Enhancements in Damn Vulnerable iOS app version 2.0

In this article, I would like to give a quick walkthrough of the new vulnerabilities and challenges that we have added in version 2.0 of Damn Vulnerable iOS app.
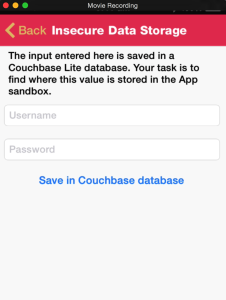
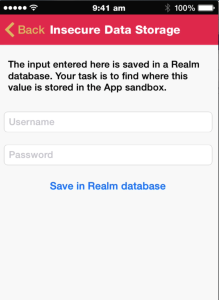
In the Insecure Data storage section, we have added challenges for the following databases.
- Realm Database
- Couchbase Lite
- YapDatabase

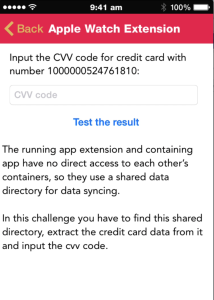
We have also added a new section on Extension vulnerabilities, which covers vulnerabilities in different application extensions, a feature that was introduced with iOS 8.
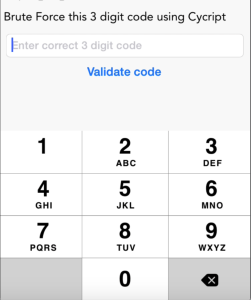
In the Runtime Manipulation section, we have added a challenge where you can write a cycript script to brute force a login screen.
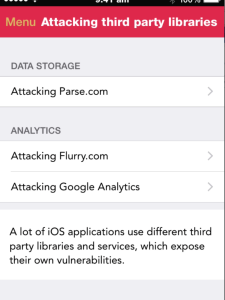
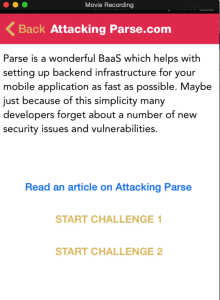
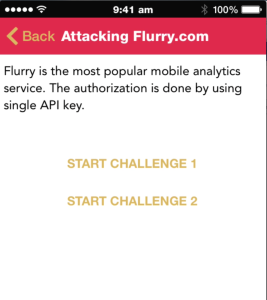
Another new section is Attacks on third party libraries, which demonstrates the security gaps that can occur in your application when you use third party libraries in your project.
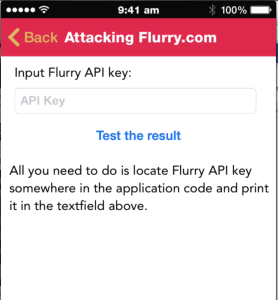
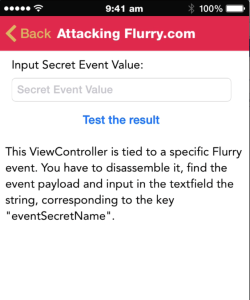

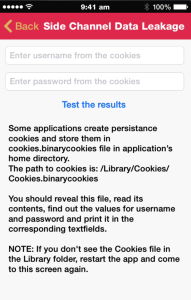
In the section on Side Channel Data leakage, we have added another vulnerability demonstrating insecure storage of cookies.
The current downloadable IPA file from the website is a fat binary that will work on both 32 bit and 64 bit devices. This app will work on all iOS versions starting from iOS 7.0.
Some important links
We are working on getting the new solutions out as soon as possible so please be patient. For previous vulnerabilities, you can download the solutions for free from here.
For any bugs, suggestions etc, please don't hesitate to contact me. Also, a very special thanks to Egor for his contributions to the project.
Prateek Gianchandani, a recent IIT graduate, has interests in the field of Penetration Testing, Web Application Security and Intrusion Detection. He is currently a researcher for InfoSec Institute. In the past he has worked for security-based startups.
You can contact him at prateek.searchingeye@gmail.com and on twitter @prateekg147 or you can visit his personal website at highaltitudehacks.com
In this series
- Enhancements in Damn Vulnerable iOS app version 2.0
- DevSecOps: Moving from “shift left” to “born left”
- What’s new in the OWASP Top 10 for 2023?
- DevSecOps: Continuous Integration Continuous Delivery (CI-CD) tools
- Introduction to DevSecOps and its evolution and statistics
- MongoDB (part 3): How to secure data
- MongoDB (part 2): How to manage data using CRUD operations
- MongoDB (part 1): How to design a schemaless, NoSQL database
- Understanding the DevSecOps Pipeline
- API Security: How to take a layered approach to protect your data
- How to find the perfect security partner for your company
- Security gives your company a competitive advantage
- 3 major flaws of the black-box approach to security testing
- Can bug bounty programs replace dedicated security testing?
- The 7 steps of ethical hacking
- Laravel authorization best practices and tips
- Learn how to do application security right in your organization
- How to use authorization in Laravel: Gates, policies, roles and permissions
- Is your company testing security often enough?
- Authentication vs. authorization: Which one should you use, and when?
- Why your company should prioritize security vulnerabilities by severity
- There’s no such thing as “done” with application security
- Understanding hackers: The insider threat
- Understanding hackers: The 5 primary types of external attackers
- Want to improve the security of your application? Think like a hacker
- 5 problems with securing applications
- Why you should build security into your system, rather than bolt it on
- Why a skills shortage is one of the biggest security challenges for companies
- How should your company think about investing in security?
- How to carry out a watering hole attack: Examples and video walkthrough
- How cross-site scripting attacks work: Examples and video walkthrough
- How SQL injection attacks work: Examples and video walkthrough
- Securing the Kubernetes cluster
- How to run a software composition analysis tool
- How to run a SAST (static application security test): tips & tools
- How to run an interactive application security test (IAST): Tips & tools
- How to run a dynamic application security test (DAST): Tips & tools
- Introduction to Kubernetes security
- Key findings from ESG’s Modern Application Development Security report
- Microsoft’s Project OneFuzz Framework with Azure: Overview and concerns
- Software maturity models for AppSec initiatives
- Best free and open source SQL injection tools [updated 2021]
- Pysa 101: Overview of Facebook’s open-source Python code analysis tool
- Improving web application security with purple teams
- Open-source application security flaws: What you should know and how to spot them
- Android app security: Over 12,000 popular Android apps contain undocumented backdoors
- 13 common web app vulnerabilities not included in the OWASP Top 10
- Fuzzing, security testing and tips for a career in AppSec
- 14 best open-source web application vulnerability scanners [updated for 2020]
- 6 ways to address the OWASP top 10 vulnerabilities
- Ways to protect your mobile applications against hacking
- Secure Coding for .NET Training Boot Camp
- OWASP Top 10 Certification Training Boot Camp
- CSIS Top 20 Critical Security Controls Training Boot Camp
- Secure Coding for C/C++ Training Boot Camp
- Mobile and Web Application Penetration Testing Training Boot Camp
- ISC2 Certified Secure Software Lifecycle Professional® (CSSLP) Training Boot Camp
- Secure Coding in PHP Training Boot Camp
- Secure Coding for Java Training Boot Camp
Get certified and advance your career!
- Exam Pass Guarantee
- Live instruction
- CompTIA, ISACA, ISC2, Cisco, Microsoft and more!

Application security
Instead of instilling security best practices earlier in the development process, incorporating them while code is written is a better approach.

December 12, 2023
Drew Robb
Application security
Find out what’s new in the OWASP Top 10 list, which explains significant threats...

November 24, 2023
Drew Robb
Application security
In the last piece, we went through the various tools that can be integrated into the DevOps Pipeline to implement security at the different stages of the sof

April 26, 2023
Nitesh Malviya
Application security
Learn about the growth of DevSecOps and key statistics associated with it for 2022.

January 9, 2023
Nitesh Malviya