Introduction to the Business of Stolen Card Data
Introduction
I receive many questions from people who don't work in the security field about the use of stolen credit card data in the cyber-crime ecosystem, so I decided to provide more information, starting from the clamorous data breach of the U.S. retailer Target.
How it is possible to monetize the information stolen during a cyber-attack? How much do sensitive information and stolen credit cards cost and where it is possible to acquire them? Groups of cyber-criminals, mostly located in Eastern Europe and Russia, are part of an organized network that is able to sell these commodities to other criminals who desire to conduct a cyber-attack or to realize a scam.

FREE role-guided training plans
Let me start by remarking that cyber-criminals find it more profitable to sell stolen credit cards than to directly use the data gathered for illegal activities. Many countries, including the U.S., still use credit cards based on a magnetic strip that are quite easy to clone; the lack of security measures such as security chips aids cyber-criminals. Fortunately, that is changing and principal financial institutions are working to replace an obsolete technology that exposes card holders to serious risks. The stolen credit card information came from identity theft through large-scale attacks based on botnets, and credit card skimming.
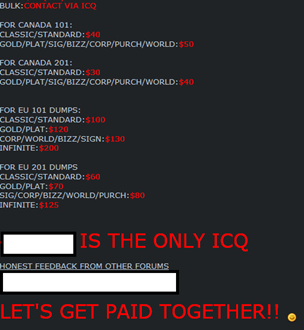
Of course, the price for stolen cards is variable and depends on different factors, including the amount, limits of the card, type of card, account balance, and geographic location of the card owner. The price for valid credit cards could reach $100 for each item and it is quite easy to buy them on specialized hacking forums; the Deep Web, for example, has plenty of black markets that offer them at cheap prices.
Card numbers are usually sold to brokers who acquire large numbers of stolen card numbers to resell to carders. The stolen card data market is not different from any legitimate marketplace; specialized sellers, escrow agents, resellers, and vendors flock to this specific business segment. The price for valid credit cards can be as high as $100 per card, depending on the amount of information available with the card, the type of card, and its known limits.
The amount of banking malware is constant increasing and old malicious codes are renewed, as happened for Zeus crimeware. The proliferation of such agents in responsible for the decrease of the average price for a stolen credit card.
The majority of websites that offer stolen card data guarantee their validity and, in some cases, they also provide replacements in case of problems.
It All Starts with a Theft
Every illegal activity related to cards begins with the theft of card data or the physical card. Card data used by criminals includes the card account number and all that is necessary to complete a legitimate transaction.
The account number, aka the primary account number (PAN), is often embossed on the card while the magnetic stripe on the back is used to archive different information, including the card holder's name, account number, expiration date, and verification/CVV code.
It must be considered that a growing number of web services on the Internet have commercial purposes and collect a huge quantity of information related to users' card data. Hackers are aware of this and exploit numerous techniques to access the precious information. Access to one of these databases that contains data for millions of card data could open the doors of heaven for a criminal.
Despite the fact that principal security firms specialize in card frauds and card issuers constantly monitor suspect activities to discover ongoing card frauds, victims do not often promptly discover the scams and report to law enforcement, so card thieves can operate unpunished for several weeks in the majority of cases.
Almost every financial institution has a 24-hour service to receive notifications of illegal activities and to make a timely block of the affected account. Without a prompt action by the card issuer, card thieves can purchase huge amounts of money in merchandise before the cardholder or the card issuer discovers the card fraud.
The bad news arrives to the cardholder after seeing a billing statement from the card issuer and, in many cases, the amount of stolen money could be considerable.
How Crooks Steal Your Data
Every year an impressive number of persons and organizations are victims of card frauds. The Internet carding industry is responsible for the identity theft and financial losses. The crime industry is able to steal an impressive amount of data, including banking credentials, card data, and personally identifiable information to sell and trade on the online black market.
The most common risky scenarios that expose users' data are:
- The term "skimming" is used to indicate the theft of credit card data used for a legitimate payment. Usually the criminals adopt a small electronic device dubbed a "skimmer" to swipe card data and store user's credit card information. Skimmers can be placed in front of ATM card readers and used to intercept data about the transaction for payment at markets or in any commercial activity. The use of a skimmer is usually combined with the use of small keypads or hidden cameras to capture the user's PIN.
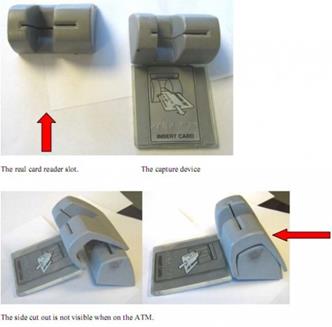
Figure 1. ATM Skimmer
- Data breach via "wardriving"—Cyber-criminals tap wireless networks by positioning their systems in the vicinity of retailers and markets. The attackers are able in this way to inspect network traffic, capturing account numbers as cash registers process purchases. In 2010, 11 individuals were charged with computer intrusion, fraud, identity theft, and many other crimes after stealing 40 million credit and debit card numbers via wardriving. The criminals tapped the wireless networks of popular retailers including the Sports Authority, TJ Maxx, and Barnes & Noble.
- Phishing attacks are another common method used by cyber-criminals to steal users' data. Phishing scams are very well articulated and are increasing in level of sophistication. Victims usually receive unsolicited mails that request them to provide information with the character of urgency (e.g., requesting the info to avoid account suspension). Recently the phishers are exploiting new channels, such as social networking platforms and mobile. Users are unaware of the cyber-threats and new schema of attacks have shown their efficiency in recent attacks.
- Malware-based attacks represent another common method adopted by cyber-criminals to collect banking data to resell in the underground. The amount of banking malware has increased; 2013 was a prolific year for malware authors who increased their efforts in the development of malicious agents able to gather all the user's information in the payment phase.
Case Study: Dexter and the Rise of Malware that Hits the Point of Sales
At the end of 2012, the Israel-based company Seculert announced that it had detected a new malware called Dexter, used for parsing memory dumps of specific POS software-related processes looking for Track 1/Track 2 credit card data.
The Dexter campaigns mainly hit hotels, restaurants, and big retailers in 40 countries, most of them located in the U.S. and the U.K. One year later, Dexter is still active in Russia, the Middle East, and Southeast Asia, but it isn't the only malware designed to attack point-of-sales systems. In early 2013, Group-IB detected a new POS malware called "DUMP MEMORY GRABBER" just a few months after the detection of the popular malware vSkymmer and Project Hook.
Security experts at IntelCrawler have discovered a huge credit card fraud realized through a point-of-sale botnet mainly based on compromised machines belonging to U.S. merchants. The botnet had infected nearly 150 Subway sandwich shops, stealing 146,000 credit card numbers. The discovery demonstrates the alarming trend toward infecting PoS machines instead of installing skimmer devices.
Figure 2. Point of Sale
The most recent discovery was made by a group of researchers at Arbor Networks in November that found two servers hosting the Windows-based Dexter malware. Arbor Networks senior research analyst Curt Wilson revealed that, while monitoring activity, its team saw 533 infected endpoints call back to the command and control infrastructure that are no longer on line.
Arbor experts haven't discovered when the infections started; it is likely that the attack was started with a classic spearphishing attack that lured victims to compromised websites hosting Dexter malware or the attackers exploited the knowledge of the default settings of targeted systems.
The security firm has reported the discovery to the Financial Services Information Sharing and Analysis Center (FS-ISAC) and, of course, to law enforcement.
"The way the attackers had the server set up, we saw credit card data posted to the site … The attackers were clearing the log files periodically, so there's no telling how long these campaigns have been ongoing," said Wilson.
Arbor experts have identified three different versions of Dexter:
- Stardust, which represents substantially the original version.
- Millennium.
- Revelation, the newest instances that also implement data transfer also over FTP.
Once they have collected dumps of credit card data, cyber-criminals sell them on the black market to allow other criminals to produce clone cards.
"This data will most likely be used by cyber-criminals to clone credit cards that were used in the targeted POS system."
Point-of-sale systems are privileged targets for cyber-criminals; in most cases, these systems are not dedicated PoS servers and they are poorly protected.
"The data being exfiltrated that we've seen suggests that the compromised machines are doubling up functions and running point of sale on a machine doing something else. PoS machines should be dedicated, locked down and have special policies applied to it … That's a bad practice to pile so much on one system. An attacker with access to credit card data would also have access to anything else the management system has access to," Wilson said.
Fortunately, as confirmed by Wilson, it is possible to use defense systems able to recognize the presence of Dexters, including basic anti-malware that should catch the process-injection techniques used here.
No doubt, the amount of malware used to steal data from PoS will increase in the next months. That's the time to think seriously of the security level of systems so critical for the business.
The Carding
The term "carding" refers the verification of the validity of stolen card data; it is a crucial activity for credit card fraud because it is indispensable for the card thief to remain under the radar. Cyber-criminals try to verify the card on a website that provides real-time transaction processing: If the card is accepted for the payment, it is valid. The card thief prefers to make payments for immaterial service with small amounts, for example testing the card for a donation. Small amounts are preferred by cyber-criminals because it is very difficult with them to reach a card's credit limit and, at the same time, the operation doesn't suspicious card issuers and site managers.
Another common method of carding is based on a shell game. Stolen credit cards in this case are used to charge pre-paid cards that are then used to purchase store-specific gift cards.
A collection of credit card data that has been verified is usually referred in the cyber-crime ecosystem as phish and the carder sells data files of the phish to other criminals who directly carry out the fraud.

Figure 3. Carding Process
More Info on Stolen Card Data, Higher Price
In numerous posts I have highlighted the possibility of acquiring stolen card data on the black market. Various websites on the underground and within the Deep Web listed the precious commodities at varying prices, depending on several factors such as the validity of the card, card amount limits, and the available amount of money in the bank account.
The recent data breach at the U.S. retailer Target has drawn new attention to the market for stolen card data. In particular, it has exposed another interesting trend in the cyber-crime ecosystem, the commercialization of the card information on the location of stores and point of sales where cards were used.
Why Provide the Above Data?
Financial security experts consider the information very precious for the arrangement of scams. The knowledge of the places where the cards were used allows the attackers to choose the points where they can use the cards and reduce the risk of detection for the ongoing scam.
Security expert Brian Krebs, who first reported the data breach suffered by Target, wrote a couple of interesting blog posts on the incident, presenting evidence that cyber-criminals behind the attack are offering on the black market also information on the state, city, and ZIP code of the Target store where the cards were used. The commercialization of stolen card data with localization information is a very clever tactic to increase the monetary value of the stolen commodities. Location information included in the stolen card data allows buyers to use cloned versions of cards issued to people in their immediate vicinity.
"Later, I learned from a fraud expert that this feature is included because it allows customers of the shop to buy cards issued to cardholders that live nearby. This lets crooks who want to use the cards for in-store fraud avoid any knee-jerk fraud defenses in which a financial institution might block transactions that occur outside the legitimate cardholder's immediate geographic region," Krebs explained.
According to Krebs, it is the first time that investigators have observed the sale of stolen card data with detailed localization information. Card thieves are aware that local use of a card makes it more likely that the cyber-criminals can use it for a long period before they are identified and blocked; stolen card data including information on their use makes such cards much more valuable to the cyber-crime industry.
Nearly 40 million credit and debit card accounts belonging to customers of the American retailing company Target were stolen during the traditional holiday shopping season.
The news was provided by the company with a public statement. All the users who have shopped at Target's stores during the Black Friday weekend were advised; at risk are all those customers who made purchases by swiping their cards at terminals in the stores of the Target company during the above period.
The stolen card data exposed during the data breach includes the cardholder's name, the credit or debit card number, the card's expiration date, and the CVV security code used to activate the card in a store. Of course, the alert was shared with the major U.S. credit card issuing banks and credit unions. JP Morgan Chase announced that it had put restrictions on the amount that the accounts affected by the Target breach could spend or withdraw daily. Fraud detection tools adopted by banks and financial institutions use complex analysis to track illegal activities especially after a data breach. One of the monitored behaviors is the use of the card data far from the space where it is used by legitimate card owner.
The location and frequency of expenses made with cards cloned from stolen card data are principal parameters controlled by investigators; it is now clearer why the value of the data is higher.
"Whoever is behind this breach appears to have a tremendous amount of not only technical, but also retail operations and payment industry knowledge. This could indicate someone who has previously worked in the retail payments industry," said James Huguelet, an independent consultant who specializes in retail security.
The incident raises the urgency for improving fraud detection capabilities to deal with the new sophisticated threat that is able to avoid being spotted by classic fraud detection methods.
How to Use Stolen Card Data?
There are various ways to use stolen card data. Criminals can clone legitimate cards and try to purchase products in local stores, but the Internet represents the privileged channel for fraud against merchants and retailers who sell online. When fraudsters pay for a service or product in the absence of a card, the technical term used is "card not present." In this case, the merchant must rely on the information provided by the buyer online. A common preventive measure for merchants is to allow shipment only to an address approved by the cardholder and merchant banking systems offer simple methods of verifying this information.
Transactions characterized by small amounts and a request for shipment of goods to the same location as the card holder generally undergo less scrutiny and avoid being investigated by either the card issuer or the merchant.
Selling Card and Stolen Card Data Online
As explained by Brian Krebs in his post, it is easy to find online websites that offer bank cards for sale. The search can start by simply googling for the bank bank identification number (BIN).
The BIN is the first 6 digits of a credit card number (16 digits in length), according the ISO/IEC 7812 standard, which identify the specific institution that issued the card to the card holder.
With similar research, it is easy to find card shops that offer stolen card data of interest for the cyber-criminal. Almost every market, of course, asks for payment in alternative currency schema, including Bitcoin, Litecoin, WebMoney, and PerfectMoney and also traditional wire transfers via Western Union and MoneyGram.
Crossing those researches with other results obtained by searching for terms such as "credit cards," "cvv," "sell credit card dump," "valid number," and "carding," it is possible to discover a huge number of websites that offer everything necessary for carding activities including plastic, electronic equipment (e.g., card reader/writers) to produce the cards and, of course, credit card dumps.
On the Internet it is possible to acquire stolen data from different E-shops. Each of them has specific goods; for example, many services offer complete access to data primarily belonging to US citizens.
Figure 4. E-Shop offering Stolen Card Data (Danchev 2012)
The black market today offers all the instruments to realize a fraud; the vendors of dumps are integrating their offer with additional services such as credit card validity checkers, botnets, and anonymizing services.
Almost every shop requests a registration fee from the customers to give access to various functions.
Figure 5. E-Shop Offering Stolen Card Data (Danchev 2012)
The prices vary with different parameters and, of course, are different if buyers need debit cards or credit cards; the cost of the second group has almost doubled. The most frequent questions I receive are:
"Why do cyber-criminals sell stolen credit card data for a few dozens of dollars when the account balance could amount to several thousand USDs?"
"Why would a cyber-criminal sell access to a stolen credit card details for such a low price, given that the actual balance of the card may outpace his original price a thousand times?"
Dancho Danchev, a popular cyber-crime expert, provided an insightful answer by defining the practice as "risk forwarding": The E-shop's owner sells the data at a low price to achieve instant financial liquidity of his assets, focusing his sales on bulk orders and forwarding the risk of getting caught to the prospective customers of his services.
Card Dump Format
A typical card dump could have the following format:
B41111111111111111111^LASTNAME/FIRSTNAME^060910100 000000000000000000
41111111111111111111=0609101000000000000000000000
- Where the letter B identifies to the POS system that your card is a bank card
- 4111111111111111 - Credit Card Number
- Last name - Last name of cardholder
- /- Separator
- First name - First name of cardholder
- 06 - Expiration Year
- 09 - Expiration Month
- 101 & Beyond - Bank data
Consider that, in many cases, stolen card data includes only the second track information, leaving the buyer with trying to figure out how to write track1 because most stores do not check the track.
4111111111111111=060910100000000000000
Track2 in most cases is just like the first track; to begin making track1 add a B that will indicate it's a Bank card.
B4111111111111111=060910100000000000000
then replace the " =" character with ^lastname/firstname^ .
B4111111111111111^LASTNAME/FIRSTNAME^0609101000000 00000000
And finally add six zeros at the end of the dump.
B4111111111111111^LASTNAME/FIRSTNAME^0609101000000 00000000000000
And that's your dump; a track1 has been created from track2.
On the market various software programs are available to encode the dumps. The Jerm application can help you for these activities.
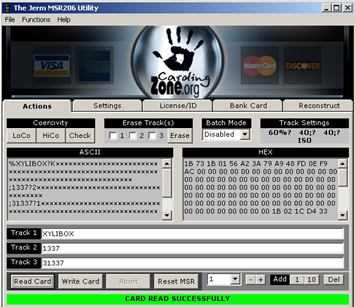
Figure 6. The Jerm Application
Dumps commonly available on the black market can be generated by specific applications or can be obtained by skimming activities. In most cases, generated dumps are not correct; a skimmed dump ensures that the actual card data was used while the cardholder swiped it onto a portable mag stripe reader that extracted the correct information for track1 and track2.
Another possibility for cyber-criminals is the theft of entire databases containing a collection of dumps.
Once a cyber-criminal has managed to obtain access to a set of credit card data by either compromising an insecure database, or through crimeware dropped on an affected host, he needs to purchase blank plastic and holograms and transfer the stolen information onto them to cash out as much money as possible.
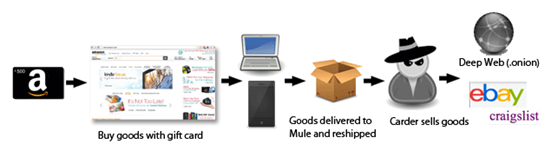
Cash Out, Reshipping and Money Mules
A common way to monetize stolen card data is to use gift cards to purchase goods such as electronic components (e.g., gaming consoles, laptops, smartphones) and high-value clothing. This process is very difficult to combat. In many cases, companies succeed in detecting and blocking the transaction only after the criminal is in possession of the purchased goods.
A crucial role in the scam is played by money mules. The goods are shipped via legitimate channels to unsuspecting individuals recruited as mules. The mules are recruited with email scams that promise easy profits just for re-shipping the purchased goods.
While the re-shippers are usually located in the same country as the criminal gangs that organize the illegal business, their tasks are to rearrange the shipment of multiple packages, usually outside the country. At this point, the schema is succeeding because the carder may then sell the product acquired and reship it through legitimate channels, such as popular consumer-to-consumer e-commerce platforms like eBay. Another possibility is to sell the goods on the black market, exploiting also online channels like specialized hacking forums or hidden services within the Deep Web.
To incentivize the sale on these website, the goods are sold at great discounts, usually around 50% of the original price, and they are reshipped or sent to a secure drop (e.g., vacant offices, multi-service facilities) that a purchaser has set up or that the seller uses for the purpose.
Figure 7. Monetization Sample (KrebsOnSecurity)
Of course, to avoid transaction tracking operated by law enforcement, cyber-criminals use alternative currencies. Virtual currency schema such as Bitcoin or Webmoney are very popular in the underground. Money is stored in the criminal's electronic bank account service.
Conclusions
Credit card fraud is one of the illegal activities of the most concern, a crime that is spread on a global scale and that doesn't require advanced hacking skills. The cyber-crime industry provides all the necessary products, tools, and services to aid criminals who intend to arrange credit card scams. Criminals could decide to acquire a dump of stolen card data from third parties, or set-up/rent a botnet to infect point of sales to capture payment information. The credit card scams are hard to detect and cause huge losses every year; for this reason, it is fundamental that victims report crimes and any suspicious activity to law enforcement and also stay informed on the evolution of principal cyber-threats.
References
http://krebsonsecurity.com/2013/12/cards-stolen-in-target-breach-flood-underground-markets/
http://krebsonsecurity.com/2013/12/non-us-cards-used-at-target-fetch-premium/#more-24132
http://securityaffairs.co/wordpress/20776/cyber-crime/dexter-hits-point-of-sales.html
http://securityaffairs.co/wordpress/20660/cyber-crime/israeli-banks-extortion.html
http://www.thebuzzmedia.com/atm-card-skimmers-hidden-in-plain-sight-and-hard-to-spot/
http://securityaffairs.co/wordpress/20605/cyber-crime/target-data-breach-40m-accounts.html
http://researchedsolution.wordpress.com/2013/09/14/the-life-and-crimes-of-a-carder/
http://ddanchev.blogspot.it/2011/10/exposing-market-for-stolen-credit-cards.html
http://blogs.wsj.com/ideas-market/2013/04/22/when-selling-stolen-data-reputation-matters/
http://credit-card-details-free.blogspot.it/

What should you learn next?