Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources

Top Cyber Security Challenges in Smart Cities

The components of a successful security awareness program
Zico 2: 1 CTF Walkthrough

Deserialization Attacks for Crypto-Mining

Hacking tools with Python: Part one
Hacker tools: Sniffers
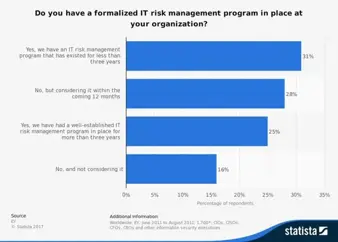
Expert Interview: Security & IT Risk Management Best Practices
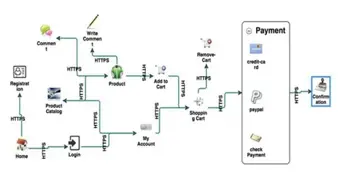
Understanding the Role of Threat Modeling in Risk Management

How to Create an Effective Incident Response Plan

Computer Forensics: The Computer Hacking Forensics Investigator (CHFI) Certification

Top 10 database security tools you should know
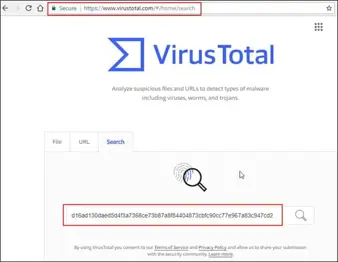
Threat hunting – Malware/angler EK analysis with security onion - GOOFUS AND GALLANT

OWASP top ten testing and tools for 2013

How to Use Security Incident & Event Management (SIEM) for Early Threat Detection

Top 20 security awareness slogans, catchphrases, and taglines
An Enterprise Guide to Using Threat Intelligence for Cyber Defense

5 Ways Hackers Can Breach Your Company Undetected

Computer Forensics: Civil Investigations

Computer Forensics: Criminal Investigations

How to Secure Data With A Data Loss Prevention Prevention Plan

Public Cloud Penetration Testing from the Customer Viewpoint
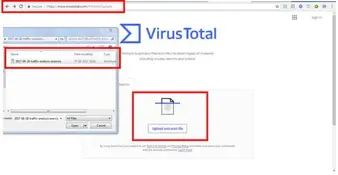
Threat Hunting – Malspam –Japan Office Infected

10 Steps Leaders Can Take to Improve Cybersecurity in their Organization

The Top 25+ Information Security Events and Conferences of 2018