An Examination of the Security Threats Posed to a Mobile Wallet Infrastructure
Introduction
Our last article reviewed in depth just what precisely a Mobile Wallet is, and how it works. In summary, it is essentially a mobile app from which you can download from either the App Store or Google Play.
Once it has been installed onto your wireless device, you enter in your credit card information, and the next time you are at a local store, you can pay for your products by just tapping your Smartphone onto the Point of Sale Terminal.
The development of more sophisticated Mobile Wallets is also exploding. As of now, the most popular one is that of Apple Pay, designed by Apple. However, just like anything else, the Mobile Wallet is also prone to Security threats and risks, which is the focal point of this article.
The Security Threats Posed to the Mobile Wallet Infrastructure
It is essential to keep in mind that there is a distinction to be made between a Mobile Payment and a Mobile Wallet. With the former, you are entering in your credit card information (unless you have it stored in your account, like that of Amazon) at the final point in the E-Commerce transaction to complete the checkout process.
Thus, no intermediary is involved.
With the latter, you are using a specialized form of a mobile wallet to make the payment for you, so thus, it becomes an intermediary. As a result, the Security vulnerabilities of the two different types of payments thus significantly differ. For example, with the Mobile Payment, the main threat is when you transmit your information, there is the real risk that a Cyber attacker could covertly capture that specific information.
However, with the Mobile Wallet, the entire payment infrastructure is at risk, thus exposing the Mobile Wallet to an entire array of Security threats and risks. This can be depicted in the following model:
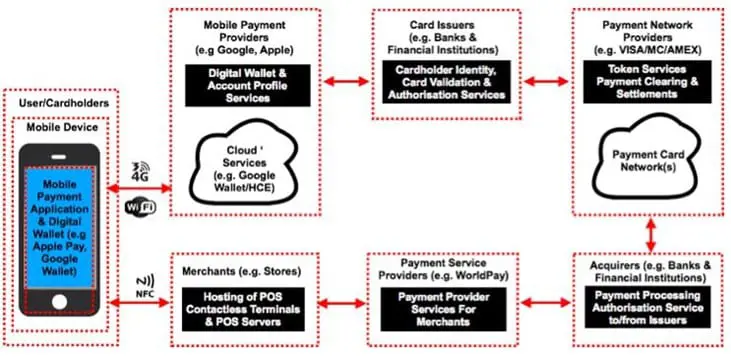
We will now examine all the Security threat vectors that are present in all the sub-components which are depicted above:
-
From the perspective of the end user:
If you think about it, this is probably one of the most critical subcomponents in the entire Mobile Wallet Infrastructure. True, the end user is very much exposed to the technical side of the threat vectors, such as rogue mobile applications, Malware, and even Spyware being covertly installed on the Smartphone. However, the end user is also prone to Social Engineering attacks as well. For example, there is the risk of Phishing E-Mails (this has become a prevalent issue yet once again, given the fact of how many individuals use their Smartphone to receive and send E-Mail). However, there is also the old-fashioned trick of a crank call to the end user, and convincing he or she to share their private/confidential data, and even giving out their financial information as well.
-
From the perspective of the Mobile Wallet Provider:
This entity is the sub-component that creates and develops the Mobile Wallet app which is downloaded onto your Smartphone. As it was described earlier, Apple creates the Apple Pay platform, and other vendors create their own brands for the Samsung/Wireless devices, which of course use the Android Operating System. In this regard, Mobile Wallet Providers are prone to all sorts of Cyber-based threats, which include the following:
àThese kinds of attacks are more common if the Mobile Wallet app has been developed on a Closed Source platform versus an Open Source platform. The primary reason for this is that is there is more of a gain to be achieved for the Cyber attacker than with the latter. After all, with Open Source Code, everything is revealed, so there is not much motivation to reverse engineer a mobile based on this platform.
One of our previous articles went into detail about "Rootkitting" a Smartphone. Essentially, this means that bypassing or circumventing the existing Security features on the Smartphone to gain full, one hundred percent administrative privileges to it. Most of the time, this involves misconfiguring the Configuration Profile. The same concepts that are used to "Rootkit" a Smartphone can also be applied to the Mobile Wallet application as well. However, in this regard, it is not so much the Configuration Profile which is sought after. Instead, it is the APIs which are used in the Source Code.
-
From the perspective of the Merchant:
From this angle, the most common Cyber related threats which are posed to this subcomponent is the installation of Malware on the Point of Sale (PoS) terminals. There is nothing new about this, as we have seen large-scale Malware attacks at the retail giants of Home Depot and Target. The primary goal of this is to covertly hijack the credit card data of the end user who has had their card swiped at the PoS. However, keep in mind, with the Mobile Wallet Infrastructure, the end user is not actually swiping their credit card. Instead, the payment is being made from the Mobile Wallet app, and the financial information is transmitted on the Near Field Communications (NFC) wireless protocol. It is at this point that the Cyber-attacks are targeted towards. Keep in mind that now, NFC is an unencrypted protocol, so any information and data which is sent across it sent in Cleartext. So, in this regard, the most common Cyber based threat is that of the "Man in the Middle Attack." All one needs is a Network Sniffer, and to be in close range when a Mobile Wallet transaction is being carried out.
Another critical Cyber based threat in this regard is that of the "Relay Attack." Malicious software can be installed on the end user's Smartphone, and thus can be used to relay specific commands to the Card Emulator (this is used as a proxy on the POS). This has been a known problem on the Smartphones which make use of the Android Operating System in testing environments. It has been shown that a Cyber attacker can easily conduct unauthorized payments.
-
From the perspective of the Payment Service Provider:
This subcomponent of the Mobile Wallet Infrastructure sends the credit card information from the merchant's Point of Sale Terminal to their respective financial institution to further process the Mobile Wallet transaction which was just initiated. Although the Payment Gateways have been a long-favored target, a newer attack vector is that of the network connections between the merchant and the Payment Service Provider. Although these connections are reasonably secure using Secure Sockets Layer and Virtual Private Networks (VPNs), the Cyber attacker of today is very sophisticated and is continually trying to find ways to get into these network connections. Once in, the favored type of attack is once again the Man in the Middle Attack.
-
From the standpoint of the Acquirer:
These are the actual financial institutions that process the Mobile Wallet payment after the Payment Service Provider has received it. In this regard, the main point of interest for the Cyber attacker are the servers which contain the financial information and data of the end user. To get into the system, the Cyber attacker tries to determine and ascertain any weaknesses which can be found in the Security defense perimeters. They can also launch their attacks by installing rogue backdoors and from there install Malware files on the primary servers to get this valuable information/data. Also, covert Repudiation Attacks can occur. A Repudiation Attack can be defined as follows:
"Repudiation is the ability of users (legitimate or otherwise) to deny that they performed specific actions or transactions." (SOURCE: 1).
This is when a legitimate Mobile Waller transaction can be covertly reversed. As a result, the issuing bank of the credit card automatically puts a hold on the credit card, and the end user is greatly inconvenienced by having to get a new credit card.
-
From the standpoint of the Payment Network Provider:
This subcomponent of the Mobile Wallet Infrastructure attempts to settle the transaction between the Acquirer and the credit card Issuer. In this regard, tokens are often created as a proxy for the actual credit card number. This was reviewed in the last article, and essentially, it is a fictitious number which is used to hide or "mask" the actual credit card number. It should be noted that the tokenization service is outsourced to a "Token Service Provider." The Cyber attacker will primarily target this area, by trying to capture the token lookup tables to determine how the tokens were mapped. These lookup tables contain such information as to how the tokens were individually created, and how the validity of the token was determined (in other words, checking for the integrity of it, and determining if the token has been altered in any way). Another threat to this subcomponent is known as the "Denial of Payment Services" attack. This is like a Denial of Service Attack, but instead of flooding a server with malformed Data Packets, the Token Service Provider is bombarded with these types of Data Packets, to halt the token creation process.
Conclusions
In summary, this article has examined some of the subcomponents of a Mobile Wallet Infrastructure, as well as the types and kinds of Security threats and risks which are posed to it.
It is essential to keep in mind that although the primary interface is that of the Mobile Wallet, there are a lot of other pieces which are required to make the entire process function smoothly.
In a way, the Mobile Wallet Infrastructure is much more complicated than just a typical credit card transaction, as there are more Security mechanisms put into place to safeguard the financial information and data which is transmitted in the whole system.
However, despite these efforts, the Cyber attacker will more than likely always find a way to penetrate a weakness or a vulnerability of it and exploit it to the maximum possible.
For example, Google Wallet and Apple Pay are the most widely used Mobile Wallet platforms, and despite the enormous efforts which have transpired to make the transactions secure, researchers and even Penetration Testers have found a way to find vulnerabilities and weaknesses.

What should you learn next?
This will be the focal point of the next article, as well as completing the review of the Security threats which are posed to the overall Mobile Wallet Infrastructure.
Resources
- https://msdn.microsoft.com/en-us/library/ff648641.aspx
- https://www.americanbanker.com/news/is-your-mobile-wallet-ready-for-the-fraud-wave
- https://books.google.com/books?id=sJGeBgAAQBAJ&pg=PA60&lpg=PA60&dq=the+security+issues+weaknesses+of+mobile+wallets&source=bl&ots=TcuqEqObsT&sig=VoFprtkH0Wz5Q-D3vC6uIYtP0j4&hl=en&sa=X&ved=0ahUKEwimjafIysXUAhUKxYMKHZ6OAc04ChDoAQhLMAQ#v=onepage&q=the%20security%20issues%20weaknesses%20of%20mobile%20wallets&f=false
- https://www.javelinstrategy.com/blog/mobile-wallet-fraud-just-beginning
- https://yourstory.com/2016/09/fending-off-cyber-evil-in-the-mobile-wallet-space/
- https://www.bluefin.com/bluefin-news/security-traditional-payment-methods-vs-alternatives-spotlight-mobile-wallets/
- http://www.banktech.com/payments/google-apple-paypal-pose-mobile-wallet-threat-to-banks/d/d-id/1295436?
- https://www.state.gov/j/inl/rls/nrcrpt/2008/vol2/html/101346.htm
- https://www.lexisnexis.com/risk/intl/en/resources/whitepaper/Understanding-The-New-Payment-Methods-CSMB.pdf
- http://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=1095&context=bblj
- https://www.ftc.gov/sites/default/files/documents/public_comments/ftc-host-workshop-mobile-payments-and-their-impact-consumers-project-no.124808-561018-00013%C2%A0/561018-00013-82732.pdf










