How to protect files with canary tokens
We are living in a world where terms such as data breach, vulnerability and cyberattack have been headlines. The number of vulnerabilities doesn't stop growing and we only have to look back at the year 2018 to see that.
According to CVE Details, a free CVE security vulnerability database/information source, 16,555 vulnerabilities were addressed in 2018. Last year established a new record — an indicator that should be kept in mind for 2019.
The number of problems are on the rise due to the fast growth of technology and the number of devices connected to the Internet. According to statista.com, 23.14 billion IoT devices were connected to the Internet in 2018.
This article provides some hints and tricks on keeping data away from hackers. However, we will not describe an approach to stop the exploitation of vulnerabilities and the leak of information. Instead, a method based on canary tokens can be used by developers and IT professionals to receive alerts when something strange happens in their infrastructures and applications.
What are canary tokens?
Canary tokens, also known as honeytokens, are not new but can be useful as a source of information. They can be understood as unique identifiers that can be embedded in different places. If they are touched, an alert is triggered.
We can use canary tokens in different scenarios:
- Embedded into applications to help in reverse-engineering detection
- Detect when someone triggers the canary by activating the token (for example, via a “target file” especially dropped in a private folder. When this file is accessed by an unauthorized user, an alert is generated)
With this simple approach, it’s possible to create a track log on something. Based on the Canarytokens platform available at GitHub, we will perform four use cases below in order to demonstrate its total functionality and usability.
Use cases based on canary tokens
Setting up the tokens is very easier. All we need to do this is enter an email address and a description, set the type of token that we want and generate it.
The uses cases presented in this article are:
- Get an alert when a PDF document is accessed
- Get an alert when a Windows folder in browsed in Windows Explorer
- Trigger an alert when a website is cloned
- Obtain an alert when an application is reversed
1. Get an alert when a PDF document is accessed
This can be achieved by placing a token in the document met-data, giving us a reliable ping when the document is opened. The  Canarytokens platform generates both a Word and a PDF document.
Canarytokens platform generates both a Word and a PDF document.
So we can drop the file on a Windows network share or leave the file on a Web server in an inaccessible directory to detect possible breaches.
As a next step, we need to create a new canary token and drop the generated file in a protected directory in a Microsoft Windows operating system: c:unautorized_directorypasswords.pdf.
When someone accesses and opens this file (e.g., an adversary), an alert is triggered.
The token reminder is also described in the email in order to identify its origin. Note that this information was input during the creation of the canary token.
By clicking on “Manage this Canarytoken here,” the operator can disable the canary token. When the link “More info on this token here” is clicked, the user can access a page where more information is presented.
 Note that it is also possible to export all the data in a JSON or CSV file format.
Note that it is also possible to export all the data in a JSON or CSV file format.
2. Get an alert when a Windows folder is browsed in Windows Explorer
This kind of token can be used in some cases, such as:
- Unzip the file on a temptingly-named Windows network share
- Unzip the file on the CEO's laptop on a folder on their desktop in order to detect suspicious access attempts
To carry out this task, we need to create a folder named “protected” in the C: drive.
 Windows provides an even better way to get notified, in the form of the venerable old desktop.ini configuration file. Dropping a desktop.ini file in a folder allows Explorer to set a custom icon for a file. Since this icon can reside on a remote server (via a UNC path), using DNS we can effectively make use of a token as our icon file.
Windows provides an even better way to get notified, in the form of the venerable old desktop.ini configuration file. Dropping a desktop.ini file in a folder allows Explorer to set a custom icon for a file. Since this icon can reside on a remote server (via a UNC path), using DNS we can effectively make use of a token as our icon file.
[.ShellClassInfo]
IconResource=%USERNAME%.%USERDOMAIN%.INI.kdh1.canarytokens.comresource.dll
This configuration allows the generation of a notification any time someone browses the directory in Explorer and can prevent data breaches or unauthorized accesses.
3. Trigger an alert when a website is cloned
Canary tokens can also be used to detect when a website is cloned by an adversary. For that, we need to access the platform and pick the option “Cloned Website.”
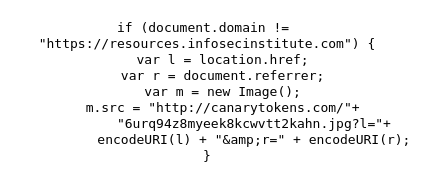 The canary token server can also send a notification if a Web page is copied (and hosted on another top-level domain). This is usually the first step in a well-executed phishing campaign. By clicking the “Create my Canarytoken” button, this snippet of code is presented. You can see our example to the right, using our example website.
The canary token server can also send a notification if a Web page is copied (and hosted on another top-level domain). This is usually the first step in a well-executed phishing campaign. By clicking the “Create my Canarytoken” button, this snippet of code is presented. You can see our example to the right, using our example website.
The generated source code is very simple to understand:
- Load in client browser
- Check if URL is https://resources.infosecinstitute.com
- If not, it loads the canary token and generates a new alert
When someone clones the website, they'll include the JavaScript. When the JavaScript is run, it checks whether the domain is expected. If not, it activates the token and an alert is triggered.
To make it difficult to "detect" by hackers, we can:
- Run the script through an obfuscator to make it harder to pick up
- Deploy it on the login pages of your sensitive sites, such as OWA or tender systems
4. Receive an alert when an application is reversed
By reversing an application such as a Java application, an APK or .NET executables, attackers can access data embedded in that files. This data may include API keys, secret keys, passwords and other sensitive information.
 To do this, we can use a URL encoded or even obfuscated with base64. With this trick, it looks like a legitimate website URL, causing the attacker to click on the URL and triggering the alert.
To do this, we can use a URL encoded or even obfuscated with base64. With this trick, it looks like a legitimate website URL, causing the attacker to click on the URL and triggering the alert.
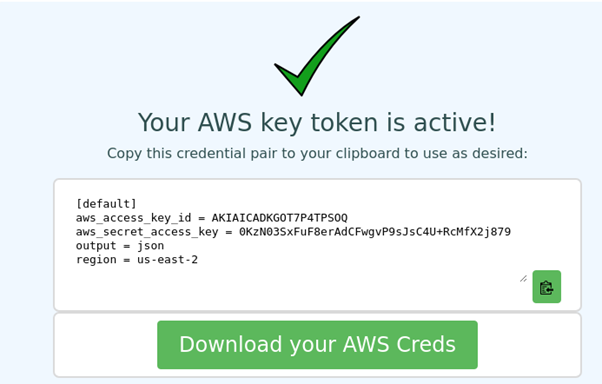
The Canarytokens platform has a feature that can be used to generate AWS S3 tokens. Let’s use it.
This canary token is triggered when someone uses this credential pair to access AWS programmatically (through the API).
The key is hyper-unique: There is zero chance of somebody having guessed these credentials. If this token fires, it is a clear indication that this set of keys has "leaked."
Ideas for use:
- These credentials are often stored in a file called ~/.aws/credentials on linux/OSX systems. Generate a fake credential pair for your senior developers and sysadmins and keep it on their machines. If someone tries to access AWS with the pair you generated for Bob, chances are that Bob has been compromised
- Place the credentials in private code repositories. If the token is triggered, it means that someone is accessing that repo without permission
Bonus: How to detect when a file is “infected” with canary tokens
PDF and DOC files are extremely useful to prevent unauthorized access in a server or directory. However, this approach can be used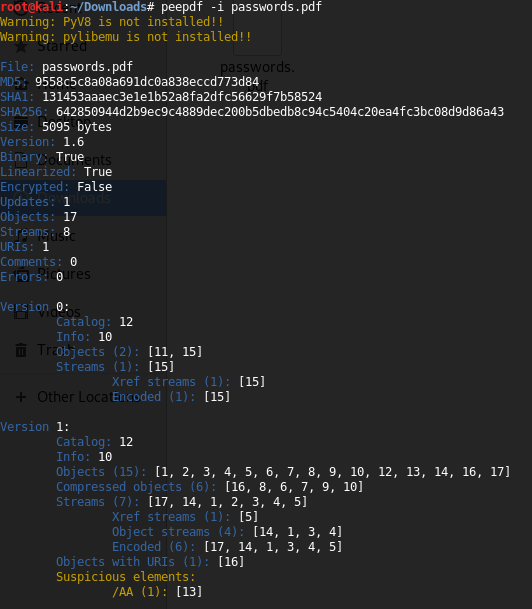 offensively by criminals as well.
offensively by criminals as well.
It’s possible, however, to detect if a particular PDF file has a canary token embedded in its metadata. To detect that, we can use the platform to generate a token and download the target PDF. We decided to fire up peepdf to analyze the internals.
Some of the top features of peepdf are:
- Analyzes a PDF document
- Extracts data objects & streams
- Extracts metadata
- Extracts data from encoded and encrypted files also
- XML outputs provided
- Interactive console (-i option)
To start this task, we used a Kali Linux distribution. Next, we type the following command in the terminal: peedf -i passwords.pdf.
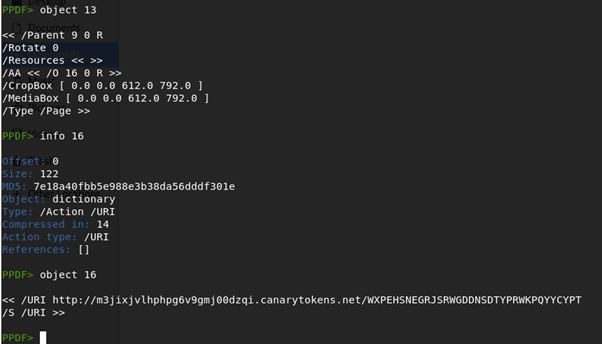
As can be seen, the PDF version is 1.6. Peepdf has detected a suspicious element, /AA, so that will definitely be the first object we want to investigate.
To understand a little more about the structure of a PDF, we need access V1.6 PDF Specification to see what the /AA and other elements are.
Basically, it is an additional-actions field defining actions to be taken in response to various trigger events. We need to take a look at the object.
At this point, we can see a line reading /AA << /O 16 0 R >>, which we assumed is referring to object 16.
Object 13 has a /AA content embedded, and that represents a suspicious indicator. Next, we will examine this reference by typing info 16 in the terminal (metadata from object 16).
This object records an URL that refers to the Canarytoken platform and was generated when the file was created. This token is triggered any time that file is opened.
Conclusion
Canary tokens are a free and quick methodology to help defenders discover they’ve been breached by having attackers announce themselves.
Notice that data breaches happen from organizations to governments, and critical data can be exfiltrated without user knowledge. Keep in mind that many data breaches are identified weeks or even months after the initial violation. Preventing this problem is essential in order to keep data safe and away from criminals.
Hackers typically focus on personal data such as passwords, emails, contacts, credit cards, customer lists, strategic plans, bank account data and more.
However, canary tokens can also be used offensively to get information from an organization you are targeting on a Red Team assessment. For example: Consider creating a word document with your CV inside it and sending it over to the HR department. When they open the file, the token is triggered and will return the domain and username of the “victim.”
In general, there are many scenarios where canary tokens can be used in both a defensive and offensive landscape.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
Sources
- Canarytokens by Thinkst, Thinkst Canary
- Canarytokens, GitHub
- Canary Tokens, RedPacket Security
- CanaryTokens, StationX
- Palavras-passe e Honey Words, Segurança Informática