Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.
Our resources

Legality of Electronic Signatures in the EU and the US

Cryptography Fundamentals, Part 5 – Certificate Authentication

Cryptography Fundamentals, Part 4 – PKI

Cryptography fundamentals, part three - Hashing

Cryptography Fundamentals, Part 2 – Encryption

Cryptography Fundamentals – Part 1
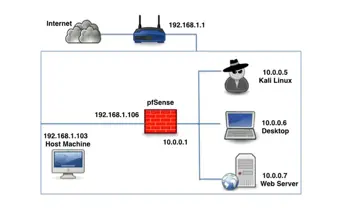
Setting up a pentest Lab with pfSense in virtualBox

Android Application hacking with Insecure Bank Part 2

OWASP ProActive Controls: Part 1

Dridex Downloader Analysis

Cyber Threat Analysis for the Aviation Industry

OWASP ZAP Reconnaissance – Without Permission!

Cybersecurity and Artificial Intelligence: A Dangerous Mix

Windows Exploit Mitigation Technology – Part 2
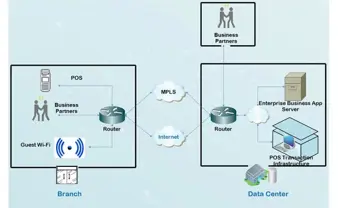
Data Traffic & Network Security

PCI compliance interview questions

Comparison of Cloud Automated Malware Analysis Tools

Gh0st RAT Part 2: Packet Structure and Defense Measures

Clean up Your WordPress Site after Hack and Secure it against Future Threats
Current Trends in the APT World

Carbanak Cybergang Swipes Over $1 Billion from Banks

TrueCrypt Security: Securing Yourself against Practical TrueCrypt Attacks

Windows Exploit Mitigation Technology – Part 1

Introduction to Smartcard Security