Installing and configuring CentOS 8 on Virtualbox [updated 2021]
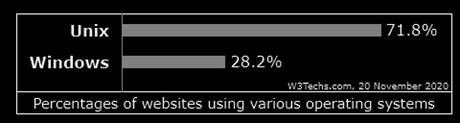
Unix-based operating systems are ruling the webserver OS market. According to data from W3techs, in 2017 Unix servers were used by 66.5% of all the websites, and 33.5% are using Windows OS. In the last few years, the market changed, but the Unix advantage is very clear:
To fight this trend, Microsoft have done fast and close proximity with Unix systems in the last years. For instance, Microsoft is promising to dramatically improve its Windows Subsystem for Linux (WSL) with GUI app support and GPU hardware acceleration. Another clear signal is the new release of Microsoft Defender for Linux environments.
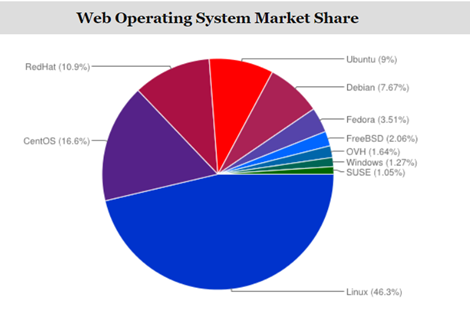
Unix is clearly leading. Let’s break it down into the actual OS, because there are many operating systems based on Unix are available in the market. According to the report concluded by SolveDNS, CentOS, RedHat, Ubuntu and Debian are the top, and Fedora follows them.
The CentOS clearly stands out amongst the others. It has its advantages and disadvantages. However, it has been clearly adopted by a large number of community members, so it must have some weight over others. In this article, we will discuss the core architecture, how it is different from others and how to install and configure it on the VirtualBox (demonstration).

What should you learn next?
How to install CentOS on VirtualBox
The things that you will need:
Download the appropriate version of both the packages. The 64-bit architecture has been used for this demonstration, so download the software accordingly.
Step 1
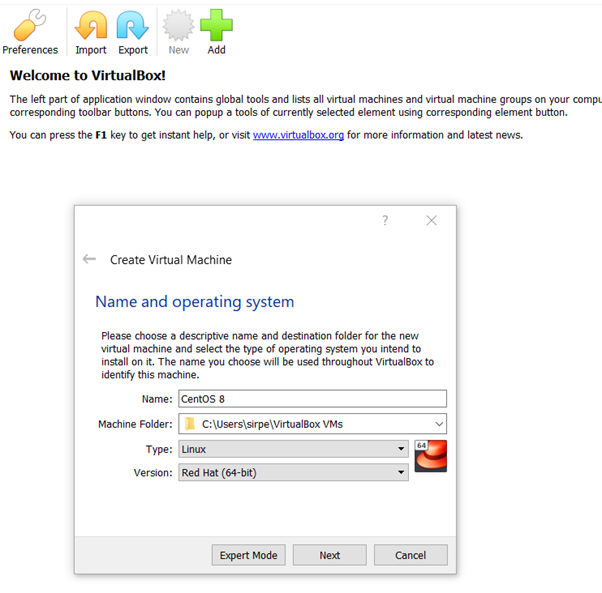
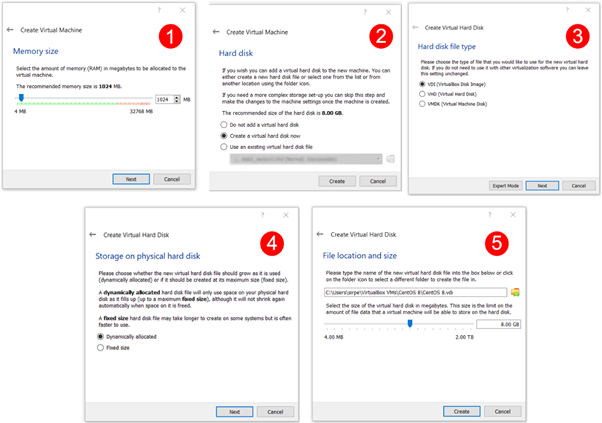
Install VirtualBox and open it. Click on the new to set up the new VM, select the Linux and then Red Hat, since CentOS is the clone of Red Hat and uses a similar architecture.
In the next window, allocate the memory size. Allocate at least 1024MB; you can allocate more if you have enough memory.
Next, create the virtual disk (VDI) and move to the next screen. Fixed size of the disk is not recommended in any scenario because you will be downloading many packages to run various applications.
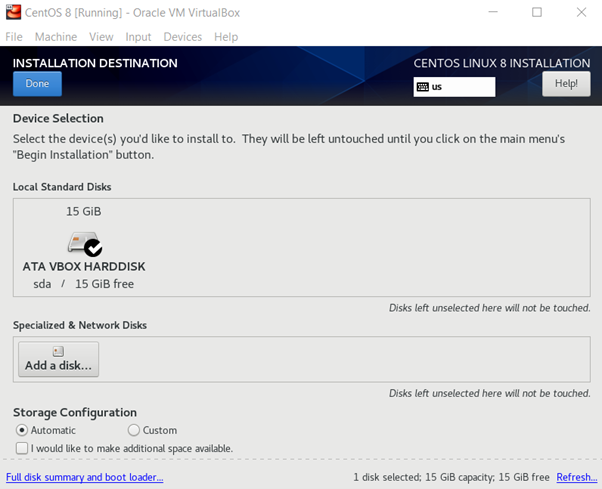
Select the dynamically allocated, make sure that your hard drive has enough free space. The 8GB space is insufficient, then set up at least 15 GB to start with (image 5 below), select and then finish the setup. Every step is presented below for a better understanding.
Step 2
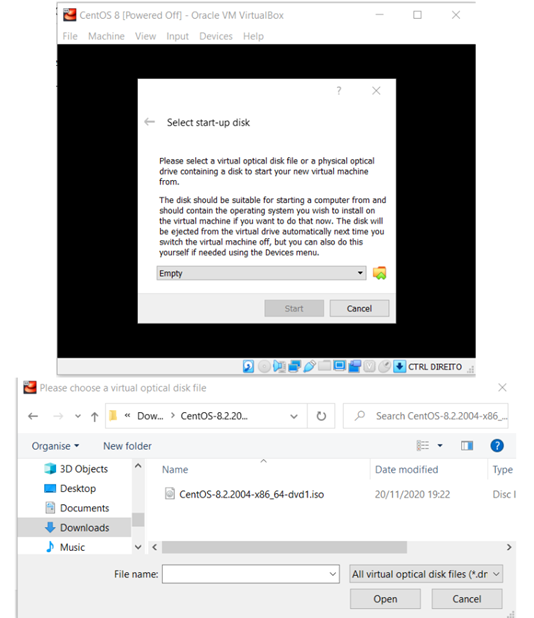
The ISO image of the downloaded CentOS has to be linked to the newly created virtual machine. Click on the setting - storage - empty and browse the ISO image.
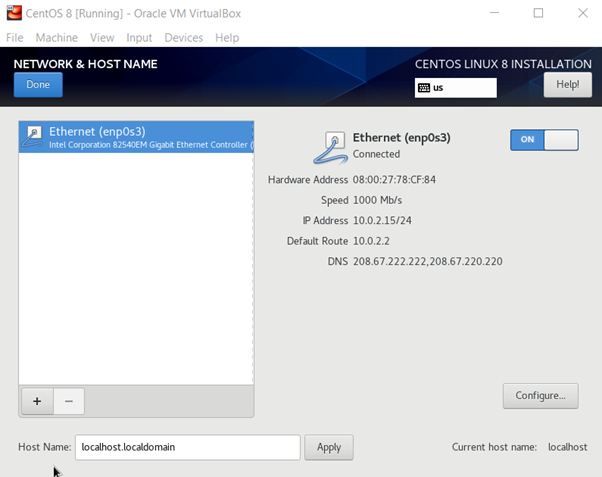
Enable the network adapter so that it can use the internet to download the required packages.
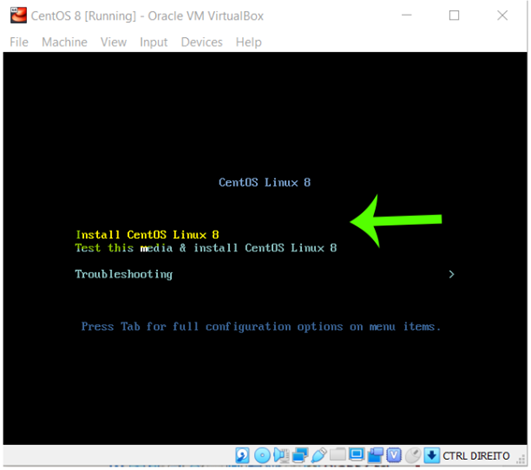
After that, the following screen is presented. Select “Install CentOS Linux 8” and proceed.
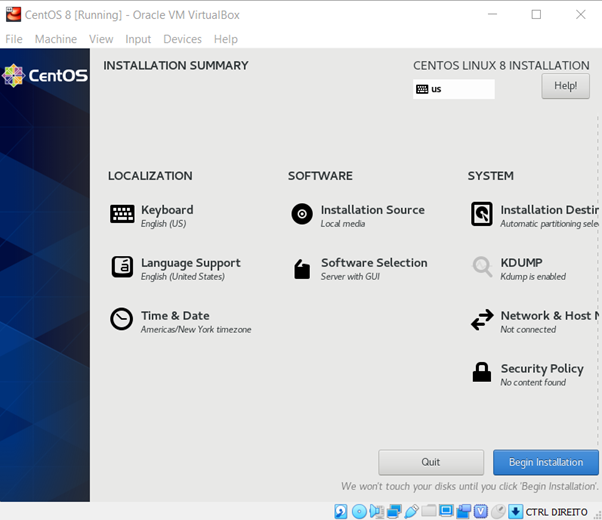
It will take time to load the packages, and you will see the opening screen of the server. It requires the basic information to set up the server:
- Time zone
- Keyboard layout
- Language support
- Installation source
- Software selection (important)
- Installation destination
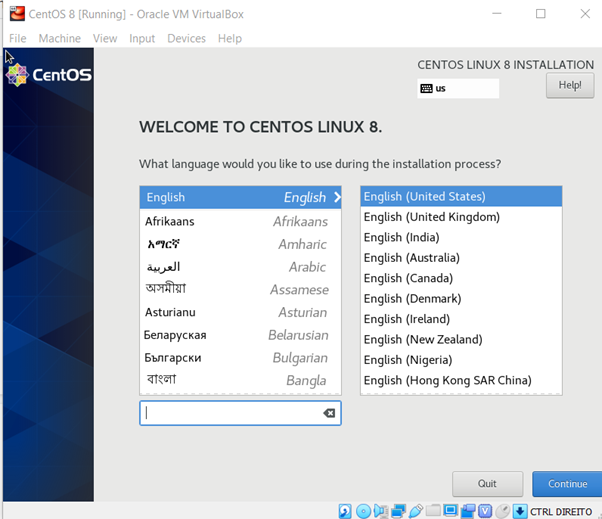
From the first opening screen, select the language that you would like to use during the installation process; for example, English (United States).
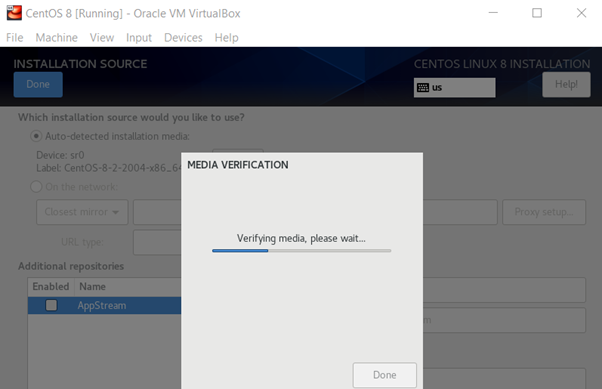
Once you have finished providing the basic information (language, keyboard, date and time), click on the installation source to confirm the ISO image that we have linked in step 2. Verify the installation source, go back and click on the software selection option.
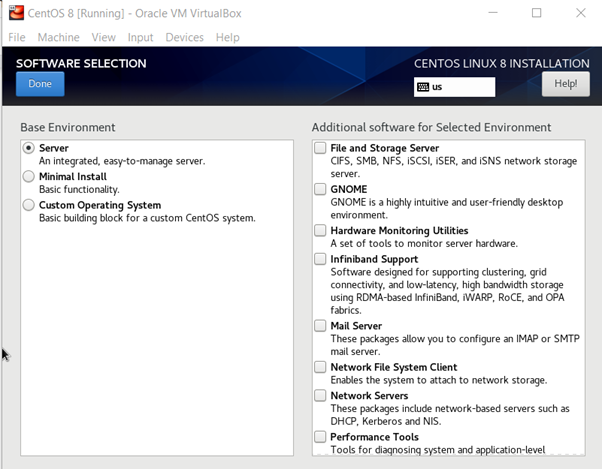
Select the desired option; for example, if you want to create an infrastructure server to run the complete network operation, select this option to get all the required packages installed. Similarly, it goes to the other option as well. Select the server with GUI to get the server installed with the graphical interface option, you can select the add-ons at this moment or get them whenever you need them. Click “done”; it will check the software dependencies and you will see the confirmation in a couple of seconds.
Next, click on the installation destination and select the newly created disk space. In the network and hostname setting, enable the network. You are done!
Finally, you can begin your CentOS 8 installation.
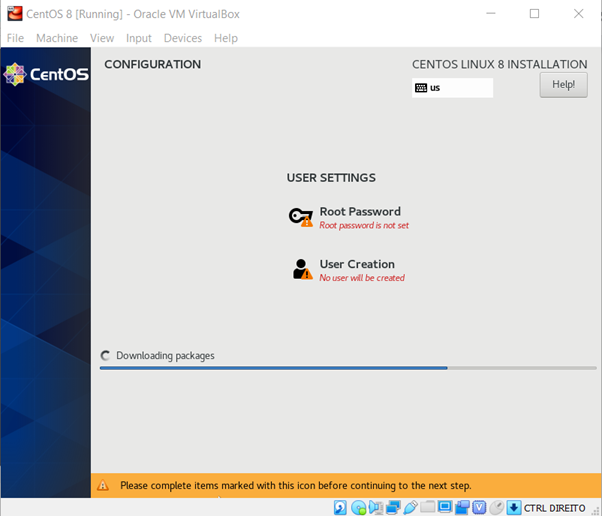
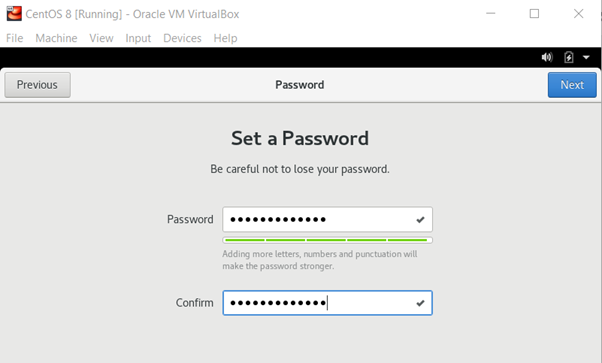
In the next screen, you will be asked to set up the root and username details. Select the strong root password and create your user.
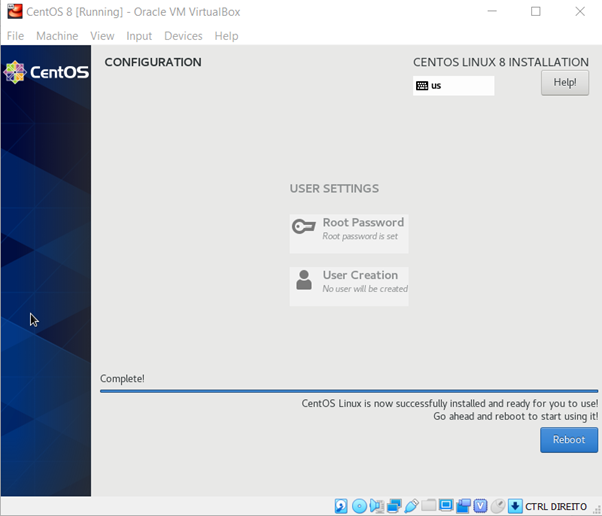
It will take time. Sit back and watch the installation operation.
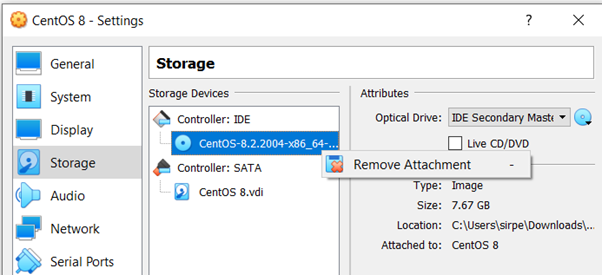
After a few minutes, click on “Reboot” button to start the operating system. At this moment, you need to remove the disk of the CentOS, if not, a new installation can start. To do this, stop the virtual machine at the first start after the installation process. For this, click on “Options”, “Storage” and over the Controller: IDE click on “Remove Attachment”.
Step 3
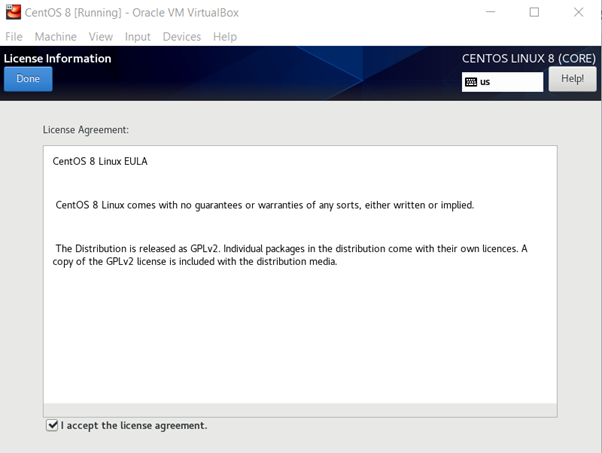
After finishing the initial setup, you need to execute some additional steps. First, you need to accept the OS EULA.
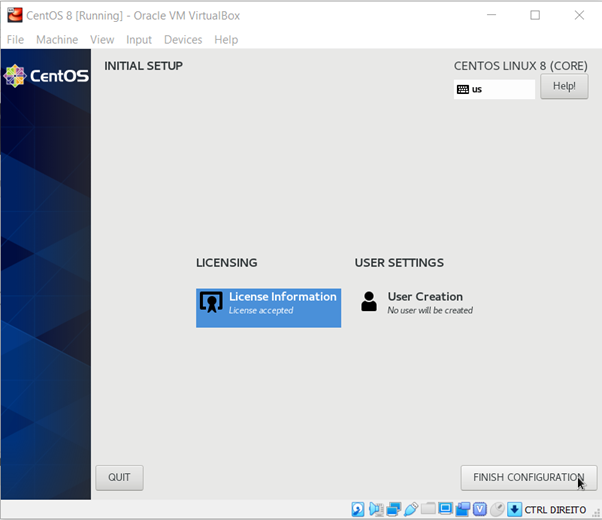
Next, you can finish the configuration steps.
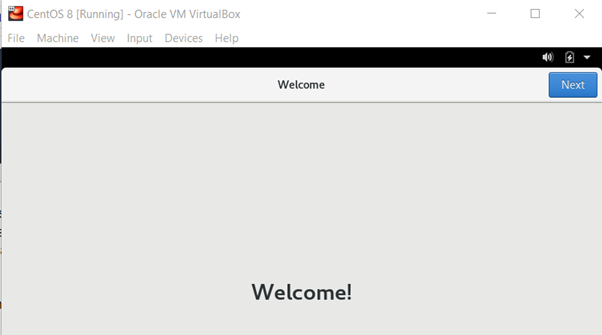
You will see the welcome screen. Click on “Next” to proceed and configure the settings as desired.
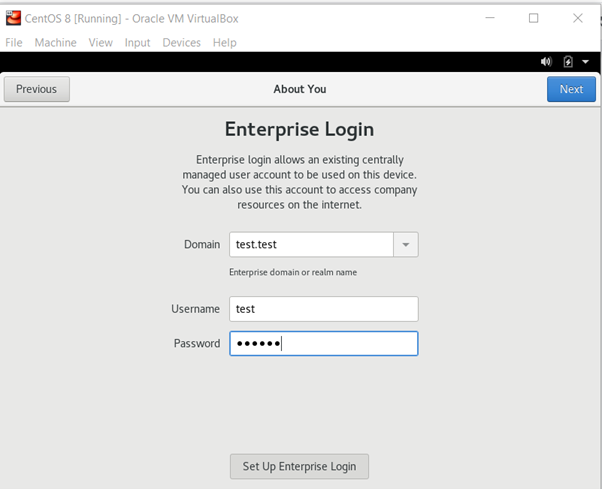
In the next step, you need to configure the enterprise login. Add the domain of the business, a new user and password.
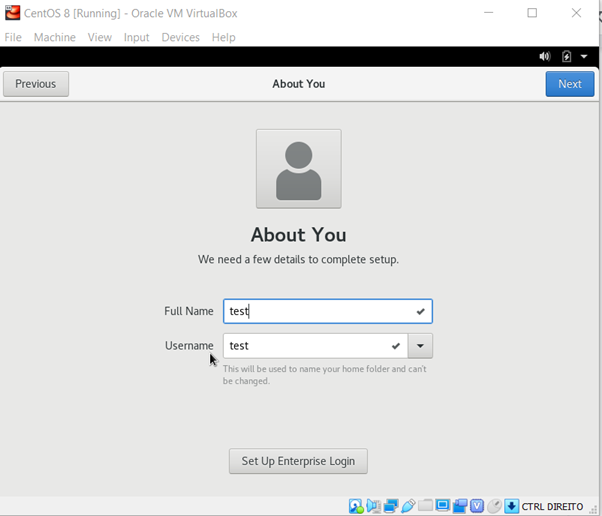
After that, configure your home folder.
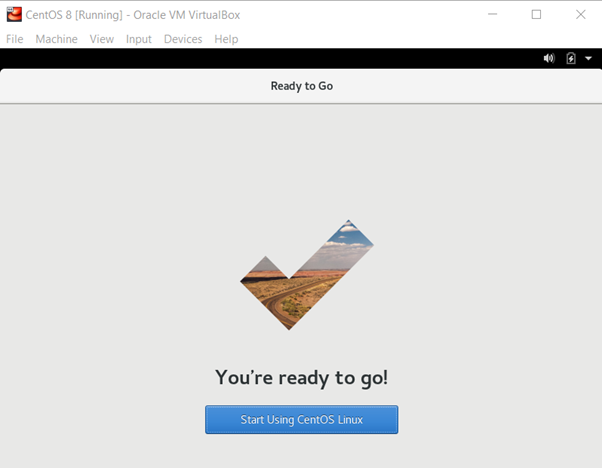
Click on “Start Using CentOS Linux” and then log in, using your credentials.
Next, click on Activities and select on the left-side Terminal.
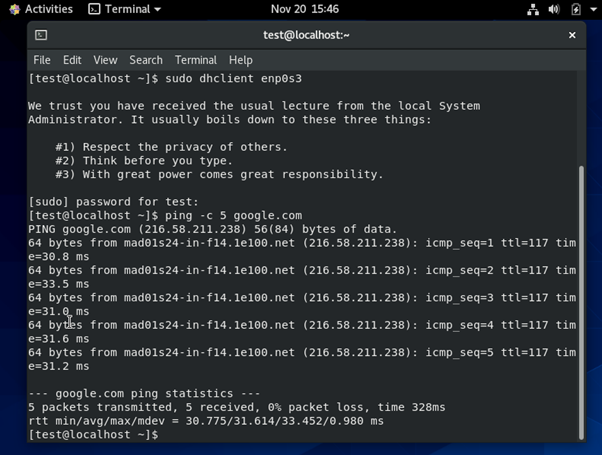
Now, you need to get an IP address. To do this, you need to execute the following command:
dhclient enp0s3

What should you learn next?
Now, try to ping google.com as follows:
$ ping -c 5 google.com
As you can see, internet connectivity works.
On your terminal, hit the following command to get the entire repository installed:
# yum install epel release
EPEL (Extra package for Enterprise Linux) is an open-source and free repository. It provides 100% high-quality add-on software packages for Linux distributions including Red Hat, CentOS and Fedora.
Finally, enjoy your CentOS installation!