Botnets and cybercrime - Introduction
Preface
One of the most insidious cyber threats for security community is represented by diffusion of botnets, networks of infected computers (bots or zombies) managed by attackers due the inoculation of malware. The controller of a botnet, also known as botmaster, controls the activities of the entire structure giving orders through communication channels; the use of botnets is very commons in various IT contexts, from cybercrime to cyber warfare.
A botnet could be used to conduct a cyber-attacks, such as a DDoS, against a target or to conduct a cyber-espionage campaign to steal sensitive information. There are various classifications of botnets, it's possible to discriminate them from the architecture implemented, the used network protocol or technology on which they are based.

FREE role-guided training plans
The level of diffusion of the botnets depends on the capabilities of managers to involve the largest number of machines trying to hide the activities of the malicious architecture. A critical phase in the arrangement of a botnet is represented by its constitution; the attackers have essentially two options, recruit bots diffusing a malware, typically via phishing campaign or sending the malicious agent via email, or renting in the underground the entire architecture.
As we will see in the post the diffusion of botnet is increased due various factors such as the availability of unprotected mobile platforms and the presence in the underground market of cyber criminals that rent services and structures to compose the malicious systems.
Infected machines receive commands from Command & Control (C&C) servers that instruct the overall architecture to operate to achieve the purpose for which it has been composed such as creation of SMTP mail relays for targeted spam campaign, implementation of a fraud scheme (e.g. Banking information gathering) or to launch a denial of service attack.
Current situation
According the analysis proposed recently by principal security firms botnets represent one of the most insidious cyber threats that caused in 2012 huge financial losses and serious damage to companies all over the world. The cyber threat botnet is creating great concern between security experts due its diffusion, millions of compromised computers connected to the Internet are in fact daily used to realize scams and cyber-attacks. The ease with which criminals can organize a botnet, although without having either special technical knowledge or complex infrastructures, is a factor that contributing in a meaningful way to the diffusion of botnets. Overall messaging botnet growth jumped up sharply from previous years. Behind the principal botnets, there is the cybercrime industry that is pushing on the diffusion of malware to infect an increasing number of machines, but also proposing new models of business, such as botnet rental or the commerce of the agents for botnet creation.
In many cases, the cyber criminals instead of monetizing botnet activities by directly implementing fraud schemas, rent a series of services to other criminals –a trend confirmed by the constant monitoring of the underground market offers.
According F-Secure, ZeroAccess is the most prevalent botnet observed in 2012. It compromised the largest number of machines in France, United States and Sweden, and it is considered most profitable malicious architecture. ZeroAccess infected millions of machines globally in 2012 with up to 140,000 unique IPs in US and Europe. F-Secure Threat Report H2 2012 states:
"The malicious site contains an exploit kit, usually Blackhole, which targets vulnerabilities on the user's machine while they're visiting the site. Once the machine is compromised, the kit drops the malware, which then turns the computer into a ZeroAccess bot."
To give an idea of the economic impact of the botnets, the report revealed that the ZeroAccess threat reportedly clicks 140 million ads a day. It has been estimated that the botnet is costing up to USD 900,000 of daily revenue loss to legitimate online advertisers. ZeroAccess author also designed another revenue scheme through Bitcoin mining using the computational capabilities of its victims. More than half of the botnet is dedicated to mining Bitcoin for profit. Unfortunately, it is not the unique one. Botnets such as Zeus, Carberp, Dorkbot and SpamSoldier (a mobile botnet) were also very active.
Zeus botnet is confirmed as the most insidious and specialized botnet that hit banking sector. The United States, Italy and Germany were counties with major diffusions of the malware. According "2013 GLOBAL THREAT INTELLIGENCE REPORT (GTIR)", proposed by the Solutionary security company, the US and Germany are the countries with the most prevalent sources of botnet Command and Control (C&C) traffic.
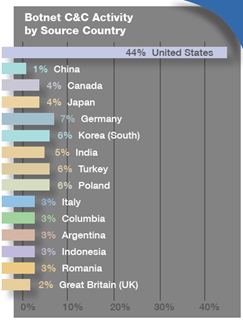
Figure 1 Botnet C&C Activity by Country - Solutionary Report
Solutionary experts confirmed that the emergence of the Blackhole 2.0 exploit kit will sustain the growth of number of botnets; SERT expects that this exploit platform will evolve in a much faster and more efficient manner being as an essential component for attackers.
Another interesting fact noted by security experts is that cyber criminals, to hide CnC communications, have started to adopt a solutions such as securing them using HTTPS protocol or hiding command messages within the traffic of social networks.
The process allows the safe passage of cyber threats, such as malicious code, and protects communications from control of security firms, but only once the victims have been already infected. For malware updates or stolen data, these communications often make use of data encryption. That's why monitoring inbound HTTPS traffic is crucial to identify and block attacks even though it provides minimal value in detecting CnC communications.
Classification of botnets
Trying to categorize the concept of botnet is not easy. There are many purposes for which these architectures are created. They inevitably influence factors such as the malware used to compromise victims, rather than the technology that you want to use.
Botnets could be discriminated by the structure they implement. Some networks are based on one or more C&C, every bot is directly connected with Command & Control server. The C&C manages a list of infected machines; it monitors their status and gives them operative instructions.
This type of architectures is simple to arrange and manage but present the drawback of being very vulnerable, shutting down the C&C the entire botnet could not operate, the server in fact represents a single point of failure because the operation of the botnet is functional to the capability of its bot to reach the control systems. Principal detection techniques are based on the analysis of traffic between bots and C&C, to improve resilience to eradication-decentralized botnets have been designed.
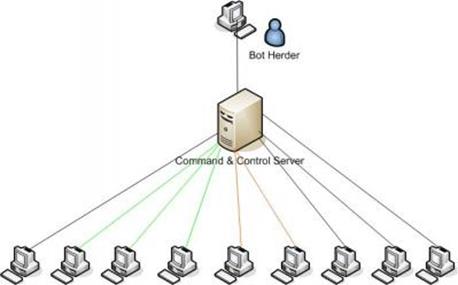
Figure 2 - Botnet C&C based
In decentralized botnet architectures, also known as Peer-to-Peer botnets, the bots are not necessarily connected to the C&C servers, but they compose a mesh structure in which commands are also transmitted from the zombie to the zombie. Each node of the network has a list of addresses of "neighbor" bots with which they communicate and exchange commands. In a similar structure, each bot could send orders to others and attackers to control the entire botnet, but they need access to at least one computer.
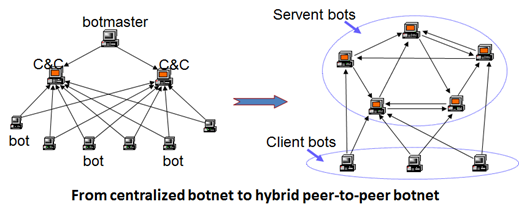
Figure 3 - P2P botnets
Last year Symantec security researchers detected a variant of the popular Zeus malware that relies on P2P communication as a backup system in case the C&C servers were not reachable. The variant isolated by Symantec doesn't use C&C servers implementing an autonomous botnet, the experts Andrea Lelli declared:
"Every peer in the botnet can act as a C&C server, while none of them really are one,""Bots are now capable of downloading commands, configuration files, and executable from other bots — every compromised computer is capable of providing data to the other bots,"
This type of botnet is really concerning. It's hard to fight due the absence of a point of failure as represented in a classic botnet architecture by the C&C servers. Despite the fact that destroying a decentralized botnet is more difficult, this type of architecture presents a management superior complexity. That's why hybrid structures are the hackers' privilege choice.
Botnets could be also classified by using network protocol or the technology on which they are based. Various architectures could be based on different communication protocols. One of the classic botnet scheme is the IRC-oriented, that is, based on Internet Relay. Each bot receives a command through an IRC channel from an IRC-Bot Server. An IRC bot is composed of a collection of scripts that connects to Internet Relay Chat as a client.
Most advanced botnets use their own protocols based on protocols such as TCP, ICMP or UDP. For example in the case mentioned before of Zeus Peer to Peer variant, the expert noted that authors implemented communication through UDP protocol.
Botnets could be based also on instant messaging services, so they are called IM-oriented, in this case commands are sent to the zombies via IM-services such as AOL, MSN and ICQ. Of course we cannot miss web-based botnets, a collection of infected machine controlled through www. HTTP bots connect to a specific web server, receiving commands and sending back data. This type of architecture is very easy to deploy and manage. A particular variant is represented by social network botnets. These architectures use popular social media platforms to send messages to zombies. These architectures are very difficult to trace due large of volume generated by social networking activities.
This type of botnet has become very popular with the diffusion of exploit kits able to compromise remote machines and control them. Usually cyber criminals send malicious links to the victims, via mail or social network messages, that hijack user on a compromised website that hosts the exploit kit. In a dynamic way, the victim is infected and one or more malware is downloaded to victim's host.
According to Group-IB, the new trend in C&C communication methods is the usage of public and well-known application protocols as well as placing C&C on social networks profiles and user accounts. The architecture of such botnets can be different and can be used for different purposes:
In such cases, it is hard to detect the anomalies in network traffic to find the malicious activity, as the bots just check the prepared file or text signature in social network. Sometimes the functions of modern social networks, cloud services and WEB-portals are used as a covert channel for information storage. One of the latest incidents was related to Evernote services, where the hackers prepared their own user account and uploaded the file with the commands to the botnet. The same method was used also with Twitter in Flashback botnet. The Zeus botnet is a classic example of this type of architecture, it was known to be able to steal banking credentials from victims.
Figure 4 - Zeus Builder
Mobile botnets
As explained, one of most interesting evolutions in botnet world is the opening to mobile to mobile platform. Damballa Research Laboratory discovered 40,000 infected mobile devices that have communicated through C&C servers for the first six months of 2011. Meanwhile, colleagues at McAfee Lab were some of the first firms to announce a large scale diffusion of new variant of Zeus malware on mobile platform. Today, mobile botnets are a reality. Millions of mobile devices have been infected by botnets in China via 7,000 Trojanized applications.
"Security researchers say they have discovered a huge botnet running on the smartphones of more than a million unsuspecting mobile users in China. The botnet can allow the smartphones to be hijacked remotely and potentially used for fraudulent purposes. (BBC)"
Exactly as for a desktop machine, mobile botnets exploit the same communication channels (e.g. IRC, HTTP, P2P), and the technological evolution of mobile solution provides environments having advanced capabilities that are attracting an increasing number of botmasters.
Drew Williams, President at Condition Zebra declared:
"Since July 2012, more than 100 million Android phones have found their way to new owners, which represents slightly more than half of the market in smartphones (sorry, iPhones). Fake apps and bad SMS messaging is all the rave with the malware writers these days, and as the new year unwinds, we have already seen report after report of this rising tide of "new" target exploits."
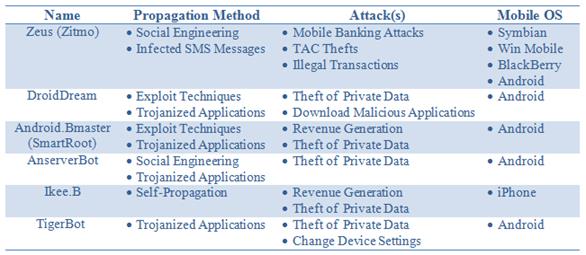
Following a list of principal mobile botnet observed in the last year
Figure 5 - Principal Mobile Botnet (Meisam Eslahi for Security Affairs)
Security researcher and digital forensic investigator Meisam Eslahi listed for Security Affairs the principal mobile cyber threats to emphasize their existence and their negative impacts on mobile network environments:
Zeus
The Zeus in the Mobile or Zitmo is a multiplatform agent that infects a variety of mobile operating systems, such as Symbian, Windows Mobile, BlackBerry, and Android, mainly by social engineering approaches. It sends an infected SMS to victims contain a fake URL to dupe users to download a security certificate that is, in fact, the Zitmo bot. It is also able to intercept messages sent by banks to their customers and authenticates illegal transactions by stealing mobile Transaction Authentication Numbers (TAC).
DroidDream
DroidDream was one of the good examples of this silent and insidious malware, since it is activated silently and at night (11pm to 8 am) when the mobile's users are asleep. It was designed to gain root privileges on infected mobiles and install a second application to steal sensitive information and protect itself from removal.
Android.Bmaster
The Android.Bmaster has infected a high number of mobile devices by using Trojan applications and exploited techniques. The Symantec named Bmaster as "A Million-Dollar Mobile Botnet" since it has gained millions of dollars through premium SMS, telephone or video services. However, recently a new mobile botnet called MDK has overtaken the Bmaster by infecting nearby 7,000 applications and having one million mobile devices under the control of its botmaster.
Ikee.B
Although the Ikee.B is a simple botnet in nature, it can be named as one of the early generations of mobile botnets that operates on jailbreak iPhones with almost the same functionality as computer-based botnets. Scanning the IP range of iPhone networks, looking for other vulnerable iPhones in global scale and self-propagation are the main activities of this malware.
AnserverBot
Amongst different types of mobile botnets, the AnserverBot can be considered as one of the most sophisticated malwares. Its command and control is designed based on a complex two-layer mechanism and implemented over a public blog. In addition to detecting and disable the security solution in infected device, the AnserverBot periodically checks its signature to verify its integrity in order to protect itself from any type of changes.
TigerBot
TigerBot is fully controlled by SMS instead of the Internet and web technologies. However, it detects the C&C messages and makes them invisible to the mobile device owners. In addition to collecting private data like SMS messages, it has sophisticated capabilities to record voice-call conversations and even surrounding sounds.
There is also appeared new kind of mobile malware oriented on banking fraud called Perkele Lite, which costs $7, 000 for a configured file and $12,000 for preparing and placing it on Google Play WEB-site – said Andrey Komarov, Group-IB. It provides own C&C interface and exclusive functions for designing as legit banking application.

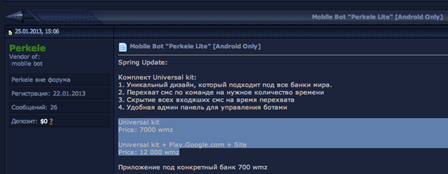
Figure 6 . Perkele Lite post in the undergrond
Cost of botnets and DIY trend
One of most concerning phenomena related to malware diffusion is the increasing of the offer of tools and services to allow criminals to implement and manage similar structures.
An increasing number of ill-intentioned individuals are requesting services and are acquiring the tools and malicious code for the arrangement of powerful botnet thanks the explosion of the sales model of malware as a service. Security expert Dancho Danchev is considered one of the most careful observers of cyber-criminal activities in the underground, he has posted many articles updating his readers on the evolution of black markets and described the tendency, dubbed "Do it yourself", that refers the diffusion of instruments in criminal world that make possible the establishment of malicious botnet.
Malware as a service model allows the outsourcing of criminal services. Let's think of botnet architecture management and C&C hosting services, thanks to the offer in the underground, criminals don't need to own a botnet architecture neither need particular skills to manage it, they just need to rent infected network to spread of malicious agents.
Recently the researcher described a new service offering access to thousands of malware-infected hosts, Danchev also estimated the cost to arrange a botnet composed of 10,000 machines located in the US.
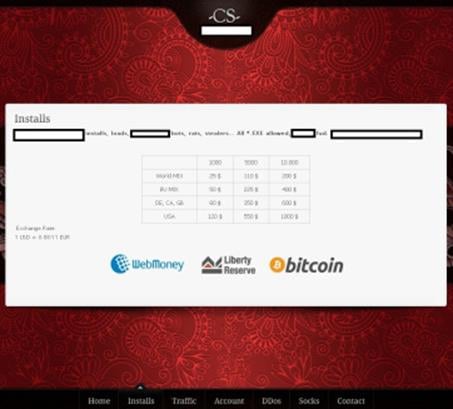
Figure 7 - Botnet Admin Panel
The expert analyzed a service offering access to infected hosts located everywhere in the world that is active since middle of 2012 and that despite its official Web site is currently offline it remains in operation until the present day.
Offer of similar services will increase in the next months, also attracting ordinary criminals and inexperienced cyber criminals. This will cause a decrease in the cost needed to acquire infrastructures and services to conduct a cyber-attack.
Purchases of US-based, malware-infected hosts are more expensive than machines located elsewhere due higher online purchasing power compared to the rest of the world.
Following the price list proposed by Danchev, as it is possible to note the expense is contained, and the offers various and articulated.
- 1,000 hosts World Mix go for $25, 5,000 hosts World Mix go for $110, and 10,000 hosts World Mix go for $200
- 1,000 hosts EU Mix go for $50, 5,000 hosts EU Mix go for $225, and 10,000 hosts EU Mix go for $400
- 1,000 hosts DE, CA and GB, go for $80, 5,000 hosts go for $350, and 10,000 hosts go for $600
- Naturally, access to a U.S.-based host is more expensive compared to the rest of the world. A 1,000 U.S. hosts go for $120, 5,000 U.S. hosts go for $550 and 10,000 U.S hosts go for $1,000
Last year Trend Micro published an excellent analysis on the Russian underground market, researcher Max Goncharov analyzed the services and the products offered by cyber on online Russian forums and services attended by hackers such as antichat.ru, xeka.ru, and carding-cc.com. It is relatively simple to come across sites that offer rented service for pre-built botnets, if the following table reflects the cost of Botnets, organizing a botnet has never been so easy!
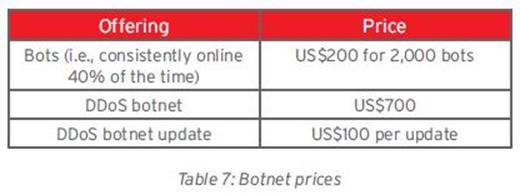
Figure 8 - Botnet prices (Trend Micro)
Conclusions
The scenario presented demonstrates the rapid diffusion of botnets, and the increased ease for criminals to acquire products and services to create and manage malicious architecture. This first article is an introduction of the botnet world that provides an overview of the state of the art on this cyber threat detailing also offers that support the growing phenomena of DIY.
The fight against the proliferation of botnets, in my judgment, goes through following key factors:
- Timely and methodical study of evolution of technological solutions on which are based botnets. It's important to define a universally recognized set of indicators to deterministically qualify the threat and its evolution.
- The promotion of joint operations that involve government agencies and the major private industry players. In this sense, some large companies have already embarked on a close collaboration with governments, as in the case of Microsoft.
- Awareness of the cyber threats and divulging best practices for the containment of the infection.
- Approval of regulations and penalties, recognized globally, for those who develop or contribute to the spread of botnets. Unfortunately today, different legislative frameworks represent an advantage for those who intend to commit a crime using these tools.
Despite the good intentions, we are still far from global agreement on the definition of the proper action against botnet diffusion, both on legislative and operative perspectives.
In the second part of the article that I'll submit in the next weeks, we will analyze most sophisticate solutions implemented by botmaster to keep secure their infrastructures and monetization method behind them. The second part will also propose methods for detection and fighting of malicious architecture.
References
http://securityaffairs.co/wordpress/6545/cyber-crime/on-new-generation-of-p2p-botnets.html
http://www.f-secure.com/static/doc/labs_global/Research/Threat_Report_H2_2012.pdf
http://malwarelist.net/2012/10/18/classification-of-botnets/
http://www.mcafee.com/it/resources/white-papers/wp-new-era-of-botnets.pdf
http://securityaffairs.co/wordpress/12862/malware/mobile-botnets-from-anticipation-to-reality.html
http://go.solutionary.com/GTIR.html
https://www.damballa.com/downloads/r_pubs/Damballa_Threat_Report-First_Half_2011.pdf
http://conzebra.com/top-ten-risk-management-issues-for-2013-crystal-ball-not-needed
http://securityaffairs.co/wordpress/12655/cyber-crime/botnet-organization-easy-and-cheap.html
http://blog.trendmicro.com/trendlabs-security-intelligence/backdoor-uses-evernote-as-command-and-control-server/
http://ddos.arbornetworks.com/2009/08/twitter-based-botnet-command-channel/