Writing Exploit for Mini Share Software: Introduction
In this article, we will analyze another software and develop our own working exploit for it. The software which we will be discussing in this article is called "Mini Share Software." The purpose of this article is to analyze the existing software and from that get the knowledge about the real-world application.
Note: We will not develop any zero-day exploit for this software, we are just taking an old software buffer overflow vulnerability and developing an own exploit for it. One more notable thing here for readers is that this article is based on the previous articles, so kindly read the previous articles first for better understating about buffer overflow exploitations.

11 courses, 8+ hours of training
So, in this article we will be developing an exploit for Windows XP Professional Server Pack 3.
Lab Setup:
The lab setup is the same as we have used in the previous article. We have installed two virtual machines in which the first machine is Windows XP SP 3 and the Second machine is Kali Linux. The XP virtual machine is denoted by "Machine A" and Kali Linux machine is denoted by "Machine B."
About the MiniShare Software:
MiniShare is a Windows program that allows the users to share files without any additional software or services. The shared files can be accessed by anyone using their web browser. So, let's install the MiniShare software on the machine A. The URL to download the software is given in the end of this article. You can download it by clicking on it. The software will look like the one in the following screenshot after installing on machine A, which is the Windows XP SP 3 machine.
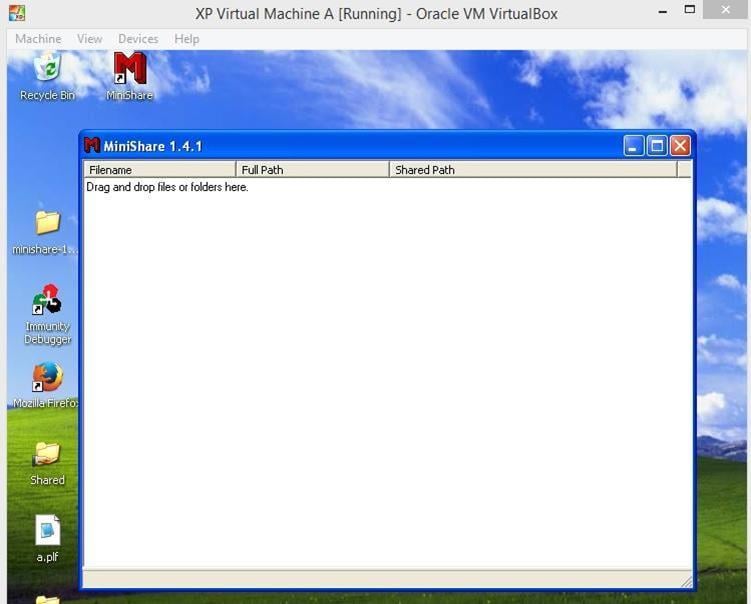
Image 1
The software is successfully installed on machine A. The IP address of Machine A is 192.168.1.208. (Note: It could be changed, depending on the network configuration.) We can access the MiniShare program by typing the IP address in the browser on machine B, which is the Kali Linux Machine. Now, open the URL in machine B.
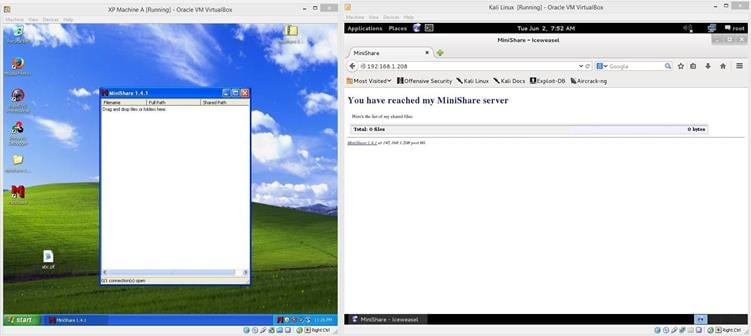
Image 2
As can be seen in the above screenshot, the MiniShare software web client view is now open on the machine B browser, which is on the right-hand side. Now the user can download the shared file by clicking on it. So, this is the basic functionality of MiniShare software, i.e., to share files within a network.
Now let's go ahead and start the exploitation process. The first step in this process is to verify the vulnerability.
Verifying the Buffer Overflow:
Configure the Burp Suite with the browser on the machine B. (If you don't know what Burp Suite is and how it works, just Google it; you will get a lot of tutorials.)
Note: First of all, we will verify the buffer overflow vulnerability by using the Burp Suite. After that we will use python script for further analysis.
When we refresh the page again, the browser request is captured by the Burp Suite. We can see the same in the screenshot given below.
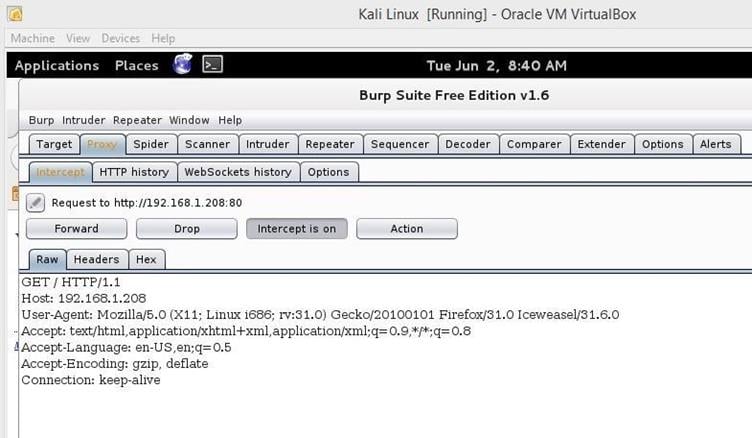
Image 3
Now just right click and after that click on "send to Repeater" or you can press the shortcut key, which is CTRL+R. After that the same request would be sent to the Repeater. Let's put a large number of A's in the GET request, as follows.
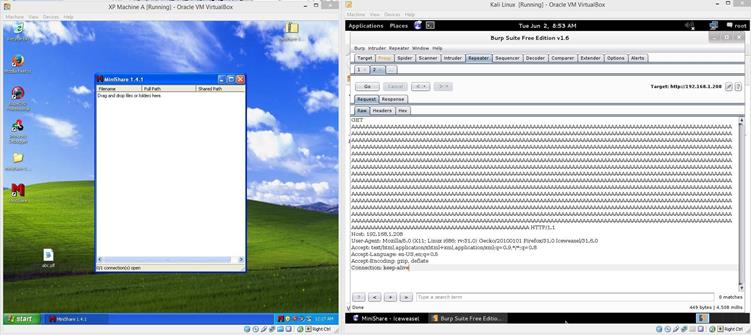
Image 4
As can be seen in the above screenshot, we have successfully edited the browser GET request by inserting a large number of A's with the help of Burp Suite. Now, as we click on go, we will see a popup window opened on the machine A that says "the program encountered some errors and need to be closed." We can see the same in the following screenshot.
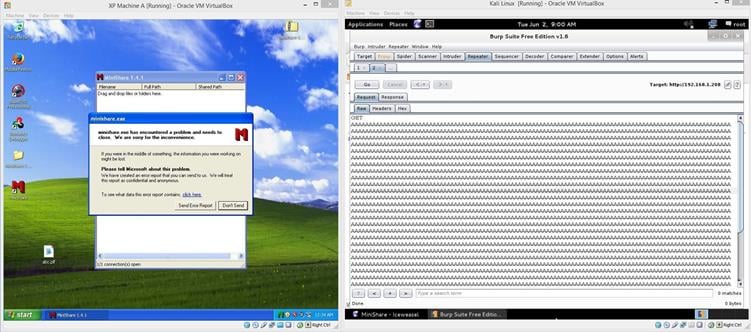
Image 5
After putting the large numbers of A's in the GET request (on Machine B) the MiniShare program crashed on the machine A. Now, click on "Click Here" for further analysis.
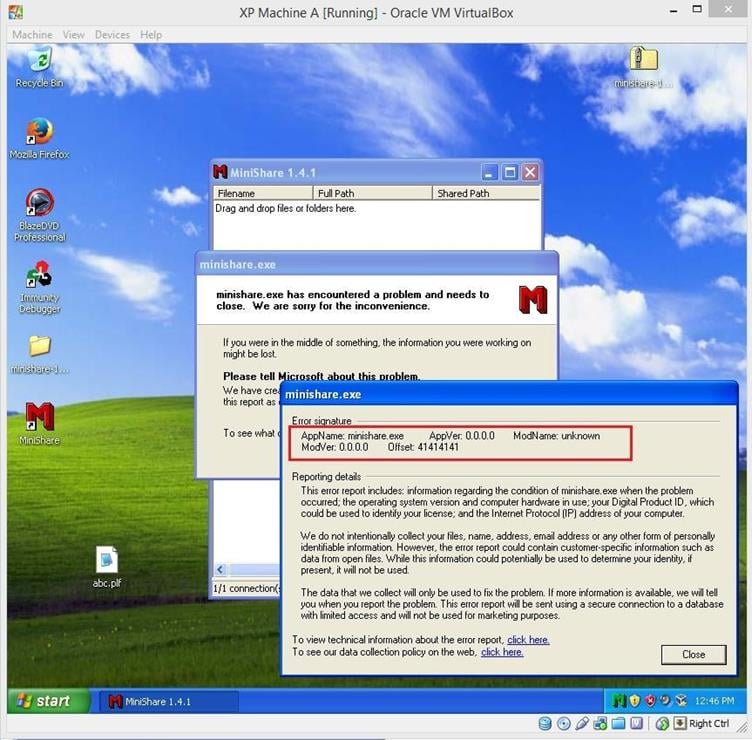
Image 6
It can be seen in the above screenshot that "Offset" is overwritten by 41414141, which is basically our A's in Hexadecimal. It confirms for us that this program is vulnerable to buffer overflow.
We have completed the first step and we have identified that the GET request is vulnerable for buffer overflow attack. Now let's move ahead towards the next step, which is identifying the overwritten position in the user input. In this step, we will be developing a simple python script for creating the GET request.
Identifying the Overwritten Position in User Input:
Now we will have to identify the overwritten position in the user input. It is not possible to write a large number of A's on the Burp Suite every time. So let's create a python script that will do the same thing in a simple and better way.
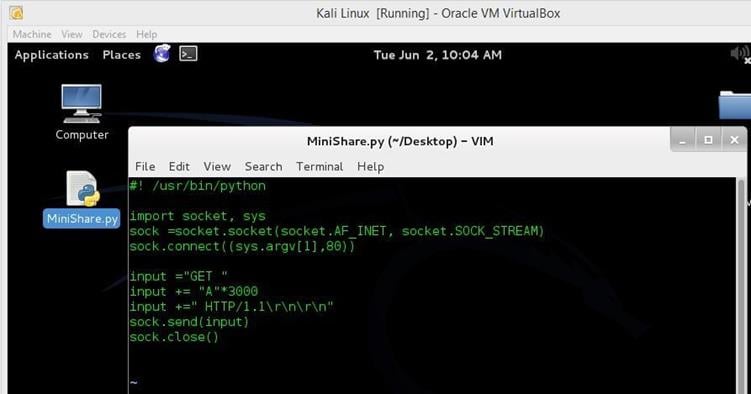
Image 7
As can be seen in the above screenshot, we have created a simple python script that will do the same thing as we did in our previous articles. In this script, the first four lines are to create the remove connection with the machine A, the next three lines are to create the GET request and add 3000 A's in the GET request, and the last two lines send the GET request to the machine A and close the remove connection.
Now we need to run the script on the machine B to verify the Crash.
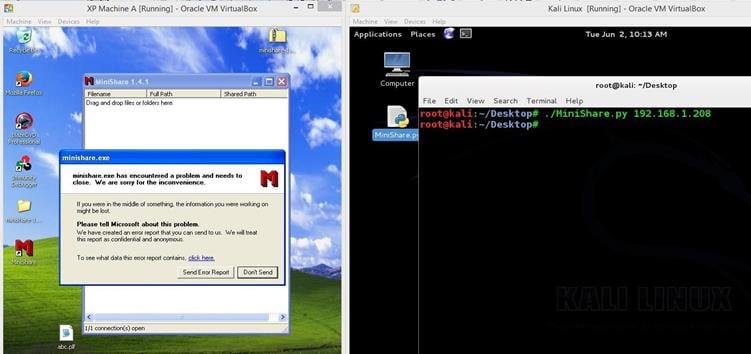
Image 8
As we can see in the above screenshot, we ran the python script on the machine B with the machine A IP address and the program got crashed again. Now we will create the pattern on the machine B by running the following command.
-
/usr/share/metasploit-framework/tools/pattern_create.rb 3000
After running this command, we can see the pattern on the screen as follows.
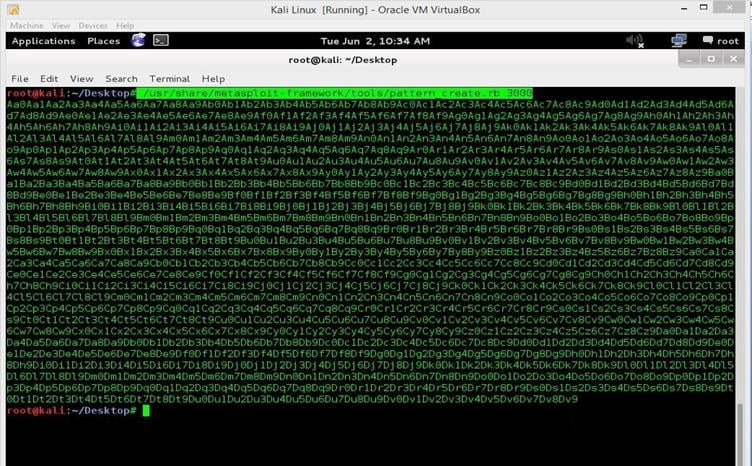
Image 9
Now, we will copy this pattern in the python script in the same way we did in previous articles. So Let's run the MiniShare software with the Debugger and also run the python script again in machine B.
Image 10
As can be seen in the above screenshot, when we ran the program with the debugger and ran the python script on machine B, the MiniShare program again crashed. When we closely look into the debugger we can see that EIP is overwritten with 36684335 and "Top of Stack" is pointing to the value 43376843. You can see the same in the screenshot given below.
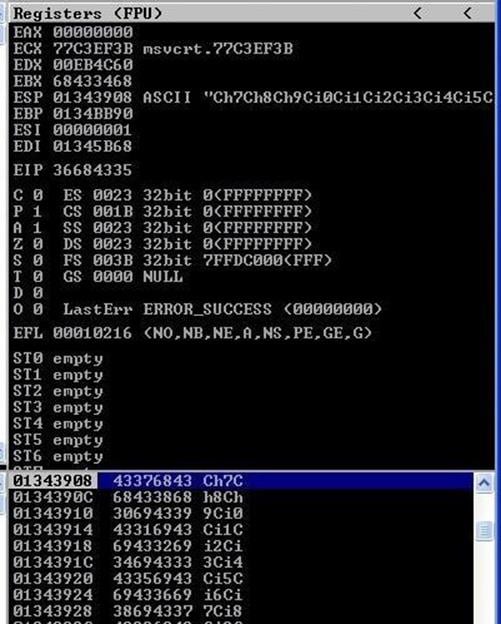
Image 11
Now we will run another command on machine B with EIP and Top of Stack (TOS) to find out the exact location in the user input.
-
/usr/share/metasploit-framework/tools/pattern_offset.rb 36684335
-
/usr/share/metasploit-framework/tools/pattern_offset.rb 43376843
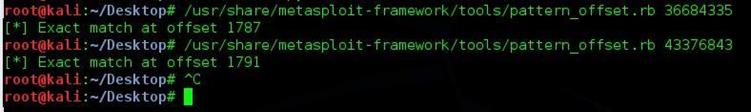
Image 12
As can be seen in the above screenshot, we got the exact match location in the user input. The notable points are following.
-
EIP is overwritten after the 1787 byte or characters
-
Top of Stack is pointing to 1791 bytes or characters
So we have now successfully completed the first two steps and identified the overwritten position in the user input. The next step is to identify the list of the bad characters, according to the software.
Identifying the Bad Character:
Now let's identify the bad characters. The process of identifying the bad character is the same as we did in the previous articles. So let's run the badchar program to generate a list of all the bad characters.
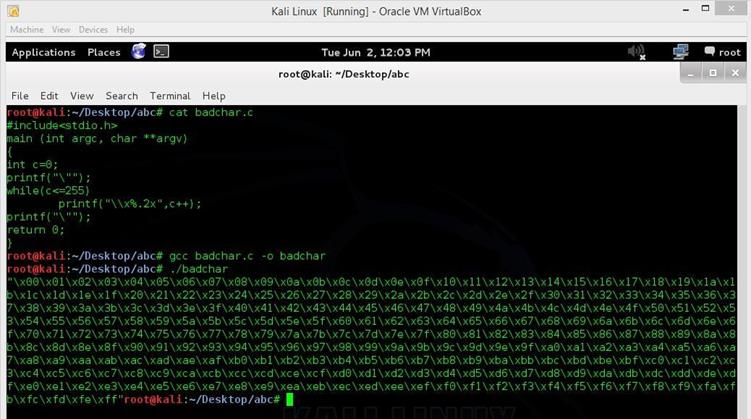
Image 13
As we can see in the above screenshot, we have first written a simple C program, "badchar.c" (you can download this program by clicking the URL given in the end of this article). After that, we have compiled it and run it. Now copy all the character list and paste it into the python script, as follows.
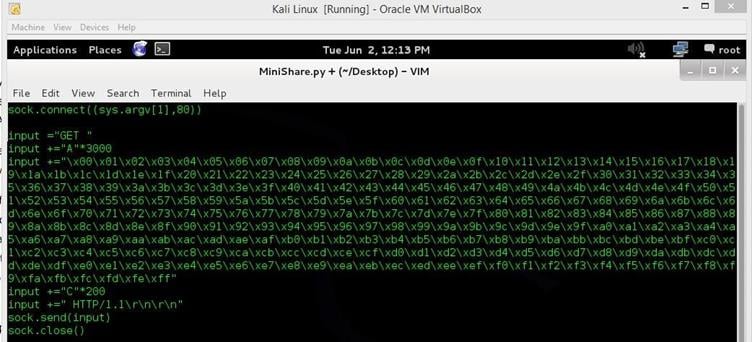
Image 14
As shown in the above screenshot, we have appended the bad character list after the A's. The steps to find the bad characters are given below.
-
Run the python script and analyze the buffer in the debugger if the input breaks.
-
Find the character in the debugger that caused it to break.
-
Remove the character from the list and note down the character in some place and then again go back to the first step.
-
Repeat till input no longer breaks; the rest of the characters can be used to generate the shell code.
After completing all the above steps. We have identified the following bad characters in this software.
In simple words, we can say that, while generating the shell code for this software, we cannot use the characters that we have listed above.
The rest of the steps will be continued in the next article.
References
- https://www.owasp.org/index.php/Buffer_overflow_attack
- http://en.wikipedia.org/wiki/C_file_input/output
- http://www.exploit-db.com/
- http://www.pentesteracademy.com/
- https://www.corelan.be/
- http://en.wikipedia.org/wiki/NOP_slide
- http://www.securitytube.net/
- https://github.com/rapid7/metasploit-framework/wiki/How-to-use-msfvenom







