Protect Data by Preventing Insecure Cryptographic Storage
Daily, we read news about hacking and data leaks. Hackers are really active these days. So, it is our responsibility to prevent them in getting unauthorized access of sensitive data. For this, we need to create secure applications. But there is an important point that people generally forget. Is having a secure application is enough to protect data from unauthorized access? Most of the people say if the application is secure; it will never allow hackers to access any data of your website by unauthorized manners. Yes, it is true. But can you be 100% sure that no one can break your application's security? Are you sure, your application is free from all security vulnerabilities. If you are not sure, you should take extra measures to protect your website data. This is why researchers introduced cryptography. No one can be 100% sure, so storing sensitive information in database in encrypted form can protect your data even if someone gets unauthorized access. Here comes another big OWASP vulnerability that exists because of improper use of cryptography or no use of cryptography. This vulnerability is called Insecure Cryptographic Storage. In this article, we will learn about this OWASP A7 vulnerability, its dangers and methods to prevent it.
Insecure Cryptographic Storage:
Insecure Cryptographic Storage vulnerability occurs when an application fails to encrypt sensitive data or encrypt data with poorly designed older cryptographic algorithms. Poorly designed cryptographic algorithms may include use of inappropriate ciphers, weak encryption method and poor key handling. This flaw can lead to sensitive information disclosure to attackers. This is very dangerous for e-commerce websites.
Most of the times, attackers do not need to break the cryptographic algorithm to gain unauthorized access. They get what they want just by finding keys stored in insecure manner or access data from insecure channels that can decrypt. In this way, a weak encryption strategy cannot protect your data. So, you should know how to use it in a proper manner.
As an example: a website that also takes payment from users, and payment is taken on a monthly basis. So the website store credit card details for automatic monthly payment. If the website store's credit card details in plain texts of weak hashes, it may be dangerous to users. If an attacker gets access to the website database, he will get credit card details of all users' of the website. Now, you can assume how harmful this is.
What kind of improper usage of encryption can lead to this vulnerability?
Actually, there may be various cases which can describe how this vulnerability can expose your sensitive data to hackers. In past few months, LinkedIn and few other companies faced hacking and intrusion to their system. Hackers also leaked the user data publicly. What was the good thing for those companies? They encrypted the passwords of users. What was the bad thing if they encrypted the passwords? They use simple MD5 algorithm to create password hashes. MD5 can be broken in few hours of day attempts. Use of weak or unsalted hashes, made the user data vulnerable because of insecure cryptography storage. These are few general mistakes people made while designing their applications and put user data at risk.
- No Encryption: This is the most dangerous thing found these days. There are many websites that still store data in plain text. If attacker gets the database dumps, he will be able to see all passwords. In past few months, hackers have posted many websites' dumps that contains plain password.
- Use of Weak hashes or unsalted hashes: This is another most common mistake webmasters make. They encrypt the password to add security, but weak encryption algorithm (RC3, RC4, MD5 and SHA-1) cannot help them. Although, using these encryption algorithms will increase attacker's effort. But it's not as hard as it seems. Most of the general hashing algorithms can be cracked with few hours of effort. This is why researchers have developed salted has methods. Properly salted data can take many years to break.
- Insecure way of key management: If you are using a good encryption algorithm, but your key management is insecure, your effort is useless. What if you lock the room but put the key open to thief. This is similar kind of situation. If an attacker can easily get the key, he will be able to decipher the sensitive data. In few cases, we have identified that website use insecure channels for key transfer.
- Storage unnecessary but, confidential data on your database: Sometimes website unnecessarily stores confidential data to its database. It may be credit card details of users. In case of a data leak, users' credit card details will be at risk. According to standards of PCI (Payment Card Industry), a website cannot store the CVV numbers of credit cards in its database. If a website fails to follow this rule and stores the information in database, strict legal action will be taken.
How to Prevent Insecure Cryptographic Store on websites
For identifying and patching this vulnerability, you need to start with manual approach. Scanners and tools cannot verify cryptographic weakness. Best way is the review of code, review of used cryptographic algorithm and key management. In the code review process, you should take care of various important things that can help you in identifying this vulnerability. Below, we will show you a few important things which must be done to prevent Insecure Cryptographic vulnerability on our web application. Review your code as per this information and identify weak places.
Make your website secure and try to patch common vulnerabilities: This is the most important thing to be done, websites must be secure. Try to patch all SQL injection, LFI, RFI and other kind of injection vulnerabilities that can lead to a data leak. Most of the time, hackers gain access to website databases by exploiting SQL injection vulnerability. Everything must be checked twice because a single vulnerable place can put your sensitive data at risk.
Store Sensitive data only when needed
Webmasters should always avoid storing sensitive data on their server. Many eCommerce business store payment details and credit card information for recurring bills. If your website is doing this, try to implement a secure encryption method. If you don't know how to store data in a secure manner, it's advised not to store data in your database.
Only use Widely Accepted Cryptographic Algorithms
There are various cryptographic algorithms available. With time, researchers are developing stronger algorithms. So, you should keep yourself updated with Cryptographic algorithms. MD5, SHA like algorithms are easy to crack with latest computers. Even a simple Google search can help you in cracking MD5 hash in few seconds. Just copy the hash and search in Google. Sixty percent of the time, you will find the result.
For example, we have MD5 hash of a password: 5f4dcc3b5aa765d61d8327deb882cf99
And we want to know the plain text password of this hash. Copy it, and paste in Google search box. Then press enter and see the results. See the snapshot below and check how Google search can help you in cracking general and common passwords.
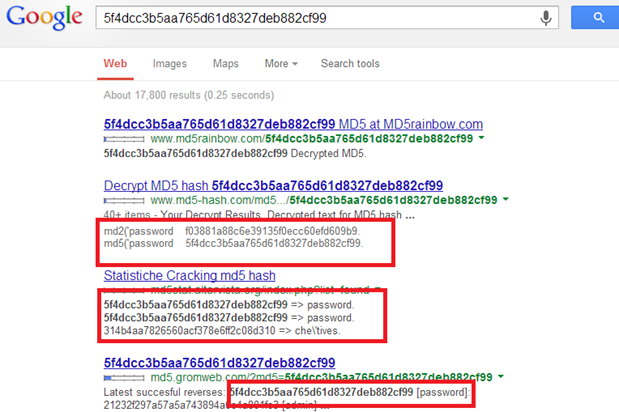
Image 1: Google Search Result of a MD5 hash
Similar kinds of Google searches can be done to crack the SHA1 password. If you are not getting the password, use online MD5 or SHA cracking tools.
Here, you should also remember one important thing. Never try to be over smart by developing your own algorithm to encrypt data. Leave this work for algorithm developers, researchers and experts.
Secure way of Password encryption to avoid risks.
Most web developers use hashing algorithms like MD5, SHA1 and SHA256. These are designed to be very fast and efficient. But we already said that these are now easy to crack via Bruteforcing. With modern technologies and fast processors, we can bruteforce the output of these algorithms and match with found hashes. In few thousands efforts, we will get the result. Above, we have also shown a simple Google method to crack the hashes of common passwords. This is why security professionals always advise not to use these old and insecure hashing algorithms for password encryption. And here comes hashes with salt for improved security...
Here, we are explaining PHP functions for proper hashing of passwords with salt. In PHP, there are two functions hash() and crypt() which are generally used to create password hashes with salt.
Crypt()
[plain]
crypt ( string $str [, string $salt ] )
Crypt() function return the hashed string of a given string using the standard Unix DES-based algorithms. See details of this function here: http://www.php.net/manual/en/function.crypt.php
Hash()
[plain]
hash ( string $algo , string $data [, bool $raw_output = false ] )
Ex:
[php]
<?php
echo hash('ripemd160', 'Mypassword');
?>
Crypt() function is widely used and recommended by most of the researchers. Here is the simple implementation of crypt() for hashing passwords.
[php]
<?php
//use this function to generate the salted password in registration process.
function HashPassword($password) {
$salt = '$2y$11$' . substr(md5(uniqid(rand(), true)), 0, 22);
$password_hash = crypt($password, $salt);
return $password_hash;
}
// use this function to authenticate password while login process
function authenticateuser($password, $Password_hash) {
return crypt($password, $Password_Hash) == $Password_hash;
}
?>
We don't need to store the salt in the separate column of the database. Crypt function adds it in password hash and uses it while authentication.
There may be various other ways to generate salt. You can use as per your choice.
Generate keys offline and never transmit over insecure channels: This is another big and important thing which must be used with care while key management. If there is a need of key transfer, make sure that you are doing it in a secure manner. Never use insecure channel for this. MIMT attack can expose your key and hence your encryption.
How to handle credit card details to avoid risks
If your website accepts online payments, store credit card details, you should know how to process and store data. Visit the website of PCI Data Security Standard and read the guidelines. PCI (Payment Card Industry) Data Security Standard was developed to enhance credit card data security on websites.
Ensure Offsite Backups are encrypted: Every business either does daily or weekly backups. But it should be kept in encrypted form. If an attacker gets access to your backup, he will not be able to gain access to your data. An encryption key must be kept separately to ensure proper security.
If you don't know how to do this, or don't want to hire people for this, you can outsource this work. There are many third-party companies which provide secure and encrypted backup services. You can take service of those companies to avoid any kind of risk.
Conclusion:
Insecure Cryptographic Storage is one of the top 10 most dangerous web application vulnerabilities. It stands at number 7 and exposes the developers' trust on weak encryption. If you do not know proper use of cryptographic algorithm, you must learn it before using it. Most important thing is that you should not start experimenting with your new encryption method. Learn how to use strong salted hashes. Learn proper key management and learn how to make secure web applications to stop attackers.
You should also identify the data that should be protected and then apply encryption before storing it in the database. Never compromise with it. There are various secure algorithms that have been developed, and most of the programming languages come with built-in support of those cryptographic algorithms. So, by using those functions or classes, you can add extra layer of protect and good encryption. So, why compromise security. Just learn how to do it and then do. If you are a website owner, then talk with your developers about the security and see what they do to protect their website's confidential data. You can never be 100 percent sure about security, so you should use proper encryption to reduce the amount of data loss. If an attacker intrudes in your system or database, he will get encrypted data. This way, you will prevent attacker even if he has already broken security.









