Modern Online Banking Cyber Crime
Introduction
In recent years, cyber crime has grown by leaps and bounds. Cyber crime revenue grew to levels comparable to that of a state, and major security analysts agree that it'll experience sustained growth in the coming years. In this post, I'll analyze the impact of organized cyber crime on online banking services. I'll introduce primary methods of attacks used by hackers, and statistics related to each technique.
Methods of attack are becoming even more sophisticated with the passage of time. Online banking has existed since the 1980s. Few cases of fraud have been reported until 2004. That means that the escalation of attacks is relatively recent, and was concentrated in the last decade.
The improvement of online banking system, and its increased use by consumers worldwide has made this service a privileged target for cyber criminals.
What are the main methods used by cyber crime, and how they have evolved over the years?
We will analyze the most insidious cyber threats to online banking services, including phishing attacks, malware-based attacks and DDoS.
Phishing
The number of phishing attacks against banking systems is constantly growing. Practically every sector of society is targeted by cyber criminals with various techniques. Phishing attacks make large use of social engineering techniques to fool the user and steal sensitive information and banking account credentials.
In a typical phishing scheme, spoofed emails lead users to visit infected websites designed to appear as legitimate ones. The websites are designed to coax customers to divulge financial data, such as account credentials, social security numbers and credit card numbers.
In the classic attack scheme, fraudsters send e-mails or advertisements to the victims with content that looks like they were sent by a bank or by a credit card company. The emails request victims to click on a link to go to a website that replicates a bank's website.
The malicious email could contain a link to the fake website or could include an attachment that once opened, involves exactly the same task. Phishing attacks use social engineering techniques mixed with technical tricks to fool the user and steal sensitive information and banking account credentials. Phishing messages usually take the form of fake notifications from banks, providers, e-payment systems and other organizations. They request the user to submit sensitive information such as passwords, credit card numbers and bank account details
In literature, there are several variants of phishing, many of them involve the use of malware specifically designed to steal credentials from victims while hiding evidence of an attack.
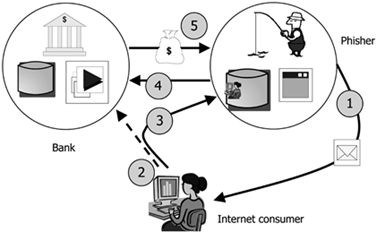
Figure - Phishing attack
A report issued by McAfee on phishing activities detected in Q2 2013, companies from the United States are the most targeted, suffering 80% of all attacks. A recent survey conducted by Kaspersky revealed that about 37% of all banks were affected by phishing attacks at least once over the previous 12 months.
Phishing attacks hit almost every sector, predominantly banking, e-payment systems and e-auctions. According to Kaspersky Labs, nearly 20.64% of all phishing threats registered between May 2012 and April 2013 were aimed at accounts of banks and other financial organizations worldwide.
Cyber crime involves an increasingly sophisticated phishing attacks. The last edition of the APWG Global Phishing Survey report revealed that attackers increasingly target shared web hosting servers for use in fraudulent activities such as mass phishing attacks. Phishers are concentrating their efforts to break into hosting providers with unprecedented success and abusing of their resources to conduct large scale phishing attacks.
The APWG Global Phishing Survey report states that the number of phishing attacks that targeted shared web hosting represented 47% of overall phishing attacks. The hackers compromise the servers and update their configuration so that phishing pages are displayed from a particular subdirectory of each domain hosted on the machine. Compromising a single shared hosting server, it's possible to exploit hundreds or even thousands of websites at a time for the attacks.
Prevention is better than cure
Despite the simplicity of the schema implemented, phishing attacks are still very aggressive and represent a serious problem for the banking system. The following are a few good practices to avoid the insidious threat:
- Request confirmation for personal or financial information with high urgency.
- Request quick action when users are threatened with frightening information.
- Take care with email and other online communication from unknown senders.
- Verify online accounts regularly to ensure that no unauthorized transactions have been made.
- Never divulge personal information via phone or on insecure websites (TCP/IP port 80.)
- Don't click on links, download files, or open email attachments from unknown senders.
- Beware of pop-ups. Never enter personal information in a pop-up screen, or click on it.
Watering hole
"Watering hole" attacks are considered an evolution of spear phishing attacks. They consist of injecting malicious code onto the public web pages of a website that that a small group of people usually visit.
In a "watering hole" attack scenario, the attackers wait for victims to visit the compromised site instead of inviting them with phishing messages. The efficiency of the method could be increased with exploitation of zero-day vulnerabilities in many large-use software programs such as Internet Explorer or Adobe Flash Player.
Cyber criminals could easily compromise an improperly configured or updated website using one of the numerous exploit kits available on the black market. Usually attackers hack the target site months before they actually use it for an attack.
The methods are very efficient. It's very difficult to locate a compromised website. "Watering hole" is a considerably surgical attack that allows hackers to hit only specific community, comparitively, classic phishing is less noisy.
"Targeting a specific website is much more difficult than merely locating websites that contain a vulnerability. The attacker has to research and probe for a weakness on the chosen website. Indeed, in watering hole attacks, the attackers may compromise. Once compromised, the attackers periodically connect to the website to ensure that they still have access…" Symantec
One of the most interesting cases of "watering hole" attacks against a financial institution was discovered in late 2012 by RSA's FirstWatch research team.
The campaign was called "VOHO attack," and compromised a regional bank in Massachusetts using the tactic of crafting a "watering hole." The majority of the redirection activity occurred because of JavaScript elements on two specific websites, one of a regional bank in Massachusetts and the other a local government serving Washington DC suburbs:
- hxxp://www.xxxxxxxxtrust.com
- hxxp://xxxxxxcountymd.gov
Despite that, it's unknown if this method was also used to compromise the "watering hole" sites. Files found on one of the compromised websites indicate that the server was likely compromised with a remote buffer overflow (CVE-2008-3869/CVE-2008-3870) against the server's sadmind daemon, giving the attacker the ability to establish a remote shell.
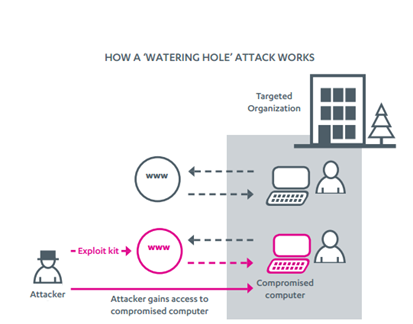
Figure - Watering Hole attack
Another famous "watering hole" attack against the banking sector was observed in March 2013 when several South Korean banks were hit by a widespread attack that wiped data and shut down systems. Internet banking servers went down causing an interruption of their services, including online banking.
Pharming and Credit Card Redirection
Pharming occurs when attackers are able to hijack a bank's URL so that when users try to access their bank's website, they get redirected to a fake site that looks like the real thing.
The term "pharming" is a neologism based on the words "farming" and "phishing." Despite that it's difficult to carry out, it's technically possible with following techniques:
- DNS Cache Poisoning- DNS servers are deployed in an organization's network to improve resolution response performance by caching previously obtained query results. Poisoning attacks against a DNS server are made by exploiting a vulnerability in DNS software. That causes the server to incorrectly validate DNS responses that ensure that they're from an authoritative source. The server will end up caching incorrect entries locally, and serve them to other users that make the same request. Victims of a banking website could be redirected to a server managed by criminals who could use it to serve malware, or to induce bank customers to provide their credentials to a copy of a legitimate website. If an attacker spoofs an IP address; DNS entries for a bank website on a given DNS server, replacing them with the IP address of a server they control, makes an attacker able to hijack customers.
-
Hosts File Modification- The HOSTS file maps domain names to IP addresses, entries in the file override DNS entries maintained by the ISP. Malware authors are increasingly using the HOSTS file to redirect users on website they manage.
Credit card redirection is new technique we're seeing being used on compromised e-commerce websites to steal credit and debit card information, by compromising legitimate web services (e.g. legitimate shopping websites.)
Security experts note that websites implementing e-commerce services are under attack, the most hit open source e-commerce system is Magento. In one case observed, the file used for payment handling was altered to replace every occurrence of paymentexpress.com for paymentiexpress.com, that's a domain managed by cyber criminals.
Credit cards are valuable in the underground market. An attacker modifies the flow of the payment process, so that instead of just processing the card, they redirect all payment details to a domain they manage, so they can steal card details.
The user that accesses the compromised e-commerce site is stealthily redirected to a well designed phishing site, so that the website could acquire card information, and send it back to the attackers.
Redirection is possible also by modifying the credit card processing file, giving the criminals access to all transaction data, including credit card details (name, address, CC and CVV.)
"The attackers modify the flow of the payment process so that instead of just processing the card, they redirect all payment details to a domain they own so they can steal the card details."
Malware based-attacks
Malware based attacks are among the most dangerous cyber threats related to online banking services. The number of families of malicious code specifically designed for financial attacks are constantly increasing. Some of the most popular banking malware are Zeus, Carberp, Spyeye, Tinba and the recent KINS. But surely, the first three agents are considered to be the most by the security community. Zeus is the oldest of them. Numerous variants were detected during the last five years, and they have been often used to commit cyber fraud on a large scale. The first version of the Zeus trojan was detected in July 2007, when it was used to steal information from the United States Department of Transportation.
Almost every banking trojan presents a group of shared capabilities, including backdoor and credential stealing features, and form grabbing. The majority of malware use has methods of attacking the "Man In The Browser."
Man In The Browser
Financial service professionals consider "Man In The Browser" to be the greatest threat to online banking and cybercrime increases, due to its efficiency. In the classic MITB schema, attackers integrate social engineering methods with the use of malware that infects the browser of the victim's client machine. It appears in the form of a BHO (Browser Helper Object), Active-X control, browser extension, add-on, plugin, or API–hooking. "Man In The Browser" attacks are based on the presence of proxy malware that infects the user's browser, exploiting its vulnerabilities on the victim's machine. The malicious code resides in the browser and it's able to modify the content of a banking transaction or to conduct operations for victims in a completely covert fashion. The agent also hides transactions from victims, altering the content presented to the browser with injection techniques. It's important to state that neither the bank nor the user can detect the attack. That's despite when a bank has implemented a multifactor authentication process, CAPTCHA, or any other forms of challenge response authentication.
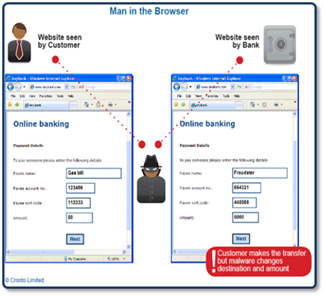
Figure - MITB
Zeus, Carberp, Sinowal, and Clampi all have built-in MITB capabilities. So, it's important to distinguish which are efficient mitigation techniques for this category of attack. In the following table, I show their effectiveness against principal mitigation techniques. As it's possible to read, the majorityof them aren't effective against MITB, except the use of hardened browsers or an outbound-channel for the validation of transactions.
There are, of course, exceptions also for those cases. For example, hardened browsers are ineffective against zero-day exploits.
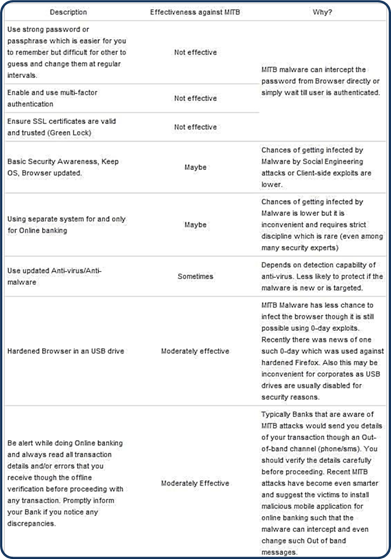
Figure - MITB mitigation techniques
The Zeus Trojan
Zeus is a trojan used to steal banking credentials by "Man In The Browser" keystroke logging, and form grabbing. It's spread mainly through drive-by downloads and phishing schemes. To give an idea on the use Zeus within the cyber crime ecosystem, consider that 9 million of those phishing e-mails have been sent since 2009.
Zeus was first detected in July 2007, when it was used to steal information from the United States Department of Transportation. Another important milestone in the story of Zeus is on October 1st, 2010, when the FBI announced it had taken down the main cyber crime network which had used Zeus, stealing nearly $70 million. Unfortunately in May 2011, the then current version of Zeus' source code was leaked, and in October, the abuse.ch blog reported a new custom build of the trojan that relies on more sophisticated peer-to-peer capabilities.
In reality, the availability on the Zeus source code online has made it possible to develop a model of sale known as "malware-as-a-service." Many groups of cyber criminals have started to offer customization of malicious code underground, according to the specific requests of their clients. In a short time, numerous customized variants of Zeus were found on the black market, including a version to work with social media, or to be able to be controlled by C&C servers hidden in Tor network.
For a deeper understanding of Zeus malware, I suggest you look at the ZeusTracker (https://zeustracker.abuse.ch/statistic.php) website. That's a valuable source of information. The portal reports statistics on Zeus, including current geo-localizations of infections, and the number of servers tracked online. The various Zeus' botnets are estimated to include millions of compromised computers (around 3.6 million in the US.) The following data is from a month ago.
- Zeus C&C servers tracked: 881
- Zeus C&C servers online: 325
- Zeus C&C servers with files online: 28
- Zeus FakeURLs tracked: 1
- Zeus FakeURLs online: 1
- Average Zeus binary Antivirus detection rate: 38.9%
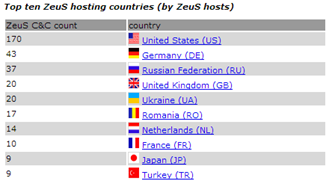
Figure - Zeus Statistics form ZeusTracker
"Hand of Thief" Trojan Hits Linux users
I'll conclude this overview of malware-based attacks against online banking services with a reference to the Linux and Mac platforms. Unfortunately, too many people think Linux and Mac OS X are immune to malware.
Due the growing popularity of Linux on the desktop, the cyber crime ecosystem has finally produced a Linux trojan. RSA, the Security Division of EMC, has reported that a Russia-based cyber crime team has begun to offer a new banking trojan targeting the Linux operating system.
"Hand of Thief" is the name of the trojan. It's a new financial malware that's being sold on Russian underground forums, capable of infecting Linux users. The trojan archives stolen credentials and user data (e.g. timestamps, websites visited, and cookies) in a MySQL database.
"Hand of Thief" is currently for sale for $2,000 with standard functionaly, including form grabbers and backdoor infection vectors. In the "very near future," however, its sellers will add a suite of web injections which should push the price up to $3,000.
An author declared that the malware had been tested on fifteen different Linux operating system distributions for desktop users, including Ubuntu, Fedora and Debian. Eight Linux desktop environments, including KDE and GNOME, also support the malware.
Since Linux has fewer users, and is known for dispatching speedier patches given its open source nature, it's surprising that attackers developed a high-price banking trojan that specifically targets the operating system.
Figure - Hand of Thief malware
Mobile
Security researchers are observing the increasing interest of cybercriminals in new platforms, including cloud, mobile and social networking. The reason is the capability of these infrastructures to reach a wide audience, and the lack of awareness in cyber threats.
Mobile platforms, due to their high penetration level, are the technology most used to provide banking services. For that reason, it's a popular target for cyber crime.
When we speak about mobile, we cannot ignore that Android is the OS that has the greatest market share. The downside is that Android malware has monopolized the mobile scenario, as showed in a picture extracted by the last F-Secure Threat Report.
It's evident that the cyber criminal black market is specializing its offer in malware that targets Android, exactly as for any desktop PC. In the underground market, it's possible to acquire various exploit kits specifically designed for mobile devices that allow for criminals to recruit machines for botnet architecture, or to organize prolific scam, typically premium SMS and click fraud.
The number of "highly specialized suppliers" who "provide commoditized malware services" is increasing. Popular malware such as Zeus, SpyEye and Citadel have been ported to mobile devices, ZitMo, SpitMo and CitMo are their respective mobile versions.
The purposes for products offered on the black market are varied, from spam distribution, the sale of malicious code for data theft, or for stealing of banking credentials. Many agents present a multi-feature profile that allows for the implementation of these features in a single flexible malware program.
In July 2013, Group-IB experts found a new kind of Android banking trojan («hardcore88») offered on the
black market. Cyber criminals spread it through traditional banking malware with web injections.
Figure - Ad for hardcore88 on a Russian forum
To have an idea of the capabilities of such malware. let's look at the technical specifications provided by the authors of the Android banking trojan:
- Very high vitality after the infection of mobile device (stealth mode)
- Comfortable WEB-interface, no need to use any gates or numbers, all is like in C&C for banking trojans
- SMS interception (detection of the device status, interception by sender, general interception)
- Blocking of the incoming calls from the banks
- You can control multiple infected mobile devices from different countries from C&C
The price of the new Android banking trojan is near $2000, and payment is allowed only through the escrow procedure, requested by the authors to avoid problems with non-trusted contacts. Another payment variant is to work on 10-15% of revenue.
Case study – Carpberp via Google Play
I decided to propose this case, because it demonstrates how bold and effective cyber crime is. This attack is an interesting case study, due to the capability of the attacker to use the official Google Play store as channel for mobile malware distribution.
The attackers used a version of Carberp malicious code to infect both mobile and desktop devices. The following are its phases of attack:
- The victim's PC is infected with a desktop version of the malware.
- When the victim visits the banking website for the first time on their PC, the malware opens a new window via web injection.
- Injected code creates a message that requests the installation of an application on the user's mobile to continue the login process.
- Users can get links to that application via scanning QR code or via SMS.
- The victims get the malicious app from Google Play, and install it.
- Once installed on a mobile device, the app sends information about the device to a C&C.
The main function of the application is the interception of incoming messages with one time passwords sent by banks. All received messages are stored in a special text log file that's transferred to a C&C server.

Figure - Carberp Frame Injection
Figure - Malicious App on The Google Play store
What's interesting about the analysis of the timeline of attacks is that it's possible to verify that the attackers were able to exploit the official Google Play to serve the malware on mobile devices.
- Development and testing (01/11/12)
- Start of infection (03/12/12)
- Detection (11/12/12)
- Removal from Google Play (13/12/12)
DDoS attacks
Another insidious cyber threat for online banking services are DDoS attacks. Security experts and law enforcement warned the banking sector of a possible rise of DDoS attacks, both financially and politically motivated. In late 2012 and early 2013, the self-proclaimed Muslim hacktivist group Izz ad-Din al-Qassam Cyber Fighters conducted Operation Ababil. That caused the destruction of banking websites of the US top banks including U.S. Bankcorp, JPMorgan Chase & Co, Bank of America, PNC Financial Fervices Group, and SunTrust Banks.
Security experts noted that the hackers adopted an anomalous strategy for DDoS attacks. Instead of using botnets, they hit targets involving a network of volunteers that deliberately have participated in the operations. While a classic botnet, although is very efficient, is quite simple to detect due the presence of anomalous traffic to and from the Command and Control servers, in this case the presence of volunteers complicates the mitigation of the attack.
The DHS and FBI have reportedly been liaising with cyber security officials in 129 other countries, and shared details of a total of 130,000 IP addresses that have been used in the attacks. The attacks have resulted in customers sometimes being unable to access online or mobile banking services, due to the extension of the attack.
Main categories of DDoS attacks are:
- Volume Based Attacks- The attacker tries to saturate the bandwidth of the target's website by flooding it with a huge quantity of data.
- Protocol Attacks- The attacker's goal is to saturate the target servers' resources or those of intermediate communication equipment (e.g., load balancers) by exploiting network protocol flaws.
- Application Layer (Layer 7) Attacks- Designed to exhaust the resource limits of web services, application layer attacks target specific web applications, flooding them with a huge quantity of HTTP requests that saturate a target's resources.
Major trends that DDoS mitigation solution providers are observing are:
- Larger and larger network attacks- These large-scale attacks often use SYN flood and DNS amplification as their tools of choice.
- Hit and Run attacks- These are smaller scale application layer attacks that don't last very long, but occur every few days.
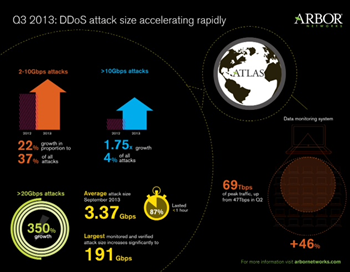
Figure - Arbor Q3 2013 Report
DDoS attacks are also used for the purposes of extortion, or as a diversion to hide the effects of an ongoing attack. The latest trend observed for recent offensive operations against numerous US banks is that fraudsters are targeting wire payment switches, instead to hitting directly into the banking accounts of individuals and businesses.
The attacks hit financial institutions directly. Security experts believe that bank staff are targeted by a spear phishing campaign. Despite that, it's still not clear how the attackers obtained access to twire payment switches at banks. A wire payment switch is a component that manages and executes wire transfers at banks. Its impairment represents one of the worst scenarios of an attack that banks could suffer from.
In spring 2013, the Dell SecureWorks Counter Threat Unit (CTU) published the "2012 Threatscape Report," which highlighted that fraudsters have been using Dirt Jumper, a $200 crimeware kit used for DDoS attacks. It's used to divert bank staff attention away from fraudulent wire transactions.
"The CTU research team continues to observe growth and active development within the underground economy, both in offering DDoS as a service as well as creating DDoS kits used by threat actors with any skill level. Dirt Jumper is the DDoS malware family most often encountered by CTU researchers, and it went through several iterations throughout 2012. While Dirt Jumper can still be found by its original name, the most recent version has been named Pandora. A number of other DDoS kits surfaced, such as YZF, DiWar, and ArmageddoN. Some of these kits turned out to be a rebranded version of Dirt Jumper. Others, such as BlackEnergy and Optima, remained in active use as well."
In September 2012, the FBI, Financial Services Information Sharing and Analysis Center (FS-ISAC), and the Internet Crime Complaint Center (IC3), issued a joint alert
about the diffusion of the Dirt Jumper crimeware kit, being used to DDoS attack banks, to hide fraudulent transactions.
Cyber criminals used "low-powered" distributed denial-of-service (DDoS) attacks as a diversion strategy, while they operated fraudulent wire transfers. The losses due to credit institutions amounted to several million dollars.
Once a DDoS is underway, hackers take over a payment switch (e.g. wire application), using an accredited privileged user account. That way, cyber criminals could control a master payment switch, and transfer as much money from as many accounts as they can get away with, until they're discovered.
Once the credentials of multiple employees are obtained, cyber criminals were able to get privileged access rights on a wire payment switch and "handle all aspects of a wire transaction, including the approval." The wire transfer amounts have varied between $400,000 and $900,000, and, in at least one case, the actors raised the wire transfer limit on the customer's account, to allow for a larger transfer.
Figure - Dirt Jumper Tool
Assessment of the cybercrime market size
It's very difficult to provide an estimation of losses related to cybercrime activity against banks. The majority of financial institutions prefer to keep data related to suffered attacks and cyber fraud reserved. Some independent organizations and security firms have produced shocking information based on their investigations.
The Financial Fraud Action UK reported that in 2012, online banking fraud losses totaled £40 milion, a 12% increase compared with losses in 2011. Meanwhile, Group-IB has recently published an interesting report titled "Group-IB Threat Intelligence Report 2012 – 2013 h3" that estimated Russian online banking fraud at $446 million. According to the Group-IB research team, the average amount stolen from legal entities and from individuals were estimated at $54,700 and $2,500, respectively.
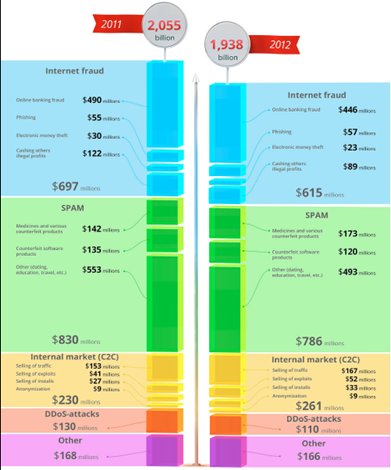
Figure - Group-IB on Russian Underground
According to Group-IB, there was an average of forty-four thefts carried out from online banking systems in 2012.
The Bank of Russia reports that 7870 incidents were recorded in banks in the second half of 2012 alone. Of those incidents, 43.1% were related to illegal transfer of funds via internet banking. Having said that, the Bank of Russia claims that an average of twenty-eight thefts are committed daily.
The Group-IB Threat Intelligence Report contains an entire section on attacks against financial institutions. Experts remarked that the main problems for banking are a very low level of security, and the habits to hide some incidents, where their systems have been compromised or experiencing data leakage.
There's a continuous and incessant action of cyber crime, thanks to a sustained and effective offering of tools and services underground. Cyber thieves are mainly targeting small and medium sized organizations every week, stealing millions of dollars in an ongoing scam that has moved about $100 million U.S. out of American bank accounts.
The major products on the black market for online cyber crimes against banking services are:
- Source code for malware, customizable according to user needs. Security experts have detected numerous variants of Zeus and Carberp malware released in the wild, and designed for specific financial institutions.
- Managed SMS flooding services and DIY DoS-ing (Denial of Service) tools to hit a phone of a bank payment service's customers, in an attempt to prevent customers to be reachable when a suspicious real-time withdrawal or transaction takes place.
- Millions of harvested emails, spam-ready SMTP servers, and DIY spamming tools are available to target bank customers.
- Bank information stealing applications for Android devices (e.g. Android.Bankun.)
- DIY RDP-based botnet generating tools with features for collecting information about a payment or banking system.
- Trained fraud assistants, speaking multiple languages, to socially engineer a user or their bank or payment processing service.
Conclusion
It's too easy to predict an increase of cyber attacks against online banking services. Due to the factors explained in this article, while I write, nearly two dozen major U.S. and European banks are in the crosshairs of the Shylock, or Caphaw. Hesperbot malware is creating great concern among security experts. Hesperbot is able to infect Android, Symbian and Blackberry OSs. It's also able to create a VNC server on the victim's system, and intercept network traffic using HTML injection techniques. All of its features make it very dangerous.
Early 2013, RSA discovered traces of a new banking trojan named KINS. An announcement was found on the Russian black market. According to RSA experts, the KINS trojan could have an impact on banking ecosystem superior to Spyeye and Zeus.
On the other hand, banking has adopted even more sophisticated countermeasures to mitigate the risks, and to evaluate the level of security of their infrastructure. For example all major UK banks will take part in the most extensive cyber threat exercise in two years, to test their ability to survive a sustained online attack against payment and market systems.
One of the most important ways to mitigate cyber attacks and data breaches is to share information about major incidents and cybercrime trends. Banks, law enforcement and intelligence agencies must cooperate to prevent further damage and mitigate cyber threats that are even more sophisticated.
References
http://securityaffairs.co/wordpress/19010/cyber-crime/online-banking-cybercrime.html
http://securityaffairs.co/wordpress/13991/cyber-crime/apwg-global-phishing-survey-report.html
https://resources.infosecinstitute.com/phishing-dangerous-cyber-threat/
http://securityaffairs.co/wordpress/15379/cyber-crime/carberp-banking-trojan-code-or-sale.html
http://securityaffairs.co/wordpress/16611/malware/kins-trojan-is-threatening-banking-sector.html
http://securityaffairs.co/wordpress/18772/cyber-crime/atlas-q3-2013-ddos.html
http://securityaffairs.co/wordpress/15003/malware/facebook-zeus-malware-targeting-bank-accounts.html
https://zeustracker.abuse.ch/statistic.php
http://www.zdnet.com/linux-desktop-trojan-hand-of-thief-steals-in-7000019175/
http://blogs.rsa.com/wp-content/uploads/VOHO_WP_FINAL_READY-FOR-Publication-09242012_AC.pdf
http://securityaffairs.co/wordpress/12195/malware/threat-report-h2-2012-proposed-by-f-secure.html

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!










