Fitting cyber attacks to jus ad bellum — Instrument-based approach
Introduction
The coming of new technologies is challenging to many fields of human activity. In particular, there is a discrepancy between IT and the laws that regulate armed conflicts. It seems that legal frameworks, such as that stipulated by the UN Charter, are a little bit outdated in the context of cyber attacks. Nevertheless, one must realize that this is the lex lata, or existing law, and that there are useful theories and methods which may assist in diminishing the discrepancy.
Speaking of useful theories and methods, there are three main approaches that address this problem and attempt to make cyber attacks conform to jus ad bellum norms. These are:
- Instrument-based approach
- Target-based approach
- Consequence-based approach
For the sake of completeness, it should be noted that there are other theories, for instance, Actor-based and criminal law methodology, but now we will focus on the principal ones.
I. What is jus ad bellum? Purposes, prerequisites and how it relates to cyber attacks
Generally speaking, jus ad bellum, which means literally in Latin "right to war," is part of the just war theory and it determines the situations when is lawful to resort to war. Its main purpose is to maintain international peace and harmony within the community of nations.
The jus ad bellum nowadays is governed by the UN Charter and customary international law (e.g., necessity and proportionality principles), a legal body that gradually emerged prior to drafting the UN Charter (National Research Council, 2009). The most applicable jus ad bellum provisions are Article 2(4) /prohibition of the use of force, Article 51 /the right of self-defense, as well as Articles 39, 41, and 42.
Jus ad bellum norms regulate only international relations, more specifically a situation of conflict between two or more states. Hence, for a state to invoke some of the aforementioned articles, there should be a given war-like act against one state duly attributed to another state. It worth noting, however, that with respect to cyber warfare, the jus ad bellum body is applied by analogy. In other words, because it is not devised specifically to regulate these events, they may not fit perfectly into this legal framework.
In fact, one legal team supports this fact: "while the law of war provides useful guidelines for addressing some of the most dangerous forms of cyber attack, the law of war framework ultimately addresses only a small piece of full-range of cyber-attacks" (Hathaway et al., 2012, p. 840).
Although the assertion is perhaps 100% truth, this contribution may yet hold some value for evaluating the acts, whether cyber or not, that fall within the jus ad bellum ambit.
II. Jus ad bellum Force and Armed Attack
For the sake of good analysis, we should begin with key jus ad bellum notions such as the use/threat of force and armed attack. Once their meaning is clear, switching to cyber warfare will probably be less complicated.
The Jus ad bellum 'Force' Notion

Provisions of interest:

The point of departure for any interpretive Endeavour in the realm of law is the text of the treaty/provision in question. In this regard, the Vienna Convention on the Law of Treaties stipulates:
Article 2 (4) of the UN Charter expresses a prohibition which is both ambiguous and straightforward. Its complex nature predisposes to a trident analysis of one of the most important components–force:
Fig. 1:
Trident Interpretation of the Use of Force
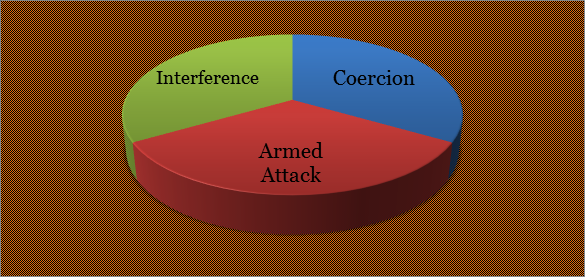
Force as Kinetic Armed Attack
The overwhelming majority of theorists and scholars find that the meaning of "force" is more or less equivalent or synonymous to kinetic armed force (Melzer, 2011). However, the textual distinction between "force" and "armed" that one can discern in the UN charter preamble ("armed shall not be used"), Article 41 (armed force is excluded from non-forceful measures), and the exception on the use force (Article 51) serves as evidence that the notion of "force" is "broader in scope than the common understanding of the term" (Schmitt, 2011, p. 574).
Moreover, the UN charter's negotiation history and the discussion of various means throughout the document strongly suggest that the drafters had an intention to regulate kinetic armed force otherwise and more strictly than the rest of coercive instruments (Waxman, 2011).
Force as Coercion
Although admittedly expansive in range, a faction of specialists in the area of international law suggests that the use of force should include other forms of coercion—political and economic— instead of just focusing on kinetic armed force as the only instrument of coercion.
While at first the United States and its Western allies pushed for adoption of the narrow, verbatim definition of force revolving generally around military attack events, the developing countries, many from the Eastern bloc, sought the broader interpretation, which covers, as mentioned, a prohibition of force grounded on political or economic coercion (Waxman, 2011).
On the other hand, given today's military superiority, and at the same time, the indispensable dependence on information technology of the leading nations, it comes as no surprise that less advanced states attempt to shorten the margin by incorporating asymmetric warfare which may change valence as overall—a trend necessitating different behavior from these leading countries, namely, a demand for a more expansive reading of Article 2(4) in the event of cyber attacks (Hathaway et al., 2012).
If nothing else, this is a good demonstration of how states tend to make a 180-degree turn in their policy when the wind of change starts to blow.
Force as Interference
A third and final possible approach to interpreting force would lay a special emphasis on the states' right of sovereign dominion. The rights the states exercise on their territory and the obligation of other states to respect their domain are the leading credos of this concept. Improper interference with the right of the states often takes into account the object and specific type of states' actions, not the means (Waxman, 2011). Infiltration, propaganda, and subversion are examples of such acts.
Explanation for limiting use of force to specific occurrences
The primary purpose of the UN Charter is to maintain international peace and security and, as set out in the preamble, "to save succeeding generations from the scourges of war." Success in this department would be highly inconceivable if the UN charter is allowed to be circumvented by the use of non-violent methods and means (Melzer, 2011).
As apparent in not one or two treaties, ICJ decisions, and UN resolutions, less grave forms of force are condemned by the international community, as well. For instance, interference with a state violates the customary international norm of non-intervention (O'Connell, 2012). However, it does not do so with respect to Article 2 (4).
In summary, the foregoing analysis more or less supports the assertion that the prohibition of threat or use of force includes kinetic armed attack, but excludes economic and political coercion. The UN charter text and travaux preparatoires (negotiation history)
back up this position. At the same time, the use of force scope is not to be equated precisely with armed attack (Schmitt, 1999).
Fig. 2: Use of Force
Charter text, intent, travaux preparatoires, and Nicaragua case
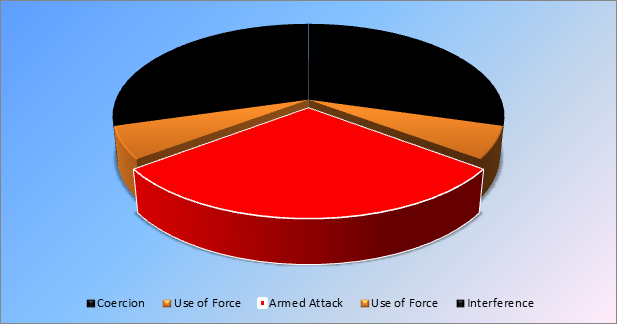
Hint:
In
Armed Attack + Additional UoF
margin; Out Less grave forms
The Jus ad Bellum "Armed Attack" Notion

Provision of interest:
Armed attack, in accordance with Article 51, a norm based on the foundational customary concept of self-defense, is the only exception to the prohibition on the use of force. As we have seen from the previous part, the "use of force" and "armed attack" stands in peculiar correlation. To continue further the interpretation efforts from "Force as Kinetic Armed Attack," we must scrutinize in detail the intentional dichotomy of these two notions.
For an empirical base, the verdict and complementary documents from the Nicaragua case should be used.
A. The following text is of significance to our current analysis:
…while the arming and the training of the contras can certainly be said to involve the threat or use of force against Nicaragua, this is not necessarily so in respect of all the assistance given by the United States Government. In particular, the Court considers that the merely supply of funds to the contras, while undoubtedly an act of intervention in the internal affairs of Nicaragua…does not in itself amount to a use of force
(Nicaragua case, 1986, par. 228).
Apparently, the judgment is that shady activities such as training or arming guerrillas constitute use of force, but at the same time fall short of armed attack. As a result, Schmitt draws the conclusion that "the threshold for a use of force must therefore lie somewhere along the continuum between economic and political coercion on one hand and acts which cause physical harm on the other" (Schmitt, 2011, p. 575).
Fig. 3:
Use of Force / Armed Attack correlation
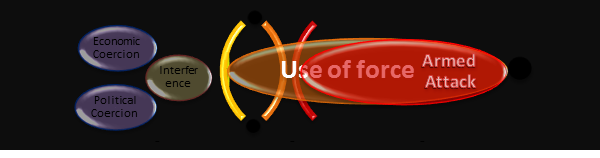
Additionally, it would probably mean that by analogy even a non-destructive, in terms of physical integrity, cyber attack may be classified the same way.
B. Also with a tight relation to the first point, the ICJ provides really crucial determinations about some ambiguous questions concerning the notions under discussion, which represented a legal conundrum in this concrete case. For instance, the court contends that "measures which do not constitute an armed attack may nevertheless involve a use of force" (Nicaragua case, 1986, par. 210). As a result of this finding, ICJ goes on to ascertain that only the "most grave forms of the use of force" (Nicaragua case, 1986, par. 191) should rise to the magnitude of armed attack as in Article 51 (Schmitt, 2011), a distinction based on a sufficiently justified "scale and effect" criterion (nevertheless vaguely prescribed) (DeLuca, 2013).
Fig. 4:
"Most Grave Forms of Use of Force"
('Scale & Effects')
This entire line of reasoning was made for one important purpose—merely to display the premeditated discrepancy between two corner-stone terms with respect to the jus ad bellum. In recognizing the gap between use of force and armed attack, ICJ acknowledges that guiding principles are not to rely on the particular instrument of force employed, or at least not as a prime model. Instead, a model which seeks to envisage the "scale and effect" should have dominance.
To conclude the "armed attack" matter, the term by itself presupposes the use of a weapon. In another opinion by ICJ, the court makes clear that Articles 2(4), 42, 51 of the UN Charter apply "to any use of force, regardless of the weapons employed" (ICJ, 1996, paras.37-50) —just another indirect affirmation that cyber warfare pertains to jus ad bellum (Melzer, 2011).
III. Instrument-Based Approach
This approach represents actually the classical inquiry of whether a particular act amounts to an armed attack as in Article 51 view, however, through the prism of cyber attacks. The exact point of interest is confined to the particular instrument of use of force—military kinetic force. Thus, the solely existence of this occurrence is the only precondition to qualify this act as an armed force.
Under this methodology, a cyber attack is considered an armed attack only if it employs conventional military weapons. Hence, provided that bombing Internet cables or computer servers is of sufficient gravity, the act could fall within the meaning of the instrument in question, namely, an armed attack (Hathaway et al., 2012).
The instrument-based approach holds that cyber attacks do not rise to "armed force because it lacks the physical characteristics traditionally associated with military coercion (Hollis, 2007, p. 1041)".
Legal reasoning in support of the instrument-based approach:
Article 41 UN Charter
Some scholars ascertain that by enumerating measures not involving the use of armed force such as "the complete or partial interruption of telegraphic, radio, and other means of communication," Article 41 of the UN Charter indirectly underpins the logic embedded in an instrument-based approach (Hollis, 2007). Therefore, other forms of aggression suit better the requirement of an act to constitute an armed attack under the UN Charter, because of the presupposition that most cyber attacks' magnitude or purpose is only to cause disruption or inconvenience to certain means of communication—for example, a powerful DDoS attack directed against a website in attempt to incapacitate it (DeLuca, 2013).
Definition of Aggression
Some support for the instrument-based approach, nonetheless in implicit fashion, stems from the U.N. General Assembly's Definition of Aggression. Instrumentality expression could be drawn from the list containing a number of deeds that would be taken as "aggression" under Article 39 (presumably, a term having a broader meaning than armed attack as in Article 51). What all of these acts have in common is that they all are associated with the use of military weapons or force. In addition, in its official policy, NATO has adopted this view as well (Hathaway et al., 2012).
Real/Fictive cases and Instrument-Based Approach
The uncomplicated character of this methodology would simply rule out cyber attacks, since these activities do not possess the traditional kinetic characteristics of a conventional military attack. Therefore, the instrument-based approach would not apply, for instance, to cyber attacks such as those on Estonia's information infrastructure, the South Ossetia's Russian against Georgia conflict, the Stuxnet worm that struck down the centrifuges at the Natanz nuclear plant, the alleged governmental attacks on WikiLeaks, or cyber attacks with the participation of non-state actors such as terrorist organizations. As a result, under the instrument-based approach, these real life cyber cases would constitute neither a use of force nor an armed attack within the UN Charter's regulation (DeLuca, 2013).
Furthermore, it seems that the application of the instrumentality approach would dispense with the prohibition on the use of force in relation to cyber attacks directed against communication systems. With the horrific 9/11 scenes appearing before our very eyes as a flashback to these tragic events, it will not be arduous to imagine the downing and crushing of airplanes into the ground or buildings, a disastrous aftermath of a cyber attack disabling an entire civilian air traffic communication system. Duncan Hollis (2007) then rightly poses the question of whether and why such an act will not qualify as a use of force or providing a viable opportunity to act in righteous self-defense. The author goes on further in the spirit of this rationale:
"In raising this possibility, I do not mean to suggest the downing of any civilian aircraft would otherwise qualify as a prohibited use of force. States did not regard Lockerbie incident as such, using a criminal law approach instead to try the two accused Libyan intelligence agents for their role in downing Pan Am Flight 103. At the same time, however, the possibility of IO (information operations) accomplishing results akin to that tragedy are not entirely theoretical. In 1997, a Massachusetts hacker shut down all communications to a Federal Aviation Administration control tower at an airport for over six hours" (Hollis, 2007, p. 1042).
Complementary Thoughts on the "Instrumentality" Doctrine
The promulgation of the UN Charter enforced this instrument-based paradigm of the use of force in which assessment of violation is to be made on the basis of the type of coercive instrument—military, economic, and political.
However, in spite of this instrument classification, in real life an economic embargo or major interference in the other state's foreign policy may frequently entail greater repercussions than a minor border incursion. Nonetheless, the instrument-based methodology would treat the former event as short force, and the latter as an armed attack (Schmitt, 1999).
In addition, while in the past it was relatively easy for experts to establish to which instrument certain nefarious activity pertains, the advent of the cyber attacks challenges this structure with its "refusal" to fit neatly to a certain type of instrument.
For these reasons, inter alia, many scholars suggest that the international community is more interested in the consequences of an act than its nature.
Reference List
DeLuca. C. D. (2013). The Need for International Laws of War to Include Cyber Attacks Involving State and Non-State Actors. Retrieved on 02/07/2013 from http://digitalcommons.pace.edu/pilronline/34/
Hathaway, O., Crootof, R., Levitz, P., Nix, H., Nowlan, A., Perdue, W., Spiegel, J. (2012).
California Law Review, 100 (4), 817-886.
Hollis, D. B. (2007). Why states need an international law for information operations. Lewis & Clark Law Review, 11, 1023-1061.
International Court of Justice (1996). The legality of the threat or use of nuclear weapons. Retrieved from http://www.icjcij.org/docket/index.php?sum=498&code=unan&p1=3&p2=4&case=95&k=e1&p3=5
Melzer, N. (2011). Cyberwarfare and International Law. Retrieved on 02/07/2013 from http://www.unidir.org/files/publications/pdfs/cyberwarfare-and-international-law-382.pdf
National Research Council (2009). Technology, Policy, Law, and Ethics Regarding U.S. Acquisition and Use of Cyberattack Capabilities. Washington D.C.: The National Academies Press.
O'Connell, M., E. (2012). Cyber Security without Cyber War. Retrieved on 02/07/2013 from http://jcsl.oxfordjournals.org/content/17/2/187.full.pdf?keytype=ref%2520&ijkey=T6J6KDRCRcHM4Ao
Schmitt, M. (1999). Computer network attack and use of force in international law. Columbia Journal of Transnational Law, 37, 885-937.
Schmitt, M. (2011). Cyber operations and the jus ad bellum revisited. Villanova Law Review, 56, 569-606.
United Nations (1945). United Nations Charter. Retrieved from http://www.un.org/en/documents/charter/
United Nations General Assembly (1974). Definition of Aggression Resolution 3314 (XXIX). Retrieved on 02/07/2013 from http://untreaty.un.org/cod/avl/ha/da/da.html
United Nations (1979). Vienna Convention on the law of the treaties. Retrieved from http://untreaty.un.org/ilc/texts/instruments/english/conventions/1_1_1969.pdf

What should you learn next?
Waxman, M.C. (2011). Cyber-attacks and the use of force: Back to the future of Article 2(4). Yale Journal of International Law, 36.










