Fitting cyber attacks to jus ad bellum — Consequence-based approach, Part III
1. Criticism and Possible Flaws of Consequence-Based Approach and Seven-Factor Test
There are people from the field of law, and not only from that field, who do not think that fitting cyber attacks to the law of resort to use of force with the help of consequence-based approach will go smooth as silk. One of them, Jason Barkham, is highly critical of Michael Schmitt's seven-factor test and the consequence-based theory as a whole.
Low-Level Cyber Attacks
To begin with, the comparison, analysis, and adherence of the conventional military force do not correspond well with the innovative form of warfare that cyber attacks represent. Moreover, Schmitt's method cannot cope properly with low-level cyber attacks because they are out of the use of force range under his analysis. In event of a real attack, the target would just have to guess whether its magnitude is significant enough (Barkham, 2001).
Presumptive Legitimacy Factor
On the other hand, the legitimacy factor has an improper function. The main question in a given case is whether a cyber attack is a use of force or a mere act of coercion—the former is illegitimate and the latter is legitimate, at least according to Article 2(4) of the UN Charter. Then, assuming that an act is legitimate in advance to establish at some point later whether it is force or coercion is devoid of sense. "In effect," Barkham (2001, p. 85-86) writes, "Schmitt's approach is backwards, because it requires determining the legitimacy of an attack under the international law (i.e., distinguishing between acts of coercion and uses of force) by asking whether the attack is legitimate."
Analysis after the Fact
Another important blemish is the consideration that cyber attacks "cannot be assessed readily at the time of the attack to determine their magnitude and permitted responses"
(Barkham, 2001, p. 86). Any framework that requires ex-post analysis would be ineffective to solve this problem. Adding to this fact the inherent feature of these types of aggression—the existence of severe obstacles in identifying the wrongdoer, a.k.a., the attribution problem—we can recognize the reason that would probably make waiting before responding imperative" (Barkham, 2001).
Because the consequences need to be ready available, a demand for accurate analysis of results under the methodology in question would necessitate the victim state to wait for the attack to commence. Undoubtedly, this prudent behavior would diminish considerably the chances for successful defense, especially if the attack is ongoing and the victim state needs to react immediately to protect itself. Therefore, a post factum analysis stands most likely no alternative due to the specific nature of cyber attacks, which can undergo quick modifications and in the matter of an instant can shift from an act having perfectly legal status to a severe violation of jus ad bellum (Ophardt, 2010).
The following statement comes as a direct continuation of the line of thought made in the previous point: "the greatest flaw in Schmitt's proposal" is its inability to cope with the flexible nature of cyber attacks—"states faced with a decision of how to respond to a cyber attack that could quickly morph into clearly aggressive act lack guidance on the appropriate response (Ophardt 2010 p. 24)."
Curiously, even the aggressor may not know exactly what kind of consequences are going to appear after a given cyber attack takes place. Consequently, the wrongdoer may have serious difficulties assessing the exact outcome of the attack and considering also all possibilities like secondary and tertiary effects (Hathaway et al., 2012).
Nevertheless, Sklerov speaks in defense of the consequence-based approach, ascertaining that "in no way does effects-based analysis require a state to delay its response until it can fully measure a computer network attack against all six of Schmitt's proposed axes. Decision-makers, at times, must make choice with imperfect information"
(Sklerov 2009: 70).
Additional Questions that Need Resolution
The application of consequence-based interpretation leads to the emergence of insidious secondary questions with regard to:
- Proportionality of an armed response — difficult to assess consequences and measure the eventual casualties
- Imminence — difficult to discern the onset of cyber assault and the fact that typically the attack sequences happens in split seconds
- Responsibility — calculation of attribution dilemma is inevitably bound to cause doubts about protagonist non-state actors with loose relationships to states
(Waxman, 2013)
Consequence-Based Approach and Politics
As one scholar notes: "Very challenging for lawyers applying an effect-based (consequence-based) analysis, it may not be quite so problematic in practice, because States are unlikely to respond to small-scale attacks with military force
(Waxman, 2013, p. 120)."
Political planners and decision-makers will have to face very challenging situations when they bid for domestic support for more drastic responses, that is, military actions against isolated cyber attacks which do not breed significant publicly discernible consequences.
By comparison with low-level hostile kinetic assaults, in those situations a counterattack is practically not only justified but demanded politically (Waxman, 2013).
2. Final Plea: Consequence-Based vs. Target-Based vs. Instrument-Based
Table:
The strong sides of each method
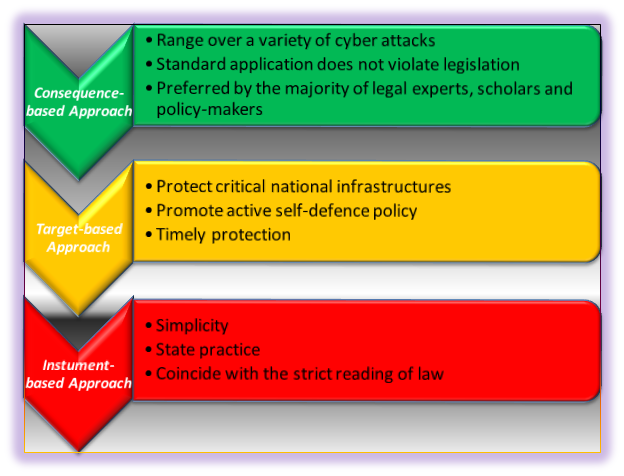
For the sake of breaking most of the stereotyped summaries, let us put the beloved "consequence-based" methodology in a defensive position on an imaginary witness box and then throw at it some accusations of "incompetence" when compared to the other two proposals that adjust cyber warfare to the jus ad bellum.
Arguments in Favor of Target-Based over Consequence-based
The following statement points to a defect in the consequence-based mechanism when it has to tune up national infrastructures from critical importance:
"A cyber attack that shuts down any part of a nation's critical infrastructure may have an effect that is much more debilitating than a traditional military attack. The threat in such a situation may be more terrorizing and harmful than a traditional military attack. Certainly, a country that is unable to use its banking system, or whose power grid has gone off-line due to a cyber attack, possesses legitimate claims for reparation, justice, and security. Because the consequentiality approach focuses on the same type of physical damage caused by a kinetic attack, it does not sufficiently protect critical infrastructure" (Stevens, 2009, p. 676).
Presumably, opponents generally criticize the consequence-based approach because it would be a useful tool only after the attack has really taken place. In addition, the unique character of cyber attacks predisposes decision-makers to take prompt reactions regarding ongoing cyber attacks and the consequence-based analysis would prove itself unreliable for dealing with these situations.
As noted before, in order to evaluate the consequences, the victim states should wait until they suffer real damages. Therefore, in situations of attack against critical national infrastructure many scholars advocate an immediate response, pointing out that it would be too risky to waste time assessing the magnitude of the attack while the vital critical national infrastructure is at stake (Sklerov, 2009).
Arguments in Favor of Instrument-Based over the Consequence-Based
While the instrument-based approach distinguishes itself with its relative simplicity of application and there a significant number of state practices and cases have been amassed, the situation with a probable promulgation of the consequence-based method may be unsatisfactory. The main problem perhaps would be unclarity and lack of state practice which eventually will lead, as Schmitt (1999) admits, to a grey area.
On the other hand, a resort to the instrument-based technique provides the interpreter with a standard with that makes it is easy to predict the nature of acts without impairing its internal coherence. The instrument-based approach allows for more consistent application of the acts in concordance with the already existing normative structure. Thus, this fact would lead us to the conclusion that the international community would be more inclined to adopt this method while the legal scheme is the same, mostly because this would avoid unwanted confusion and disputes (Schmitt, 1999).
Arguments in Favor of Consequence-Based
In order to transfer the exchange of arguments smoothly, we ought to begin with the consequence-based approach plea by saying that there is no question that the community did not seek to put a greater emphasis on the consequences. Simply for practical reasons, at the moment of drafting the UN Charter, it was perhaps more reasonable for the states to adopt a method which is more widely accepted and known (Schmitt, 1999). Back then it was the logical choice because the conflicts waged with conventional traditional weapons are simply identifiable and the instrument-based approach certainly gave a time-efficient result. Nevertheless, most of the scholars interested in studying cyber attacks and their significance in the arena of international law opine that since the cyber attacks have unique features that are not comprehensively covered by the legal mechanisms, another approach would bear better results than the obsolete instrument-based criteria (Hathaway et al., 2012).
Jonathan A. Ophardt (2010) thinks that Michael Schmitt's true belief about the original intention of the drafters is that they wanted to regulate the consequences of an armed attack between states. Instead, the drafters decided that a restriction on the means would be more convenient approach due to legal normative standards they needed to take into consideration. Consequently, "the interpretive dilemma" (Schmitt, 2011, p. 573) arises from the fact that in enacting the legal framework based on the instruments of force and coercion, the drafters sought to restrict also obliquely the consequences of these acts (Ophardt, 2010).
In support of this rationale comes a 1999 Assessment International Legal Issues in Information Operations made by the U.S. Defense Department:
"If we focused on the means used, we might conclude that electronic signals imperceptible to human senses don't closely resemble bombs, bullets or troops. On the other hand, it seems likely that the international community will be more interested in the consequences of a cyber attack than in its mechanism." (Defense Department, 1999, p. 18)
Right after this quote comes another one that highlights
the turning point in this line of thought:
"Yet, it is seldom the instrument employed, but instead the consequences suffered, that matter to states. At the time the Charter was drafted an instrument based approach made sense, for prior to the advent of cyber operations the consequences that states sought to avoid usually comported with instrument based categories. Cyber operations do not fit neatly into this paradigm because although they are 'non-forceful' (that is, non-kinetic), their consequences can range from mere annoyance to death" (Schmitt, 2011, p. 573).
Moreover, Schmitt argues that "scheme-imbuing consequences, rather than acts, with normative valence are nothing new" (Schmitt, 1999, p. 20). By way of example, here are several logical assertions that may back up analogously the supremacy of consequences over the acts themselves:
-
The prohibitions in Protocol I to the Geneva Conventions on starvation of civilians, infliction of "widespread, long-term and severe damage" to the environment [Article 55 (1) of Additional Protocol I], and attacks on facilities that "may cause the release of dangerous forces and consequent severe losses among the civilian population"
[Article 56 (1) of Additional Protocol I].
-
The Environmental Modification Convention ban on the utilization of any modified environmental tools and procedures for hostile purposes that may bring "widespread, long-lasting or severe effects" (1978, p.7).

-
The principle of proportionality [Article 56(5) (b) AP I] that seeks to balance the positive consequences as military initiative against the negative ones as superfluous death/injury to individuals or destruction/damage to tangible objects.
-
Even if a particular approach is forbidden by a certain international provision, usually the norm that approves the act has a consequence-based character (Schmitt, 1999).
Apparently, the consequence-based declaratory style predominates in the jus in bello design as well (Schmitt, 1999). Knut Dörmann in his paper "Applicability of the Additional Protocols to Cyber attacks" (2004) also centers his approach on the consequences, but he deems that an attack does not always have to bear violent consequences as death, injury of civilians or soldiers, or destruction, damage to tangible objects (Adler, 2011).
The Consequence-Based Approach—the Leading Guideline
If we take into account all these arguments, it would right away make sense that the predominant view of most experts privy to international law and IT (2009) supports of the consequence-based approach, defining it as "the best analytical model for dealing with cyber attacks" (Sklerov, 2009, p. 68).
To stand out in sharp contrast, this method includes the cases which the instrument-based framework regulates and, on top of that, it includes events of attacks that are non-kinetic. The consequence-based approach is also better than the strict liability analysis — the other denomination of the target-based approach — because it does not violate international norms and customs (Sklerov, 2009).
Admittedly, the current normative scheme cannot cope well with non-kinetic acts and perhaps "a new normative architecture" is required to take into account these acts. Applying the consequence-based approach may put policy-makers in a position in which the existing law needs an interpretation or needs an extension beyond what textually prescribes. Strictly speaking, that broad interpretation/extension beyond the current paradigm constitutes a new standard (Schmitt, 1999).
Others find that the jus in bello is well-established enough to adjust itself to new categories and means of warfare. The big problem with the cyber attacks is that they do not exist in a specific environment — they can cause both physical (hardware) and non-material damage (software) (Brown, 2006).
Nevertheless, a point should be made that even though the current jus ad bellum and in bello do not regulate cyber attacks well, they can still serve as "a model for devising rules." (Brown, 2006, p. 183) With respect to that "if the definition of a use of force is static, then the ban on the use of force gradually will become less effective as new interstate actions occur beyond the boundaries of what the drafters considered" (Bond, 1996, p. 29).
Conclusion
Although only a small number of interstate cyber attacks reach the high threshold, apparently applying the existing jus ad bellum norms to those cases could be very challenging. Again, fitting or adjusting these new forms of warfare necessitates a dose of interpretation skills mixed with a pinch of majestic improvisation and the talent to see the norms a bit out of their initial modus operandi.
Many deem that not only do the current jus ad bellum laws fail to accomplish the assignment to classify the cyber attacks as an armed attack or a use/threat of force, but they also uncover major fractures in the legal system.
The truth is that the process of fitting an act to the legal system is dictated by the fact that at the time of the drafting of the UN Charter there were no cyber attacks. Otherwise, the drafters would have created a norm regulating cyber attacks with which this acts could be categorized in terms of quantity and quality.
Turning our sight again to the three approaches, we realize that the proposed set of techniques may come be able to give some interpretive solution that may work well under the current legal framework so that the past and the future can converge and find a common language.
Nevertheless, the definition of "fitting" is an action or act of one that fits (Merriam-Webster dictionary), a meaning that suggest some activities are inclined to bear a particular form of straining something that is cast in a different mold. Ultimately, it seems vital then that even the most sublime moments of straining should not go beyond the breaking point.
Reference List
Adler. H. (2011). Cyber Bellum? Retrieved from http://law.huji.ac.il/upload/AdlerHilaUpdated%281%29.pdf
Barkham, J. (2001). Information warfare and international law on the use of force. N.Y.U.J. INT'L L. & POL 57, 34.
Bond, J.N. (1996). Peacetime Foreign Data Manipulation as One Aspect of Offensive Information Warfare: Questions of Legality under the United Nations Charter Article 2(4). Retrieved from www.au.af.mil/au/awc/awcgate/navy/nwc_bond.pdf
Brown, D. (2006). A Proposal for an International Convention to Regulate the Use of Information Systems in Armed Conflict. Harvard: Harv. Int'l L.J.
Dörmann, K. (2004). The applicability of the additional protocols to computer network attacks: an ICRC approach. In Bystrom, K. (Ed.), International Expert Conference on computer network attacks and the applicability of international humanitarian law: Proceeding of the Conference. Stockholm: National Defence College.
Environmental Modification Convention (1978). Retrieved from http://www.state.gov/t/isn/4783.htm
ICRC (1977). Protocol Additional to the Geneva Conventions of 12 August 1949, and relating to the Protection of Victims of International Armed Conflicts (Protocol I). Retrieved from http://www.icrc.org/IHL.nsf/FULL/470
Hathaway, O., Crootof, R., Levitz, P., Nix, H., Nowlan, A., Perdue, W., Spiegel, J. (2012).
California Law Review, 100 (4), 817-886.
Ophardt, J. A. (2010). Cyber Warfare and the Crime of Aggression: the Need for
Individual Accountability on Tomorrow's Battlefield, Duke L. & Tech. Rev, 003.
Sklerov, M. (2009). Solving the dilemma of state responses to cyberattacks: A justification for the use of active for the use of active defences against states who neglect their duty to prevent. (Master's Thesis, The Judge Advocate General's School, USA)
Schmitt, M. (1999). Computer network attack and use of force in international law. Columbia Journal of Transnational Law, 37, 885-937.
Schmitt, M. (2011). Cyber operations and the jus ad bellum revisited. Villanova Law Review, 56, 569-606.
Stevens, (2009). Internet War Crimes Tribunals and Security in an Interconnected World. Retrieved on 02/07/2013 from http://www.uiowa.edu/~tlcp/TLCP%20Articles/18-3/stevens.finalfinal.me.mlb.100109.pdf
United Nations (1945). United Nations Charter. Retrieved from http://www.un.org/en/documents/charter/
U.S. Defense Department (1999). An assessment of international legal issues in information operations. Retrieved on 02/07/2013 from http://www.au.af.mil/au/awc/awcgate/dod-io-legal/dod-io-legal.pdf

What should you learn next?
Waxman, M. (2013). Self-Defensive Force Against Cyber Attacks: Legal, Strategic and Political Dimensions. Retrieved on 02/07/2013 from http://papers.ssrn.com/sol3/papers.cfm?abstract_id=2235838










