An Insight into Virtual Private Networks and IP Tunneling
Introduction
In the world of Cybersecurity today, staying ahead of the hacker is the name of the game. It seems like that for one every one step that is taken forward with regards to protecting critical infrastructure of a business or a corporation; it seems like that the hacker is always two steps ahead. Probably one of the best instances of this is the newest phenomenon known as "Bring Your Own Device," or "BYOD."
This is when a business entity totally goes outside the realm of its established Security Policies and allows its own employees to use their own Smartphone or Wireless device to engage in and engage in work related tasks.

FREE role-guided training plans
Of course, this has benefits to it, especially for the employee that is constantly on the road, traveling. However, there are the obvious inherent security risks as well. Probably the biggest one is if the employee has actually "hardened" their Smartphone or Wireless Device with all of the necessary, protective mechanism.
If it is not compatible with the businesses' or corporation's Security Policies, then this is one of the surest ways that a Cyber attacker will find his or her inroads into the defense perimeters of the business entity.
In fact, BYOD is still such a new concept that many businesses and corporations are still embracing and trying to implement it the best that they can into their Security Policies. Thus, that is why employees are often left to figure out on their own how they have to configure the security on their Smartphone or Wireless Device.
Our last series of articles focused on the science and technology of using Cryptography. In the simplest terms, this is used to scramble a message from a sending party to a receiving party. Then, as the message is received, it is then descrambled into a decipherable format, using the right combination of "keys."
The added benefit of using Cryptography is that if this particular message were to be intercepted and hijacked by a malicious third party, it would still be rendered useless (unless of course, the hacker has some advanced knowledge of the keys which are being used).
Cryptographic based infrastructures can range from the simplest (such as that of the Symmetric Cryptographic one) to the most complex (such as that of the Public Key Infrastructure, which is an offshoot of the Asymmetric Cryptographic one).
When a Cryptographic based infrastructure is used, some of the most complex Mathematical Algorithms are also employed to fortify the strength of the keys further. Some of the strongest ones in this regard include those of the RSA Algorithm, the Diffie-Hellman Key Exchange, and the Elliptical Wave Theory.
However, another more popular (and even perhaps more sophisticated) approach to securing the lines of communications between a sending and receiving party is to use what is known specifically as a "Virtual Private Network," or "VPN" for short. In this article, we introduce this concept, with an emphasis on the following topics:
- What a Virtual Private Network Is
- IP Tunneling
- Mobile VPNs
What the Virtual Private Network Is
The Virtual Private Network is a much more sophisticated methodology of protecting the integrity of the Ciphertext when is sent all the way from the sending party to the receiving party, and vice versa. This type of mechanism is highly specialized, with the main intention of highly securing the flow of communications between all of the entities which are involved in the communications process. A diagram of a Virtual Private Network can be seen below:
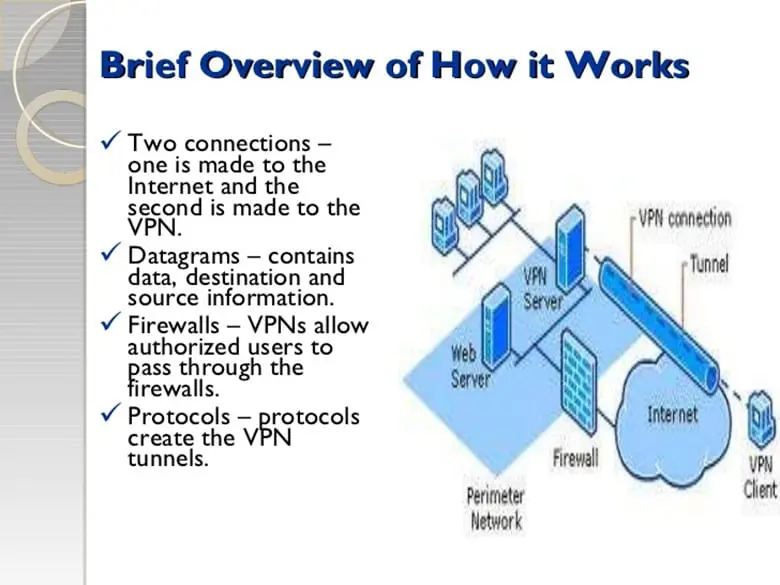
In its simplest form, the Virtual Private Network takes the Data Packet in which the Ciphertext resides in (it is important to note that the Ciphertext cannot be just sent by itself it needs to have a vehicle in which to travel across the network medium, which is namely the Data Packet).
The encryption which is used in a Virtual Private Network involves the use of another Data Packet. Meaning, the Data Packet in which the Ciphertext resides in is further wrapped inside by another Data Packet, thus providing an extra layer of protection. This process is known technically as "Encapsulation."
Once this process has been accomplished, the Virtual Private Network then establishes a dedicated network based connection (or even a dedicated network channel), in which the encapsulated Data Packet can be sent.
Although this specific type of connection uses a public network infrastructure and related systems, the special type of network connection that is established and used by the Virtual Private Network cannot be seen by others, and it cannot even be picked up by the most sophisticated of Network Sniffers.
IP Tunneling
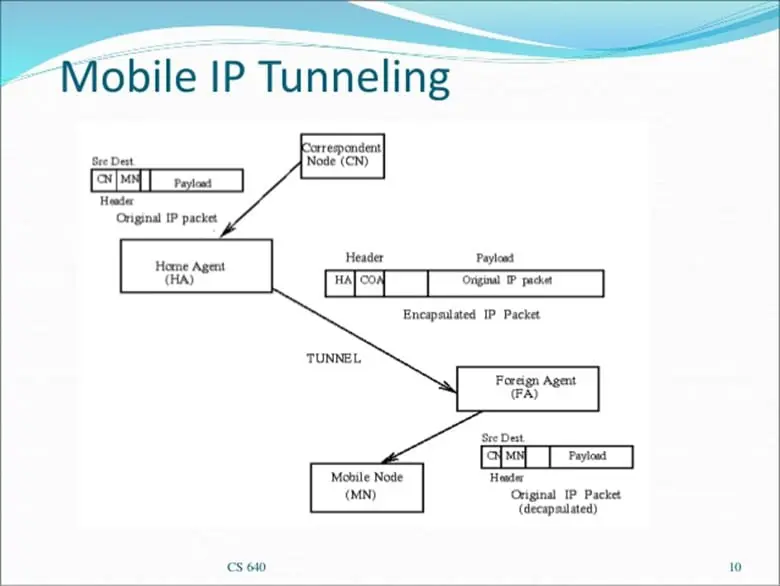
The establishment of this special type of network connection by the Virtual Private Network is known technically as "IP Tunneling." The following example demonstrates how the scheme of IP Tunneling works.
First, assume that there is an employee of a business or a corporation with a tablet/Smartphone or other Wireless device and he or she wishes to connect to an internal server which is located deep within the corporate network infrastructure.
Let us further assume that this particular device possesses a TCP/IP Address of 12.32.24.38 and that the corporate server the employee wishes to gain access to has a TCP/IP Address of 192.168.1.1; and that another public mechanism can not access it.
For the employee's device to the internal corporate server, it must first generate a Virtual Private Network Firewall that has a public address of 10.12.11.13 as well as possessing a private TCP/IP Address of 192.168.1.2. To fully establish the connection between the employee's device and the internal corporate server, a specialized Virtual Private Network tunnel must first be established.
The following steps are required to accomplish this task:
- The Virtual Private Network client will connect to the VPN Server/Firewall through a specific network interface.
- The VPN Firewall/Server will allocate a brand new TCP/IP Address (such as 192.170.60) from the Virtual Private Network's Server/Firewall subnet. This particular technique creates the "virtual tunnel" through which the encrypted Data Packet can reach the end of the other VPN tunnel endpoint.
- Now, when the individual's device (which now becomes termed the "VPN Client") wishes to communicate with the corporate server, it prepares its Data Packets to be sent over the TCP/IP Address pf 192.168.1.1, and then they are further encrypted as well as encapsulated with outer Virtual Private Network packet (such as that of the IPsec Packet). From here, it then relays extra fortified Data Packets to the VPN Firewall/Server with the public TCP/IP Address of 10.12.11.13 over the public Internet. This extra layer of protection is so well encrypted that even if a Cyber attacker were to intercept these particular Data Packets, there is nothing that they can do to reverse engineer the Data Packets to garner the confidential information and data which resides in them.
- In this last stage, when the encapsulated Data Packets reach the Virtual Private Network Firewall/Server, it then extracts the inner Data Packets, decrypts them, and then further notes the destination TCP/IP Address is 192.168.1.1, which is the actual corporate server. From this point onwards, these particular Data Packets are the sent to the corporate server.
This is the process of how this particular employee's device can be reached, connected, have access to, and communicate with the corporate server. As one can see, the beauty of the Virtual Private Network is that to an outsider (such as a malicious third party), it looks and appears as if the communications of the Data Packets is transpiring across the same network segment. However, in reality, the actual and real communications takes place across hidden, secret, and covert communications paths.
Mobile VPNs

As the explosion of Smartphones, Tablets, and other forms of wireless devices take root in today's world, and especially in the business/corporate setting, the use of Mobile based Virtual Private Networks will also proliferate at an equal pace.
The traditional Virtual Private Network model is a stationary one, meaning that it can only be used in one particular geographic location at a time. However, in today's wireless world, stationary Virtual Private Networks and the technology which is associated with them simply will not be able to keep up with the quick pace of mobile technology.
Another perfect example of this is that of mobile devices used by the law enforcement agencies. Today, these entities are equipped with various types and kinds mobile devices which allow them to confirm the identity of the suspect of whom that they have apprehended. However, rather than using the traditional ink and paper approach, Biometrics are now being used to provide a quick determination and turnaround time for the identification of the apprehended suspect.
In these particular mobile applications, the endpoint of the Virtual Private Network is not fixed upon and located at a single TCP/IP Address; instead, the Virtual Private Network connections roam across the various networks such as the data networks from the cellular carriers or in between the multiple Wi-Fi access points.
In these cases, of the traditional Virtual Private Network models were to be utilized, the respective Virtual Private Network connections would get continuously broken at each different location.
From this point onwards, the mobile Virtual Private Network software handles the necessary network authentication and maintains the network tunneling sessions in a way that is completely transparent to the mobile application and the end user (such as the employee of the business or corporation).
Conclusion
To the very large multinational businesses and corporations, the ability to afford a high-end Virtual Private Network comes is not difficult at all. However, for the small to medium sized businesses, obtaining a high-end Virtual Private Network solution can be a very expensive proposition to undertake, as this can be an extraordinary drain on any IT budget.
However, as the world is now turning more towards the use of mobile-based Virtual Private Networks, these types of business entities, whether they want or not, will have to implement it no matter what to mitigate against Cyber-attacks.
In the next article, we will examine how to conduct a Benefit-Cost Analysis for implementing a Virtual Private Network, and the variables which are associated with actually deploying one.
Resources
http://www.cse.wustl.edu/~jain/cis788-99/ftp/h_7vpn.pdf
http://ptgmedia.pearsoncmg.com/images/1587051796/samplechapter/1587051796content.pdf
http://www.cisco.com/networkers/nw00/pres/2400.pdf
http://documentation.netgear.com/reference/fra/vpn/pdfs/FullManual.pdf
http://www.net130.com/tutorial/cisco-pdf/1IP_Tunneling_and_VPN_Technologies.pdf
http://homepage.smc.edu/morgan_david/linux/n-protocol-10-ipip.pdf
ftp://ftp.hp.com/pub/networking/software/A-C09-GRE_Tunnel.pdf
http://floppsie.comp.glam.ac.uk/Glamorgan/gaius/networks/9.pdf

What should you learn next?
http://www3.cs.stonybrook.edu/~samir/cse590/mobile-routing.pdf









