Behind Cyberbullying – Legislation & Coping Strategies
1. Preface: Cyberbullying and Digital Natives
Dr. Sameer Hinduja and Dr. Justin Patchin at the Cyberbullying Research Center define cyberbullying as "wilful and repeated harm inflicted through the use of computers, cell phones and other electrical devices," and it is especially popular among teenagers. Cyberstalking and cyberharassment are forms of cyberbullying perpetrated mostly by adults.

FREE role-guided training plans
Fig. 1
A Clear-cut Breakdown of the Term
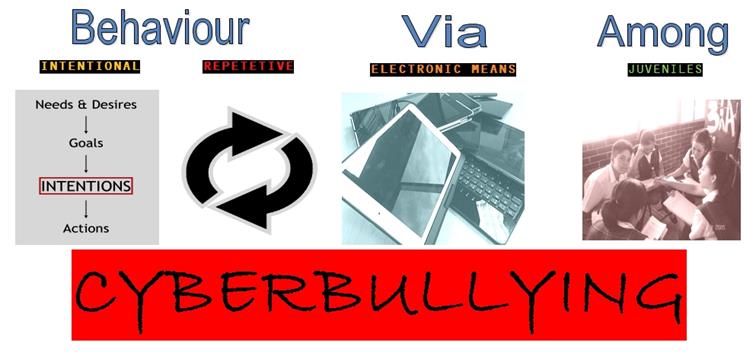
The professor of children's mental health at the University of Ottawa, Tracy Vaillancourt, said that "ninety-nine-point-nine per cent of bullying behaviour is repetitive. Being called a name once isn't being bullied." So the iterance of the act is a factor.
Forms and methods of cyberbullying include:
- Rumour Spreading and Denigration – to falsely discredit the victim
- Physical Threats – that is usually illegal
- Impersonation / Identity Theft – an example of this would be creating a fake profile for the victim
- Trolling – posting or sending hurtful messages to the recipient
- Humiliation – posting something that will (publicly) embarrass the victim
- Exclusion – leaving someone out from a group in a purposeful and cruel manner
- Instigation – inciting others to gang up against particular person
Social Networking
The culture of being socially connected adds to the problem for sure – 22% of teens not using social networks had been cyberbullied, while the number of the those who use such services is as much as 39%. "In fact, youth spend more time with media than any single other activity besides sleeping," said the writer Cloe Maxell. Cyberbullying has become a widespread disease, and for the fact that most Internet users nowadays spend over three hours a day chatting. Although cyberbullying is described as a violation of the terms of service, most social networks have been used for that purpose.
Undoubtedly, youngsters are most endangered to harm associated with cyberbullying. Kids are left unattended, since most parents do not have much of an online presence.Young people can taunt each other about many things: appearance, tastes in music or fashion, habits, social status, etc. Avenues for cyberbullying can occur even in product reviews.
Sadly, there is a little limit and almost no remorse or understanding of their cruel behaviour on and off the Web. A study proves that more than 60% of "digital natives," that is, kids born in the Internet era, are less sensitive to making a difference between jokes or teasing and harassment and invading online privacy. They aren't aware that everything negative they do online can have adverse effects on their lives in the future.
Statistics
- About 18% of young people in Europe had been bullied, harassed or stalked via mobile phones or the Internet.
- 20% of surveyed students admitted to cyberbullying others.
- One million children were harassed, threatened or subjected to other forms of cyberbullying on Facebook during the past year. (Consumer Reports, 2011)
- More girls are cyberbullies than boys (59% girls and 41% boys) (Teen Online & Wireless Safety Survey: Cyber bullying, Sexting and Parental Controls. Cox Communications Teen Online and Wireless Safety Survey in Partnership with the National Center for Missing and Exploited Children, 2009.)
- It is not uncommon for participants in cyberbullying to alternate between assuming the role of a victim and aggressor at different times. After all, 1/3 of the pupils "who had cyberbullied had also been victims of it."
- Girls are more likely to report cyberbullying
- Girls are more likely to gossip while boys prefer to post maligned photos or videos
- At over 84%, smartphones are the most popular technology used for cyberbullying
- Rumours spread (13.4%) and hurtful comments (12.7%) online are reported
- 23% admit that the reason to post something online about somebody else is to entertain others
- Self-esteem has a key meaning because "victims have significantly lower self-esteem than non victims"
- 1 in 6 parents know their child has been bullied via a social networking site (American Osteopathic Association, 2011)
Cyberbullying-related Psychology
The harm that cyberbullying inflicts may have lasting, devastating effects on a person (child):
- Physical problems (e.g., low appetite, insomnia, overall fatigue)
- Mental problems (e.g., low self-esteem, shame, fear, anger, frustration, disillusionment, distrust, withdrawal, seclusion, poor academic performance, depression, post-traumatic stress disorder, suicidal ideation)
Compared to traditional bullying, cyberbullying deprives its victims of the opportunity to retreat to home or another escape haven. In addition, the moment some data that may cause significant discomfort to somebody find its way to the Internet, it can stay there in perpetuity. Once it's posted online, removing defamatory material about a person could prove very difficult. Therefore, "[p]otentially, the effects of cyberbullying are more severe because wider audiences can be reached through the internet and material can be stored online, resulting in victims reliving denigrating experiences more often (JAMA Pediatrics)." That is for sure another aspect that upsets the victims.
Experts in the field calculated that victims of cyberbullying are more than twice as likely to be afflicted with mental disorders in comparison to traditional bullying. Thus, adolescents who suffer from mental disorders are especially vulnerable to this tech threat, as they are at moments unable to shake it off. Still, one should know that even persons in perfect mental health and mature thinking can be affected under given circumstances. No one is immune here.
Despite all the negative emotions associated with being a victim of cyber harassment, there can be positive by-products as well. People who have suffered cyberbullying "created a cognitive pattern of bullies, which consequently helped them to recognize aggressive people."
Suicidal Tendencies
Cyberbullicide is a term coined to designate a suicide influenced directly or indirectly by experiences with online aggression.
Cyberbullying contributes to grim statistics, since victims of traditional bullying are 2 to 9 times more likely to consider committing suicide, and cyberbullying causes stronger suicide ideation than the traditional form, according to a study published in JAMA Pediatrics. Consequently, middle-school victims of cyberbullying are exposed to higher suicide ideation risks – with some analyses showing that girls are immediately impacted, while boys may have suicidal thoughts after prolonged moments of online tormenting.
Unfortunately, there are many tragic stories about youngsters who commit suicide after enduring cyberbullying. Mortality rate among adolescents worldwide due to suicide is usually worryingly high. The cyberbullying charity Cybersmile Foundation calculated that every 20 minutes a child between 10 and 19 years tries to take away his life in England and Wales, while 20% of the American teens seriously consider suicide and 5-8 % of them make an attempt each year.
As innovative (but probably not innocuous) as it may seem, cases of digital self-harm and self-cyberbullying have been reported as well. It begs the question of whether cyber suicide is possible; perhaps erasing all your cyber presence would constitute some sort of equivalent, which would be much better than killing yourself in real life. Wouldn't that be a therapy then?
A Support Group

It can function as an emotional outlet for victims who will share stories with one another; this kind of therapy would relieve the unpleasant sensation that they are left alone to deal with their nightmares.
!!!Bystanders are not passive observers. Choosing not to intervene is an active choice in itself, which may entail serious consequences.
Fig. 3
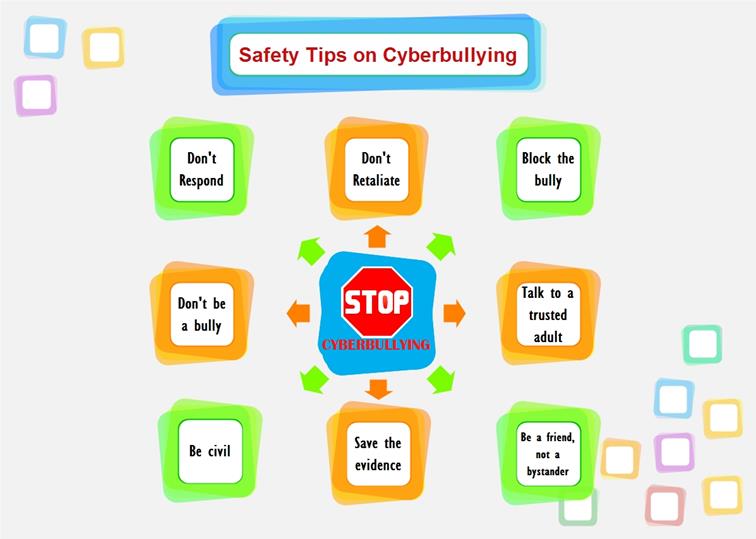
2. Anti-cyberbullying Legislation and Policy
The publication "Why Cyber Bullying Laws Aren't Working in US" draws the reader's attention to existing problems in American legislation and policies regarding the main topic. We can classify these problems as follows:
Liability of Schools
Being the "police" of the classroom, teachers should take part in every prevention or education model. They can be of assistance in dealing with cyberbullying, even more so if the victim-parent-teacher trinity can work together.
Almost all American states have passed cyberbullying laws. Let us see what the law says in states where cyberbullying is more common:
A law in California enacted in 2009 allows schools to discipline, suspend or expel students who harass their mates online and offline.
Illinois criminalized sending electronic communications with intent to harass another person, even if the activity originated outside a public school setting.
In 2010, Massachusetts legislators passed one of the toughest anti-bullying norms in the nation. Physical and emotional abuse are prohibited, and the law mandates special training programs for faculty and students at schools. The school administrators must also inform parents of bullying incidents that happen within the school territory.
In Florida, funding for schools will be withheld if their policy is not in conformity with the local legislation. The bullying prevention laws here apply to both public and private schools.
Error in the language of Florida's cyber bullying statute, however, gives authority only to schools to address it, therefore it is not extended to law enforcement as well. The school competence's would stretch even outside its property, provided the cause impacts the learning environment. Moreover, they must inform parents if their child is involved in cyberbullying.
Liability of Parents
Informing parents can be critical. Once they know about the problem, they may discipline and speak with their child so as to affect him or her positively.
Canada's Nova Scotia has a new law to counteract cyberbullying, which includes provisions that allow obtaining protection orders against cyberbullies and can hold parents responsible if their children engage in the practice. The latter might not be effective, because many parents are busy working, some of them being a single parent, and do not know what their child is doing on the Internet. Perhaps "there would be very few cases where parents know specifically what's going on, that have detailed conversation with their children, and then say it's OK."
There is more to it: kids do not like to confide in their parents that they are victims. Something should be done "to make it easy for them to tell adults even when it's not a big deal because by the time it is a big deal a lot of damage has been done."
School administration has no interest in declaring openly social issues among their pupils. Also, in most states, schools may not have authority over events that occur outside its ground. The father of a daughter who was suspended from school in California for posting a video on YouTube in which she and her friends make sexual comments about another schoolmate had recourse to an attorney in order to deal with the situation. "What incensed me was that these people were going to suspend my daughter for something that happened outside of school…The school doesn't have that kind of power. It's up to the parents to discipline their child," he said.
A reaction like this may startle the school administration and dissuade it from taking more decisive disciplinary measures to tackle cyberbullying.
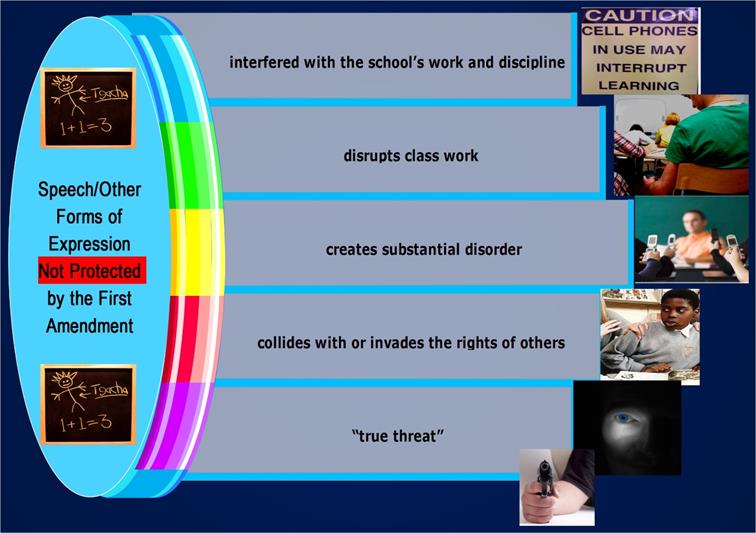
The Tinker test, a well-known litmus rule of the 1969 Supreme Court case of Tinker vs. Des Moines Independent Community School District, acknowledged that schools need to regulate speech in definite circumstances. No longer protected is speech or expression that "interfered with the school's work and discipline, disrupts class work, creates substantial disorder, and collides with or invades the rights of others."
The Supreme Court considers spoof profiles that do not foresee considerable interference with school to not be illegal. As to the question to what extent this rule operates, a defamatory profile of another student, for instance, with a chat group consisting of many students may go outside of the margin.
The following quotation paragraph will shed some light on when offenders forfeit their freedom of speech privilege:
Speech or other forms of expression loses its protection under the First Amendment only when the conduct "substantially interferes with requirements of appropriate discipline in the operation of the school." Conduct that is considered disruptive, foreseeably disruptive, or that poses a "true threat" does not fall within First Amendment protection. For example, in D.J.M. v. Hannibal Public School District #60, a student made alleged threats to shoot other students and sued the school for violating his First Amendment right for his subsequent suspension. The court held that the speech constituted a "true threat" statement.
Fig. 3 A Visualization of the Tinker Test
Distributing Images

There is an ongoing debate of whether adolescents who share nude pictures (so-called sexting) should be charged with possession and distribution of child pornography materials. Lawyers may challenge these charges, however, on the grounds that the purpose of legislation is to punish pedophiles, not children.
Identifying the real motives behind students' behaviour is always important. Students may distribute hurtful images online without forethought. On the other hand, if the photos were disseminated intentionally and without consent given from the owner, the whole deal can fulfil the factual elements of criminal offences such as cyberbullying, stalking, blackmail, extortion, sexual harassment, or distribution of child pornography.
If a probable cause of criminal violation occurs, students should be put on notice that their smartphones will be examined for inappropriate content in violation of school policy.
Liability of Law Enforcement
While schools have a rather auxiliary function that is hoped to work, law enforcement is entrusted with a duty to root out the cyberbullying problem. The chances that law enforcement and legal actions need to be taken increase diametrically if bullying is repeated, threats seem more real, and methods are more dangerous. Making threats by itself is a criminal act under 18 U.S.C.§ 875(c).
Never mind the legal levers, online tormentors are often not charged with the cyberbullying law of their state (if applicable), and instead they receive counselling or perform community service. To exonerate cyber bullies, the defense is often based on the "pre-existing mental illness" plea. Their goal, of course, is to suggest a reasonable doubt with respect to the fact that the victim's harm may have been done owing to a mental illness that had taken root even before the beginning of bullying.
However, a research study by the Journal of the American Medical Association established a definite correlation between cyber bullying and suicide ideation in teens. Besides, "as a matter of law, the existence of a victim's disability does not legally excuse a defendant's criminal actions. Under many statutory schemes, it serves to aggravate the offense, rather than mitigate it (words by the District Attorney Elizabeth Scheibel)."
And even if students have disability, educational institutions must ensure that they have equal educational opportunities and are not subjected to disability harassment, as envisaged by Section 504 of the Rehabilitation Act and Title II of the Americans with Disabilities Act.
Canada's anti-cyberbullying Bill C-13 empower police to investigate cyberbullying incidents by exerting unprecedented levels of surveillance. Greater access to metadata that ISPs and phone companies store on every email or call allows polices to locate the geographic position of a suspect. Yet many privacy organizations raise a voice against that anti-cyberbullying legislation.
Liability of ISPs
A current ruling in the UK prescribes that Internet Service Providers (ISPs) are liable for inappropriate content on websites they host. According to this precedent, any ISP must take complaints seriously and conduct an immediate investigation. And time can be a factor, because most ISPs discard the IP subscriber data within a week to 30 day period.
3. Conclusion: Tough Law is not enough
The problem with the harsh law is that it aims to establish criminal and punitive measures (secondary and tertiary prevention policy) instead of addressing the attitude and actions of the wrongdoers beforehand (primary prevention policy).
With regard to the recent changes in New Zealand's cyberbullying legislation, Microsoft suggested that the local government should provide instead education campaigns, online self-help tools, and an independent agency to act as an intermediary between victims and alleged offenders.
Legislators need to take into account the way people, especially teenagers, view and make use of social media, as suggested by the law professor and director of the cyberbullying research project Define the Line Shaheen Shariff. Not every sexually suggestive photos should be in conflict with the law if they are not posted without consent or without malicious intent. Shariff opines that "a lot of time [young people] are just going to be part of a peer group and entertain each other and test the social boundaries and their sexuality." Therefore, legislators need to possess "a better understanding of how young people are thinking these days."
The Daily Mail journalist Emily Jupp points out in the same spirit that "in an attempt to protect people, we risk curbing their right to be offensive, inane, or downright ridiculous. Even more worrying is Section 127 of the Communications Act, which suggests if you re-share or retweet something that breaks the law, you commit the same offence."
Laws and policies will not probably decrease the cyberbullying surge, because teens tend not to be deterred by such formal, arid mechanisms. Those are undoubtedly necessary components, but they should be complemented by prevention and response planning that will give precedence to overall perception of why cyberbullying is a dangerous occurrence that adolescents should be aware of. Marvin Bernstein, chief policy adviser to UNICEF Canada and a former Saskatchewan Children's Advocate, sees that solving the problem in question requires a multi-tiered approach and a sense of collective responsibility.
Reporting
Whether because the wrong has been developing in a latent manner (exchange of personal messages between users viewable only for them); or the onlookers just do what they do, namely, passively observe; or the victim is weak, unable to take action, or feel that it will not help — the result is always the same — cyberbullying remains unreported.
Two years ago, a group of teenagers from New Haven, Connecticut devised an app called "Back Off Bully" (BOB) designed to fight cyberbullying. Victims or witnesses can anonymously report the location, time and details about the accident— information that directly stream into a database where administrators examine common threads in order to break the bully's pattern. Now, BOB is a standard reporting procedure at schools across the state.
Reference List
Benlemlih, A., Fikri, A., Lahbil, S. & Boudihaj (2011). Social Network and Child Safety. Retrieved on 19/05/2014 from http://ayoub-fikri.blogspot.com/2011_07_01_archive.html
bullyingstatistics.org. Cyber Bullying Statistics. Retrieved on 19/05/2014 from http://www.bullyingstatistics.org/content/cyber-bullying-statistics.html
chanks777 (2012). Would you say that to my face? Retrieved on 19/05/2014 from http://chanks777.wordpress.com/2012/09/
Cyberbullying Research Center (2010). Summary of our cyberbullying research from 2004-2010. Retrieved on 19/05/2014 from http://www.cyberbullying.us/research.php
Cyberbullying Research Center. Sexting: A Brief Guide for Educators and Parents. Retrieved on 19/05/2014 from http://www.cyberbullying.us/sexting.php
dosomething.org. 11 Facts About Cyber Bullying. Retrieved on 19/05/2014 from https://www.dosomething.org/facts/11-facts-about-cyber-bullying
Ferman, R. (2014). Cyber-Bullying: Taking on the Tormentors. Retrieved on 19/05/2014 from http://www.huffingtonpost.com/risa-ferman/cyberbullying-taking-on-t_b_5064537.html
Gokulan, D. (2014). Initiative to raise awareness on cyber bullying. Retrieved on 19/05/2014 from http://www.khaleejtimes.com/kt-article-display-1.asp?xfile=data/youthspecial/2014/April/youthspecial_April2.xml§ion=youthspecial
http://nobullying.com. Anti Cyberbullying Laws in UK.Retrieved on 19/05/2014 from http://nobullying.com/anti-cyber-bullying-legislative-matters-in-the-uk/
Maxwell, C. (2014). Cyber bullying: If adults can't cope, what hope do our kids have? Retrieved on 19/05/2014 from
http://www.kidspot.com.au/cyber-bullying-adults-cant-cope-hope-kids/
Mayer, A. (2013). New cyberbullying law has 'larger agenda,' expands police powers. Retrieved on 19/05/2014 from http://www.cbc.ca/news/canada/new-cyberbullying-law-has-larger-agenda-expands-police-powers-1.2434797
Mayer, A. (2013). Cyberbullying bill won't stop online taunts, critics say. Retrieved on 19/05/2014 from http://www.cbc.ca/news/technology/cyberbullying-bill-won-t-stop-online-taunts-critics-say-1.2440785
McNamee, D. (2014). Cyberbullying 'causes suicidal thoughts in kids more than traditional bullying'. Retrieved on 19/05/2014 from http://www.medicalnewstoday.com/articles/273788.php
Patchin, J., Schafer, J. & Hinduja, S. (2013). Cyberbullying and Sexting: Law Enforcement Perceptions. Retrieved on 19/05/2014 from http://www.fbi.gov/stats-services/publications/law-enforcement-bulletin/2013/june/cyberbullying-and-sexting
R.I.S.E & STAND; (2014). Why Cyber Bullying Laws Aren't Working in US. Retrieved on 19/05/2014 from http://riseandstand.net/2014/04/28/why-cyber-bullying-laws-arent-working-in-us/
STOP cyberbullying. Telling the difference: Google yourself. Retrieved on 19/05/2014 from http://stopcyberbullying.org/lawenforcement/google_yourself.html
Su, Reissa (2014). Microsoft Against Proposed Changes to New Zealand's Cyberbullying Law. Retrieved on 19/05/2014 from http://au.ibtimes.com/articles/545272/20140327/microsoft-cyberbullying-law-harmful-communications-bill-new.htm#.U14eDqLEJ7Q
Wikipedia (2014). Cyberbullying. Retrieved on 19/05/2014 from http://en.wikipedia.org/wiki/Cyberbullying
Wikipedia (2014). Cyberstalking legislation. Retrieved on 19/05/2014 from http://en.wikipedia.org/wiki/Cyberstalking_legislation
Wilde, CK (2013). Share Safebook–Cyberbullying Prevention Poster. Retrieved on 19/05/2014 from http://www.3genfamily.com/2013/06/share-safebook-cyberbullying-prevention-poster/
Winterman, D. (2013). Cyber self-harm: Why do people troll themselves online? Retrieved on 19/05/2014 from http://www.bbc.com/news/magazine-25120783
Diagrams
In Figure 1, the first photo from left to right, titled "Intention Flow," is made by Richievk and it can be found here.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
Fig. 2 is based on a graph that can be found in Would you say that to my face? by chanks777
Retrieved on 19/05/2014 from http://chanks777.wordpress.com/2012/09/









