Introduction to GSM security
The Global System for Mobile Communication or GSM is a wireless communication that uses digital technology and is widely deployed across the globe for mobile communications, such as mobile phones. This technology utilizes microwaves, and its signal transmission is divided by time, mostly known as Time Division Multiple Access (TDMA). In this article, I will be discussing the method that could be used to see the traffic on a GSM network and how an attacker could abuse the GSM network.
Mobile communication technology was already developed and widely used in the early 1980s. For the first time, the C-NET system was developed in Germany and Portugal by Siemens, the RC-2000 system was developed in France, and the NMT system was developed in the Netherlands and Scandinavia by Ericsson, as well as the TACS system which operates in the UK. GSM appeared in mid-1991 and eventually turned into mobile telecommunications standard for the whole of Europe, maintained by the ETSI (European Telecommunications Standards Institute) technical committee.
GSM started its commercial operation at the beginning of the last quarter of 1992 because GSM is a complex technology and needed more assessment to be used as standard protocol. In September 1992, type approval standards for mobile agreed to consider and incorporate dozens of test items for GSM production.
In Europe, GSM was originally designed to operate at the frequency of 900 MHz. In this frequency, the uplinks use frequencies between 890 MHz to 915 MHz, and frequency between 935 MHz to 960 MHz is used for downlinks. The bandwidth used is 25 MHz ((915 - 890) = (960 - 935) = 25 MHz), with a channel width of 200 kHz.
GSM network architecture
Typical GSM network architecture is divided into 3 parts:
- Mobile Station (MS)
- Base Station Sub-system (BSS)
- Network Sub-system (NSS)
And all elements of the network at the top form a PLMN (Public Land Mobile Network).
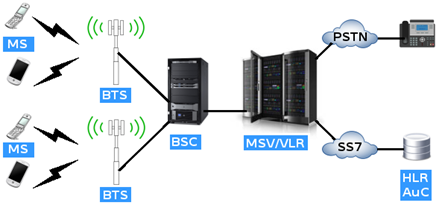
Picture 1. GSM network architecture.
Mobile Station or MS is a device used by the customer for making phone calls. This device consists of:
- Mobile Equipment (ME) or the handset (UM) is a GSM device that is located on the user's or customer's end that serves as a terminal transceiver (transmitter and receiver) to communicate with other GSM devices.
- Subscriber Identity Module (SIM) or SIM card is a card that contains all customer information and some information about services. ME can't be used without SIM in it, except for emergency calls. The data stored in the SIM in general are:
- International Mobile Subscriber Identity (IMSI).
- Mobile Subscriber ISDN (MSISDN).
- Encryption mechanism.
Base Station System or BSS consists of:
- Base Transceiver Station (BTS) is a GSM device that is directly related to MS and serves as the sender and receiver.
- Base Station Controller (BSC) is a controller device for base stations located between the BTS and MSC.
Network Sub System or NSS consists of:
- Mobile Switching Center (MSC) is a central network element in a GSM network. MSC works as the core of a cellular network, where MSC main role is for interconnection, both among the cellular or wired network PSTN or with the data network.
- Home Location Register (HLR) is a database that saves the data and customer information permanently.
- Visitor Location Register (VLR) is a database of the subscribers who have roamed into the jurisdiction of the Mobile Switching Center (MSC) which it serves.
- Authentication Center (AuC) authenticates each SIM card that attempts to connect to the GSM core network (typically when the phone is powered on). This also checks the validity of the customer.
- Equipment Identity Registration (EIR), is often integrated to the HLR. The EIR keeps a list of mobile phones (identified by their IMEI) to be banned from the network or monitored. This is designed to allow tracking of stolen mobile phones.
GSM layer
There are 3 layers in the GSM network:
- Layer 1 or the physical layer, for setting the channels.
- Layer 2 or the data-link layer, whose main role is to identify the data that is sent from UM to BTS.
- Layer 3 consist of 3 parts: Radio Resource (RR), Mobility Management (MM) and Call Control (CC) that serves as a regulator for radio, mobile management and call control.
Illustration of how GSM works
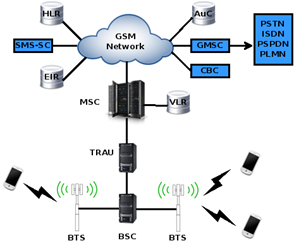
Picture 2. Illustration of how GSM works.
- Mobile phone is input with the destination number and connects to the nearest BTS.
- BSC and BTS send to MSC to continue and proceed to the AuC for checking the user identification.
- MSC proceeds to the HLR / VLR to check the existence of mobile phone.
- BSC and MSC proceed to the nearest BTS where the destination mobile located.
Problem
The background of this issues lies in the GSM network. Due to leaking of the design of encryption in 1994, it could be attacked, such as sniffing the voice in an established communication.
Attacking
1. Packet analysis
At this stage, the attacker will do packet analysis on one of GSM providers (for this example, the attacker will attack one of the service providers in Indonesia). The attacker is using multiple devices for packet analysis (Openmoko and Nokia 3310) and using Wireshark to dissect information used in GSM networks such as:
- Encryption used by the provider.
- ARFCN number.
- Location of the mobile phone, etc.
The first step is that the attacker will analyze encryption used by the provider:
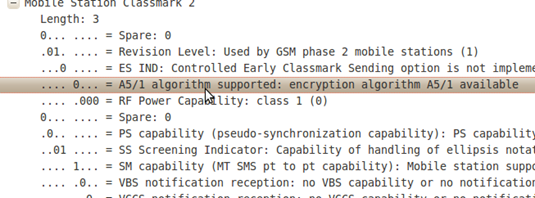
Picture 3. A5/1 encryption used by the provider.
In the picture above, the encryption used by the provider is A5/1. In the second packet, we could see the location in ARFCN, because ARFCN is determinant of the uplink and downlink signal to a GSM network.
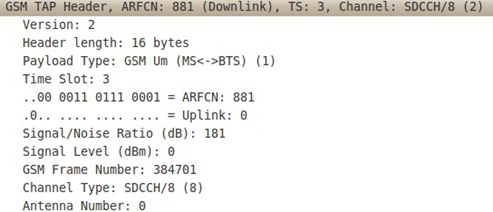
Picture 4. ARFCN (downlink) in use.
From the above picture, we could see that the provider uses ARFCN 881. For more details, the frequency for ARFCN 881 is as follows:
- ARFCN: 881
- Downlink frequency: 1879000000 Hz
- Uplink frequency: 1784000000 Hz
- Distance: 95000000 Hz
- Offset: 512
- Band: GSM1800 (DCS 1800)
It could be assumed that the provider uses encryption A5/1 and 1879000000 Hz frequency for downlink and 1784000000 Hz for uplink. However, ARFCN is not static in a communication.
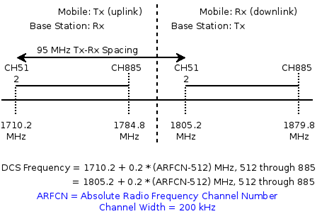
Picture 5. ARFCN calculation (GSM 1800)
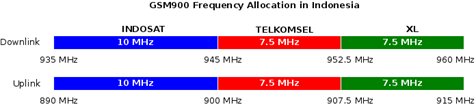
Picture 6. GSM900 frequency allocation in Indonesia.
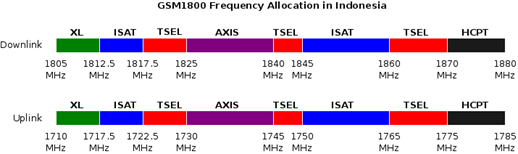
Picture 7. GSM1800 frequency allocation in Indonesia.
2. Authentication of a communication
When MS communicates to a BTS, MS identifies himself using IMSI and IMEI, and BSC to MSC communication to respond to IMSI. The authentication function is to assure that MS is a legitimate user. An illustration can be seen in the image below:
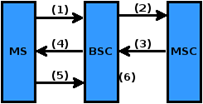
Picture 8. MS Authentication flow.
An explanation for the above picture is as follows:
- MS sends IMSI and IMEI to BSC.
- BSC requests IMSI and IMEI to MSC.
- MSC responds and sends RAND, SRES and Ki.
- BSC sends RAND to MS.
- MS responds with SRES'.
- BSC checks SRES'.
3. Kc Generation On A5/1
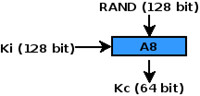
Picture 9. Kc generation on A5/1.
The picture above shows the process of Kc generation before being used to send and receive a communication.
- RAND is a random number generated by the AuC when a customer makes a request authentication to the network. RAND isused to generate SRES and Kc.
- Ki is key authentication paired with IMSI when a SIM card is made. Ki only exists on the SIM card and the Authentication Center (AuC). Ki never get transmitted over the GSM network.
- A8 is an algorithm that's being used to calculate Kc. Ki and RAND are inserted into the A8 algorithm and the result is Kc. The A8 algorithm exists on the SIM card and the AuC.
- Kc is the key used in the A5 encryption algorithm to write and decipher data that is being sent when communication occurred.
Sniffing GSM In Realtime
In order to be able to sniff a GSM packet, you must have a hardware that works as a receiver. For example, the RTL-SDR with rtl2832 chip. However, this hardware has a limitation. The maximum packet capture is 16 kHz wide. In other words, not all GSM packets can be captured using this hardware.
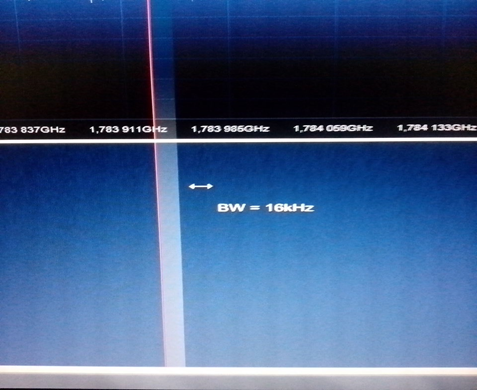
Picture 10. Sample packet captured with rtl2832 DVB (max 16 kHz).
GSM uses 200 kHz for communication and it is divided into 8 slots (200 kHz / 8 = 25 kHz / slot).
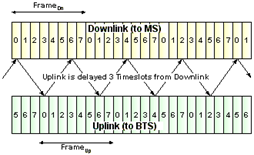
Picture 11. Downlink and uplink frame illustration.
Before we could start capturing GSM packets, first we must know the ARFCN in use. One method that could be used to find out the ARFCN is by using Blackberry Engineering Mode. In order to use that feature, you can simply search for "blackberry engineering mode calculator". After entering the engineering mode, you can see the ARFCN currently in use as you may see in this picture:
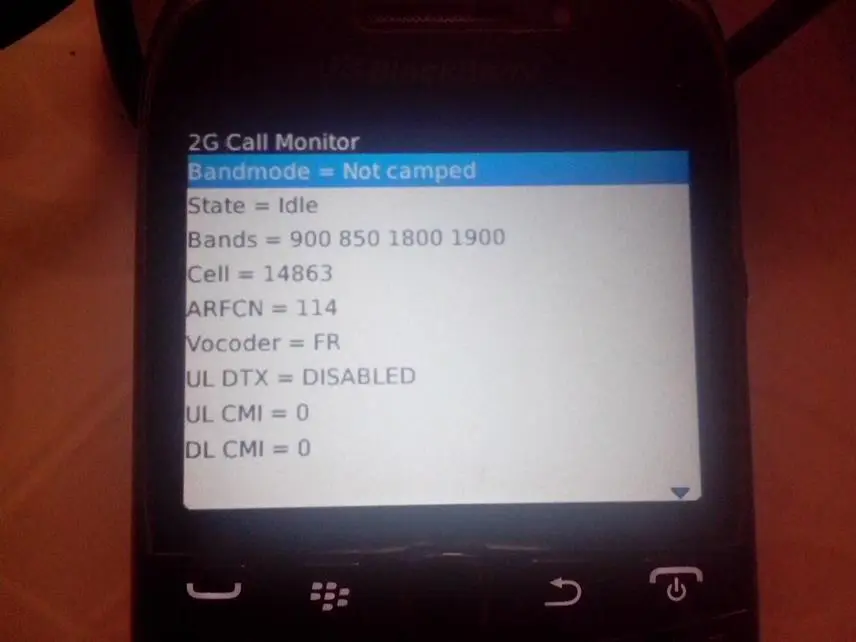
Picture 12. Blackberry engineering mode (ARFCN 114).
After knowing the ARFCN, we could proceed to capture the downlink packets. The capturing process could be seen in this picture (the result is not optimal due to a standard antenna being used):
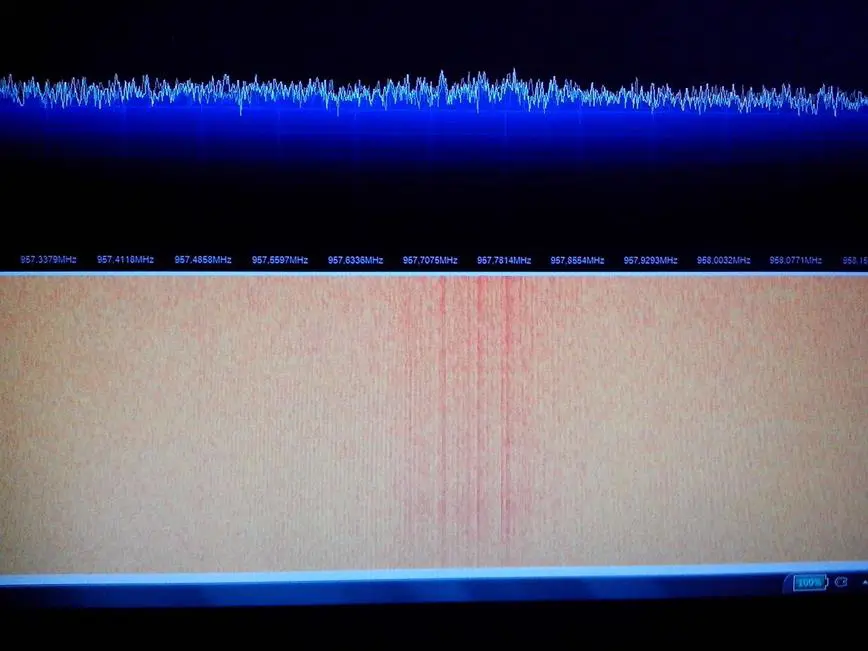
Picture 13. Sample captured with DVB (only to see the downlink frequency).
From the above picture, we could see that the signal is not strong enough and it could increase the packets lost during capture period. Here's an example of captured GSM packets using RTL-SDR and analyzed using Wireshark:
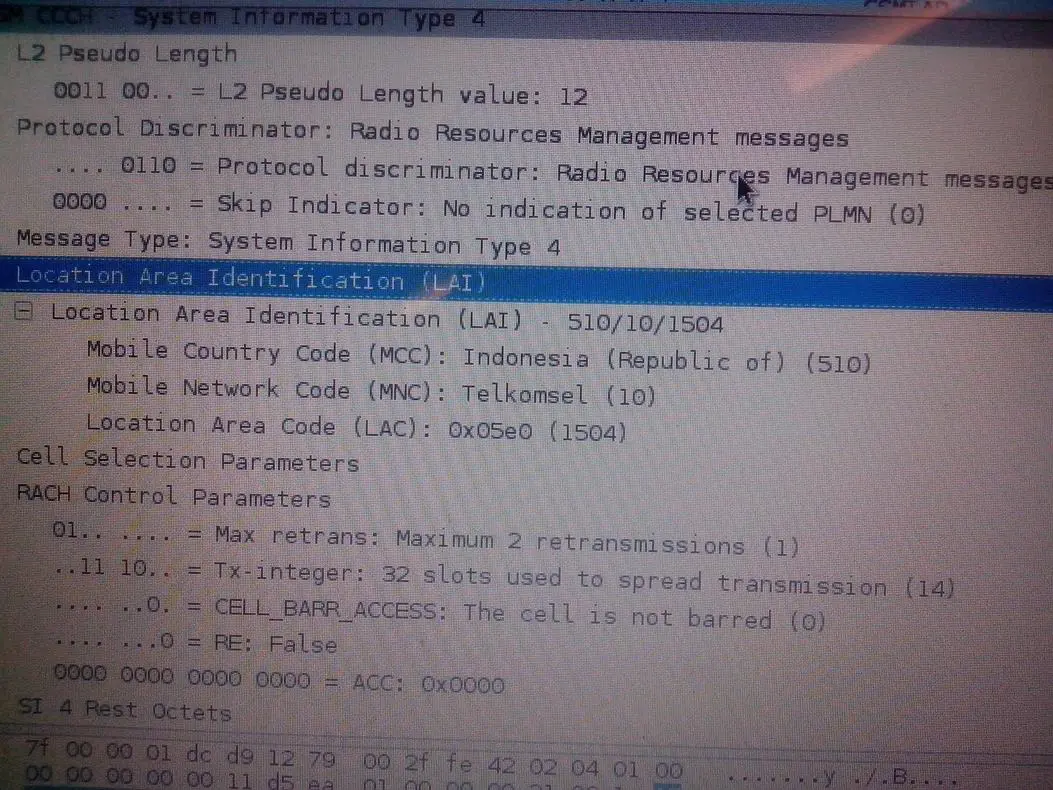
Picture 14. Sample GSM packet captured using RTL-SDR and analyzed using Wireshark.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
Conclusion
From the above explanation, we could conclude that communication through GSM exposes some security concerns. An attacker who understands how the GSM protocol works and has complete GSM standard documentation could find a way to attack the GSM networks, especially if security is poorly implemented.










