Security Assessment of a Digital Signage Solution
Digital signage is a form of electronic display used by the organizations to advertise and boost their business. They are often used to display public information, messages, news, advertisement or promotion about a product. This allows the organization to reach broader audiences by placing the display in public places. Some organization uses it in the internal environment to broadcast messages, news, etc. Digital signage solution provides the flexibility of updating the digital content on the go.
The next time you visit McDonalds or Starbucks and notice a display showing an advertisement or their latest menu then most probably it is through a digital media player attached to the display.

11 courses, 8+ hours of training

Image Source: https://i0.wp.com
Architecture
The architecture of the signage solution primarily includes a Digital Media Player (DMP) to play the media, Content Management Software which is used to roll out the media files and playing instructions to DMP, and a display to show the contents. The DMP keeps on polling the centralized server to check the availability of new content or playing instructions. If there is new content available, DMP downloads them to play as specified in the instruction files.
Digital Media Player (DMP): A Digital Media Player (DMP) is a small PC based on an OS like Android, Windows, MAC, Linux, Unix, etc., which can be mounted behind the display. A media player application running on the top of the OS is responsible for showing the media on screen. The Digital Media Player includes the following components:
- CPU
- Motherboard
- RAM
- Storage
- USB
- Memory Card Slot
- USB
- RJ45 Jack for LAN connectivity
- RS232 port for VGA/HDMI connectivity
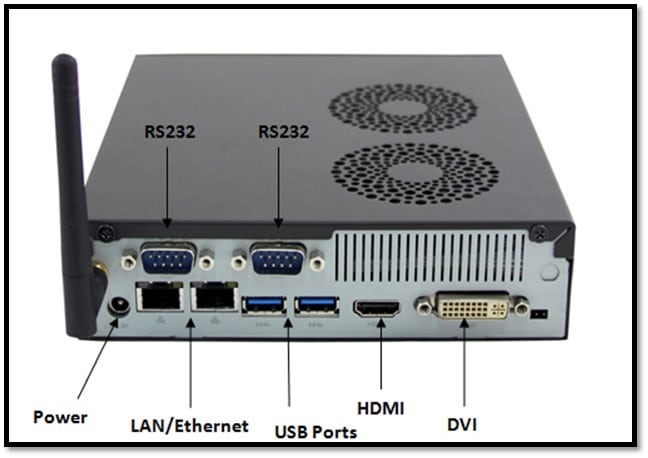
Image Source: http://ie8.ucview.com
Content Management Software: Content management system (CMS) software manages the content that will be transferred to multiple media players spread across a geographical location. This software allows you to schedule the content and playback settings like screen layout, borders, the duration for which the media must be played, etc. This act as a centralized solution from where all the DMPs can be controlled. This includes sending the new media files, playing instructions, the status of DMP (Live or Not), Patch management in some cases. The CMS software can be a browser-based web application or desktop based thick client application.
DMP supports the following (not limited to) contents:
- Image
- Video
- Text
- Animations
Digital Display: The display can be LED, LCD, Plasma monitor connected to the digital media player through VGA or HDMI cable. The digital display/monitor is used to display the media.
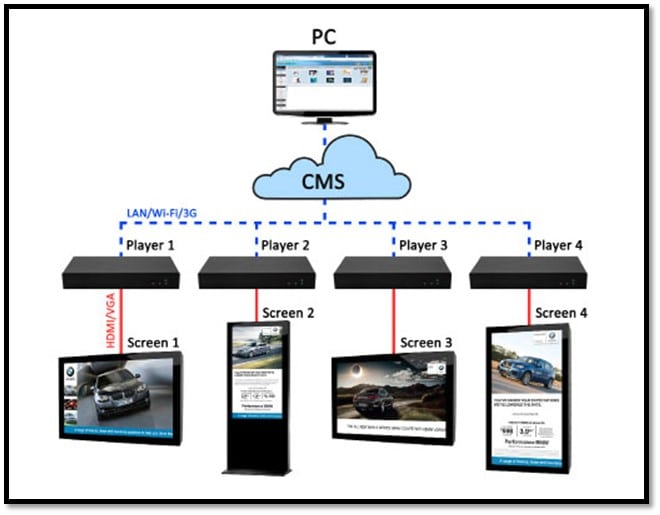
Image Source: http://eco-printshop.co.uk
Threats
Like all other IT solutions, Digital signage solutions are prone to cyber-attack, too. A compromised DMP playing an unauthorized video may result in substantial reputational as well as business loss. There are a few incidents where a signage solution was compromised to play attacker-controlled videos:
- https://www.digitalsignagetoday.com/articles/hacked-digital-signage-displays-porn-in-union-station/
- https://www.digitalsignagetoday.com/blogs/times-square-digital-signage-hacked-again-not-really/
- http://www.dailymail.co.uk/indiahome/indianews/article-4415358/PORN-shown-commuters-busy-Delhi-Metro-station.html
Setup
There can be two types of Signage solution setups:
1. When the content management application is hosted externally (on the internet), the risk of the solution being hacked is increasingly high. There will be more attacker trying to break into the CMS application to temper the existing settings and media file.
On the other side, in case of a virus/malware outbreak on DMP, your critical IT assets remain secure from the infected DMPs.
2. When the content management application is hosted internally (Intranet), the risk of the solution being hacked is reduced. Here, an attacker must compromise a network to reach the application and then to compromise the application further to temper the settings and content. This increases the overall security of the setup.
The downside is that an infected DMP may allow (if the network architecture is not secured) the virus/malware to reach to other critical IT components/system.
Security Assessment
We will discuss the different areas we can look for enhancing the overall security of the digital signage solution.
1. Setup: Identify the environment, i.e., whether you want the setup to be hosted externally or internally. As discussed above, exposing the CMS application to the public would attract more attackers. You might have to purchase a cloud-based service to host the application too.
2. Network: This is an important area to look for when planning to host a CMS application internally. It is mandatory to segregate the rest of the IT network from the signage solution network. Few points to consider:
- Create an isolated environment to host the CMS application.
- Configure a strict firewall rule to access the CMS application and associated servers.
- Hardened the servers as per security best practice. Access to these servers must be restricted.
- Access to the CMS application should be restricted too. The application must be accessible from the limited set of IPs only.
- Antivirus should be configured on all the servers related to DMP CMS application. Antivirus agent should be password protected and configured to download the signatures periodically. Antivirus agent running on the server should be configured to run at least once per day.
- Identify the desktops for accessing or managing the CMS application. The desktop must be patched against latest vulnerabilities and hardened as per the security best practice.
- Internet on the machines managing the CMS application should be restricted.
- All the component should have centralized authentication enabled.
3. Application: The CMS application is the heart of the entire setup and responsible for distribution of media and playing instructions. The security of the CMS application is paramount when the application is hosted externally. Few points to consider:
- The application should be secured against all type of web application attack which allows the unauthorized access to application and Database.
- The application should use a secure channel to communicate. Use of SSL/TLS channel is recommended.
- The application should have a maker-checker functionality. A maker user can create and upload the content, whereas a checker user can approve the addition or modification done by maker user. Make sure the implantation is safe against unauthorized access by tempering the URL or any of its parameter.
- A strong password policy for the application users.
- Added security can be implemented by adding Two Factor authentication.
- If the application is a software-based thick client application, make sure it is using 3-tier architecture. 2-Tier architecture can be compromised by gaining sensitive information by decompiling the application or dumping the memory.
4. Digital Media Player: As discussed above, DMP contains an OS which runs a media player application. It is essential to harden and secure DMP devices and player against unauthorized access. Few points to consider:
- Disable or remove the USB port. A local adversary can control the DMP devices by connecting the USB based mouse and keyboard. This would allow the attacker to enter into boot menu or delete the player application or install the virus/malware, replace the media files, etc.
- The player should have some sort of validation to secure against a file tempering attack. This could be comparing the file checksum. In the absence of the validation, an attacker can replace a legitimate media file with any other unauthorized media file.
- Protect the media player/signage application against force close.
- Access to the media player control should be restricted and authorized.
- Do not hardcode the login credentials of the media controller in cleartext.
- If the contents are being downloaded from the remote server, use an encrypted file transfer protocol.
- If using a file transfer protocol to transfer the media files, don't store the credentials of the remote server in cleartext in a configuration file or registry key.
- Configure the boot menu with a strong password.
- Make sure the DMPs are running on the latest version, and all the latest security patches are applied.
- DMP operating system should be hardened as per the security best practice.
- Remove non-essential services and application from the DMP.
- Disable the memory card slot.
- Disable the access to OS while the media player is running.
- Identify the ports required for the communication and close rest of unnecessary ports on DMP.
4. Physical Security: Physical security of the DMP is required to deter smash and grab tactic. Few points to consider:
- Protect the DMP in a break-proof enclosed space.
- Secure the DMP by installing it on a wall behind the screen. Leave minimum space between the display and DMP.
- Placement of DMP at a height above the reachability of average human.
5. Bandwidth Requirement: It is essential to understand the load on the network caused by the DMP operations. The bandwidth requirement may vary from the organization to organization. Some organization would require multiple media files to be transferred daily, whereas some organizations have a fixed number of digital content. Bandwidth utilization may have following points to consider:
- The bandwidth requires sending the image/video/animation files to an individual DMP.
- The bandwidth requires maintenance or patch management.
- The bandwidth required for Polling requests by each DMP.
Based on the number of files transferred per week and duration of polling request we can check the rough estimation of overall operation:
Total Size of Media Files x Number of DMP = Total data bandwidth
Conclusion
The Digital Signage Solution offers a variety of the features to enhance the business. The signage needs to be secured against known security threats. This is important where the screen is visible to thousands of the people, an unauthorized video uploaded by the attacker may cause a severe reputational loss. The areas discussed in this article can be used as a checklist before implementing a new signage solution or can be used for performing the security assessment of existing signage solution.







