Insecure Data storage with NoSQL Databases
In one of our previous articles, we discussed how Android applications could be vulnerable to insecure data storage. This is a follow-up article to that, as we are going to discuss another flavor of insecure data storage here.
NoSQL is being widely adopted by large enterprises. Giants like Google and Facebook are using NoSQL for managing their "BIG DATA." NoSQL is moving towards mobile world as well. NoSQL databases are available for mobile applications as well. Though we see couple of NoSQL solutions for Android here and there, Couchbase Lite is a good solution, which is being used for local data storage in both Android & iOS.
Similar to other insecure data storage concepts that we discussed earlier, even NoSQL data that is saved in clear text format can be accessible to others using various techniques such as "rooted devices," "backup techniques" etc.
This article will demonstrate this with a sample application.
NoSQL demo Application functionality
Let us first see the application functionality.
Launch the application. This will show a screen as shown below.
A user can enter his card number into the app and click the submit button.
If everything goes well, the user will end up seeing a success message as shown below.
A look at the source code
In this example, the user-entered data is stored in the form documents.
Below is a sample code snippet taken from the code used to build the demo application.
[plain]
String dbname = "carddetails";
// create a new database
Database database;
try {
database = manager.getDatabase(dbname); //manager is an object of Manager class.
} catch (CouchbaseLiteException e) {
return;
}
String cardnumber = editText.getText().toString().trim();
Map<String, Object> data = new HashMap<String, Object>();
data.put("cardnumber",cardnumber);
Document document = database.createDocument();
try {
document.putProperties(data);
} catch (CouchbaseLiteException e) {
}
[/plain]
The code above creates an object of HashMap to hold the name-value pairs. Then, we create a document and insert the data into that.
Testing for NoSQL data:
Let's install our target app in an emulator and insert some sample data into it. Then we will see where and how the app is storing the data we entered.
As we always do, let's first get a shell on the emulator.
Type the following command to navigate to /data/data directory.
[plain]
cd data/data/
[/plain]
Now, let's navigate to the location of our target package. We can find it from AndroidManifest.xml file using APKTOOL.
In our case, we need to run the following command.
[plain]
cd com.androidpentesting.couchdatastorage
[/plain]
Let's run "ls" command to see the subdirectories
[plain]
root@generic:/data/data/com.androidpentesting.couchdatastorage # ls
cache
files
lib
root@generic:/data/data/com.androidpentesting.couchdatastorage #
[/plain]
There are a few interesting directories. However, we don't have any directory with the name "databases." Usually, Couchbase Lite stores its data inside the "files" directory.
So, let's navigate to the files directory and again see the files inside it.
[plain]
root@generic:/data/data/com.androidpentesting.couchdatastorage/files # ls
carddetails
carddetails.cblite
carddetails.cblite-journal
root@generic:/data/data/com.androidpentesting.couchdatastorage/files #
[/plain]
We can see the file with the ".cblite" extension. This is the database file that is generated by our target app.
Let's pull this file out on to the workstation to explore further.
[plain]
root@generic:/data/data/com.androidpentesting.couchdatastorage/files # pwd
/data/data/com.androidpentesting.couchdatastorage/files
root@generic:/data/data/com.androidpentesting.couchdatastorage/files #
[/plain]
I am using the "adb pull" command to get this file onto the workstation as shown below.
[plain]
srini's MacBook:Desktop srini0x00$ adb pull /data/data/com.androidpentesting.couchdatastorage/files/carddetails.cblite
1027 KB/s (114688 bytes in 0.108s)
srini's MacBook:Desktop srini0x00$
[/plain]
Well, now the interesting stuff.
We need a client to view the content of the database extracted.
Couchbase Lite Viewer is an application available for Mac OSX to view the content of Couchbase Lite, and you can download it here:
[download]
After downloading, launch it and open up the Couchbase Lite database.
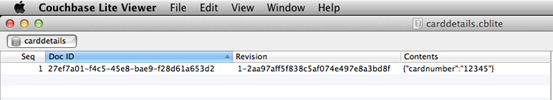
Couchbase Lite Viewer displays the content of the file as shown in the figure above.
If you don't have a Mac, you can use strings command as shown below.
[plain]
srini's MacBook:Desktop srini0x00$ strings carddetails.cblite | grep '12345'
1-2aa97aff5f838c5af074e497e8a3bd8f{"cardnumber":"12345"}
srini's MacBook:Desktop srini0x00$
[/plain]
Hex-Editor is another option if you can't manage to get the strings command working on a Windows machine.











