Security Dangers of Web Management Interfaces
Web based interfaces are convenient for managing networking equipment, but under no circumstances should these be open to the world and the internet. Many networks alarmingly have their firewall, gateway, and other device management pages open to the world. This is a huge security concern as the web management pages of such devices are commonly prone to various exploits which are typically slow to be updated from the vendor in the high paced world of web-based exploits.
Web based management interfaces are often coded without security in mind, full of holes from allowing administration bypass to incorporating poor or broken implementations of SSL.
Simply using particular Google searches a hacker can locate hundreds if not thousands of potential targets. Logs of network devices are often not monitored for changes or login attempts so compromises can often go undetected for a long period of time.
The default management pages of devices along with the default passwords are logically published online by vendors in publicly available manuals and documentation. From this documentation various Google searches ("Google Hacking") can be performed to locate networks with the device login pages open to the internet and indexed in Google.
Example Google Searches / Google Hacking
To locate SonicWALL Firewall login pages indexed in Google, use the following search query:
>inurl:auth.html intitle:SonicWALL - Authentication
Various Barracuda devices can be found with the following queries:
inurl:index.cgi intitle:Barracuda Spam Firewall: Welcome inurl:index.cgi intitle:Barracuda Load Balancer: Welcome
VMWare Management Interfaces:
inurl:"vmware/en/" intitle:"VMware Management Interface"
The obsolete but still in use CyberGuard gateway devices are numerous:
"Welcome to the CyberGuard unit! "
Various critical network management pages found from Google Searches
Shodan
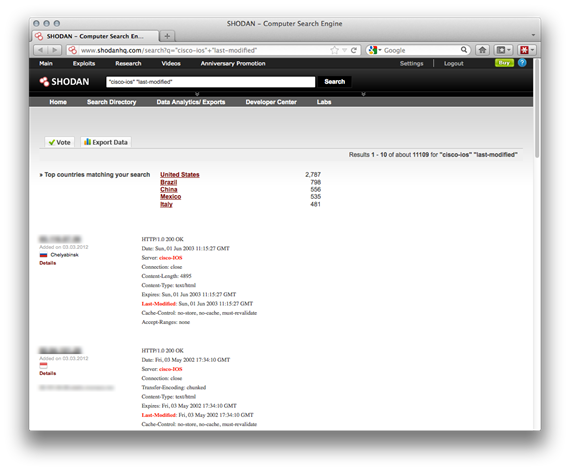
Using shodanhq.com even more detailed searches can be performed as this search engine indexes HTTP headers and other information.
"cisco-ios" "last-modified"
is a popular search to locate Cisco IOS devices on the internet which have web authentication disabled. This information is broadcasted in the http headers and is easy to identify.
http://www.shodanhq.com/search?q="cisco-ios"+"last-modified"
Another example search on shodanhq.com reveals WatchGuard Firewalls with web management open to the internet:
http://www.shodanhq.com/search?q=WatchGuard+Firewall
Your Cisco device should not be open to the internet without authentication!
Information Disclosure
Information disclosure or information leakage is often not viewed as a security concern. However, this is typically the starting point for potentially larger security holes. Even with a long password protecting your internet facing device, the device is still providing information to hackers. Metasploit modules and other tools are able to query the management interfaces of networking devices to obtain a fair amount of information or at least identify the brand of the device if the login page does not give this away.
Once the brand of a device is known to the attacker, various published exploits for the device can then be easily identified as easy as searching http://www.exploitsearch.net or other various outlets. Not surprisingly no brand model is safe or immune from exploits for their web management interfaces.
Many exploits are a few years old for these devices. However if a company's device management interface open to the internet and indexed in Google reflects their security policies, perhaps the device has not been patched lately or at all since implementation. Relying on only a vendor's login page is not enough security and largely increases risk to compromise and breach.
Example Exploits
Past exploits for web management interfaces are numerous and cover every vendor in the market. A few examples are outlined below as a sample.
In May 2011 Cisco released a patch to cover several serious web management vulnerabilities. A document on their website outlines the risks:
http://www.cisco.com/en/US/products/csa/cisco-sa-20110525-rvs4000.html
"The Cisco RVS4000 and WRVS4400N Gigabit Security Routers contain three web management interface vulnerabilities:
- Retrieval of the configuration file
If an administrator of the device has previously created a backup of the configuration, using Administration --> Backup & Restore --> Backup, it is possible for a remote unauthenticated user to access the backup configuration file. This file contains all configuration parameters of the device, including the HTTP authentication password and VPN pre-shared-keys (PSKs).
- Root operating system arbitrary command injection by an authenticated attacker
A user who is authenticated to the device can inject arbitrary commands into the underlying operating system with root privileges, via the ping test and traceroute test parameters.
- Retrieval of admin SSL certificate private key
The admin SSL certificate private and public keys can be retrieved (used for Quick VPN) by a remote unauthenticated user."
A much older vulnerability which is still fresh in the minds of most security researchers is CVE-2001-0537, which allows a remote attacker to bypass the web management login and gain full administrative control of Cisco IOS devices. Of course this has long been patched but is perhaps the most alarming example of the concerns of allowing web management open to the world (http://cve.mitre.org/cgi-bin/cvename.cgi?name=2001-0537).
Metasploit makes this vulnerability easy to execute:
http://www.metasploit.com/modules/auxiliary/scanner/http/cisco_ios_auth_bypass
Other examples of past exploits of web management interfaces include Barracuda product-wide unauthorized file access and retrievals (http://www.osvdb.org/68301), denial of service in Dell OpenManage devices (http://cve.mitre.org/cgi-bin/cvename.cgi?name=2004-0331), Cisco Content Service Switch device reboot from a single HTTPS POST request (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0792), Check Point CSRF vulnerability leading to privilege escalation (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-3489), F5 BIG-IP XSS (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-1503), and likewise DoS exploits in most all home and consumer routers with web interfaces such as the Linksys WRT54G (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2005-2912) and Netgear WGR614 (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-6122).
Power Management Web Interfaces
Perhaps more concerning are APC and other power management devices which have web interfaces that are open to the world.
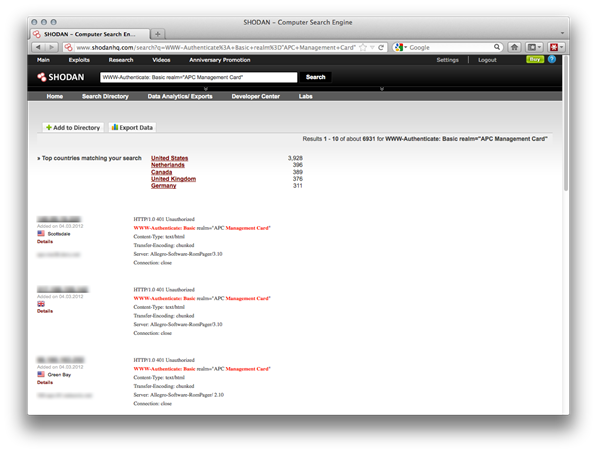
Searching shodanhq for
WWW-Authenticate: Basic realm="APC Management Card"
provides surprisingly many results (http://www.shodanhq.com/search?q=WWW-Authenticate%3A+Basic+realm%3D"APC+Management+Card")
Power management web interfaces should most certainly not be available to the internet. Unauthorized access to a power management device could lead to gaining control to not only power down the device but also power down all servers or equipment connected to the device.
Example exploits of APC web based interfaces are fairly serious in nature from CSRF and XSS vulns which can lead to administrative access and other malicious exploitation (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-1797, http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-1798, http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-4406, http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4263).
If users rarely upgrade firmware or software on network devices, they are even less likely to update firmware or software for a power management device, if ever at all. This increases the chances that power management devices open to the internet could potentially not be running the latest patched firmware and provide excellent targets for compromise and exploitation.
Securing Web Management Interfaces
Several steps can be taken to secure web management interfaces of networking and other equipment.
If a web based management interface is optional and not required, disable it. Even though it may be a little less convenient, a secure shell to manage a device may be the preferred way to go for security.
Restrict access to the web interface by IP. Most, if not all, devices allow IP restriction to restrict access to the device from a particular network or the admin's IP range.
Restrict access to the web interface by VPN. Keep the device accessible only by private IP on the LAN side and use a VPN to establish access.
Restrict access to all management interfaces via a dedicated management machine for the company and admins. Create a company policy that any remote management management must be done from this management PC, available by restricted access through VPN or SSH tunnel.
Use a good password. At the very least, use a 26 or longer character passphrase or password for critical network devices. Use a password generator such as https://www.grc.com/passwords.htm to create a unique long password. Change this password after any staffing changes as a policy.
Disable telnet on any Cisco devices, even if the device is only accessed internally.
Enable brute force prevention or rate limiting. If a device supports rate limiting or brute force prevention for the admin login page, enable this feature. Every layer of security helps.
Vendors may have specific information about specific settings and changes that can be implemented for more in-depth device security. Cisco, for example offers a detailed guide for IOS devices here:
http://www.cisco.com/en/US/tech/tk648/tk361/technologies_tech_note09186a0080120f48.shtml
The NSA provides hardening guides not only for various operating systems and also guides for Cisco networking devices:
http://www.nsa.gov/ia/mitigation_guidance/security_configuration_guides/cisco_router_guides.shtml
http://www.nsa.gov/ia/mitigation_guidance/security_configuration_guides/switches.shtml
Conclusions
Relying on only a vendor login prompt is clearly not nearly enough security for critical network hardware. Additional steps to isolate and prevent access to web management interfaces must be put in place by policy for good security practices. Hardware vendors must implement strong default security policies for their products. The default configuration of any firewall or gateway devices should disallow management access from the WAN and only allow access to administration from the LAN. Upon logging in once with the default password users should be prompted to immediately change the default administrator password for the device.
As network devices become more and more complex, the web interface to control and configure these devices has slowly become more and more involved and complex. More complexity and more interactive web portals can often lead to more exploits due to more bells and whistles and moving parts. Vendors must work to prioritize security for various aspects from the web server issuing up the web management page to sanitizing inputs from all fields in the application itself. This is challenging from a programming standpoint as many interfaces and controls are tied to hardware and/or restricted by general memory limitations available on embedded devices.
Vendors and companies are increasingly implementing various all-in-one boxes which provide a firewall, IDS, mail server, VPN, WAF, web server, anti-virus, and a variety of other services. The risks of putting all of your eggs in one basket apply even more so in these cases. These devices logically have a central management page to configure all of these services which also makes the management pages an attractive target for hackers to gain access and control for various parts of your network. The management pages of these devices should be secured and certainly kept off of the internet.
Creating a policy on how to manage all web based network interfaces for a company or network is ideal for an organization and IT staff. A central management PC that is dedicated for remote administration of web interfaces is ideal as a starting point. Keep this PC dedicated for management purposes only and free of any third party software or general web browsing which often leads to malware or other infection. Since most all web based interfaces work in most any browser, consideration for this management PC should be a Linux desktop or server which is less prone to Windows security concerns and can also easily be connected via SSH.
There is always a sliding scale of security versus convenience. However, if a management interface comes up in a Google search, chances are the network needs to tip more towards the security end of the scale, even at the cost of convenience. Simply relying on a strong password for a device open to the internet is leaving your device and entire network open to compromise.








