The Internet Drafts and Security Issues Around a Virtual Private Network Infrastructure
All of our articles in this series have reviewed what a Virtual Private Network Infrastructure is all about. Essentially, it is simply another layer of Security that a business or a corporation can implement into their existing Information Technology Infrastructure, also known more specifically as a "VPN."
The design of a VPN can either be quite simple or quite complex, depending on what the exact Security requirements are.
For example, if the organization is small enough, obviously the requirements will not be that extensive, of course, depending on the employee size. Perhaps just a few RSA tokens and a change in the login protocol will have to be made.
However, if the business is very large, with offices all over a certain geographic territory or even around the world, then the requirements will, of course, become much greater, as will the complexity of the VPN.
More servers will have to installed, as well as more Active Directory services to synch up all of the usernames and passwords (along with their associated rights and privileges) when the new Virtual Private Network Infrastructure has been fully deployed.
Also, new RSA tokens will have to be distributed, and the employees of the business or corporation will have to be trained in its effective usage as well, to garner its full effectiveness.
Also, extra hardware and software may have to deployed and implemented as well into the VPN system, in order so that it can be interoperable with the environment in which it will operate in. As it was discussed in another article, simply deploying a Virtual Private Network Infrastructure is not just a matter of implementing it.
It must be tested first in a pilot test to see how well it will interoperate in the production environment. This is the only way it can be discovered if there are any unknown issues which have not been taken into consideration and if they need to be. Many tests can be run here, especially those of QA Testing and Penetration Testing.
Although both of these are very important variables, is perhaps the Penetration Testing which is of utmost importance. By this, the testers will examine the strengths and the weaknesses of the Virtual Private Network Infrastructure from both outside as well as inside the perimeter.
There is often the misnomer that Cyber-based threats and risks can only exist from the external environment. While this is true, the crux of the matter is that many Security related vulnerabilities and weaknesses can also exist from within the internal environment as well.
For example, there could be a rogue employee or even a contractor who is intent on doing harm. This would be the best venue in which to do this, because the employee already has advanced knowledge of the existing Information Technology, along with the requisite permissions and rights to launch such an attack.
In this regard, the various Penetration Testing techniques employed should also include that of Social Engineering attacks so that the employees of the business or the corporation can become much more proactive in their respective work surroundings.
Apart from the testing component, our other articles have also further examined the following topics as well:
-
IP Tunneling:
This article reviewed how the Data Packets are encapsulated into another Data Packet, and how the second line of communications in a Virtual Private Network Infrastructure.
-
The Benefits and Risks of Implementing a VPN system:
From a financial standpoint is it even worth to deploy a VPN? When will the payoffs occur, and what is the Return On Investment (ROI) going to be like?
-
Security Policies:
The thinking is that a Security Policy only relates to the overall objectives of the business or the corporation. However, it is important to keep that each component of the Information Technology environment also needs to have its own Security Policy as well.
-
The Impacts of a VPN System:
As it has been discussed before, when a Virtual Private Network Infrastructure is fully deployed, it must interoperate with the legacy Security systems which are put into place. Therefore, its impacts on these various sub-components must be further examined as well in the test environment.
-
Building your own VPN or procuring an "off the shelf" VPN:
With the advances in technology, these days, business or a corporation can readily create and build their own Virtual Private Network Infrastructure. Although it may be cheaper to utilize this approach in the short term, there could be long-term consequences if the IT staff does not have the prior knowledge or expertise in building a VPN System.
This article is the last in our series of VPNs. In this, we will be focusing primarily on two main topics:
- The Internet Drafts Which Are Associated with a VPN
- The Vulnerabilities of A Virtual Private Network Infrastructure.
The Internet Drafts Which Are Associated With a VPN
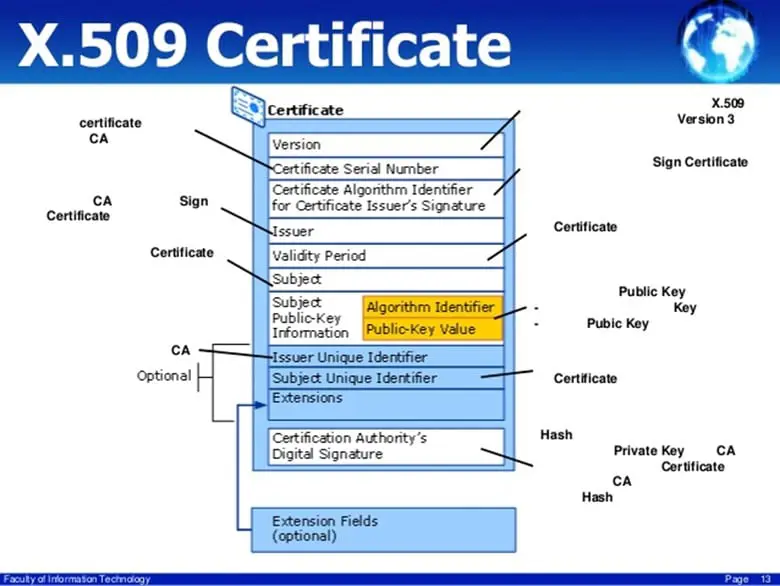
An Internet-based draft which is related to the Virtual Private Network Infrastructure is that of the "Internet X.509 PKI". Specifically, this relates to the Elliptical Digital Certificate Algorithm which is heavily used in a VPN System.
This Internet Draft deals with the following topics as it relates to the VPN:
-
Certificate Management Messages over the CMS:
Generally speaking, this covers the need for a Certificate Management Protocol utilizing a CMS in two different ways:
- The need for an interface that connects to the PKI products and services.
- The needs for a Certificate Enrollment Protocol using the Diffie-Hellman Public Keys.
- The Internet X,509 Public Key Infrastructure Time-Stamp Protocol Time stamps prove beyond a doubt that a transaction indeed took place at a certain point in time, and thus it serves as a "Trusted Third Party," also known as a "TTP" for short. This piece of the draft regulates how the format of the Timestamp Request should be sent to a Time Stamping Authority and what type of particular response is valid enough.
-
The X.509 Public Key Infrastructure Data Certification Server Protocols:
This document describes in detail the Data Certification Services for the Network Protocols used when communicating with it:
- The validation of the Digital Signature;
- Providing updated information with regards to the status of the Public Key Certificates.
-
The Internet X.509 Public Key Infrastructure PKIX Roadmap:
This document goes into the actual detail of the theory, and the implementation of the X.509 Digital Certificate based PKI.
-
The Internet X.509 Public Key Infrastructure-Qualified Certificates:
This document specifies the Digital Certificate profile for what is known as a "Qualified Digital Certificate." The primary purpose of this document is to define the syntax of the language that literally shies away from legal based jargon.
-
The Diffie-Hellman Proof of Possession Mathematical Algorithms:
This specialized document details the particular of two separate methodologies to produce a digital signature from a Diffie-Hellman key pair. The mathematical algorithms are designed to create an audit trail rather than just for digital signing.
-
The X.509 Attribute Certificates:
This document specifies two very mathematical based profiles that are used to provide the digital certificate authentication services.
-
The Basic Representation Token V1:
This technical document helps to define data structures that have been established and distributed by a trusted provider.
-
The Internet X.509 Public Key Infrastructure Extending Trust:
This technical document establishes the details that are needed to maintain a certain level of confidence by a trusted provider.
-
The Internet X.509 Public Key Infrastructure Operational Protocols LDAP V.3:
This document highlights in details the LDAP V.3 features that are required to maintain a PKI based on the X.509 digital certificates.
-
The Simple Certificate Validation Protocols, also known as "SCVP":
This specialized network protocol permits the client's computer to allow the primary servers to handle the digital certificate processing. As a result, this type of server can then provide certain types of information and data about the details of the digital certificates, especially its validity or invalidity.
The Vulnerabilities Of A Virtual Private Network Infrastructure
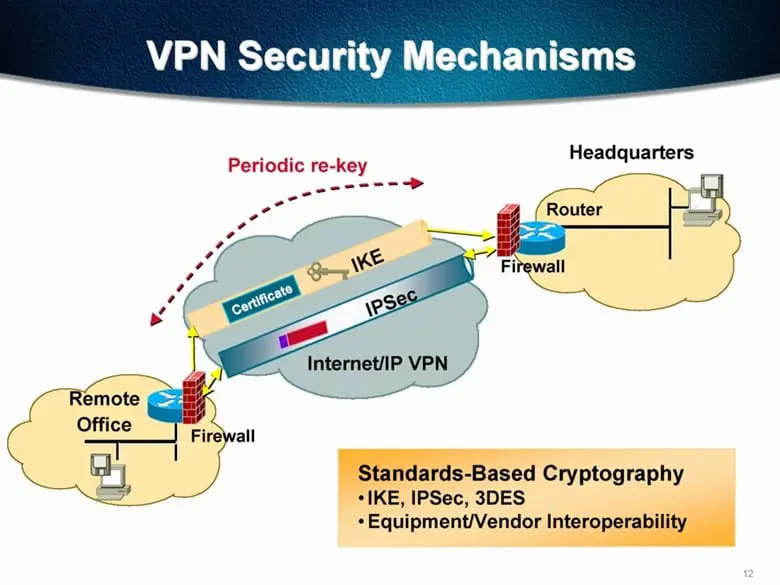
With regards to the Virtual Private Network Infrastructure, there are four critical areas where the Data Packets are the most risk for hacking and theft:
- Just after the Data Packets have been created, and before they have been encapsulated into another Data Packet.
- Immediately after a remote login connection from a workstation and/or wireless device to the Central Server(s).
- In a Client-Server Network based Topology, the transmission of the Data Packets to and from the Central Servers in a Wide Area Network setting. This is based on the assumption that IPsec is not being used, rather just the TCP/IP Protocol.
- If the VPN System is being used in a "Hosted" fashion, meaning, it is outsourced to a third party such as that of an Internet Service Provider (ISP), then the Data Packets will be secured by the policies which have been implanted by the ISP.
Conclusions
In summary, this article has examined the primary Internet Draft which surrounds the use of a Virtual Private Network Infrastructure, which is primarily that of the Internet X.509 PKI. In many businesses and corporations of today, you will find that many VPN Systems are actually integrated into a Public Key Infrastructure as well, of which a previous article also examined in greater detail. Also, the some of the major Security vulnerabilities of a VPN were also examined.
However, it should be noted that a Virtual Private Network Infrastructure has many sub-components, and that these particular Security weaknesses come from the standpoint of attacks and threats towards the Data Packets which traverse across the network medium in the VPN System.
After all, these are the most prized possessions of a Cyber attacker, because this is what contains the information and data which are transmitted from the sending party to the receiving party, and vice versa.
This article concludes our series on the Virtual Private Network Infrastructure. Our next articles will examine the Security issues of Smartphones and other types and kinds of wireless devices. It is important to note, that as reviewed before, securing remote login sessions from these types of hardware often requires the use of a VPN.
With the background information provided in this series of articles, we will also examine how a VPN can make Smartphones and other wireless devices secure as well.
Resources
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.138.8254&rep=rep1&type=pdf
https://www.infosec.gov.hk/english/technical/files/vpn.pdf
https://www2.informatik.hu-berlin.de/~redlich/publication/virtual_networks_in_the_internet.pdf
http://www.syringanetworks.net/Documents%20and%20Settings/27/Site%20Documents/PDFS/Cisco_MPLS_wp.pdf
https://eprint.iacr.org/2006/097.pdf
http://www.sersc.org/journals/IJAST/vol8/2.pdf
http://proceedings.informingscience.org/InSITE2012/InSITE12p053-067Awodele0012.pdf
https://www.infosec.gov.hk/english/technical/files/wireless.pdf

What should you learn next?
https://www.blackhat.com/presentations/bh-europe-06/bh-eu-06-Rey-up.pdf










