NIST CSF: Risk management framework
In February 2014, the National Institute of Standards and Technology (NIST) published its “Framework for Improving Critical Infrastructure Cybersecurity,” which offers a holistic way for organizations to better understand their cybersecurity risk and how to manage it.
The NIST Cybersecurity Framework (CSF) was the result of collaboration between the public sector, private sector and academia, and its methodology is meant to complement other cybersecurity best practices, standards and industry guidance regardless of the organization’s mission. At its core, the CSF implements President Barack Obama’s February 2013 “Improving Critical Infrastructure Cybersecurity” Executive Order, signed following years of rising threats to U.S. banking, telecommunications, utilities and other businesses.

Get NIST CSF training
Although organizations are not required to implement the CSF, one of its components, the Risk Management Framework, helps to present them with a clearer picture of their cyber risk profile and a road map to mitigate the potential impacts if these risks are realized. Furthermore, a well-implemented Risk Management Framework (RMF) can help to provide avenues to escalate risks and issues to the leadership level so their potential operational, financial, legal and technical impacts can be more broadly understood.
The purpose of this article is to provide a high-level introduction to the various components of the NIST Risk Management Framework, key concepts, its scope and key processes, so that your organization can better understand the value that it can play in bolstering your cybersecurity posture.
The Risk management framework tiers
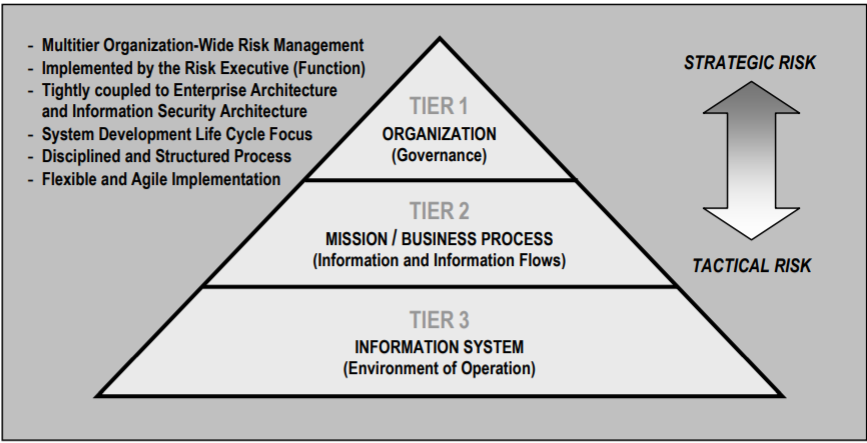
Before an organization begins their first journey through the Risk Management Framework (RMF), NIST first seeks to help them organize the different levels of accountability and ownership throughout the process.
Because managing information security, information systems and risk is complex, expensive and a time-intensive process, decisions should involve each facet of the organization. This should include management providing strategic direction and budgetary authority down through the mid-level leaders leading projects, and right to the front-line professionals implementing and operating the systems.
With this holistic view of risk management in mind, NIST has developed a three-tiered view of organizational risk management, as seen in the graphic below: [CLICK IMAGES TO ENLARGE]
(Source: NIST)
Tier 1
Tier 1 outlines an organizational-wide governance structure and comprehensive risk management strategy, developed and supported by senior management. NIST recommends the organizational governance model implemented includes the following features:
- The techniques and methodologies the organization plans to employ to assess information system-related security risks and other types of risk of concern to the organization
- The methods and procedures the organization plans to use to evaluate the significance of the risks identified during the risk assessment
- The types and extent of risk mitigation measures the organization plans to employ to address identified risks
- The level of risk the organization plans to accept (i.e., risk tolerance)
- How the organization plans to monitor risk on an ongoing basis given the inevitable changes to organizational information systems and their environments of operation
- The degree and type of oversight the organization plans to use to ensure that the risk management strategy is being effectively carried out
Tier 2
Tier 2 looks at risk at “a mission and business process perspective and is guided by the risk decisions at Tier 1.” In other words, after the enterprise strategy is defined and governance established, Tier 2 lays out expectations for the following activities as defined by NIST:
- Defining the core missions and business processes for the organization (including any derivative or related missions and business processes carried out by subordinate organizations)
- Prioritizing missions and business processes with respect to the goals and objectives of the organization
- Defining the types of information that the organization needs to successfully execute the stated missions and business processes and the information flows both internal and external to the organization
- Developing an organization-wide information protection strategy and incorporating high-level information security requirements into the core missions and business processes
- Specifying the degree of autonomy for subordinate organizations (i.e., organizations within the parent organization) that the parent organization permits for assessing, evaluating, mitigating, accepting and monitoring risk
As with other processes and functions, these activities will have their own life cycle of development, evaluation, mitigation, acceptance and monitoring that is specific to each. This is to ensure they evolve with the organization’s mission.
Tier 3
Tier 3 focuses on risk at an individual information system level. Addressing risk at this level is based on the decisions and priorities set in Tiers 1 and 2, but also the function and nature of the system and where it operates. The security controls selected and deployed are based on the requirements of the individual system, but also the operational and management expectations for that system.
At this level, risk is managed by security controls that are implemented beginning during initial development and maintained through implementation and beyond.
The Risk management framework process
The NIST Risk Management Framework was created to provide a structured, yet flexible process to integrate into an organization’s existing information security tools and procedures. While a lot of the work and roles will align with the Tier 3, operational level, different steps and components will touches on Tiers 1 and 2, such as to provide management feedback and to obtain budgetary and policy approval.
At a high level, the NIST RMF process:
- Encourages the idea of “near real-time” risk management, thanks to checks and steps that promote continuous monitoring and risk evaluation
- Promotes the use of tools to automate information sharing, especially with senior leaders as to not impede timely, cost-effective decision-making or to allow risk mitigation to negatively affect business operations
- Integrates information security and risk management into enterprise infrastructure, solution development and operational decision-making
- Provides guidance on the selection, assessment and monitoring of information security controls
- Encourages the acknowledgement of accountability and responsibility for risk management throughout the organization and the use of system controls to enforce those roles
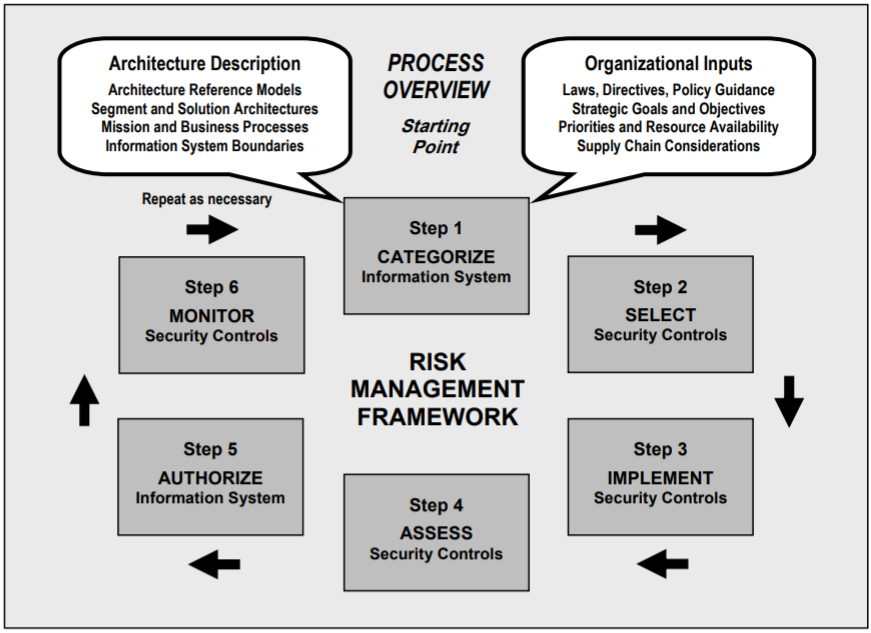
With all of these aspects in mind, the RMF was designed by NIST to be a cyclical process. It consists of six individual steps, outputs from one phase serve as inputs to the next.
The following are the six steps, according to NIST:
- Categorize the information system and the information processed, stored and transmitted by that system based on an impact analysis.
- Select an initial set of baseline security controls for the information system based on the security categorization; tailoring and supplementing the security control baseline as needed based on an organizational assessment of risk and local conditions.
- Implement the security controls and describe how the controls are employed within the information system and its environment of operation.
- Assess the security controls using appropriate assessment procedures to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system.
- Authorize information system operation based on a determination of the risk to organizational operations and assets, individuals, other organizations, and the Nation resulting from the operation of the information system and the decision that this risk is acceptable.
- Monitor the security controls in the information system on an ongoing basis including assessing control effectiveness, documenting changes to the system or its environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to designated organizational officials.
(Source: NIST)
System development life cycle and the RMF
In addition to integrating the NIST RMF process at the organizational level, risk evaluation and mitigation can also be brought into the solution development life cycle (SDLC). As information systems are developed, modified or upgraded, integrating risk evaluation and mitigation into the requirements definition process can help to ensure that cybersecurity is truly seen as a functional requirement and not just a secondary or after-the-fact activity.
When done, information systems can have fewer weaknesses and vulnerabilities that make risk management a more efficient process in the long run. Early consideration of risk also helps to make sure that risk management is not an isolated process, but rather a continuous function that all members of the organization participate in. Without the early consideration of security and risk mitigation in the SDLC processes, organizations may find themselves facing significant costs or delays to rework or address components of a system that could have been adjusted more easily earlier in the process.
Boundaries of the RMF
One of the hardest parts about implementing the RMF is understanding the scope of where it applies, both technically and realistically. This is why NIST has, within the RMF, explained how organizations can identify appropriate boundaries to define what information systems should be evaluated for risk and how assets should be protected in line with operational priorities.
Ultimately, what falls within the scope of information systems will be different for every organization and even for each cycle of RMF implementation, but components will include people, processes, hardware, software and data, among others, that support mission delivery. However, boundaries that are too broad and include too many secondary components or technology systems make the RMF process complex and unwieldy. On the other hand, boundaries that are too narrow can increase the number of information systems that could be left vulnerable or that must be managed separately, potentially increasing overall costs.
Within the NIST RMF, organizations can identify the different components that make up their information system ecosystem and establish an appropriate scope to cost-effectively mitigate risks to their important assets.
Using security controls
To assist with the implementation, maintenance and monitoring of risk management within an organization, the NIST RMF also identifies three types of security controls that can be deployed across the enterprise:
- System-specific controls: These include controls that provide a security capability for a particular information system only
- Common controls: These include controls that provide a security capability for multiple information systems
- Hybrid controls: These include controls that have both system-specific and common characteristics
The decision on which types of controls, where they should be deployed and how many should be one made in a way that is consistent with the organization’s risk profile, management priorities and their enterprise information security architecture.
As part of the decision-making process, NIST also recommends that security controls be selected and implemented that can support multiple information system components simultaneously, which can encourage efficiency and effectiveness in its maintenance and use. Use of security controls in this manner — what they refer to as “common controls” also allows for security to be simplified and for information sharing to be easier versus having many system-specific — or inherent — controls that need to be managed separately.
Conclusion: Bringing it all together
Just as with other NIST publications, the Risk Management Framework is meant to not only be a cyclical process, but one that supplements and complements other security practices an organization has in place. Additionally, it is industry- and tool-agnostic, which means the exercise of structuring, organizing and controlling risk with an enterprise focus is more important than a recommendation for a tool or control that may not fit every organizational need. Therefore, the RMF can be used just as flexibly and successfully at new and mature organizations to help organize and simplify their information system risk management processes.

Get NIST CSF training