Critical security concerns for the education industry
Balancing cybersecurity & compliance requirements in a resource-limited industry
Executive summary
The education industry has become a top hacker target: birth certificates, Social Security numbers, medical records, financial data, biometrics and even intellectual property give cybercriminals ample motivation to access educational databases and sell this data on the black market.
Aside from the typical security challenges facing the industry like phishing and malware, students themselves present another level of risk. The same young minds challenged and stimulated in classrooms can become cyber offenders, since they usually have ample access to technology, spare time and, often, poor judgment concerning the consequence of their actions.
This may lead to undesirable situations, including improper online conduct or even complex and damaging issues such as fraud or cyberbullying. Organizations in the education industry failing to understand these risks as a natural part of business will probably discover — the hard way — how damaging security incidents can be to operations, finances and reputation.
In the following pages, we review critical security concerns facing the education industry and how security awareness training can help educational organizations increase their security posture and stay compliant.
Digital education and cyberthreats
Education, like other industry sectors, is going down the digital transformation pathway. The result is a mixed bag of digital measures to enhance and augment teaching. EdTech includes areas such as virtual reality, IoT and online learning portals; digital learning is increasingly interwoven with traditional learning.
With connectivity comes cybersecurity threats. The education sector is a target for a number of these cyberattacks, including:
Ransomware: In 2019, over 1,000 US public schools were victims of ransomware.[1] One school, Rockville Center School District, paid a ransom of $88,000 to receive a decryption code for ransomware-encrypted files.[2]
Trojans: Security vendor Malwarebytes found that education is the top target for Trojan malware. The report stated that in 2020:
“… educational institutions must brace themselves for a continuing onslaught of cyberattacks …”[3]
Dark web and free textbooks: During research into infected online textbooks, Kaspersky found 356,000 malicious files; 233,000 of them were malware-infected essays and 123,000 malware-infected textbooks.
Email-based threats: malware & ransomware
Most schools and colleges have an open approach regarding their technology infrastructure. While many maintain an administrative network restricted to employees, it is common to see it mixed with the academic network used by teachers, professors, students and visitors.
This scenario, combined with the fact that many institutions have limited funding, makes educational institutions especially prone to cyberattacks. Educational institutions must balance the need to keep systems running with the need to keep them protected on limited funds.
As far as threats go, email has become the weapon of choice for a wide range of cyberattacks. However, as time passes and education increasingly goes online, other phishing methods including social media and mobile messaging apps are also being incorporated into the cybercriminal’s arsenal. A 2019 survey into education cybersecurity issues found that phishing and social engineering remain the top-most threat in the education sector.[4] In parallel with the finding, the 2019 Verizon Data Breach Investigations Report (DBIR) found that phishing was behind one-third of all data breaches. [5]
· Email is used at all organizations
· It is a time-tested attack channel used because malware infection
· Attacks such as phishing are not necessarily new, but their frequency (combined with the amount of information cybercriminals can leverage to launch an attack) has caused this risk to escalate even further
Security vendor Kaspersky is predicting that social media will increase in prevalence as a phishing conduit, stating that “the focus on social engineering will increase as other types of attacks become more difficult to carry out.”[6]Source: Symantec™ Internet Security Threat Report, volume 22
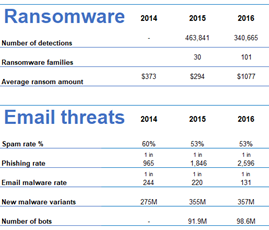
For most educational institutions, the contact information of both employees and students are readily available from a wide variety of sources, including institutional websites or social media profiles. Attacks created using this sort of information have a much higher chance of success, as details are carefully crafted into emails that look completely legitimate.
This is just one of the factors that makes educational institutions and their employees so susceptible to email-based attacks, including ransomware. As hackers become more and more successful, they continue to raise the stakes. The average ransomware demand was in $84,000 in 2019, increasing two times over the year.[7]
Miscellaneous errors
Continuing the theme of human error and human factors in cyberattack facilitation, the 2019 Verizon Data Brach Investigation Report (DBIR) found that “miscellaneous errors” was the top cybersecurity issue in the education sector with 35% of data breaches caused through this route. Miscellaneous errors include areas such as mis-delivery of information.
Over half of the data breaches were caused by external parties; however, almost half were from insiders. The DBIR highlighted the use of phishing to harvest login credentials.
Navigating the sea of compliance regulations in education
In terms of compliance requirements specific to the education industry, there are a considerable number of cybersecurity laws and regulations that education leaders must understand. These regulations are designed to protect employees and students from many of the threats discussed above. Here are four of the widest-reaching mandates:
Family Educational Rights and Privacy Act
The Family Educational Rights and Privacy Act (FERPA) is a federal law applying to all schools receiving funds under an applicable program of the US Department of Education. FERPA grants parents the right to their children's education records. Those same privileges are transferred to students when they become 18 years old or attend post-secondary education.
FERPA dictates the right to inspect and review student education records maintained by the school. It also gives parents and students the privilege to request correction of records they deem inaccurate or misleading. As expected, FERPA also clearly forbids the disclosure of confidential student information (e.g., name, student identification number or Social Security number) in a personally identifiable manner, without the student’s or authorized party’s written consent.
General Data Privacy Regulation & Payment Card Industry Data Security Standard
Schools and colleges constantly deal with personally identifiable information from both their employees and students. If any of their records include data from a European Union citizen, this means the organization will have to comply with the General Data Privacy Regulation (GDPR). Also, since many educational institutions perform credit card transactions, they must comply with the payment card industry data security standard (PCI DSS). For both examples, a non-compliant organization could face severe consequences, including:
- Hefty fines
- Suspension of credit card acceptance
- Damage to reputation
- Civil litigation if a breach occurs
Children’s Internet Protection Act
In the early 2000s, the Children’s Internet Protection Act (CIPA) placed internet safety requirements on schools and libraries regarding internet usage. The CIPA was created to prevent access to adult content or any other form of information considered harmful to children.
Student Online Personal Information Protection Act
Enacted in 2014, California’s Student Online Personal Information Protection Act (SOPIPA) created much stricter legislation pertaining to the permissible activities of online school service providers in the digital age.
In 2016, student data privacy became a priority issue for state legislatures. Therefore, SOPIPA formed a basis for many of the 112 bills introduced in more than 34 states from 2015 to 2017. Currently, schools must deal with the privacy concerns of education data collection and pay close attention to governing the data use and privacy activities of the online services they provide. At the same time, they must manage and provide for district resource needs, especially given the increased data privacy and security responsibilities many districts and school boards were charged with in 2014.
Cost of non-compliance
Education organizations rank fourth in terms of the number of data records stolen or lost by industry, sitting only behind the government, financial institutions and technology companies. Considering how prone schools and colleges are to security incidents, ensuring compliance must be a top management priority.
Recently at Cabrillo Community College, an unauthorized party gained access to the information of approximately 28,000 students. Data compromised included student names, dates of birth, email addresses, usernames, passwords and in some instances, Social Security numbers. This breach may lead to severe consequences, including complete or partial loss of funding provided by the Department of Education.
There is an immense variety of compliance approaches underpinning an organization’s legal framework regarding cybersecurity. The first step should be assigning responsibility for compliance to an individual or creating a compliance department that will oversee essential regulatory requirements, compliance standards and guidelines.
Those responsible for cybersecurity compliance must employ a strategy to gain practical information on compliance and make sure there are sufficient controls to monitor and uncover any regulatory and/or legal breaches. Again, as each organization requires a unique approach, it’s important to consider how compliance fits, how well it aligns with key business objectives and how compliance processes can reinforce and strengthen a cybersecurity-aware culture.
Mitigating security threats with security awareness training
Security awareness training is a prerequisite for many security standards and compliance regulations. However, an effective security awareness program can also add considerable value to the overall security strategy at any educational organization. A recent survey from JISC found that 43 percent of universities in the UK provided no security awareness training for students.[8] However, the 2019 DBIR study shows that by corporate users have decreased over the last seven years due to continued awareness training by corporates.
The human element is often the primary cause of many data breaches through simple mistakes like downloading malware or clicking phishing links. By teaching employees and students how to detect cyberthreats, they will be better equipped to prevent data breaches and keep data secure.
According to Verizon’s 2019 Data Breach Investigations Report, 32% of breaches used phishing including targeted emails and social engineering. Other findings include:
- Email was used for 94% of malware delivery
- 33% of all attacks were social in nature
- 34% of breaches involved internal actors
- 29% of breaches involved stolen credentials
- 60% of web application attacks are against cloud-based email servers
Cybercriminals have humanized their hacking methods — and as the data shows, it’s working. By exploiting common drivers of human behavior like eagerness, distraction, curiosity and uncertainty, hackers can easily convince uninformed users to share sensitive data or install malware. With so many security risks stemming from human behavior, awareness training for employees can be an effective tool in the prevention, detection and early reporting of security breaches.
Getting executive buy-in for security awareness training
 As information security efforts shift from reaction to prediction, security awareness training stands out as one of the best and most cost-efficient ways of avoiding cybersecurity incidents.
As information security efforts shift from reaction to prediction, security awareness training stands out as one of the best and most cost-efficient ways of avoiding cybersecurity incidents.
With so many security threats facing the education industry, getting buy-in from top management for any security initiative should be a simple matter of presenting the facts in a business-oriented way. In most cases, resistance to security projects is rooted in poor understanding of their benefits to the business. Therefore, linking security awareness training to business goals and value will help build executive support for awareness training initiatives.
In general, before approving any initiative, executives will first consider:
- Is it something required by a law, regulation or contract?
- Will it improve company financial results?
- Will it make our business processes more efficient?
- Will it create a competitive advantage?
- Will it reduce our operating costs?
- Will it solve an issue we are already facing?
Positioning security awareness as a positive answer to these six questions will likely result in an approved project budget and ongoing program support. You can also build a business case by drawing from security-related industry studies or mishaps. A quick Google search yields many compelling statistics:
- Ransomware continues to plague the sector
- The average cost of a data breach in education is $4.77 million
- The average cost per compromised record at U.S. education organizations is $142
- Education organizations take an average of 212 days to identify breaches
Using data and case studies as a basis to construct a what-if scenario will facilitate meaningful presentations relatable to any organization in the education industry. This creates a formidable argument for security awareness training and its benefits:
- Building staff confidence: Security awareness training will teach staff what to do and what not to do to help protect the business
- Creating a security-aware corporate culture: Informed employees share ownership for organizational cybersecurity and feel accountable for their actions. This creates a corporate culture that protects business data and reduces the likelihood of incidents
- Saving money and time: Having a cyber-aware staff does not mean incidents will never happen. However, if an incident does occur, the time-to-discover period and overall impact will be drastically reduced. This means less impact on operations, reducing the possibility of damaged reputation, compliance issues or financial losses
These three examples illustrate just a few of many security awareness training program benefits. By tying training impacts to business initiatives and company value, security awareness program managers can increase executive buy-in and overall program success.
Conclusion
The cyber threatscape is constantly evolving. As new and more advanced risks emerge with astonishing frequency, it’s clear that without proper security controls and workforce education initiatives, educational institutions are at risk for potentially catastrophic security incidents.
Due to the amount of high-value data collected and stored in their servers, educational institutions will remain a top hacker target. It’s up to security leaders to select the right security strategy, including both tech- and education-based solutions, to protect their infrastructure from attacks. By tying these preventative measures to business value and goals, they can capture executive buy-in and secure support for their awareness training initiatives over the long term.
Sources
- University of East Anglia investigates another data leak, ComputerWeekly.com
- Baylor College of Medicine notifies former applicants after data from 2016 breach found on publicly available web site, DataBreaches.net
- Malware attacks San Ysidro School District, demands $19K ransom, inewsource.org
- 2017 Data Breach Investigations Report, Verizon
- 2017 Ponemon Cost of Data Breach Study, Ponemon Institute
[1] ITPro Portal: https://www.itproportal.com/news/over-a-thousand-us-schools-hit-by-ransomware-in-2019/
[2] Emisoft: https://blog.emsisoft.com/en/34822/the-state-of-ransomware-in-the-us-report-and-statistics-2019/
[3] Malwarebytes: https://blog.malwarebytes.com/trojans/2019/08/trojans-ransomware-dominate-2018-2019-education-threat-landscape/
[4] Jisc, Cybersecurity Posture Survey 2019: https://www.jisc.ac.uk/reports/cyber-security-posture-survey-results-2019
[5] Verizon, Data Breach Investigations Report: https://enterprise.verizon.com/resources/reports/dbir/
[6] Kaspersky 2020 predictions: https://securelist.com/corporate-security-predictions-2020/95387/
[7] Dark Reading: https://www.darkreading.com/risk/average-ransomware-payments-more-than-doubled-in-q4-2019/d/d-id/1336893

FREE role-guided training plans
[8] Jisc, Cybersecurity Posture Survey 2019: https://www.jisc.ac.uk/reports/cyber-security-posture-survey-results-2019










