A Project Management Guide to Deploying Biometrics: The Basics
Overview of the Last Article
Our last article examined the concept of E-Voting, and how it is taking precedence worldwide. Essentially, many nations around the world, especially those in the developing regions are quickly implementing an E-Voting based infrastructure.
All of us to some degree or another, are used to casting our ballot in an election the old fashioned way, either filling in the ovals with a specialized black color pen or punching a hole to make our selections. But with E-Voting, a special kiosk is devoted so that a voter can cast their ballot electronically via the use of a touch screen.
Obviously, there are some advantages with this in that a vote can be cast in just a matter of a few minutes. They can be tabulated in a much shorter time rather than having to manually count the responses on each ballot and to some degree, there is an audit trail created by the citizens who have voted.
But in most of these E-Voting infrastructures, the kiosks are networked together, and connected to a central server(s). Because of this interconnectivity, it is prone to a number of Cyberattacks, which include the following:
- Adware/Malware/Spyware attacks
- "Buggy" Software attacks
- Insider attacks
- Man In The Middle attacks.
Pretty much all of the Biometric modalities can be used in an E-Voting infrastructure, with the exceptions of Keystroke Recognition, Retinal Recognition, and Voice Recognition to help combat these security threats.
It is also important to keep in mind that E-Voting does not take place physically at the kiosk, it can also transpire remotely as well from a wireless device, or even a Smartphone, provided that the right applications are available. In these situations, the chances of a Cyberattack become even greater.
As a result, the need to further confirm the identity of the individual casting his or her vote becomes of paramount importance, as well as securing the connection between the application and the E-Voting infrastructure.
In this regard, use of BioCryptography can be used to bolster the lines of defense. Specifically, the use of an OpenVPN was closely examined. This is basically a subset of the Virtual Network Interface (VNI). As it was also reviewed, the VNI would fit into a Public Key Infrastructure (PKI), using a combination of Public and Private Keys, primarily using the principles of the RSA mathematical algorithm and its associated hashing functions.
Our recent articles have covered a common theme, which are the applications of Biometrics, including the E-Voting infrastructure. But before any major implementation can be further considered, it is the
Biometrics Project Management Overview
Long before the Biometric Modality and its respective hardware and software are decided upon, the C-Level Executive must first have a clear picture of what truly they want out of a Biometric system at their place business or organization.
For instance, apart from providing Physical or Logical access, will Time and Attendance also be a component of the overall needs of the corporation? Or will this fall under a different need category? These questions and much more must be carefully considered and answered by launching four different and succinct Project Management efforts, which are as follows:
- Conducting an exhaustive systems design process
- Analyzing the system requirements with the appropriate development management life cycle
- Defining the specific goals of the Biometric System (also referred to as the "System Concepts")
- Deciding for what applications the Biometric system will be used for. For example, will it be used Physical Access Entry, Logical Access, Time and Attendance, or even a combination of all three of these?
It is important that all of these questions be answered and that nothing is left to haphazard guesswork or even blind assumptions. The framework for this can be answered by using what is known as the "Waterfall Model." This is a very popular approach which is utilized in technical and security based implementations.
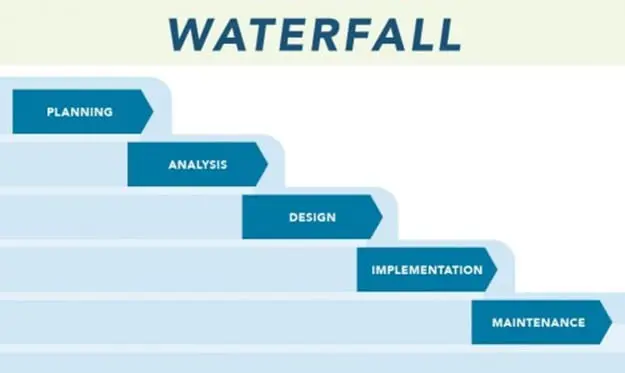
To first develop the systems concept and classification scheme, there are four processes which must be thoroughly examined by both the IT staff and the C-Level Executives. These are:
- Acquire
- Supply
- Develop
- Operations and Maintenance.
In the Acquire process, the C-Level Executive executes the various Requests for Information (RFIs) and Requests for Proposals (RFPs). These rather substantial documents are used to help decide which Biometric technology will be the best fit for each security need.
Regarding the Supply Process, this is where the respective Biometric Vendor(s) come into the decision-making scene. For instance, each Vendor can present and showcase their technologies to the C-Level Executives and even to the head of the IT staff.
In the Develop Process, this is where the actual Biometric system analysis and design starts. The design, the system specifications, the architectural design, and the testing of the proposed modalities takes place at this stage before anything goes live.
Finally, with the Operations and Maintenance Process, the Biometric system is finally used for its intended purposes and applications, and must also be maintained. This includes the exact monitoring of the Performance and KPI metrics.
System Design Interoperability Factors and Considerations

There are three main topics which are of importance when considering the Systems Design aspect in the procurement and deployment of a Biometric system, and they are as follows:
- The Infrastructure Assessment
- Human Factors/Ergonomic Issues
- Evaluating the Feedback System
- Population Dynamics.
The Infrastructure Assessment
The Infrastructure Assessment involves a careful analysis of the following components:
- The Physical Infrastructure
- The Platform Infrastructure
- The Network and Directory Infrastructure
- The Database Infrastructure.
With Physical Infrastructure, this aspect must be considered very early on in the decision-making process. This part examines the physical premises, power capacity, the blueprint layout, as well as any types of enhancements that need to be made to accommodate the specific Biometric modality which will be deployed.
For example, special lighting may be required for a Facial Recognition system, or there could be different mounting heights that need to be considered for a Fingerprint Recognition system.
Regarding the Platform Infrastructure, this is also a crucial support that needs to be considered very seriously. For example, the chosen platform needs to be able to provide enough processing power to meet the high demands and speed of the Biometric system, especially when it comes to conducting the Verification and Identification transactions.
The chosen platform must also be compatible with the hardware and the software which are being supplied by the Biometrics Vendor.
With regards to the Network and Directory Infrastructure, it is also very crucial to have support bandwidth which will provide enough capacity and throughput for the quick transmission of the Biometric Templates. The raw images which are captured will be different from the point at which the Verification and Identification transactions (as well as the threshold decision making) occurs.
Thus, there can be no bottlenecks whatsoever in the network if Verification transactions are supposed to occur in just two seconds. Also, if the Biometric is integrated or coupled into a directory structure (such as that of the Microsoft Active Directory), the choice of communications protocols to be also used becomes of prime importance.
Finally, the Database Infrastructure is there the Biometric Templates will be stored thus the choice of the software and the design of the Biometric system are of utmost importance. Also, key questions such as who will own and manage the database (and especially how the Biometric Templates will be protected) must be fully answered before the Biometric system can even be procured.
Human Factors/Ergonomic Issues
Regarding this phase of the Biometrics Project Management Cycle (Human Factors), the views of other people who are involved and impacted by the Biometric system need to be taken into serious consideration as well. In the end, it is not just the C-Level Executive whom will be affected by the deployment of a new Biometric system, but all of the employees as well at the corporation or business.
These individuals are known as the "stakeholders" and include the following groups:
- The individuals who are responsible for the procurement and the acquisition of the Biometric system (for example, this would include the CISO [Chief Information Security Officer] and their IT staff)
- The individuals that will monitor and run the Biometric system and the supporting technologies (this would be primarily the IT support team)
- The individuals who will be ultimately using the Biometric system on a daily basis (these would be the employees).
The C-Level Executive also needs to take into consideration all of the psychological aspects of the Biometric system before it is procured, and the social impacts that it will potentially have upon all of the stakeholders. Obviously, not all of these issues will be resolved, but if they are at least addressed from the outset, this will help to bolster the end user acceptance of the modality in the long term.
Some of the psychological issues which need to addressed include the following:
- The varying viewpoints and differences towards Biometrics
- Any type of medical conditions or illnesses which could affect and impact both the psychological and behavioral traits of the end user population
- Manual labor jobs, which can affect the quality of both the physiological and behavioral traits of an employee (for example, construction workers often have their hands and fingers impacted and degraded over a period of time because of their job requirements).
Another key component of Human Factors is that of Ergonomic Issues. As it specifically relates to Biometrics, this takes into consideration how to create a Biometric system so that it is comfortable to use for all employees of the business or corporation.
Some of these considerations include the following:
- The height variances and differences amongst the end users
- The frequency of usage of the Biometric system
- The design of the physical space of the Biometric system by giving the end user a sense of privacy.
Finally, another key aspect in addressing the psychological aspects of a Biometric system is to foster an open line of communication between the C-Level Executives, the IT staff, and the employees, and to address any concerns immediately. By allowing this kind of environment to permeate, the adoption rate of the Biometric system will ramp up quickly.
Evaluating the Feedback System
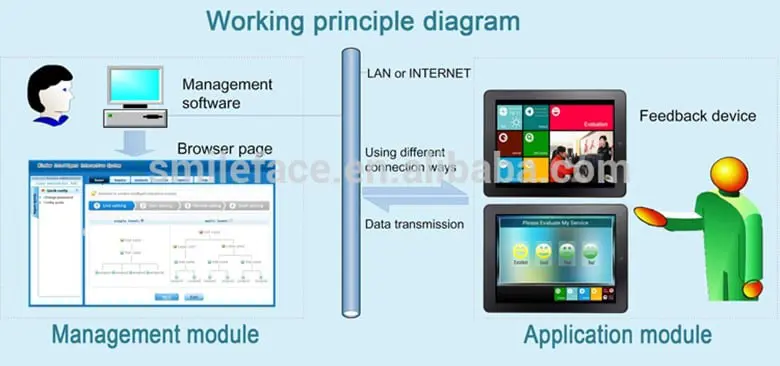
With regards to a Feedback System, the intention is to provide aids (verbal, visual, audio, etc.) for the employees so that it will help facilitate the adoption process to be a smooth and quick one. The Feedback System is composed of the following sub components:
- Audio feedback in different languages to accommodate end users of different cultures and countries
- Process-based visual content (such as that of Infographics) depicting to the end user how to easily enroll their physiological or behavioral traits into the respective Biometric system
- Any type on-screen Graphical User Interfaces (GUIs) which are quick to understand
- Other visual cues (also known as "Passive Feedback") which operate in real time to help guide the employees through other Enrollment and Verification processes which are unforeseen.
It is best to accommodate the employees by offering a combination of the above Feedback Mechanisms. As a result, all individuals with different needs and concerns can be potentially serviced. Equally important are the Change Management mechanisms. It can be defined specifically as " . . . the process of preparing the organization for a new system". (SOURCE: 1).
To make Change Management easy and effective, once again, clear and open communications from the C-Level Executive all the way down to the employees (and vice versa) becomes extremely vital. Thus, it is important that the communication chain starts at a very early stage, even before the procurement process is initiated.
The Change Management process can also be facilitated with the following tools:
- The "advertising" of the benefits of the proposed Biometric system
- Openly addressing the Privacy Rights issues and Civil Liberties fears that employees may have with the new Biometric system
- Keeping employees informed that Enrollment into the proposed Biometric system is not mandatory, and that other options for Identity confirmation will be available (it is important to note that this facet should only be used as an extreme, last resort).
- The preannouncement and initiation of training sessions for the employees giving instruction into the proper way using the proposed Biometric system.
The Biometric Project Management Plan must also take into consideration as to how training will be provided if the corporation or business is very large, and has thousands of employees. Thus, the facet of Population Dynamics becomes crucial.
Population Dynamics

This component of the Biometric Project Management methodology is actually a quantitative based, statistical analysis which examines the capabilities of an end user in using a particular Biometric Modality. From within Population Dynamics, there are two types of variability which can be demonstrated:
-
Interclass Variability:This is the amount of uniqueness, or the degree of distinctiveness, among each end user. A much lower interclass variability means that there could be a potentially escalated False Acceptance Rate, which means that an impostor has been accepted and authorized to use a particular resource at the business or corporation, or even a higher False Enrollment Rate. This happens when an end user simply cannot enroll into the Biometric system.
-
Intraclass Variability:This is the amount of uniqueness or distinctiveness between repeat measurements of the same end user. If this particular variability is high, there could be an escalated rate of false non-matches occurring during the Verification and/or Identification processes.
An important aspect of Population Dynamics is determining which type or kind of Biometric should be used based on the employee size of the business or corporation. A deployment/implementation can be considered to be large scale if the size is 10,000 or greater number of employees. Thus, in these scenarios, there are other special considerations which need to be taken into account by the C-Level Executive. These are:
- Should a Multimodal Biometric system be used to help assure the scalability of a large scale deployment?
- Should the IT staff use the concepts of Winnowing, Filtering, Binning, and Indexing to help with the transition to a larger scale deployment?
- The need to determine the exact network throughput which is required when the Biometrics database is scaled upward.
- Calculating the difficulty in scaling upward the existing Biometric system to the hypothetical largest Biometric system that the business or corporation could potentially support.
- Trying to estimate the per unit cost of the Biometrics database processing versus the total cost of processing the Verification and/or Identification transactions that are needed for the total employee size.
Conclusions
Implementing a Biometric system can either be very easy or very difficult to do, depending upon how the size of the corporation or business. For example, If it is just a very small organization and the management team is examining the deployment of a Single Sign On solution using Biometrics, then this is a relatively easy task. All that is needed are the modalities (either Fingerprint Recognition or Iris Recognition), and for them to be plugged into the workstations of each employee.
But if the Biometric deployment is going to be much larger, then the complexities of it will be much greater. This is where the principles of Biometric Project Management are much needed, to plan for a smooth deployment.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
There are many variables to be considered in these scenarios, both from a qualitative and quantitative aspect. This article touched upon the former, with a focus on employee and other human factor related issues. Our next article will continue into the Biometric Project Management methodology, with more emphasis on the latter aspect.
Sources
- Certified Biometrics Learning System, Module 2. Biometrics System Design and Performance, 2010 IEEE.
- http://www.unhcr.org/550c304c9.pdf
- http://www.unhcr.org/50c85dd69.pdf
- http://seor.gmu.edu/projects/SEOR-Fall09/BEA/BMEA_PMP.pdf
- http://www.cic.gc.ca/English/pdf/pub/biometrics-trial.pdf
- http://www.lse.ac.uk/management/research/identityproject/identityreport.pdf
- http://www.eulisa.europa.eu/Publications/Reports/Smart%20Borders%20-%20Technical%20Annexes.pdf
- http://www.rand.org/content/dam/rand/pubs/monograph_reports/MR1237/MR1237.appa.pdf
- https://www.boozallen.com/content/dam/boozallen/media/file/Biometric-Enabled_Intelligence.pdf
- https://www.microsoft.com/en-us/research/wp-content/uploads/2016/02/thies-persuasive12.pdf
- http://bcs.org/upload/pdf/ashaikh.pdf
- http://www.dematerialisedid.com/PDFs/feasibility_study031111_v2.pdf
- http://www.worldbank.org/content/dam/Worldbank/Event/social-protection/Building_Robust_Identification_Systems_Session_Packet.pdf
- http://www.pmi.org/-/media/pmi/documents/public/pdf/white-papers/value-of-project-management.pdf
- https://www.beat-eu.org/papers/d83.pdf










