Attacks over DNS
DNS is a naming system used for all devices connected to the Internet or a network. DNS is easy to remember instead of IP addresses for users. It is a method in which domain names are translated into an IP (Internet Protocol) addresses. The DNS works transparently in the background doing the conversions. DNS works as an Internet's directory service with a domain name for each and every IP address. All the information from domain name servers across the internet are gathered and stored in a Central Registry; e.g., search for a website with the domain name www.examplesite.com, the computer's search engine doesn't know the domain name exists or not. Then it converts to the respective IP address and the name location is loaded.
DNS is a type of protocol used to set standards for exchanging information on the Internet and private networks. DNS is a kind of navigation, like GPS for computers. When a new domain name is registered or updated in a DNS server, it takes about 12-36 hours for all the DNS servers to get updated and gain access to the information. The time period is also referred as propagation. DNS servers are present within every geographic proximity through each ISP (internet service provider) that maps the domain names for your computer's requests. It also forwards them to other servers.
Domain names in DNS are separated by dots. The last word in a domain name is called the top level domain. The word in the left-most end is known as the host name. It specifies the importance of a host for specific purpose. The words or characters in between the dots are known as labels. The domain entered should be unique, so it is controlled by an authority called registry which is under the service of ICANN. The domain name hierarchy is divided in terms of tree nodes.
How Does DNS Work?
A DNS server or name server is the management device containing large database that connects domain names to IP addresses. This process of mapping can be called DNS name resolution. DNS servers always rely on internet protocols and efficiency of network. The DNS working can be explained as a step-by-step process.
-
Name Entry: Domain name of the site should be entered in the search engine. Then a query is created to access the DNS.
-
Requesting Information: The place the computer looks first is the DNS cache. DNS cache is the location where recently retrieved information is stored. If it is not found there, a DNS query should be performed.
-
Recursive DNS servers: If the information is not stored in local history, then the ISP's recursive DNS servers are queried by the computer. Since the recursive servers contain their own caches, the information is returned to the computer user if found.
-
Root Name Servers: After the unsuccessful recursive DNS server query, the computer queries the root name servers. It acts as like a phone switchboard for the DNS. It answers the questions of each domain name by the IP addresses. It also directs the query to some other server, if the query is not answered.
-
TLD Name servers: Root name servers take the last part of the request and direct the query to TLDs (top level domain name servers). TLDs have their own name servers so, even if the TLDs don't have the information we need, they refer us directly to the name servers containing the information.
-
Authoritative DNS servers: TLD name servers check the next part of the request and search or direct the query responsible for this particular domain. Authoritative name servers are the servers that contains the information about every specific domain. This information is stored in DNS records. Each record has a different type of information.
-
Retrieval of Record: The recursive server retrieves the data or information obtained from authoritative name servers. It then stores the retrieved record in its cache locally. The advantage is that if again someone need the same information, it doesn't need to perform the same process again. Once in a while, the recursive server asks for new copy to update information without being out of date.
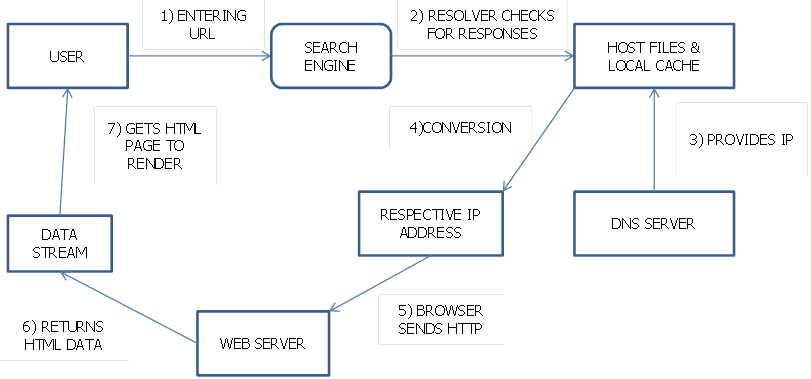
Figure 1: Working of DNS
-
Receiving Answer: The computer receives the record of data from recursive server. It then stores the data record in its cache for future references. The IP address is read and information is passed to the web browser, which will open a connection to the web server, obtaining the website.
The entire process from start to finish will take only very little milliseconds.
How Are DNS Servers attacked?
DNS servers having cyber attacks are the significant threats to the Internet security. DNS attacks threaten modern communications since it is used by many network application, e.g., email, web browsing, ecommerce, etc. The DNS attacks changes are varied due to the ever-growing IT infrastructure. Some of the common attacks are made directly and indirectly on DNS. The attacks are
-
Cache Poisoning Attacks: DNS cache poisoning attack is also known as DNS spoofing. DNS spoofing is a computer hacker attack where the data is introduced in DNS resolver's cache, therefore diverting the internet traffic from genuine ones to fake ones; e.g., the user is sent to malicious site even after entering the correct name. A single attack on the DNS server affects the users attached to that server. The hacker exploits the DNS software. The attacker also uses DNS ID hacking to find the ID number of the user to poison the cache of the user. It is a kind of rerouting domain name to another IP address which may be phishing page of attacker.
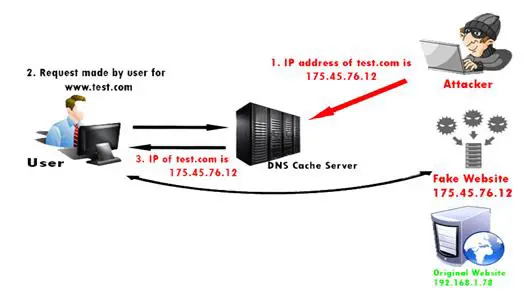
Figure 2: Poison attack
-
DNS amplification attack: This is also called a DOS attack. It is a reflection-based distributed attack. The attacker hides the source of exploit and provides the target. The small DNS query is changed to larger payload. It attacks servers supporting open recursive relay. It may feature a botnet's help to use less bandwidth use for large attacks. The advantage of this attack is that it shows the path as coming from valid servers with valid traffic.
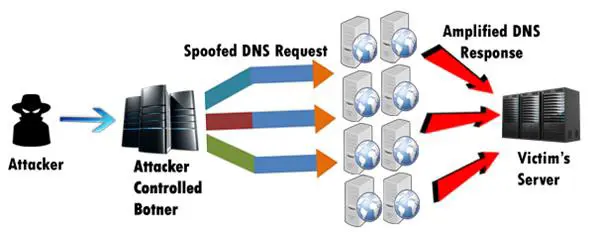
Figure 3: Amplification attack
-
Query redirection attack: This happens when a query is intercepted and modified on the path to the DNS server. If the interception occurs on the way to caching name server, it shows the attack is on LAN. It is different from the mitigation technique since it occurs outside local networks.
-
Zone enumeration: Zone enumeration happens when the user calls DNS diagnostic commands to gain information about the network architecture of a site. It provides a path for the attacker to attack. It can be attacked by knowing the zone information of site, what the site advertising.
-
UDP flood attack: In this attack type, a large number of UDP packets are sent to a random port on the server. This flooded packet confuses the system, causing it to fail.
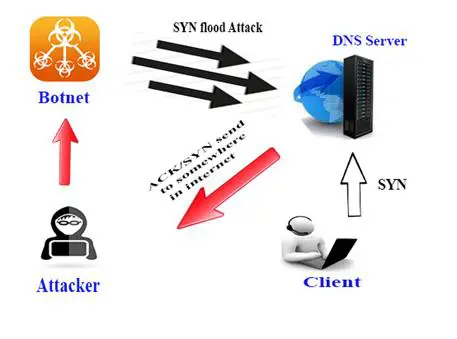
Figure 4: Flood Attack
TCP SYN flood attacks: This is a type of distributed DOS attack that hangs the connection by flooding the DNS server with multiple TCP connection requests. After a certain point the system fails to manage the exceeding number of request, resulting in the server's failure. It also sends SYN-ACKs to many fake destinations. These attacks exhaust the memory. Thus this stops request coming from new connections, even from legitimate server users.
-
DNS fast flux: In this attack type, the ability to change the location of any DNS, web, email or distributed service from many computers connected to internet to some other different set of computers for delaying and evading detection.
-
Registration change: this is a difficult type of attack, where the domain's registration is taken over and the authoritative name servers are changed. An attack like this affects globally cached DNS servers. Among the other features of this attack is that the data can be changed.
-
Cyber squatting: In this attack, a domain name is registered with the intent of profiting and undermining a third party. It is used to steal identity and divert of traffic.
-
Tunneling: DNS is used as covert communication for bypassing the firewall. It helps to tunnel IP traffic without any detection. It acts as a full remote control channel. It even helps to bypass captive portals to use Wi-Fi service and also data exfilitration.
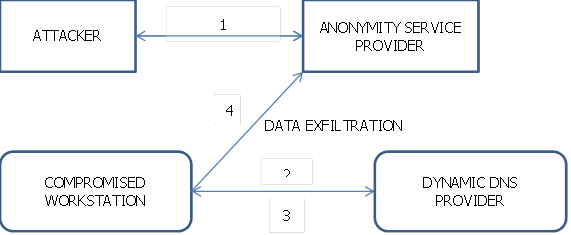
Figure 5: Tunnel Attack
-
DNS hijacking: In this attack, DNS records are modified to some rogue servers. This method helps to acquire personal details of user like passwords, credit card information, and user names.
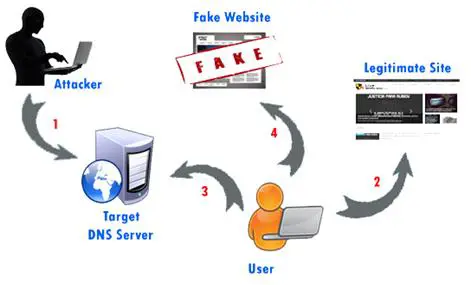
Figure 6: DNS Hijacking
-
Random sub domain attacks: In this attack, infected users or clients create queries by sub domain strings to the domain of the victim. It makes it harder to detect and many of these infected send requests. It thus targets the authoritative server.
-
Phantom domain attack: This attack is setup for an attack where the DNS resolver will be trying to resolve all domains that are phantom domains. These domains are slow and will not send responses. This will consume resources for waiting the responses.
-
NX domain attack: In this attack, the attacker sends many queries to the DNS server for resolving a domain name. The recursive server for locating a non-existing domain carries out multiple queries, causing the cache to be filled with NX Domain. this creates a longer time for genuine requests and also resources for finding a resolution result of query.
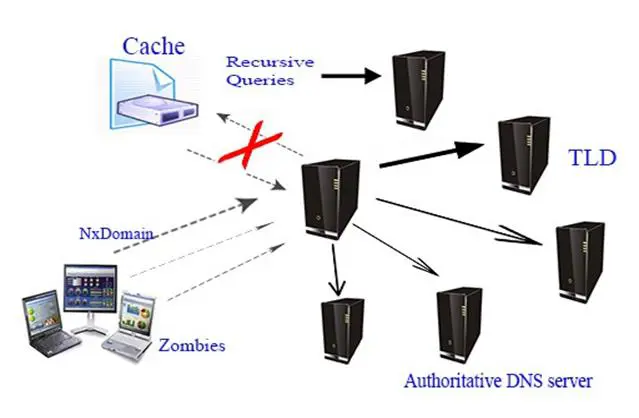
Figure 7: NX Domain attack
How to Avoid DNS Attacks?
-
Hosting of authoritative servers on their own organization helps to protect from registration attack.
-
Traffic controlling along with monitoring and configuration will help to reduce the DNS tunneling; i.e., attacks from TCP and UDP transport mechanisms.
-
Separate out functionality between recursive servers and authoritative name servers, thus preventing the external user from attacking the recursive resolver.
-
Use of DNSSEC with validation enabled in the recursive resolver will help the mitigation.
DNSSEC: It is a most important security suite. It provides clients with original authentication of data in DNS and integration of data. It works by signing digital records by public key cryptography. The record is authenticated with set of public keys that are verified for DNS root zone.
-
New addresses should be checked minimally against all black lists and whois registry.
-
Split DNS views by running both internal and external servers.
-
To prevent spoofing, forbidding recursive queries helps.
-
IP-based ACLs provide protection to DNS servers.
-
Training program with solid social engineering is also effective.
-
Limiting of rate and blocking specific open recursive relay servers, along with tightening security of DNS server.
-
Only data of the requested domain should be stored.
-
A separate management port, use of VPN, and encrypted communications help to secure the DNS server.
-
Use of selective packet discards mechanism to control the traffic.
-
Use of cryptographic signatures will help with authenticity. HTTPS will help for validation of server.
-
Restrict the allowed queries and hosts to the minimum. Also restrict queries to requested domain.
-
Set up the best redundancy methods with improvements along the security and performance.
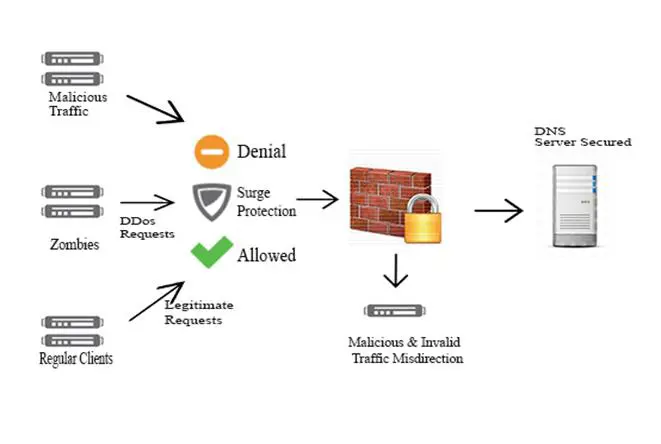
Figure 8: DNS attack prevention
-
Updating of BIND is to limit bug problems and maximize amount of randomness. Bind provides compile-time for storage of zone in all the databases.
DNS Traffic
Traffic patterns in the DNS server will show the malicious activities affecting the server. Traffic due to spoofed addresses in the DNS server while requesting query shows the infected hosts on the network that are engaged in an attack. It may be due to many attacks, like TCP/UDP or DDoS attack. The fast flux, NX Domain, and phantom attacks cause large delays that cause heavy traffic that will also attack the recursive servers. Cache poisoning, amplification attack, covert channel, etc., cause traffic to local networks.
DNS Traffic Monitoring
The traffic can be monitored using security systems and name resolvers. Traffic monitoring is a real-time function. Some methods of traffic monitoring are:
Firewall: Primarily, firewalls help us to prevent IP spoofing. For protection from DDoS attacks, include a protocol for denying queries coming from outside the allocated space. It thus acts as an open reflector to the name resolver. Inspection of DNS traffic should be enabled for checking malicious byte patterns. It also checks to block name server vulnerable attacks by anomalous DNS traffic.
Intrusion detection system: It composes rules for reporting various DNS requests from malicious and authorized clients. The rules are composed by detection systems like Snort, OSSEC, etc. It also reports attacks from NXDomain responses, responses containing records with short TTLs, queries made from TCP, large attacked DNS responses, some queries to non-standard ports, etc. Intrusion protection helps to both permit/deny mechanisms for services in firewall also.
Traffic analyzers: Analyzers show that for identifying malicious traffic, passive traffic analysis can be carried out. In this process, the DNS traffic between name server and clients is captured and filtered. It is then saved as PCAP file. Then create some scripts for searching some malicious activities in the file.
DNS monitoring: It is always best to monitor DNS traffic of our environment to identify any suspicious activity within the organization. Monitoring of DNS traffic can be done by using an SIEM. SIEM has the capability to visualize the traffic and identify any anomalies in the network. Automated alerts can be configured in SIEM to fire alarms which needs an attention there by to provide immediate response.
Conclusion
The DNS server is a globally used method for connecting to the Internet or network. It decouples the name used by humans from IP addresses to access the information. DNS also decouples logical names from machine names and the names are not even related to routing. The DNS name servers have distributed databases with very simple database mechanisms. It doesn't lose consistency in logging of records. The DNS servers are strict hierarchical databases with zone conceptions to reduce delay. It also has a high survivability due to the replication within one zone. The DNS server performs caching for improving performance. DNS has become a key component in internet and network but survivability and security the key issues.

What should you learn next?
References
- http://www.itworldcanada.com/article/3-dns-attacks-and-how-to-thwart-them/84214
- http://searchsecurity.techtarget.com/tip/Types-of-DNS-attacks-reveal-DNS-defense-tactics
- http://computer.howstuffworks.com/dns.htm
- http://www.darkreading.com/attacks-breaches/monitor-dns-traffic-and-you-just-might-catch-a-rat/a/d-id/1269593
- http://www.networksorcery.com/enp/protocol/dns.htm
- http://searchsecurity.techtarget.com/answer/Using-DNS-monitoring-to-detect-network-breaches
- https://technet.microsoft.com/en-us/library/cc772774(v=ws.10).aspx
- https://www.bytemark.co.uk/support/document_library/dnsworks/
- http://cr.yp.to/djbdns/intro-dns.html










