Rootkits On Your Smartphone
While security of mobile operating systems is one of the most researched topics today, exploiting and rootkitting ARM-based devices gets more and more interesting. This article will focus on the exploitation of TEEs (Trusted Execution Environments) running in ARM TrustZone to hide a TrustZone-based-rootkit.
First let's take a look over what we are protecting on our modern mobile phones:

11 courses, 8+ hours of training
- We protect our communication - doesn't matter if it's calls or text messages
- Our data - lots of people have documents on their phones (from their businesses, presentations, contracts and so on)
- Our Credentials - like email passwords, different type of keys, etc.
- Our Payments - like online wallets (google wallet, yahoo wallet), PayPal, and other bank information.
Let's see what famous rootkits succeeded to collect information from mobiles, and remain hidden for a long time.
CarrierIQ
Used for logging user keystrokes, recording telephone calls, storing text messages, tracking location and more than that was difficult or impossible to disable.
The software's meant to improve the customer experience, however in nearly every case, CarrierIQ users don't know about the software's existence, as it runs hidden in the background and doesn't require authorized consent to function.
This rootkit was discovered by Trevor Eckhart and he demonstrated in a video that CarrierIQ is tracking our data.
http://www.youtube.com/watch?&v=T17XQI_AYNo
At the end, his questions are:
- Why do key presses submit UI01 & unique key codes?
- Why does SMSNotify get called and show to be dispatching text messages to CarrierIQ ?
- Why is my Browser data being read, especially HTTPs on my WiFi?
- Why is this not opt-in and Why is it so hard to FULLY remove?
What you can do?
Trevor Eckhartcreated a tool called Logging TestApp which turned into a full security suite and can be used to verify what logging is being done on your phone and where data is going. It will assist you in manually removing parts you do not know are running. Alternatively, the pro version of Logging TestApp -automates everything - and is available in the Android Marketplace for $1 – it has also proven successful in most situations.
FinFisher – FinSpy
FinSpy is a Remote Monitoring Solution that enables governments, agencies and companies to face the current challenges of monitoring mobiles. It has been proven successful in operations around the world for many years, and valuable intelligence has been gathered about target individuals and organizations. It's spread by links, email attachments, infected websites.
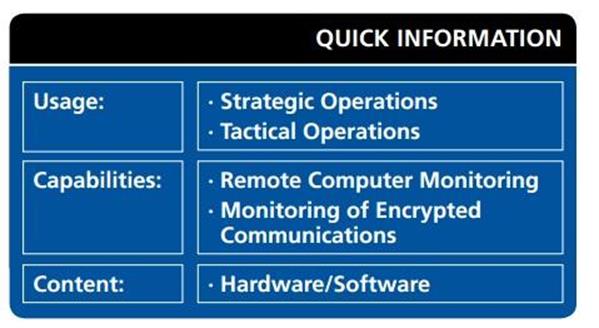
FinFisher was made by a company called Gamma International, and it is marketed as a powerful tool for accessing the computers of suspected criminals and terrorists secretly. Once it has infected your computer, FinFisher is not detected by anti-virus or antispyware software. Some of FinFisher's capabilities are the following: steals passwords from your computer, allowing access to your e-mail accounts; wiretaps your Skype calls; turns on your computer's camera and microphone to record conversations and video from the room that you are in.
A quick description of the FinSpy tool collected by Privacy International among others and posted on Wikileaks make a series of claims about functionality:
Be wary of opening unsolicited attachments received via email, Skype or any other communications mechanism. If you believe that you are being targeted it pays to be especially cautious when downloading files over the Internet, even from links that are purportedly sent by friends.
You can find some very well explained articles regarding FinFisher on citizenlab.org (find the links in resources section)
Where rootkits are hidden?
On mobile phones there are just two places where rootkits can hide with success: CPU and Baseband. On most operating platforms, both CPU and Baseband have full memory access so if you can own the Baseband you actually own the device. Even so, we can find around the CPU and Baseband, a small hardware addition by ARM called TrustZone and I will focus on this for the rest of article.
The ARM processor is a 32-bit RISC processor, meaning it is built using the reduced instruction set computer (RISC) instruction set architecture (ISA). ARM processors are microprocessors and are widely used in as many as 98% of mobile phones sold each year. They are also used in personal digital assistants (PDA), digital media and music layers, hand-held gaming systems,
calculators, and even computer hard drives.
TrustZone is basically a secure chip in your ARM processor that allows the processor to switch into a "secure mode" which hopefully will execute only trusted code.
Here are other TrustZone functions:
Trusted Execution Environmentals is a small operating system running in TrustZone that provides services to the real operating system. To better understand TEEs we can look at Netflix as an example:
The image below by Thomas Roth explains perfectly how the whole system works, connecting
the normal world and secure world together
[caption id="" align="alignnone" width="621"]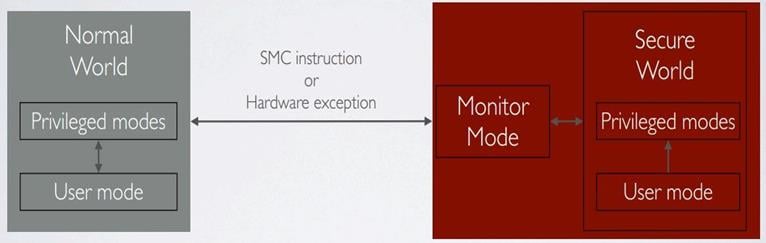 Click to Enlarge[/caption]
Click to Enlarge[/caption]
The SMC is sorted out of the information received from the normal or secure world, store registers of the current world, load new world registers, toggle NS and execute the application.
Memory allocation by Thomas Roth
[caption id="" align="alignnone" width="620"]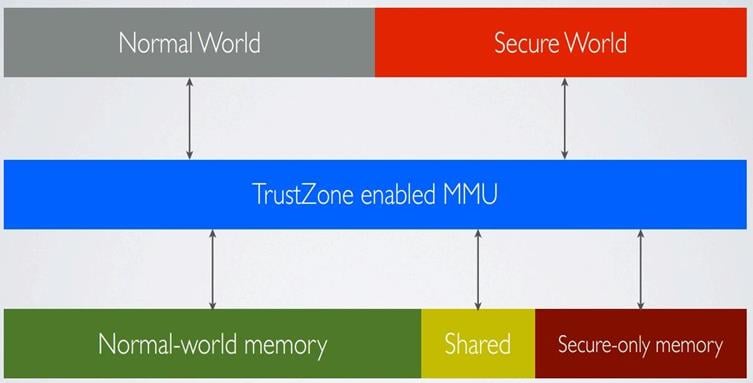 Click to Enlarge[/caption]
Click to Enlarge[/caption]
Normal world can only access its own memory and shared segment, secure world can access everything.
The boot process will start the trusted segment first, then the normal segment, as bellow (image by Thomas Roth)
[caption id="" align="alignnone" width="620"]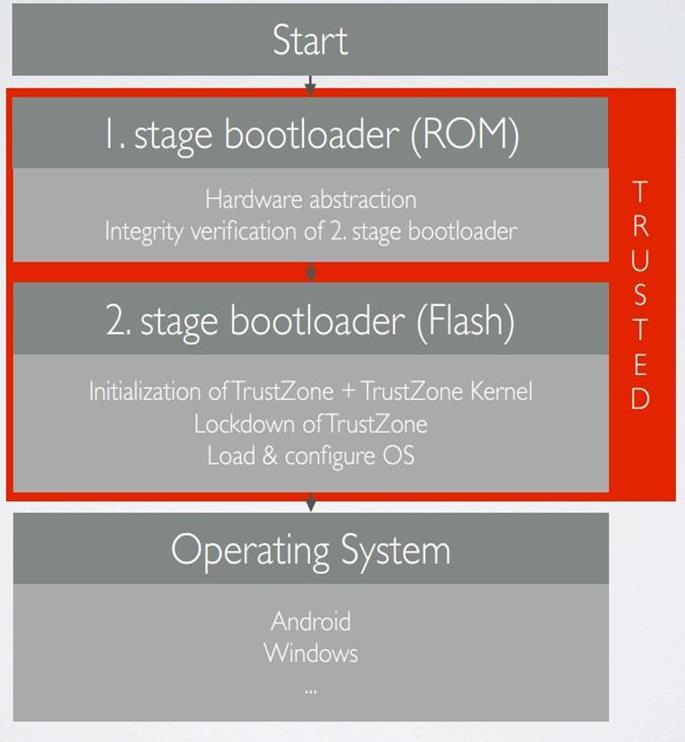 Click to Enlarge[/caption]
Click to Enlarge[/caption]
Basically, the vendor installs a small operating system in a part of the CPU and this OS can do anything. Also third party apps are installed on it as well.
Knowing these facts, let's see what we need to build a rootkit in TrustZone
OMAP HS development board. (Open Multimedia Applications Platform)
- Connectivity and system integration
- Support best-in-class video, graphics and multimedia performance.
- Security - OMAP processors support secure boot and run time,
-
Vision Analytics - distributed vision processing, or DVP, framework and includes a
programmable DSP.
- OMAP processors provide hardware and software support for the virtualization and cloud computing
- Packaging - TI offers OMAP processors in a variety of package options
- System performance support a range of applications and demands.
- Quality & reliability - rigorous quality assurance practices and has a zero-DPPM strategy to continuously improve its products.
QEMU - Quick EMUlator hosted virtual machine monitor:
TEE (Trusted Execution Environment)
Note* A tutorial about how to create a small virus for android you can find in my References links
Supposing you already created your rootkit and have it integrated inside TrustedZone there are few things to keep in mind:
How to infect other phones?
How to avoid infection over your phone?

11 courses, 8+ hours of training
References
- Trevor Eckhart - CarrierIQ
- Xda-developers - Logging TestApp
- FinFisher - Wikileaks
- FinFisher spykit exposed by citizenlab.org
- Bootloader Project - wikipedia page
- Generic emulator - QEMU
- Open Virtualization - TEE
- Create a virus for android
- HIP13 - Next generation rootkits dor ARM based devices






