Securing Your WordPress Admin Panel
Today, anyone can create their own website with tools such as WordPress, Joomla or Drupal. However, many people suffer when they do not take precautions to secure those installations. If you look at the jobs in a freelancing website, it is likely that you will see job offers of people telling that their WordPress website was hacked and requesting help to solve the issue.
Below, we will examine how you can secure your WordPress Admin Panel and its associated Login Page. We will start by discussing usernames and passwords and move to enabling account lockouts, serving the login page over SSL, adding a CAPTCHA in the login page, whitelisting IPs that would be able to use the login page, hiding the login page and adding extra layers of protection such as entering two different usernames and passwords to be successfully logged in in your WordPress website.

11 courses, 8+ hours of training
Choose your usernames and passwords wisely, especially for the administrative account
If you are about to install WordPress, do not allow the default administrative account to be called admin. This is the first username all attackers try to exploit via brute-forcing, dictionary, or other attacks.
Figure 1: Setting up an administrative account in WordPress
Even if you pick something slightly different such as iamadmin, it can save you a lot of trouble. When picking a password, be sure that WordPress deems it is strong. Observe the bar below the password and ensure it is green in color.
You have to be aware that even if an attacker cannot gain financial advantage from gaining administrative privileges in your website it does not mean that he will not try to gain such privileges.
Look at the figure below:
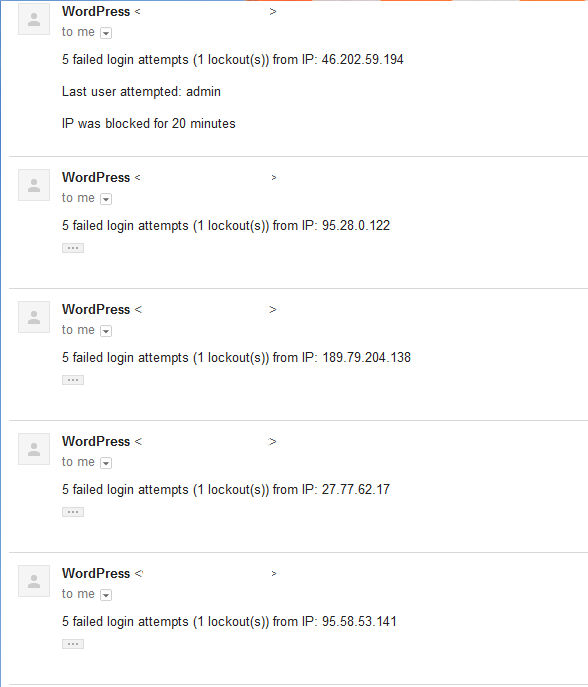
Figure 2 A brute-force or dictionary attack against a WordPress site
In the figure above, you can see an attack against the WordPress admin panel. All lockouts have occurred on the same day and all targeted a possible weak admin username. Dictionaries does not contain that many words for the trial and error process to take that long. So, if you are using the default admin user and have guessable passwords it is highly likely at some point to be hacked.
This is so because WordPress does not ban attackers if they attempt to log in unsuccessfully too many times which gives attackers infinite time to try to log in as administrators.
This brings us to the next point.
Limit the number of login attempts that can be made from an IP for a specified period
If you do not limit the number of login attempts and lockout the IP for a certain time period, attacker scripts can run forever until they find the username and password they are looking for.
A plugin that I like to use is Limit Login Attempts. It has not been updated in 4 years but it works with the latest WordPress version and it still does the job.
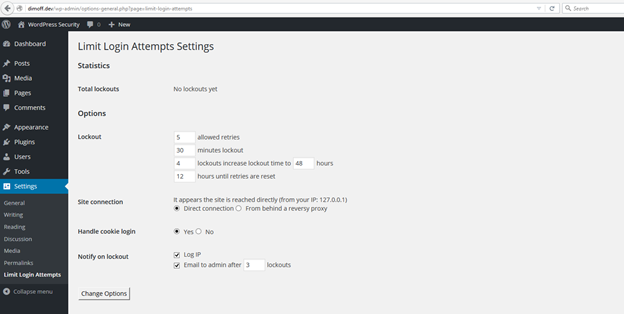
Figure 3: Customizing the Limit Login Attempts plugin
You can choose to log the IP address that failed logging in too many times so you can investigate the attacks and possibly permanently prohibit access to that IP address, you can set the plugin to send you an email after an IP address' login attempts result in a specified by yourself lockouts and you can customize many other details of the lockout process.
I have disabled JavaScript and cookies to try out the plugin in the way that automated cracking tools access web content and the plugin works as expected.
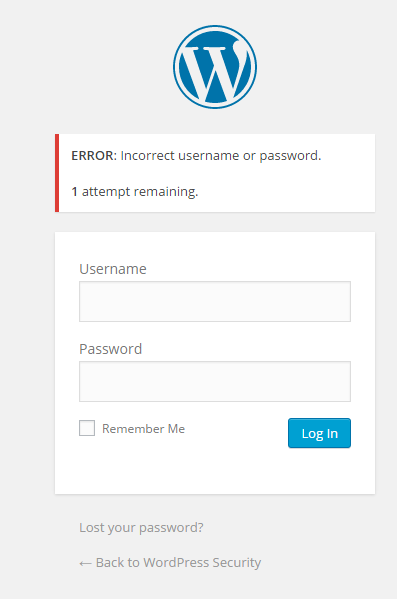
Figure 4: 1 login attempt remains until lockout
After the lockout, even if I type the correct credentials I will not be able to log in which leaves attackers in the dark as they will not be able to know if the username/password combination they are trying is valid or invalid.
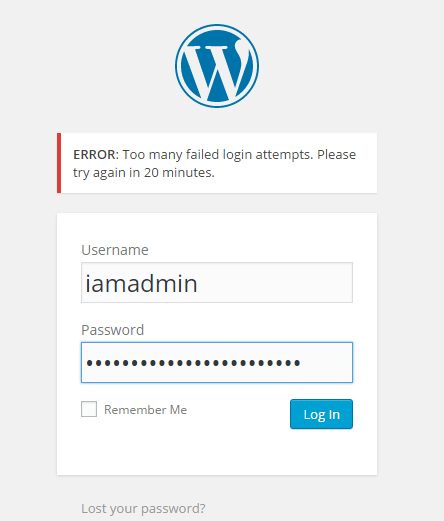
Figure 5:Lockout prevents us to log in even with the right credentials
Force SSL login to prevent Man-in-the-Middle Attacks
No matter if you have multiple users writing or editing your WordPress website there are times when you need to log in to WordPress from a public computer, from a public Wi-Fi or other Internet network. Doing this makes you vulnerable to Man-in-the-Middle attacks. Basically, attackers can listen to the traffic in that network and capture your HTTP request to the WordPress admin panel where you are trying to log in and see the credentials you are using in plaintext. To prevent this, you can use SSL when authenticating yourself or your other users in WordPress. To do this, your page has to be accessible over https. You can test whether that is the case by prepending https to your page, like https://example.com. If you get an error, then you have to buy a SSL certificate and set up your web server appropriately.
But if your website is already accessible over https, you can open your wp-config.php file (it is located in the root directory of your WordPress website), edit it with your favorite editor and add the following lines to the file:
// use ssl (https) for the login page
define('FORCE_SSL_LOGIN', true);
//use ssl (https) for the whole admin area
define('FORCE_SSL_ADMIN', true);
The FORCE_SSL_LOGIN constant would redirect and allow only https to be used when attempting to log in. The FORCE_SSL_ADMIN constant would enforce secure connection throughout the entire admin panel/area.
If you enable one of those, you would always be redirected to https when attempting to log in which will limit the possibilities of someone sniffing your traffic.
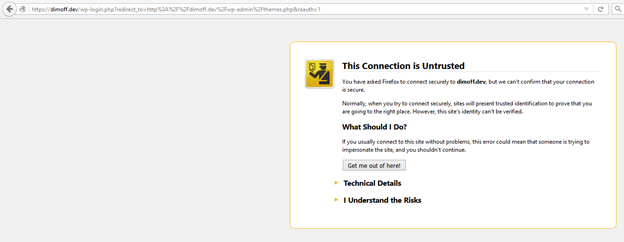
Figure 6: If you do not have a SSL certificate or the server is not configured properly you will get a similar error message
Implement a CAPTCHA in the login page
Implementing a CAPTCHA in the login page can minimize hacking attempts by prohibiting automated scripts from trying to brute-force or performing other attacks on your login page without first being able to solve the problem posed by the CAPTCHA. If you simply open the WordPress admin panel and click on Plugins -> Add New, then type captcha you will be presented with many plugins to choose from.
Let us look at one of the possible plugins. Captcha by BestWebSoft is installed more than 300,000 times and has a good rating (4.5/5). When installed, it creates a new item in your admin menu where you can customize it. It is possible to use it for your login page, your reset password page and of course it may turn useful for comments and user registrations, if they are enabled. You can whitelist IPs which would not have to solve the CAPTCHA and you can customize the messages related to the CAPTCHA such as the message being shown when a user fills the captcha field incorrectly. You can also pinpoint whether you want the CAPTCHA to include both words and numbers or only one of those.
If you simply activate it after the installation, you would have a login form with a CAPTCHA. If the person does not fill the CAPTCHA properly he cannot know if a username/password combination is valid or invalid.
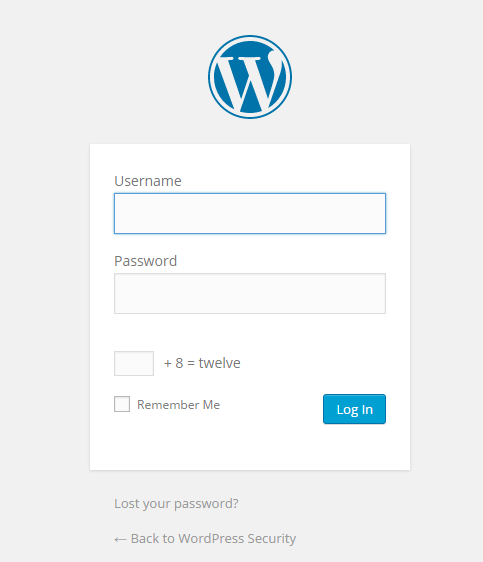
Figure 7: A CAPTCHA on the WP Login Page
Allow only specific IPs to log in
If you have a static IP and know that that your IP would not change frequently you can show the login page only if the user IP is some whitelisted value using the .htaccess file in your wp-admin folder. Even if your IP changes, you would still be able to login by modifying the .htaccess file to reflect the new IP address. You can allow numerous IP addresses if you want to be able to log in from different networks and computers or if you have other persons logging into WordPress.
To do this, you would have to open a FTP connection to the server (or access the files in any other way that suits you) and access the files of your WordPress website. Then you open the wp-admin folder and create or edit a file inside it which has to be called .htaccess (no file name, just an extension) and add the following:
order deny,allow
# Replace 99.99.99.99 with the desired IP address
allow from 99.99.99.99
#allow more IP addresses to access the wp-admin area by uncommenting the line below and editing the IP address
#allow from 98.98.98.98
deny from all
After the allow from keywords, you can add the proper IP address which would be able to login into WordPress. If you want multiple IP addresses, you just copy the allow from 99.99.99.99 line and edit the IP address value.
After you have set up the .htaccess file, users with different than the whitelisted IP addresses would not be able neither to open the login page, nor to use the admin panel.
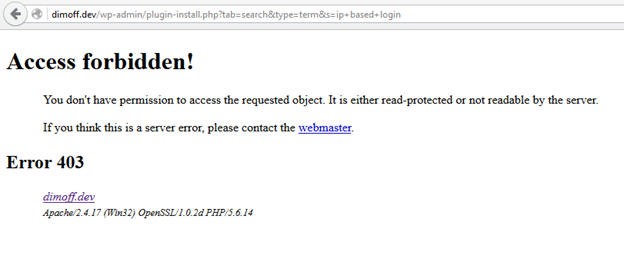
Figure 8: I do not have an allowed IP address and cannot administrate or view the login page
Obfuscate your admin area
If you really feel like the above is not enough, you can try to obfuscate your admin area. You can rename the default URL of the login page to be something different than the default URL of the login page. With the defaults, you can access the login page with example.com/admin, example.com/wp-admin or example.com/wp-login.php. To do this, you can use several plugins. We have chosen to show one of those plugins called WPS Hide Login. Once activated, it creates additional settings in the Settings -> General admin menu in which you can select an URL that will be used for logging in. Users attempting to log in with the traditional URLs will be redirected to the homepage.
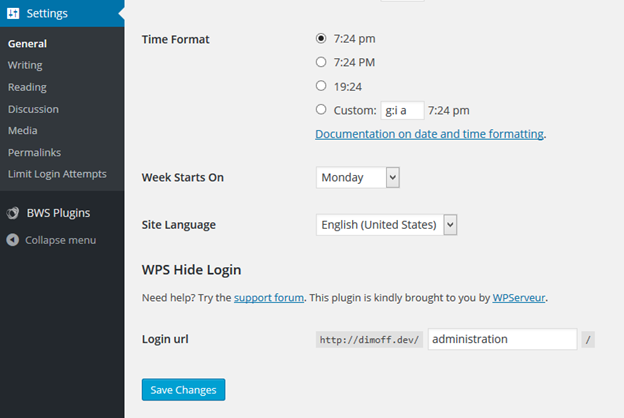
Figure 9: Setting up a new login page with the WPS Hide Login plugin.
Although attackers can still brute-force, guess or social engineer the URL to your admin page it can be a bit discouraging trying to figure out where it is and it will take an extra effort that many may not find worth it.
Adding extra layers of protection to the Login page or enabling Two-Factor Authentication
To make the login page more secure, you can choose to add an extra layer of protection to it such as users having first to provide credentials using HTTP Basic Auth in order to view the login page itself and login as a user. If you choose Two-Factor Authentication there are many plugins to choose from which will do the job.
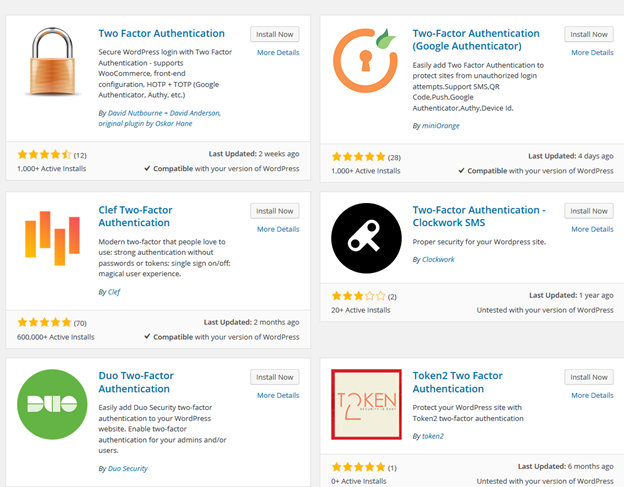
Figure 10: Some of the plugins allowing 2FA in WP
If you are not into that and do not feel that your website is so important to require 2FA you can just add another layer of protection to your website. The simplest way would be to edit the wp-login.php file located in your website's root and add the following in the top of the file:
/** HTTP Basic Auth **/
if (!isset($_SERVER['PHP_AUTH_USER'])) {
header('WWW-Authenticate: Basic realm="WordPress"');
header('HTTP/1.0 401 Unauthorized');
echo 'You need proper credentials to view this page';
exit;
} else {
$users = array('iamadmin' => 'iamtheadmin', 'johny' => 'bravo');
if (!array_key_exists($_SERVER["PHP_AUTH_USER"], $users) || $users[$_SERVER["PHP_AUTH_USER"]] !== $_SERVER['PHP_AUTH_PW']) {
echo "Wrong credentials!";
exit;
}
}
The code snippet above hardcodes some usernames and passwords which can be used to see the login page and reveals the login page only if the user has entered one of the two (you can edit them) user/password combinations in the $users array. The snippet shows the HTTP Basic Auth credentials box only once per user session (if the user types the wrong username/password combination he would have to close his browser and open it again) but this could easily be changed by adding the two lines mentioned below in the else conditional:
header('WWW-Authenticate: Basic realm="WordPress"');
header('HTTP/1.0 401 Unauthorized');
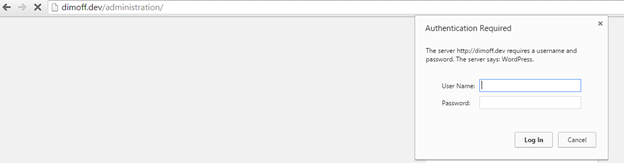
The problem with inserting the above snippet in the wp-login.php is that your changes may get lost when you install an update. Therefore, it would be best to create your own login page and use WordPress' global wp_login_form() function to show the login form in it. There, you can add HTTP Basic Auth at your leisure. Another way to implement HTTP Basic Auth (without hardcoding credentials in the code) but by editing the .htaccess file and adding a .pwd file with the possible user credentials in your web server can be seen here: http://www.helpdeskhangouts.com/securing-wordpress-admin-basic-http-authentication/
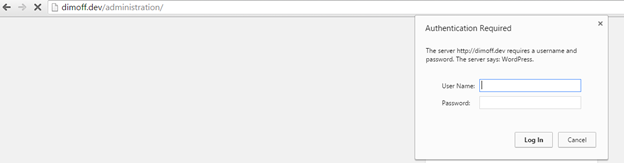
Figure 11: We will be shown the WP Login Page only after we provide correct credentials to HTTP Basic Auth
Conclusion
As WordPress is so easy to use, many people forget that extra layers of protection are required in order for their WordPress installation to live a long and fruitful life. Attacks against the admin section of WordPress are very common and unless precautions are taken, you may become a victim too. There are many ways to protect the login page and you should use several of them to increase the resilience of your WordPress installation.