Notes On Biometric Template Security
In this article I am going to tell you about biometric template security and current technologies in which researchers are working to improve biometric template security. But this won't be a normal, traditional article of mine. I am going to write this article in question/answer format. Before reading this article you should already have a basic introduction to biometrics and what types of roles they play in a big enterprise.
Introduction to Biometrics: en.wikipedia.org/wiki/Biometrics
Question 1: Assume a company's staff has multiple identities associated with its different job roles. Discuss current technologies that can be used in that context to satisfy their requirements. The company already tried the LDAP/X.500 directory service. What is an alternative to that?
Answer 1:
As mentioned in the case study, a company used the LDAP/X.500 directory service. Before talking about alternatives, we need to understand what our basic requirements are. Here there are two.
1. Authentication (Control Access)
2. Authorization
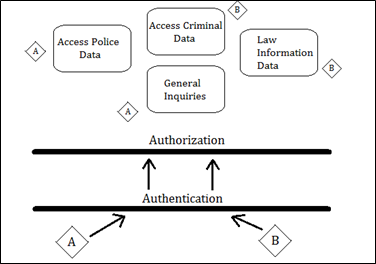
Figure : Workstation Level
Authentication means single access to the system. After entering into the system, what resources will A and B use will be dependent upon authorization. It will allocate permissions of A and B to use their resources only.
Novell eDirectory: It is compatible with X.500 directory services. It enables and allows central management of resources among multiple servers and computers within the company. It uses dynamic right inheritances. It provides a single login for accessing network resources. It also provides a single point of administration. If company sets up this mechanism into their system, then it will provide them an LDAP-based backup of their system with data encryption. It has many other features which will provide a company with better authentication, authorization and centralized management [18].
Oracle Directory Services: It provides better scalability and performance compared to Novell eDirectory. It also provides multi-level security within the system. If a company sets up this technology, then they will use a Web-based monitoring console along with the administration. It has also all those same features and benefits as Novell directory services such as proxy, synchronization, virtualization and centralized management [3].
RSA Authentication Manager: It is 2FA authentication software which can manage security tokens, multiple applications, users and resources across the networks. It centrally manages authentication policies for the whole enterprise network. It can provide flexibility, authentication and scalability. It has been said that RSA systems are more secure, easy to manage and have more features than Oracle Directory Services and Novell eDirectory [1].
Among many other technologies, one of the best which suits the requirement of the company is the Steria Biometric Data Capture System (BDCS). Steria has created BDCS for UK ministry of defense. It uses fingerprint and iris recognition system to check if the identity is valid or invalid. Not only this, but also it uses multiple biometric criteria to check and guarantee real identity. Steria focuses on security, enterprise network management, infrastructure services and system integration. Steria provides a solution according to business requirements. So considering the company (which is a defense department), it provides defense logistics, defense and shared business services, and a secure messaging service within the infrastructure of biometric identity management for staff of the company.
As mentioned in the question, let's assume the company's staff has different job roles for each one of them. Let's suppose one of the staff officers is in the Information Retrieval and Sharing Department. So she/he can use Steria's secure electronic messaging service. If one of the members is involved with the Administration Department and has a responsibility of assigning authorization to each staff or member of the company, she/he can use Steria's application management & development and centralized management features for that. So these are the current technologies which can be used as an alternative to LDAP/X.500 DirX for company. One of the best suited is Steria BDCS [2].
Question 2: Assume that the company wants to strengthen user authentication at the workstation level. What role might biometric techniques play? Critically review the role of TWO named biometric techniques. You should ensure that you fully address the role of leading edge solutions (such as template-free biometric technologies) in your answer.
Answer 2:
Here stronger authentication means that biometric authentication replaces standard authentication techniques such as passwords, smart cards and many of those traditional options. Biometrics authentication strongly binds an individual to a specific event or an action. If we place a quality biometric system over there, then it plays two important roles:
Other technologies like passwords and smartcards rely on something that an individual possesses. That can be tampered, modified or stolen. Here biometrics play an important role by binding a user's physical characteristics strongly with him/her. That characteristic does not need to be remembered, shared or written down by them. That is why it plays an essential role in stronger authentication. Another important role of biometrics at the workstation level is full automation. It does not require physical monitoring and regular updates. It reduces the time complexity by providing better security at lower cost and pretty good convenience as well.
Template-free biometrics[8] are the latest invention in biometrics. In standard biometrics we collect the value of the subject and make comparison with a stored value of a database. Here it doesn't do a comparison of collecting values. It does a mathematical analysis and generates a key. And it does a comparison of keys [21].
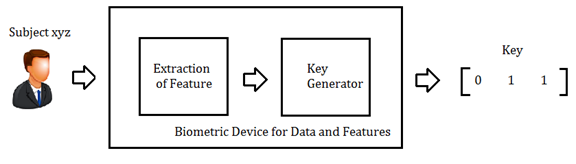
Figure 2: General Biometric Authentication Process
There are two technologies which fully address the leading edge solutions.
-
Cancelable Iris code: This approach is not a retina scan or identical to it. It is performed on iris muscles where the retina utilizes unique blood vessel patterns. It does a mathematical analysis of random iris patterns[4]. It is a very secure method for authentication because iris textures are very complex, unique and they remain as it is throughout life. It is a template-free biometric as it does enrollment and verification by the key generation [12].
US soldiers used IRIS scan biometric technique to collect the data of local Afghan civilians for future intelligence[11].

Figure 3: US army authenticating Afghan civilians using iris recognition biometric technique
The figure below shows the process of the iris recognition technique.
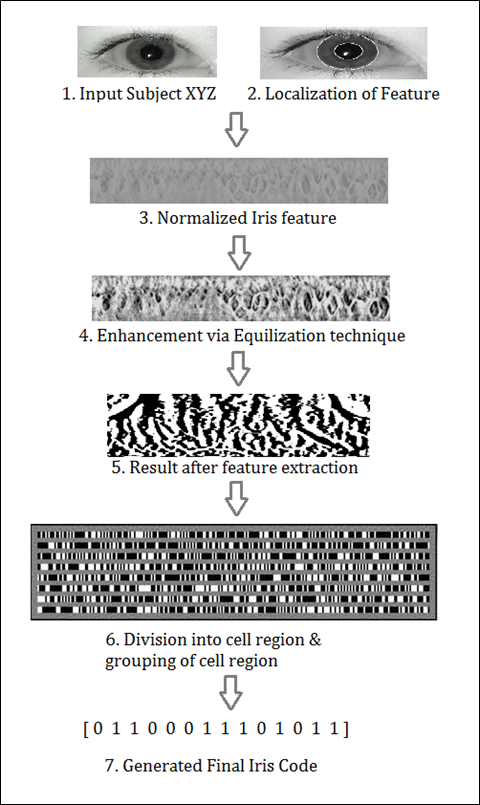
Figure 4: Iris recognition process step by step
-
Palm Vein Technology: This technique is effective even if an individual has registered his profile in childhood. It can be still recognized as he/she grows. The biometric device uses blood vessel patterns as a personal identifier factor for individuals. No two people in the world share the same palm vein pattern. The process of palm vein technology can be defined as shown in the picture[16].
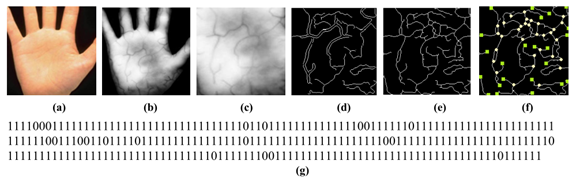
Figure 5: Palm vein technology authentication process [14]
There are some emerging technologies in biometrics, such as:
But as we are talking about technology which can be implemented at the workstation level for stronger authentication, these technologies are hard to implement and practice in everyday life at the work station level by the administrators and the staff who are going to use them[10].
Not only this, but a company can also deploy two technologies together, such as fingerprint and palm vein authentication as shown in the figure. Fujitsu company has created the world's first personal authentication system by combining two biometric authentication techniques in one device[6].

Figure 6: Fujitsu's Multibiometric system
Question 3: Distinguish between a biological identity and a digital identity. Illustrate your answer with specific reference to: a member of any police department who is working on ground duty and the other member of the police department who is working in a computer crime department (office duty - desk job). How can biometrics play different roles for these two different members of staff, and what is the role of the X.509 digital certificate?
Answer 3:
Biological identity refers to a physical feature of a particular person which can be useful to authenticate himself/herself later on. Biometric authentication uses these parts of the human body in order to authenticate them. These biological identities cannot be changed by time. Different biological identities are facial recognition, voice recognition, retinal scan, iris scan, fingerprint scan & palm vein technology. ]
In contrast, digital identity is the different tokens which can be passwords, PINs & credit card, etc. For the member of staff working in computer crime unit, a biological identity is the best suitable option compared to digital, as they will have an access to a ton of personal records of company staff, criminals and much more. So it is a must to provide stronger authentication for these people.
However, normal police have to work in the field area where they might have to engage with criminals and other things like riots. So if we are assigning their biological identity, it might fail in the case when those body parts get damaged. For example, if a company assigned one fingerprint identity to a police officer on some day and the next day he engaged with the riots in that city and his finger got burned in that (see below figure), the company would have to assign another new identity for that, and it goes on and on. So it's good to assign a digital identity which is very reliable and cost effective, as the number of normal police officers are more than the people working in a computer crime unit[5].

Figure 7: Burned Fingers – Helpless in fingerprint authentication
X.509 digital certificates play a vital role in a biometric authentication system. Generally this technique is used for the security of the template. Now this certificate can be verified using the biometric technology. It not only provides a certificate, but but also provides a request of that certificate along with verification. Here a company might place a biometric system [20].
Now it is very important to secure the templates stored in the database of that system. Unlike Web browsers, we also use a digital certificate here named X.509 to provide the encryption of the template security. Here is the list of the system vulnerabilities which might be the biggest risk for company if they are not implementing x. 509 digital certificates[9].
To protect against all these vulnerabilities, a X.509 certificate is required, especially in such a sensitive area of work. If a company implements this technique in their biometric system, it can provide authentication access control using an EV Certificate.
Question 4: Secure messaging within the company is critical. As an example, client-server messaging involves the secure transmission of encrypted information between sender and receiver. Critically review the use of PKI (Public Key Infrastructures) in this context. Is PKI unbreakable if properly installed and operated? Should the police "trust" cryptographic techniques (such as RSA) that are used as an integral part of PKI?
Answer 4:
The client server messaging system is really important a company where there is a high possibility of a spoofing attack in order to gain personal information and records or to destroy them. There are a number of attacks and lots of talks on the Internet about why cyber criminals want this type of juicy information. Against that, PKI provides authenticity, confidentiality and integrity. Encryption provides mathematical encoding of the data exchanged by client and server within the company in order to make it an unreadable format to ensure privacy. Authentication identifies the entity that can be any company staff[18].
-
Is the electronic identity of individual.
-
Is issued by the "TRUSTED" third party.
-
Cannot be tampered with if installed and operated "Properly"
-
Can be used to trace back to the identity holder.
-
Which holds an expiry date.
-
Can be submitted to someone for validation/authentication.
Due to these attacks and some breaches, a company should not trust PKI unless they install and operate it themselves using latest encryption algorithms, longer key size and advance hashing techniques. The company should create a self-signed digital certificate by considering all three major components in that. It is the best way to secure themselves up to 99% because security is just an "Illusion"[17].
Note: I have tried my best to crack these questions based on biometrics. If you have any better answer than these, then you can kindly give your suggestion and ideas to me via email, which is chintangurjar@outlook.com.
References
-
RSA Authentication Manager. (2013) EMC Corporation.
-
A Steria Capability Overview Partnering with agility in Defence. (2013) .
-
Oracle Directory Server Enterprise Edition. (2012) Oracle and/or its affiliates.
-
Iris Recognition. (2006) National Science and technology council.
-
Biometric person recognition. Available at: https://www.idiap.ch/scientific-research/themes/biometric-person-recognition .
-
Fujitsu (2011) Fujitsu develops world's first personal authentication technology to integrate palm vein and fingerprint authentication. Available at: http://www.fujitsu.com/global/news/pr/archives/month/2011/20110601-01.html (Accessed: 1 June 2011).
-
Anika, P. & Christoph. B. (2012) Ear Biometrics: A Survey of Detection,Feature Extraction and RecognitionMethods.
-
Anil, J., Karthik, N. & Abhishek, N. (2008) Biometric Template Security.
-
Coronado-García, L.C., Banco, D., & Pérez-Leguízamo, C. An Autonomous Decentralized Public Key Infrastructure. Tokyo & Hiroshima: Autonomous Decentralized Systems (ISADS).
-
Debnath, B., Rahul, R., Poulami, D., Tai-Hoon, K. & SamirKumar, B. (2009) Biometric Authentication Techniques and its Future Possibilities. IEEE.
-
John, B. (27 October 2010) US army amasses biometric data in afghanistan. Available at: http://www.theguardian.com/world/2010/oct/27/us-army-biometric-data-afghanistan .
-
John, D. (2007) New Methods in Iris Recognition. IEEE.
-
Lee, M. Brainwaves as a biometric parameter for Unique identification and authentication. Oak Ridge National Laboratory.
-
Leila, M. & Andrzej, D. Palm Vein Recognition with Local Binary Patterns and Local Derivative Patterns. Swiss Federal Institude of Technology Lausanne (EPFL).
-
Liang, W., Hauzhong, W., and Teiniu, T. & Weiming, H. Fuision of static and dynamic body biometrics for gait recognition.
-
Prasanalakshmi, B. & Kannammal, A. (2010) A Secure Cryptosystem for Pam Vein Biometrics. Singapore: .
-
Pratik, S. & Shawn, F. (2013) Attack on SSL. iSEC Partners.
-
Steffen, K. (2007) PKI auto-enrollment for novell eDirectory. Available at: http://www.novell.com/coolsolutions/appnote/18931.html .
-
Stephen, A., John, M., & Yun, S. (2007) Finger Force Direction Recognition by Principal Component Analysis of Fingernail Coloration Pattern. University of Utah.
-
Sunghyuck, H. & Sunho, L. On Biometric Enabled X.509 Certificate. Texas Tech University.
-
Weiguo, S., Gareth, H., Michael, F. & Farzin, D. (2008) Template-Free Biometric-Key Generation by Means of Fuzzy Genetic Clustering. IEEE.
-
Zahanna, K. Biometric Person Authentication: Odor. Lappeenranta University of Technology.











