Cyber-Security Career Planning
Intro
This article will
differ from ones I wrote before. You may get used to my pieces of content which usually cover in-depth aspects of cyber-security and especially SAP Cybersecurity. I'm pretty sure you've learned a lot about different technologies and hacking techniques and are keen to use them in practice. Now it's time to take a short break and to look at the cyber-security market in general, to see what it looks like, which way it is evolving, and which career path to choose.
The cyber-security market is growing rapidly, and now it is estimated at $75-100 billion a year [1]. What does "a market is estimated" mean? Simply put, $75 billion is the amount all companies spend on solutions and services related to cyber-security. So, it is a kind of a big pie shared by different cybersecurity companies.

What should you learn next?
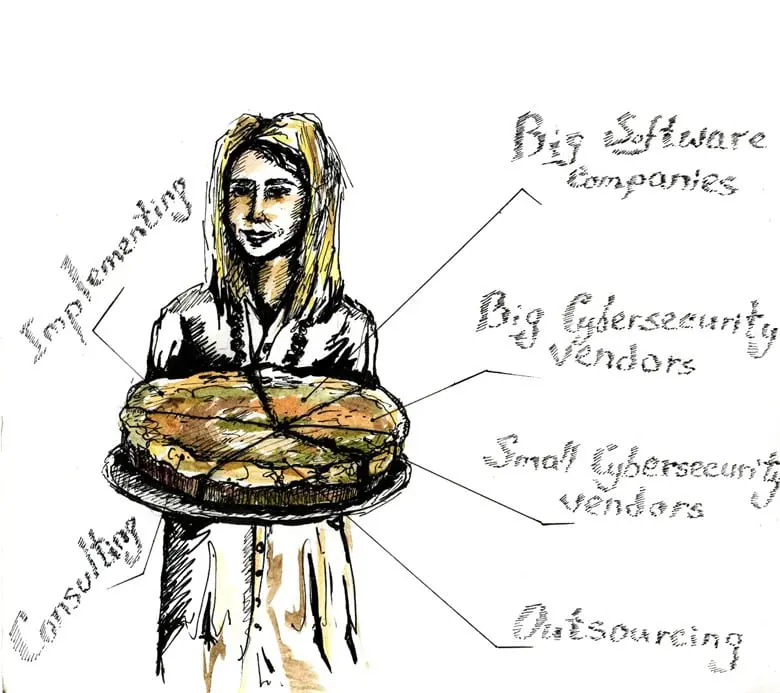
This is what the "Cybersecurity pie" looks like
On the one hand, this amount is rather big. On the other hand, many large companies don't take note of it. When a company enters the cyber-security market, in the mid-term perspective,
it may gain 10 percent in several years, that is $7,5 billion. Not all big IT players find such piece of the "pie" interesting. Just to compare: the e-learning market is also developing and is estimated at $100 billion a year. If we compare the cyber-security market, for example, with the automotive industry, it is hardly anything. All automakers earn about nine trillion dollars per year in total. So if, say, Apple decide to enter a new market, they are unlikely to introduce a kind of iFirewall. What's the use if it is more profitable to go in for self-driving or electric cars? So, we will rather ride an iCar soon.
However, it seems reasonable that cyber-security can be considered not as a separate market but as a part of security in general, which includes state military spending. Just think, who needs all those tanks, rockets, and other scary things when it is possible to perform a cyber-attack on Oil tank or electrical grid. And if we look at the cyber-security market as a part of the defense industry, it looks much more attractive because it estimates a trillion dollars a year.
Short overview
Just 10-15 years ago, there were about a couple dozens of product-based companies on the cyber-security market. They were developers of antivirus software, firewalls, and a couple of vulnerability scanners. The whole market was estimated to be worth a few billions which is next to nothing in comparison with the current state. And if we went back 20 years ago, there was not even a term like "cyber-security market."
Now, there are about 1300 software companies that are fully or partially engaged in info security; [2] 250 of them appeared just last year, and their number will exceed 1500 by the end of this year, according to conservative estimates. However, in my opinion, this number is likely to overcome a two-thousand mark. The growth is significant, to say the least, in ten times within ten years.

Most of the cyber-security companies are located in the USA, and only Israel tries to beat them in this game.
What companies share the cyber-security market? Of course, it is impossible to list all of them. In this article, I'll focus on the most noteworthy and influential market players.
The cyber-security market can be divided into two big groups – software vendors and solution providers. Let's look at them more closely.
Software vendors
The software vendors in their turn can also be divided into several groups. The first one develops security software along with other solutions; the second group focuses on the security only. Among the second segment, there are big enterprises as well as small companies. Together they constitute one-third of the cyber-security market that is about $25 billion.
Big software companies which are engaged in cyber-security are estimated to be worth about 10 billion, or 15% of the market. These companies, (e.g. Microsoft, IBM, HP Enterprise, Cisco, Dell/EMC, Intel and some others) have one thing in common – rather small share of income from security products. Exact estimates are hard to get; it's only my opinion, security business plays an important role in the annual reports only for Cisco and HPE.

Not all big software vendors are interested in having a slice of the "cybersecurity pie."
Another fact worth mentioning is that most of such companies rarely invent something innovative and brand-new in the field of information security. Their business strategy is rather simple: if they see a budding startup, they buy it and its developers and continue to use an existing process and distribution channels. In general, regarding innovative developments, the large enterprises are not the most interesting job for a security wannabe. Anyway, there are some advantages of working there.
The second subgroup is large companies that work in the cyber-security area only. They make up 15% of the market or 10$ billion per year.
Below is the listing of such companies with their approximate turnover (in billions of dollars).

Here comes the third subcategory, namely small cyber-security companies with annual revenue less than 100$ million. Their combined income is less than $5 billion a year; it is only about 3% of the overall market.
It makes no sense to list them, as while their number is growing continually, many of them disappear – some are sold to big vendors, others cannot survive in the highly-competitive market. If you need an example of such companies, just take a glance at the list of RSA exhibitors, there you can find at least 30% of them.

Cybersecurity start-ups have a small, but weighty piece of the pie
Anyway, it is such companies that invent promising solutions which tend to form new product categories, remember that SIEM and Vulnerability Management solutions were new disruptive product categories some years ago before becoming a common tool.
Not so long ago, all the companies listed in the previous chart were start-ups with fifty employees or even less. It will not take long, when, for example, a Rapid7 will outperform a Fortinet and a company we have never heard about will be a next Rapid7. This process is now faster than ever: the way from start-up to a 100$-million revenue company took fifteen years before, and now a company can reach this point within 7-8 years. With external investments, of course.
Anyway, those small companies are the places where you can quickly learn a lot and invent something that can change the history.
Service Providers
The second large part of the market is companies that outsource cyber-security or sell products by a subscription model. The service market amounts to about 60% of the "cybersecurity pie." It can be roughly divided into Consulting, Implementation, and Outsourcing.
Outsourcing
Outsourcing is estimated at $15 billion, where 9 of them is MSSP or Managed Security Service Providers.

According to Gartner, 40% of all security technology acquisitions will be directly influenced by MSSP and on-premises security outsourcing providers by 2020.
In fact, most of the MSSPs develop its monitoring system by existing solutions; it means they license products of security vendors and sell the labor of people who use these products to monitor customers' security. However, some of them have self-developed solutions. Here's a short list, just to name a few:
- IBM
- AT&T
- HPE
- Verizon
- Atos
- Orange
- Accenture
- BAE
- CSC
- BT
- Wipro
- NTT
- Symantec
- T-Systems
Besides, there is a list of companies a wide audience may be not familiar with, but they are extremely important. They appeared on the cyber-security market quite recently; however, they are rather influential and could buy hundreds of small or even medium companies. I am talking about the largest US companies engaged in the defense industry. Now they are actively involved in the cyber-security and provides MSSP services for commercial companies. Here they are:
- Raytheon
- Lockheed Martin
- General Dynamics
- Airbus
- BAE Systems
- Honeywell
They sell military equipment and some kinds of firewalls at the same time. Their acquisitions related to the cyber-security are notable. As you can see, the security market is not a toy.
Implementing
This area includes companies that are engaged in distribution, implementation, configuration and resale of solutions. In fact, they get about 30% of the vendors' revenue depending on the arrangements. Their exact market share is difficult to count, but it is approximately 10-12$ billion a year. Having experience in those companies helps you to learn how security products work and how people use them in real life.
Consulting
Consulting shares 20% of the market, or approximately 15$ billion per year.

Consulting companies hold one-fifth of the pie
Now, it's rather difficult to separate companies that focus solely on consulting from ones that provide Managed Security Service. Soon, these two types of companies will be engaged in both, but now you can still find firms for which consulting is the main concern or a big part of business at least. Here they are:
- Deloitte
- E&Y
- PWC
- KPMG
- IBM
- Accenture
- CSC
- Protiviti
- TCS
Those companies give you a great experience of large companies' operations and their main concerns. After working in consulting company, you are more likely to understand a client needs and to invent solution applied in real life.
Here comes the piece of the "pie," the most attractive to a cybersecurity novice, companies specifying in a relatively small part of consulting services – security assessment. Penetration testing, Red team, and other highly specialized services (such as security auditing of business applications, reverse engineering, researching of various devices and protocols for vulnerabilities, etc.) can also be included in this group. Those companies can be called boutique agencies.

Security assessment companies have a small piece of pie, but with a unique filling.
In comparison with the vendors, such companies are small businesses, and most of their employees are experts in security analysis. Working experience in such companies is priceless, as it gives you an opportunity to understand how the most secure system of the world's largest companies are designed and, of course, explore the ways to hack them.
When a client wants to find out security weakness and issues within his or her system, they come to these agencies rather than large consulting companies. The Big Four companies are usually the next step after such audit.
Consulting companies compound a tenth of a percent of all cyber-security market, but they evolve it. Here are some examples.
Critical infrastructure security is trending now; however, this topic was discussed in 2008 at security conferences like Black Hat. Medical device cybersecurity and IoT, in general, are an emerging market nowadays. In 2010, consulting firms delivered the first presentations on this subject. Experts have been talking about SAP and ERP system security since 2007, and this year Gartner has recognized it as a key trend for the near future. Another example is car cybersecurity; the first in-depth public research in this area was released just several years ago and won the prize for innovation at the Black Hat Pwnie Awards. What can we witness now? Companies that specialize in the development of car security devices are emerging. In short, if you want to understand the future trends, you know where to look for.
The number of large companies that are engaged in consulting only and are not affiliated with vendors is not so big. As for the USA, we can name IOActive or NCC, in Europe, there are MWR, SensePost, ERNW, and SecConsult to name a few.

What should you learn next?
So, this is it. Choose the slice of the "pie" you like more and explore it! Good luck!





