspected of hosting pirated content. Experts and Internet freedom activists are accusing the Russian government of working to introduce online censorship in the country.
"They are enemies of freedom of information … But all they will achieve is an increase in the public's computer literacy," said Anton Nosik, a popular Russian blogger.
The censorship in Russia could affect the most popular social media sites, impacting millions of Internet users. It's clear that the Kremlin fears the possibility that foreign governments could destabilize the countries, or some local areas, with PSYOPs.
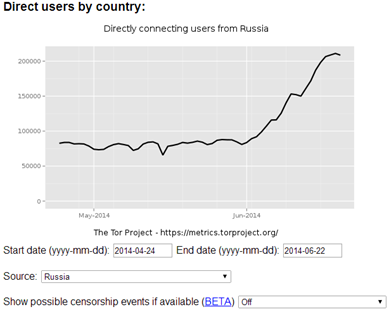
Figure - Tor Metrics - Direct users by Russia
Below is the timeline of Internet regulation activities in Russia proposed by the Moscow Time:
• 2012, November: Extrajudicial blacklisting allowed for websites promoting child pornography, suicide and illegal drugs. Data from Rublacklist.net indicates 97 percent of websites on the list committed no offense and were banned as the collateral damage of imperfect blacklisting methods.
• 2013, July: Extrajudicial blacklisting expanded to websites accused of hosting possibly pirated films. The number of Russian Tor users in the period between mid-August and mid-September 2013 rose from 25,000 to 150,000.
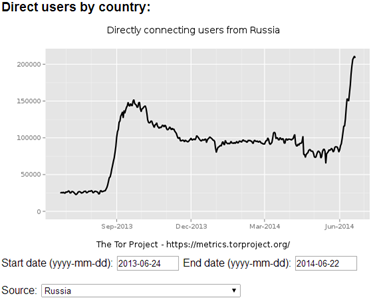
Figure - Tor Metrics Direct user by country (last 12 months)
• 2013, October: The Pirate Party of Russia, which campaigns for freedom of information, is denied official registration for the third time over its title, which, the government claimed, promotes "robbery on the high seas."
• 2014, February: Extrajudicial blacklisting expanded to websites accused of promoting riots as well as extremism, a charge frequently applied to critics of the government.
• 2014, June: Bloggers with a daily readership upward of 3,000 users are obliged by law to de-anonymize and register with the state.
On January 15th 2013, Vladimir Putin approved a decree that assigns full powers to the Federal Security Service (FSB) to "create a state system for the detection, prevention and liquidation of the effects of computer attacks on the information resources of the Russian Federation." Neither the FSB nor the Kremlin have provided further details on the government program to reinforce the security of cyber space. Russian authorities are working on the definition of an automated defense system able to mitigate incoming cyber attacks against Russian web assets inside the country and also abroad.
In November 2012, the Russian government deployed a system that is able to monitor Internet activities of millions of citizens and ban content not approved by the central government. The project will use new complex Internet-monitoring technologies to implement the "Single Register" that is able to spy on the Internet activities of Russians, officially to prevent online pedophilia. The Register is populated with requests of censorship coming from the Agency for the Supervision of Information Technology, Communications and Mass Media (The Roskomnadzor) that applies court decisions and executes orders of three government agencies: the Interior Ministry, the Federal Antidrug Agency, and the Federal Service for the Supervision of Consumer Rights and Public Welfare.
In July 2013, Vladimir Putin signed a law that contemplates also the possibility to put under judgment non only child pornography, but also online contents that express dissent against the government. The agency has established a complete control of Internet activities, exactly like many other countries, and it has in fact the power to impose to the ISP to block the indicted contents within 24 hours, according to news proposed by the media.
But how does the Register operate?
According to the article published on Wired, the government of Moscow has deployed a system which implements a DPI (deep packet inspection) technology on a nationwide scale, despite there being no official mention in the signed law. DPI is the most advanced and intrusive category of inspection tools, as it is able to analyze every single packet of the traffic, filtering for particular services or contents. Many other governments in the world have adopted it, including Iran and China, which adopted the technology to implement its Great Firewall project. The following is a passage of the declaration of the Ministry of Communications of the presence of the Deep Packet Inspection technology.
"At the end of August, under the chairmanship of Communications minister Nikolai Nikiforov, a working group was held, drawing representatives of Google, SUP Media (the owner of the Livejournal social network), and of all the other big hitters. They discussed how to ensure that the [filtering] mechanism — they used the concrete example of YouTube — how to block a specific video, without blocking YouTube as a whole. And they reached the conclusion that pleased them all," Ilya Ponomarev, a member of the State Duma and an ardent supporter of the law, declared.
Are we are talking about DPI technology? we asked.
"Yes, precisely."
Eric King, head of research at Privacy International, declared:
"No Western democracy has yet implemented a dragnet black-box DPI surveillance system due to the crushing effect it would have on free speech and privacy,"
"DPI allows the state to peer into everyone's internet traffic and read, copy or even modify emails and web pages: We now know that such techniques were deployed in pre-revolutionary Tunisia. It can also compromise critical circumvention tools, tools that help citizens evade authoritarian internet controls in countries like Iran and China."
The system is codenamed as SORM ("System for Operative Investigative Activities"). It could be used for Internet surveillance, as according to a Russian law passed in 1995, the FSB (state security organization) can monitor telephone and Internet communications.
SORM-1 system was established in 1996 to monitor telephone communications substituted by SORM-2 in July 1998 to monitor the Internet. Internet Service Providers (ISPs) must install a special device on their servers to allow the FSB to track all credit card transactions, e-mail messages and web use.
The cost of SORM equipment at the time the regulation was introduced was nearly USD 25,000, a price considered very expensive by many small and independent ISPs that decided to shut down. There was also a singular case of a small regional ISP in Volgograd, Bayard-Slaviya Communications, which tried to refuse the installation of the appliance according to the new law. As expected, the Ministry of Communications revoked the provider's license, however, when the ISP brought the question to the court, the ministry renewed its license.
An event such as the Arab Spring and the parallel growth of political activism has alerted the Russian government to the dangers of free circulation of information on social media. The imperative is monitoring everything to avoid surprises, to keep Western eyes far from "internal questions".
First Deputy Director of the FSB Sergei Smirnov declared: "New technologies are used by Western secret services to create and maintain a level of continual tension in society with serious intentions extending even to regime change…. Our elections, especially the presidential election and the situation in the preceding period, revealed the potential of the blogosphere." Smirnov stated that it was essential to develop ways of reacting adequately to the use of such technologies and confessed openly that "this has not yet happened."
There is a contradiction in the Russian approach that for years has declared to be contrary to so invasive Internet control, raising critical concerns on Chinese Internet censorship. According to the declaration of Russian intelligence, DPI technologies have been introduced a long time ago. In 2004, the security department acquired a Transtelecom system for its internal network.
Many companies sell DPI technology in Russia, such as the Canadian Sandvine, the Israeli Allot, Americans Cisco and Procera, and Chinase Huawei. Since 2013, all mobile operators in Russia have deployed a DPI:
- Procera was installed in VimpelCom.
- Huawei's DPI solutions are in use in Megafon.
-
MTS bought CISCO DPI technology.
The mobile operators motivated the acquisitions of DPI to control the use of bandwidth saturated by improper adoption of peer to peer protocols. The introduction of DPI in this case allows to suppress any undesired services, such as torrents. Also Russian ISPs have installed DPI appliances as required by law at their own expense. Minor operators have also searched for cheap solutions found in the used market of CISCO DPIs.
The situation is really worrying in my opinion. The Russian government has been demonstrated to have zero tolerance against any kind of opposition. In Russia, to express any idea against Putin's government is really dangerous. The Russian government is evaluating the possibility to regulate popular media like Facebook and Twitter in the country, and something quite similar for news aggregators including Google and Yandex.
If you interested in further data on Internet control operated by Russia, give a look to the information collected by the OpenNet Project, an initiative that collects data on worldwide Internet filtering. The organization confirms that Russia is implementing selective filtering, mainly for political and social issues.
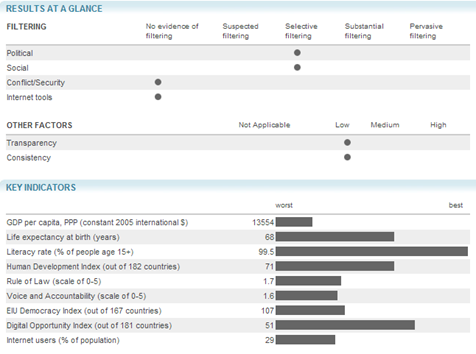
Figure - OpenNet Project - Data on Russian Internet Monitoring
System of Operative-Investigative Measures (SORM)
The System of Operative-Investigative Measures, also known as SORM, is the Russian system of lawful interception of all electronic communication. The system has been mentioned in numerous documents. In early 2013, the Bureau of Diplomatic Security at the U.S. State Department issued an official alert for US citizens wanting to assist in the Winter Olympics in Sochi, Russia.
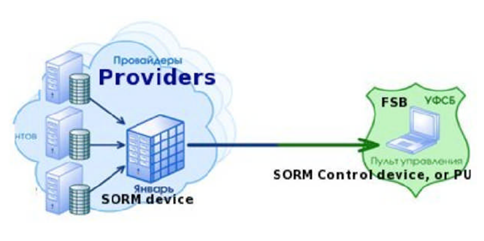
Figure - Russian Lawful Interception
The U.S. warning ends with a list of "Travel Cyber Security Best Practices," which, apart from the new technology, resembles the briefing instructions for a Cold War-era spy:
"Consider traveling with "clean" electronic devices—if you do not need the device, do not take it. Otherwise, essential devices should have all personal identifying information and sensitive files removed or 'sanitized.' Devices with wireless connection capabilities should have the Wi-Fi turned off at all times. Do not check business or personal electronic devices with your luggage at the airport. … Do not connect to local ISPs at cafes, coffee shops, hotels, airports, or other local venues. … Change all your passwords before and after your trip. … Be sure to remove the battery from your Smartphone when not in use. Technology is commercially available that can geo-track your location and activate the microphone on your phone. Assume any electronic device you take can be exploited. … If you must utilize a phone during travel consider using a 'burn phone' that uses a SIM card purchased locally with cash. Sanitize sensitive conversations as necessary," states the US warning.
The warning is clear and could give the reader an idea of the powerful capabilities of Russian Intelligence. US authorities invite Americans returning from Sochi to destroy their mobile devices. Principal Telecommunication operators and Internet Service Providers are required by law to intercept persons of interest to provide collected data to the respective government agencies.
The Federal Security Service (FSB) and any other law enforcement or intelligence agencies in the country have to receive a court order before intercepting Russian citizens, but, as reported by the World Policy Institute, Telecom providers have no right to demand that the intelligence agency show them the warrant. It is curious to note that the FSB requested to the operators and ISPs to physically install the needed SORM hardware, taking on the cost of installation and maintenance, but not having the rights to access the information they have acquired.
SORM appliances are distributed in all the country and are connected via a protected underground network to the local FSB headquarters. The SORM program is an ongoing project started by the Soviet KGB in the mid-1980s. Many technological evolutions have produced continuous updates in the lawful interception system.
The Russian government has introduced the surveillance system to improve the investigative activities of crimes and the prevention of terrorism. The Law on Systems for Operational Investigation Activity (SORM) of 1995 authorized the FSB monitoring of any telecommunication transmission. In 1999 an amendment to SORM, SORM-II, extended its efficiency on Internet traffic. SORM-II is still operating, and since 2008, thanks to an order signed by the Minister of Communications Leonid Reiman, it could be also used to monitor users' Internet activities.
SORM-II obliges ISPs to provide the FSB with statistics on all Internet traffic that passes through their servers. This is possible with the installation of SORM appliances on their servers to route all transmissions in real time through the FSB monitoring platforms. In this way, the FSB is able to track every users' transactions, e-mail communications, and online browsing.
In many sources on the web, it is referenced that SORM-3 is able to collect information from all forms of communications and analyze the huge amount of data collected. The worrying aspect of the story is that according to Russia's Supreme Court, the number of intercepted telephone conversations and email messages has doubled in six years.
"Providers must also provide the FSB with information on users' names, telephone numbers, e-mail addresses, one or more IP addresses, key words, user identification numbers, and users' ICQ number (instant messaging client), among others. Under Putin, Minister of Communications Reiman entered an order stating that the FSB officials shall not provide information to the ISPs either on users who are being investigated or regarding the decision on the grounds of which such investigations are made. Consequently, this Order offered a 'carte blanche' to the Special Services to police the activities of Internet users without supplying any further information to the provider or any other interested party," states the report from the OpenNet initiative.
Social media as a potential threat
Fearing uprisings like the Arab Spring, the Russian FSB has increased the monitoring of social media platforms. Russian intelligence is aware of the potential effect of PSYOPs.
The revolutions in the Middle East and the role played by social networks were the main topics of discussion at an informal summit of the Collective Security Treaty Organization (CSTO), a regional military alliance led by Moscow in August 2011.
In December 2011, wind of protest was blowing on Moscow, prompted by Putin's campaign to return to the presidency, and social networks assumed a critical role in the diffusion of information discrediting Putin and its collaborators. The FSB ordered suppression of the media activity of protest groups, for example, it ordered Pavel Durov, founder of the Russian social network VKontakte, to block websites of protest groups, but the man refused.
The failure in preventing protest originated on social media led the government to adopt a new platform to monitor social networks and identify participants in online discussions.
But SORM isn't the only system available for monitoring activities. The Commonwealth of Independent States (CIS) uses a special analytical search system designed by the Russian firm Analytic Business Solutions called "Semantic Archive". Semantic Archive key features are:
-
Automated collecting and processing of information obtained from heterogeneous sources, both internal (file documents, proprietary databases, e-mails) and external (online databases, news media, blogs, forums, social networks).
-
Single uniform storage for all types of collecting documents.
-
Knowledge extraction, i.e. automatic and semi-automatic extraction of objects, events and relationships from documents.
-
Maintaining of knowledge base and collecting dossiers on particular projects, investigations, partners, competitors, clients, etc.
-
Revealing of hidden or implicit relationships between objects.
-
Visual presentation of knowledge in the form of semantic network.
-
Variety of reports used to present results of research.
According to the description provided, the Semantic Archive allows the monitoring of any media archives, online sources, blogs, and social networks. It allows the composition of complex queries providing also a visual representation of the results obtained. Of course, the FSB decided that it was necessary data extracted by social media servers with similar systems, but to do this it has obliged the companies providing the web services to allow access to their data to SORM.
The operation was successful with Russian social networks Vkontakte and Odnoklassniki whose systems are hosted in Russia, but Qestern social networks including Twitter and Facebook excluded this possibility. The Kremlin is attempting to force international social media companies operating on Russian soil to cooperate with the central government in compliance with the national law framework.
In November 2012, the Russian government acquired a system for Internet filtering within the country. It was introduced the Single Register which collects the request for black list of websites by three government agencies: the Roskomnadzor, the Federal Anti-Drug Agency, and the Federal Service for the Supervision of Consumer Rights and Public Welfare. Each request must be served within 24 hours, and hundreds of websites have been already banned from the Russian Internet.
The control applied by Russian authorities is capillary. Every access point to the Internet is controlled; Internet cafes, libraries and any public place are subject to continuous inspection.
During the December's International Telecommunications Union (ITU) conference in Dubai, the Russian government proposed its design for a system for Internet monitoring. The project proposed by Russia aims to manage distribution of domain names/IP addresses from the US-based organization ICANN to an international organization such as the ITU, which could be easily influenced by Moscow.
The Russian proposal was not approved. The United States, United Kingdom, Western Europe countries, Australia and Canada didn't vote for it.
The majority of Russian Internet users are connected by broadband (40 percent), followed by dial-up (27 percent), and ADSL (23 percent), according to data provided by the OpenNet Initiative. Nearly 89 percent of the Russian telecommunications infrastructure now belongs to SvyazInvest, which is controlled by the Russian government through the Federal Property Agency. Looking to regional ISPs, it is possible to note that the principal ones (e.g. Central Telecommunication Company, North-West Tele-com, VolgaTelecom, Southern Telecom, Uralsvyazinform, Sibirtelecom, Dalsvyaz, and Central Telegraph) are SvyazInvest's subsidiaries.
Also the popular Rostelecom telecommunications operator and ISP are controlled by SvyazInvest for 51 percent of total shares.
The experts at Recorded Future have analyzed the SORM manufacturers with their platform and they identified several equipment suppliers from different countries, including Cisco Systems (US), Juniper Networks (US), Huawei (China) and Alcatel-Lucent (France).
Further evidence of the extension of the SORM system was observed in the wake of the Crimea's occupation by Russian supporter groups and claimed cyber attacks on the Ukrainian telecommunications systems.
The control over Ukrainian telecommunication systems was also possible thanks to the control of SORM equipment installed by the Ukrainian government for lawful interception activities.
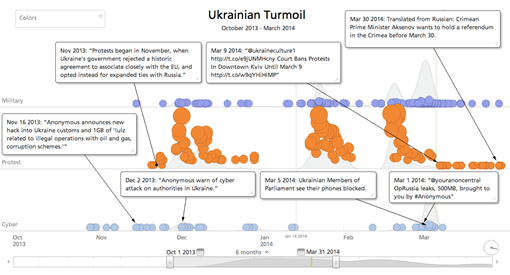
Figure - RecordedFuture Analysis Russian Timeline
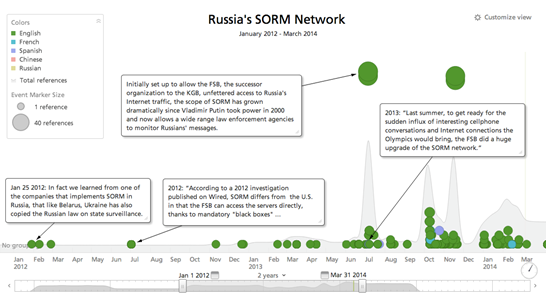
Figure - RecordedFuture SORM Timeline
Several former Soviet States, including Belarus, Kazakhstan, Uzbekistan and Ukraine have installed SORM devices. In particular, the system installed in Ukraine is considered the most advanced because it also implements a kill switch system for the target's communication channels. In April 2011, the company Iskratel announced its SORM architecture was tested successfully under the new requirements and had been approved by the SBU.
Sochi Olympic Games
Just a few weeks before the Sochi Olympics, NBC News revealed that attendees at the event were being hacked just before arriving in Sochi. Intelligence agencies of all participating governments were worried about the possibility of a terrorist attack or a cyber attack against the organization and its assets. The event represented a great occasion for bad actors which could benefit from the media attention to run clamorous cyber attacks.
The reporter Richard Engel demonstrated the efficiency of the Russian surveillance system with the support of a cyber security expert. They configured two computers to verify how quickly the device would be attacked when accessing Russian networks. The discovery was predictable: when the reporter and his collaborator went to a cafe to access the network, they were immediately attacked.
"Before we even finished our coffee" the bad actors had hit, downloading malware and "stealing my information and giving hackers the option to tap or even record my phone calls … less than 1 minute [for hackers] to pounce, and in less than 24 hours, they had broken into both of my computers," Engel said.
As the journalist explained, it was enough to go online to be a victim of the attack. The Kaspersky Lab, which was in charge to support the Sochi Olympic Committee for providing computer security, confirmed that every entity is subject to attack.
The Russian authorities, through the control of the communication channels, are able to inoculate any kind of malicious code which could be used to track individuals that accessed public and mobile telecommunications. Every single bit transmitted via phone and Internet is analyzed by the Russian System for Operational-Investigative Activities, according to the U.S. State Department's Overseas Security Advisory.
"OSAC constituents traveling to Sochi should be aware that the Russian System for Operational--Investigative Activities (SORM) lawfully enables authorities to monitor, record, analyze, and retain all data that traverses Russian networks. Through SORM technologies, Russian authorities have access to any information transmitted via telephone and Internet networks, including all emails, telephone calls, Internet browsing sessions, text messages, and fax transmissions. By Russian law, all telecommunications companies and Internet Service Providers (ISPs) are required to install SORM devices on their networks. These devices allow for remote access and transmission of information to the Russian Federal Security Service (FSB) offices. Telecommunications providers are denied access to the surveillance devices and, therefore, have no knowledge of any accessed or intercepted communications.
"Although the FSB technically requires a court order to intercept communications, there is no requirement to show it to anyone outside the agency. SORM is enabled throughout Russia and is undergoing technological upgrades and modernization. Since 2010, particular attention has been paid to Sochi in preparation for the Olympics. The system in Sochi is capable of capturing telephone (including mobile phone) communications; intercepting Internet (including wireless/Wi-Fi) traffic; and collecting and storing all user information and data (including actual recordings and locations). Deep packet inspection will allow Russian authorities to track users by filtering data for the use of particular words or phrases mentioned in emails, web chats, and on social media."
The Sochi Olympic Games have provided evidence of the complex monitoring machine managed by the Russian Intelligence. The reports issued by other intelligence agencies and the information provided by independent journalists lead to speculation of a powerful structure, comparable to the US one, used for Internet monitoring.
Don't forget that the Russian government is also considered one of most dangerous entities in cyber space due to its cyber capabilities. Many experts have attributed to the Russians cyber espionage campaigns like the SNAKE, which allowed a large-scale espionage operation.
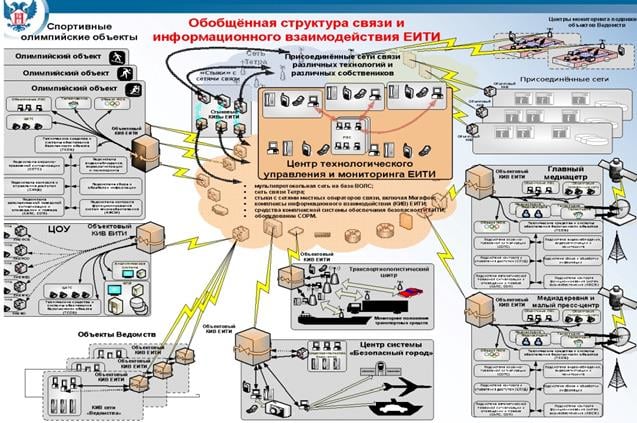
Figure - Sochi infrastructure
Conclusions
The Russian SORM surveillance systems is a worrying reality, and analyzing the data proposed, there are some reflections that raise serious questions about its final use:
- Technology used by the Russian government is very advanced. It is a mix of best surveillance devices provided by principal suppliers of foreign countries.
- From a legal perspective, SORM is far more flexible and intrusive than the Western surveillance systems. It is enough to add an entry for a subject of interest in the Register to allow monitoring of individuals without a time limit.
-
SORM is deployed in many other former Soviet countries. This could advantage Russian Intelligence in the extension of their lawful interception activities.
SORM, like any other surveillance system, is considered by governments a necessary instrument to ensure homeland security, but we cannot ignore their abuse, a circumstance that is also very frequent in countries like Russia.
I decided to write about SORM because of the numerous questions I receive daily, but it is important to remark that many other countries have deployed similar systems and operate a more aggressive policy against any form of dissent.
Unfortunately, in many countries, it is not possible to express an opinion if contrary to the central government. Millions of people every day risk their life for a blog post or for participation in a discussion on social media.
References
http://www.themoscowtimes.com/article/502169.html
http://en.itar-tass.com/economy/736804
http://securityaffairs.co/wordpress/22008/intelligence/sochi-visitors-hacked.html
http://leaksource.info/2013/10/06/russia-to-monitor-all-communications-at-sochi-winter-olympics-sorm-system-is-prism-on-steroids/
https://www.recordedfuture.com/russia-ukraine-cyber-front/
http://www.wired.com/2012/12/russias-hand/all/
https://www.us-cert.gov/ncas/tips/ST14-001
http://www.businessweek.com/articles/2014-05-01/russia-moves-toward-china-style-internet-censorship
http://www.worldpolicy.org/journal/fall2013/Russia-surveillance
http://www.anbr.ru/en/products/semarchive/
http://themoscownews.com/russia/20130617/191621273.html

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
https://www.privacyinternational.org/reports/russia/ii-surveillance-policy










