Cyberterrorism Defined (as distinct from “Cybercrime”)
Introduction
Technology is developing at an extremely vigorous pace over the last couple of decades. There are many unknown terms that come along with this rapid change. Often, the common people are not familiar with these new strange words ensuing from technological advancements and its interaction with the other branches of life.

FREE role-guided training plans
The purpose of this article is to help the reader understand the notion of cyberterrorism. Many controversial questions are set forth: "What is cyberterrorism?" "What is its objective?" "Are there any cases of cyberterrorism in real life?" "What is the difference between cyberterrorism and cybercrime?" Although there is much to be said on that increasingly popular subject, this contribution reveals some of the answers behind these tricky queries.
-
Cyberterrorism
- The Definition
- The Definition
So far, the international community has not decided on an exact definition of "terrorism" that can be applied universally. However, the United States Department of State prescribes the following definition of terrorism: "…premeditated, politically motivated violence perpetrated against non-combatant targets by sub-national groups or clandestine agents." (Title 22 of the U.S. Code, Section 2656 f(d))
"Cyberterrorism" was coined by Barry Collin in the 1980's. The fact that terrorism caused via kinetic force has not been unified yet in the international doctrine undoubtedly impeded determining a proper definition for its subcategory, , cyberterrorism. In a way, defining cyberterrorism is even more difficult because of the abstractness that is naturally implicated in understanding how certain events occur in cyberspace.
According to NATO (2008), cyberterrorism is "a cyber attack using or exploiting computer or communication networks to cause sufficient destruction to generate fear or intimidate a society into an ideological goal."
Another definition of cyberterrorism is provided by the US National Infrastructure Protection Centre, a part of the Department for Homeland Security: "a criminal act perpetrated through computers resulting in violence, death and/or destruction, and creating terror for the purpose of coercing a government to change its policies." (Wilson, 2003)
Some scholars or politicians avoid labelling acts as cyberterrorism, insisting on the assertion that these acts are mere hacking or so-called hacktivism. In their view, cyber attacks cannot bring about the same amount of death, destruction, or fear as with more traditional forms of terrorism. The word "hacking" become known in the beginning of the 1970's when Altair 8800, the first personal computer, was created. The purchaser had to not only assemble the machinery himself, but also had to install the software as well (Shinder, 2002).
Let's examine the derivative term "hacktivism." This is a word which combines two actions – hacking and activism. In short, hacktivism stands for low-level computer network attacks or digital activity which cause in most cases only temporary nuisance. Like cyberterrorists, hacktivists pursue political goals, but their activity does not correspond quantitatively or qualitatively with the possible outcome of cyberterrorist acts (Stanley, 2010).
The term "cyberterrorism" encompasses two other terms – cyberspace and terrorism. The word "cyber" designates what type of terrorism is being referred to. The prefix "cyber" originates from the ancient Greece and means "skilled in steering or governing." Many scholars claim that this term might not match well, since the Internet (the cyberspace) is not digitally, electronically, or otherwise controlled. Nevertheless, the term is deemed to be more accurate than terms like "virtual space/world/universe/reality," which have different existential context and therefore are not semantically appropriate. William Gibson first came up with the term "cyberspace" in his novel "Neuromancer" which was published in 1984. Nowadays, this term is widely known as the environment which the Internet creates - all the communication activities and interconnection of human beings through computer devices innate to this medium.
One scholar defines cyberterrorism as the "convergence of terrorism and cyberspace." Basically, the means and their application is the same as regular computer network attacks with the significant difference that in the case of cyberterrorism, the leading motive is to coerce the government or its citizens to comply with some political or social demands. Moreover, the act should result in violence or fear in order to be qualified as cyberterrorism. Minor attacks that disrupt services of no great importance are not cyberterrorist acts, yet they may prove a very expensive nuisance, in terms of economics (Stohl, 2007).
- Objectives
Without any doubt, the emergence of the Internet and its wide-range spectrum of opportunities have influenced considerably the terrorists' methods and behaviour. In his speech before the RSA Cyber Security Conference, the FBA Director Robert Mueller warned that despite the fact that terrorism still poses the number one threat, cyberterrorism may displace the conventional one from its prime position. One can identify three main objectives of cyberterrorism:
- Organizational
This organizational objective of cyberterrorism includes functions like recruiting, instigation training, fundraising, communication, planning, spying, etc. Following the intelligence reports, terrorist groups nowadays recourse to the Internet on a daily-basis. Their knowledge and skills in regard to computer technology is steadily growing and this build-up of knowledge and skills would eventually provide the necessary expertise for finding and exploiting vulnerabilities in the online security systems of governments or critical infrastructure institutions (Wilson, 2005).
Although those researching the terrorist use of the Internet often describe them as radical factions seeking some sort of virtual jihad, the actors committing cyberterrorism do not have to be religiously motivated. Furthermore, the organizational function of cyberterrorism enables the wrongdoers to pursue their objective either through the means of traditional warfare or technology (Brickey, 2012).
- Undermining
Self-explanatory, the goal which terrorists seek to achieve here is to hinder the normal functioning of computer systems, services, or websites. The methods used are defacing, denying, and exposing. Since the Western countries are highly dependent on online structures supporting vital services, these methods are of proven merit. However, disruptive activities usually do not entail grave consequences, except perhaps in cases of an unpredictable knock-on effect (Brickey, 2012).
- Destructive
Because this purpose is directed towards achieving the same or similar results as classical terrorism, it is labelled pure cyberterrorism. Through the use of computer technology and the Internet, the terrorists seek to inflict destruction or damage on tangible property or assets, and even death or injury to individuals. There are no cases of pure cyberterrorism up to date, but perhaps its occurrence is only a matter of time, given the fact that the states' critical infrastructure have significant security flaws (Brickey, 2012).
- History and Instances
The first cyber attack by a terrorist was recorded in 1998 when the Black Tigers guerillas jammed Sri Lankan embassy email inboxes with hundreds of emails for a couple of weeks, generated by special software.
In the course of the Kosovo war in 1998, NATO computers were subjected to denial-of-service attacks and email bombs. Web defacement against US government websites was conducted by Chinese activists as retaliation for the accidental bombing of the Chinese embassy in Belgrade by NATO forces.
As a whole, cyberterrorism wasn't really popular until the end of the millennium. At this particular moment, the big hysteria around the Millennium bug started to kindle peoples' imagination. There were many apocalyptic scenarios which apparently did not transpire. Nevertheless, the fear of what might happen, either intentionally or by accident, if computers or technology were to go wrong, remained. Then the 9/11 terrorist attacks happened, leading inevitably to a new wave of anxiety with relation to all possible terrorist threats.
In 2007, Estonia's government and economy was struck by distributed denial-of-service attacks allegedly conducted by a Russian group. Nonetheless, neither NATO investigators nor European Commission experts could not link the cyber attack to the Russian government. Following a more recent series of events, in 2008, the Stuxnet worm sabotaged an Iranian nuclear plant. The Iranian government cast the blame on the joint efforts of USA and Israel. The latest cyber attacks on Saudi Aramco, RasGas, and US banks are considered as a strike back from the Iranian side.
- Cybercrime
An increasing number of criminals are attracted by cybercrimes, because these types of crimes are convenient, anonymous, quick, diverse, and relatively low-risk. In the past, cybercrimes were committed by individuals or groups without decent organization, whilst nowadays organized crime structures and highly-trained professionals are deeply involved in this lucrative criminal activity.
According to Interpol intelligence, just in the years 2007 and 2008, the damage from cybercrimes worldwide in numbers was evaluated at approximately 8 billion USD. In addition, the negative impact that corporate espionage brought on the intellectual property business worldwide was estimated at 1 trillion USD (Interpol, 2012).
Cybercrimes encompass the following range of illegal activities:
- attacks against computer data or network
- internet theft
- internet fraud
- interference of online financial services
- distribution of sexual content concerning children
- distribution of malicious software, Botnets
- email scam and phishing/pharming
- copyright or intellectual property infringement
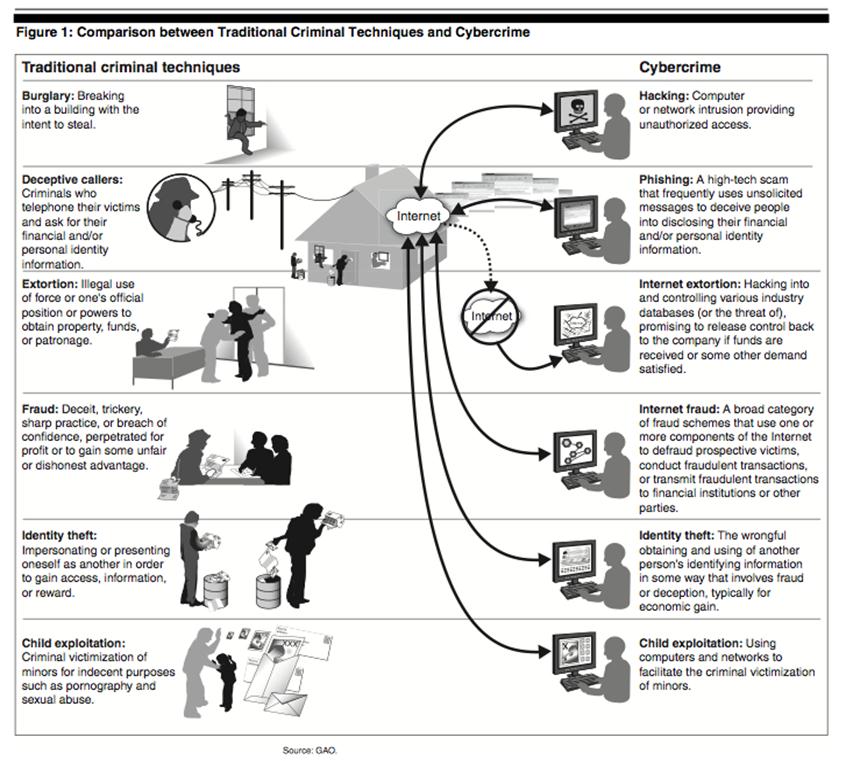
The diagram below (GAO, 2007) briefly outlines the differences between traditional criminal techniques and cybercrime:
[download]Download the full repot here:[/download]
- Noticing the difference between cyberterrorism and cybercrime
Depending on the context, cyberterrorism may overlap considerably with cybercrime or ordinary terrorism. When we talk about cybercrime and cyberterrorism, one of the underlying issues is the correct differentiation between the meaning of these terms. Often both terms are used interchangeably, a fact which brings confusion to people unfamiliar with details on that matter. If one observes a particular case and its context, this confusion may be further exacerbated by the application of other similar terms like Cyberwarfare.
Brett Pladna (2008: 5), Information Security Specialist, also admits that it is often not an easy task to make a distinction between computer network attacks performed by terrorists and cyber-crimes done by hackers. This is so because the attacker, whoever that is, always tries to exploit weak spots in the system regardless of the essence of the real motives. Nevertheless, there are certain trends that can help in making a clear difference between both acts. For instance, in most of the cases of terrorist computer network attacks, the terrorists' actions have been focused on website defacement and email bombing.
For cyberterrorism cases to be regarded in a way similar to classical terrorism, the acts of the former needs more or less to bear the character and magnitude of the latter, meaning death/injury to human beings or physical destruction or damage to property, and to be inflicted through the means of the Internet. The term cyberterrorism usually comprises acts that resemble to a certain extent those which are characteristic of terroristic attacks via conventional means. As to the term cybercrime, it generally includes an illicit activity on the Internet as a whole.
In order to overcome the disambiguation issue, scholars, institutions at international and domestic level, and legislation bodies should adopt a more appropriate course, in terms of law and politics. Once cybercrime and cyberterrorism terms are determinable, we would have a clear view on how to deal with such malignant acts. The only way to avoid that psychological condition is to strip both terms of the vagueness and ambiguity surrounding them.
Conclusion
Despite the fact that many observers deem that terrorist organizations like Al Qaeda do not rely on cyber attacks to achieve their ends, there is enough evidence material indicating the opposite. As it may seem probable from the late events connected to cyber attacks across the globe, there is an impending cyber threat. Without doubt, the terrorists desire to explore every option to cause great damage to their targets. Apparently, cyberspace provides a new battleground which every self-respecting opportunist would be willing to exploit either for criminal activities or cyber attacks at a minor or large scale.
People tend to be frightened of what is unknown, of that which is veiled under obscurity. Knowledge and enlightenment is always a power which can disperse the cloud that prevents one to see clearly the truth. By finding a way that even the common people would be able to understand clearlythe essence of terms like "cyberspace," "cybercrime," and "cyberterrorim," we can ensure that there will be less digital loopholes that the terrorists could take advantage of.
Reference List
Barry Collin, "The Future of CyberTerrorism," Proceedings of the 11th Annual International Symposium on Criminal Justice Issues, The University of Illinois at Chicago, 1996. Retrieved also on 12/12/2012 from http://afgen.com/terrorism1.html
Brickey, J. (2012). Defining Cyberterrorism: Capturing a Broad Range of Activities in Cyberspace. Combating Terrorism Center at West Point. Retreived on 12/12/2012 from http://www.ctc.usma.edu/posts/defining-cyberterrorism-capturing-a-broad-range-of-activities-in-cyberspace
Interpol, (2012). Cybercrime. Retreived on 12/12/2012 from http://www.interpol.int/Crime-areas/Cybercrime/Cybercrime
NATO, (2008). Cyber defence concept MC0571. Brussels, Belgium.
Pladna, B. (2008). Cyber terrorism and information security. Retrieved on 12/12/2012 from http://www.infosecwriters.com/text_resources/pdf/BPladna_Cyber_Terrorism.pdf
Shinder, D. L.(2002). Scene of the Cybercrime: Computer Forensics Handbook. Syngress, Rockland (MA), USA.
Stanley, N. (2010). The truth behind cybercrime, cyberwarfare, cyberterrorism and hacktivism. Retrieved on 12/12/2012 from http://www.bloorresearch.com/analysis/11652/cybercrime-cyberwars-cyberterrorism-and-hacktivism-part-.html
Stohl, M. (2007). Cyber terrorism: A clear and present danger, the sum of all fears, breaking point or patriot games? Journal of Crime, Law and Social Change,46(4).
U.S. Department of State, Office of the Coordinator for Counterterrorism, Country Reports on Terrorism, April 30, 2007.
United States Government Accountability Office (GAO), (2007). CYBERCRIME Public and Private Entities Face Challenges in Addressing Cyber Threats. Report to Congressional Requesters. Retrieved on 12/12/2012 from http://www.gao.gov/new.items/d07705.pdf
Wikia (2012). IT Law Wiki – Cybercrime. Accessed on 12/12/2012 http://itlaw.wikia.com/wiki/Cybercrime
Wilson, C. (2003). Computer Attack and Cyber Terrorism: Vulnerabilities and Policy Issues for Congress. CRS Web.
Wilson, C. (2005). Computer Attack and Cyberterrorism: Vulnerabilities and Policy Issues for Congress. CRS Report for Congress.Retreived on 12/12/2012 from http://www.history.navy.mil/library/online/computerattack.htm