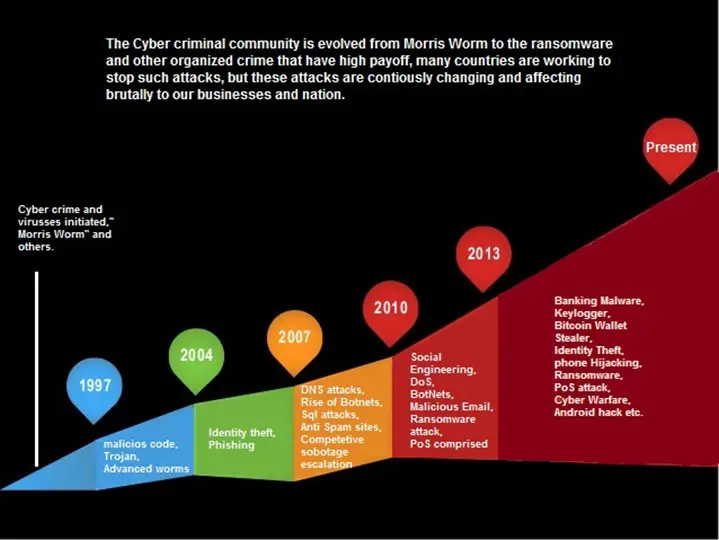
Evolution in the world of cyber crime
It is not surprising to consider the fact that whenever a person holds some valuable information, there are always some criminals looking to steal that information for financial gain or revenge. Before the internet, attackers had to dig through people's files or intercept their emails to accessing their personal information. As everything is connected through the Internet, all information is available online. The attacker also uses the Internet to steal identities and trick people into revealing their information.
Stealing information over the internet for any purpose is a cyber-crime for which many information security strategies have been implemented to secure the information. The first ever strategy of Information Security came in late 50BC when Julius Caesar introduced "Caesar cipher" a cryptographic method to encrypt the military communication. That was the first time when someone recognized the need for confidentiality of certain information.

FREE role-guided training plans
As soon as computers become an essential part of our life, the threat of information leakage has also increased. Hackers are always seeking to access confidential information, for that they are developing their techniques and strategies.
Today Cybercrime has reached the level of competition. Organizations are spending millions to protect their user's data. Somehow the continuous evolution of attackers is making it impossible to do so. Hacker's community is providing hacking as a service and making it a business of hacking with more developed and organized structure. Thus it creates competition in the business and attracts more attackers to join and participate.
In the late 70s, first ever computer virus "Creeper" was created that targeted a telephone company to make free long distance calls. That was the first encounter of any cybercrime that resulted in the launch of a first antivirus called "Reaper."
Internet Technology becomes popular and familiar in 2000's; people and organizations started using the internet for making money. It's very difficult to crack down on cyber criminals as they didn't use their actual location but located virtually. They attack anonymously and also impersonate people to receive money.
Cyber-attacks that started from the single Creeper virus has now reached to a huge collection of viruses and malware. There are many cases in the history that changed the world of hacking. The virus that changed the modern day cybercrime "Morris Worm" was one of the first computer worms distributed via the Internet in 1988. It was first to gain media attention.
The graph shows that how cyber attacks has changed over the years. Now the most widely used attacks are ransomware, point of sale attacks, Botnets, Phishing attacks, Cyber Warfare and network traveling worms. These attacks are popular nowadays and affecting millions of people around the world.
Ransomware attack
The first ransomware attack was reported in 1989, namely "AIDS" also known as "PC Cyborg" written by Joseph Popp. AIDS encrypts different files and software on a victim's computer and displayed a message claiming that the user license to use certain software has been expired. The user was required to pay US$189 to "PC Cyborg Corporation" to obtain a repair tool.
Ransomware attack has evolved a lot over the years, now as incidents on ransomware are on the rise, it has become the biggest Cybersecurity threat; a recent attack on University of Calgary had forced to pay a $20,000 ransom in bitcoins. In another ransomware attack, not only files, but the whole OS and hard disk go completely inaccessible, this led the United States and Canada to issue a joint alert on ransomware.
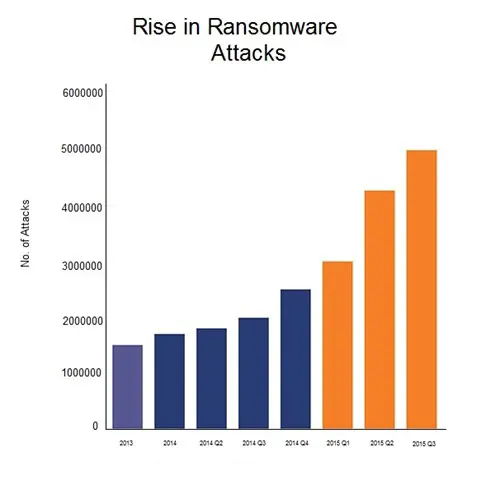
Exponential growth can be witnessed in the ransomware attack; law enforcement has also published a report stating the same, attackers are actively targeting small and mid-size organizations because the payoffs are higher, and it is growing even more in 2016.
Point of sale attacks
In Point of Sale attack, the intruder remotely attacks the environment where retail transactions and card purchases are conducted. PoS malware has been used for many years. Back in October 2008, in the report by Visa's data security, evidence of the use of PoS malware at many retail and purchase shops was shown.
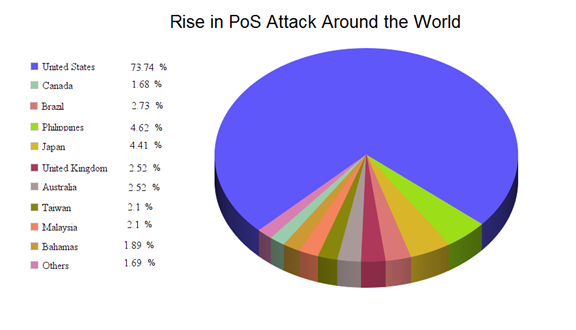
The attacker uses this attack to gain customer's personal detail such as card number, phone number, address and other confidential details. The most recent and one of the greatest attack on second largest discount retailer "Target" had exposed 40 Million customers' confidential information. The point of sale systems have become the appealing target for the attackers.
According to a recent report by KrebsonSecurity, Troy-based PoS vendor is currently investigating a breach of their NEXTEP's systems. The acknowledgment came in the notice when industry financial reports spotted a pattern of credit card fraud on NEXTEP's biggest customer "Zoup", a chain of eateries spread US and Canada.
Cyber warfare
It's not hard to believe that the world is going through cyber warfare; many countries are making efforts to steal secrets of other countries. We already heard many cases in past about these type of attacks, in 2012 researcher teams at Kaspersky Lab and Symantec discovered cyber weapons targeting Middle-East.
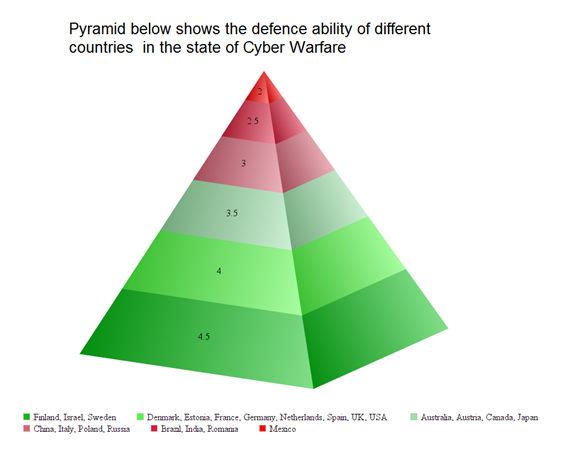
Over years many countries have made this warfare controlled by their military. In 2015 researchers have released a Worldwide Security Assessment report that shows the progress of different countries to overcome this major threat of cyber warfare.
However, we all know that we are going to encounter these types of attack rapidly. But we must also accept the fact that attackers are evolving every day and coming back with new strategies and techniques to breach our systems. They are more likely to be working as an organization than an individual. So now we have a wide group of organizations (Offensive) coming to spoil our privacy, steal our money and impersonating us.
Lack of security measures and poorly skilled professionals are giving strength to attackers. Cybersecurity professionals have failed to show their potential skills to overcome this rising issue, either they are not well known about the defending strategies or their knowledge and skills are not enough to do so. According to research, the world is facing a shortage of skilled cybersecurity professionals, and the threat will increase further in coming years. It will reach to a shortage of 2 million cybersecurity individuals and will cost $2 trillion by 2019.
While the universities are not taking this global issue seriously, universities are unable to provide proper education to prepare quality cybersecurity professionals. In the US the universities ranking shows that not even single university has earned "A" grade for cybersecurity education. This shows that universities are failing to provide quality cybersecurity education so far.

FREE role-guided training plans
Organizations around the world are working on intend to stop such kind of attacks somehow. Nevertheless, hackers are one step ahead because of their significantly growing and revolutionizing techniques. But, the future infosec professional will defend and help us to make a better cyber world.









