OWASP 2017 top 10 vs. 2013 top 10
After a long interval of four years, OWASP in April 2017 released a draft of its latest list of “Top 10 Web Application Security Vulnerabilities.” The OWASP Top 10 has served as a benchmark for the world of application security for the last 14 years. It was designed to allow developers to identify and avoid coding bugs and to provide some standard to security teams for mitigating vulnerabilities on the basis of priority. Enterprises often rely on it for developing their application security programs and it also lies at the root of various product scoring mechanisms for vulnerability testing.
Some security leaders have welcomed the important changes in the list, specifically the inclusion of application programming interfaces (APIs), which shows the acceptance of shifts in the threat landscape. Others have noted that the list seems similar to its previous manifestations in many ways.
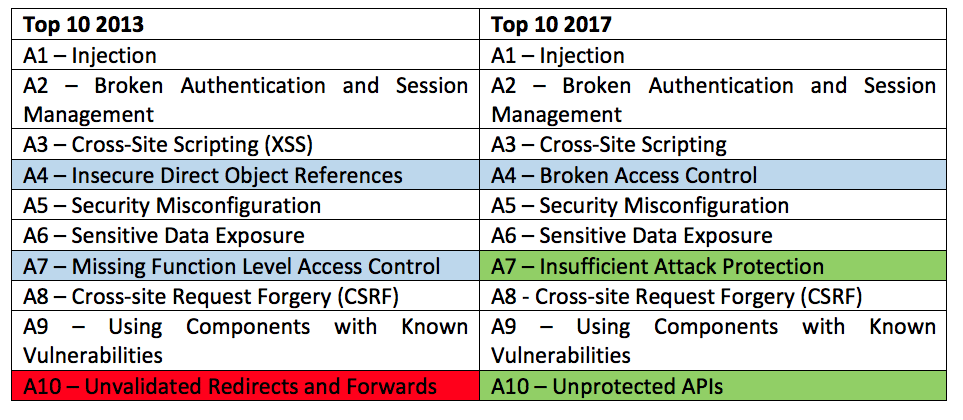
Before we go into the detail of what has changed in OWASP Top 10 vulnerabilities of 2017, let us take a glance at the table below for a quick review.
The vulnerabilities A4 and A7 in the 2013 list have been merged in 2017 list as a single vulnerability, A4 – Broken Access Control. The vulnerability A10 has been dropped in the new list, whereas two new vulnerabilities have made it to the list of 2017. These are A7 – Insufficient Attack Protection and A10 – Unprotected APIs.
Vulnerabilities that remain
We will now offer brief insights into vulnerabilities that have not changed in ranking and stay at their position in the new list.
A1 – Injection
OS, SQL, and LDAP injection flaws take place as a result of sending untrusted data to an interpreter as part of a query or command. This data can get the interpreter tricked into executing commands that may not be intended.
A2 – Broken authentication and session management
When authentication and session management are incorrectly implemented, it enables attackers to steal identities of other users or compromise keys and passwords.
A3 – Cross-site scripting
This vulnerability arises when untrusted data is included in a new web page by an application, or when an existing web page is updated with data supplied by a user by using a browser API with the ability to create JavaScript. This can allow an attacker to inject and execute scripts in the browser, which in turn can deface a website or redirect users to malicious websites.
A5 – Security misconfiguration
Default configurations are often insecure and can result in security breaches. Good security comes with secure configuration of applications, framework, servers, platform, etc.
A6 – Sensitive data exposure
Sensitive data such as financial or health records need to be fully protected. Data exposed to attackers is a vulnerability and can be misused for identity theft, credit card fraud, and various other crimes.
A8 – Cross-site request forgery (CSRF)
In a CSRF attack, the victim’s browser is forced to send a fake HTTP request to a vulnerable web app. The vulnerable application considers these requests as legitimate and answers them accordingly.
A9 – Using components with known vulnerabilities
Application components such as software modules or libraries that are vulnerable may be exploited and facilitate serious loss of data.
New vulnerabilities
A4 – Broken access control
This vulnerability results when user access control is not properly authenticated. It allows cyber-attackers to access other users’ accounts and data, view sensitive files, modify access rights, etc.
This vulnerability, which now ranks fourth in the 2017 list, is actually a merger of two vulnerabilities from the 2013 OWASP Top 10 list: insecure direct object references and missing function level access control. Both these vulnerabilities arise as a result of improper access control.
A7 – Insufficient attack protection
Many applications and APIs have insufficient ability to detect, avoid, and respond to automated and manual attacks. Complete attack protection requires automatic detection, logging, and response to attempts.
A10 – Unprotected APIs
Applications nowadays often come with APIs that may not always be protected, making them vulnerable to attacks.
The vulnerability that ranked 10th in the 2013 list of vulnerabilities is not in the top 10 vulnerabilities of 2017. This means that unvalidated redirects and forwards are not as common a vulnerability now as they were four years back.
Some thoughts on why the list has changed
The release of OWASP Top 10 is based upon the analysis of more than 2.3 million vulnerabilities in 50,000 web applications. There are two major additions to this release, i.e. insufficient attack protection and underprotected APIs. According to Jeff Williams, OWASP Top 10 project creator and coauthor, insufficient attack protection has made it to the list because of the large number of threats that applications nowadays face. Keeping this in mind, all modern applications should be able to detect, prevent, and respond to automated and manual attacks and block them.
The addition of the unprotected APIs category is a result of an explosion of API usage in modern software. APIs use a variety of data formats and protocols, such as REST/JSON, SOAP/XML, GWT, RPC, and others. These APIs are usually unprotected and they hold many vulnerabilities and signify a “major blind spot” for organizational security programs. OWASP is helping teams to refocus on this escalating problem.
“To me, T10-2017 reflects the move towards modern, high-speed software development that we’ve seen explode across the industry since the last version of the T10 in 2013,” said Williams. “While many of the vulnerabilities remain the same, the addition of APIs and attack protection in this version is designed to focus organizations on the key issues for modern software.”
Reasons for the overhaul of the top 10 in 2017
The OWASP Top 10 2017 is important for more than one reason. Generally, this overhaul was the need of the day, as it highlights and captures various key elements of application security particularly relevant for present-day apps.
Let us look at the key changes in OWASP Top 10 2017 vs. OWASP Top 10 2013, and try to understand why these changes were necessary.
Access control attacks are among the main methods that hackers use to compromise applications and get hold of sensitive information. During the past two years, attacks against access control are said to have increased, as compared to SQL injection and cross-site scripting attacks. Particularly, SQL injections are now becoming rarer mainly because all modern application frameworks are automated to carry out parameterized SQL queries with the help of object-relational mapping (ORMs). As API applications and single page applications are now more common, attacks against authorization such as authentication attacks and insecure direct object reference attacks are now becoming a larger threat. As developers implement their own rules of access control, the OWASP Top 10 is right to classify all access control and authorization vulnerabilities under one single category that they call the “broken access control.” It is important to note here that the broken access control was ranked second in the OWASP Top Ten list of 2004 and has been brought back to the 2017 list. According to OWASP, it was split into “insecure direct object reference” and “missing function level access control” categories in 2007 to concentrate on each half of the access control. Now that it is not deemed necessary anymore, the two have been remerged into the single category off “broken access control.”
Under-protected APIs as a new vulnerability
With the rise in distributed computing and client platforms, we are clearly moving toward making APIs as against classic browser-focused web apps. APIs allow bringing multiple platform applications to a specific set of web services, whether mobile apps or smart TVs. These are more susceptible to attacks than typical web applications and are prone to a large number of attack possibilities, such as standard injection attacks, token-based information disclosure flaws, and access control flaws.
Insufficient attack protection as a new vulnerability
Though this vulnerability category lies outside the application context, it is a much welcomed addition to the Top 10 list. The focus of this category is on detection, response, and application attack blocking, thus making them hard to exploit. This is important because, where application security programs focus too much on preventive measures, little focus or effort is given to detective and corrective measures. Detective measures include fundamental steps such as penetration testing, vulnerability assessment, and deploying RASPs or WAF; whereas corrective measure include the release of patches for discovered vulnerabilities to provide protection against attacks.
Removal of unvalidated redirects and forwards category
The category “A-10 Unvalidated Redirects and Forwards” in the OWASP Top 10 2013 has been removed from the Top 10 2017 because the statistical data of OWASP indicated that the vulnerability is not highly prevalent anymore. This category is related to URL redirection vulnerabilities stemming from the use of untrusted user input for redirecting users to another page.
Though the reason for including this vulnerability in the Top 10 2013 was to indicate the importance of why we should never blindly trust any user input, the truth is that most of the time open URL redirects can be identified and pose little threat to organizations, unless they involve a substantial amount of social engineering. In that case, an attacker would have to develop their own phishing website for harvesting sensitive user information. Still, there are several cases where an apparently harmless open URL redirect has combined with other web vulnerabilities to cause serious damage to user data.
The need for security awareness training
The OWASP Top 10 has reinforced the need for and importance of information security awareness training to ensure that employees are well aware of the threats they face. They need to know the consequences of disclosing information in a social engineering attack, accessing sensitive information without authentication, and failing to report any unusual observed activity. As today’s apps are released rapidly one after another and undergo constant updates with new features, we need to ensure that they are tested continuously for security vulnerabilities. Security awareness training stresses the importance of discovering vulnerabilities earlier in the application development lifecycle, rather than later because, once a security flaw makes its way into production, it can cause serious disruption.
Comments on the 2017 Top 10 Release can be submitted until June 30 via email to OWASP-TopTen@lists.owasp.org or dave.wichers@owasp.org (for private comments). The final version of OWASP Top 10 will be released in July or August.