Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources

Changes to CompTIA’s A+ exam (220-1001 and 220-1002 / 220-1101 and 220-1102) [2022 update]

Reducing IT’s carbon footprint: Good for business as well as the environment
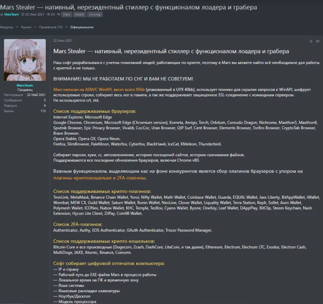
Mars Stealer malware analysis

Privacy dos and don'ts: Privacy policies and the right to transparency

Starr McFarland talks privacy: 5 things to know about the new, online IAPP CIPT learning path

5 cybersecurity resume tips to help you land the interview — and the job

Want to make more money? Here are the top 5 highest-paying infosec certifications [2022 update]

How Booz Allen Hamilton keeps their security team secure and compliant in a hybrid world

Data protection vs. data privacy: What’s the difference?

NIST 800-171: 6 things you need to know about this new learning path

THE PLANETS EARTH: CTF walkthrough, part 1

Working as a data privacy consultant: Cleaning up other people’s mess

A lifelong interest in technology: Infosec scholarship winner Jorge Almengor

Microsoft Autodiscover protocol leaking credentials: How it works

6 ways that U.S. and EU data privacy laws differ

EMPIRE BREAKOUT: VulnHub CTF walkthrough

5 tactics to improve cybersecurity hiring results

Average CGEIT Salary in 2022

Top 9 effective vulnerability management tips and tricks

Armaan Kapoor: Developer protégé turned cyber professional and social impact advocate

How to remove ransomware: Best free decryption tools and resources

JANGOW: 1.0.1: CTF walkthrough

SOC integration: Creating a well-built portfolio vs. a frankenstack

Can I make six figures working in tech? Here are the best tech jobs for 2022