An introduction to the key distribution center, mathematical algorithms, and the hashing function
Our last article reviewed some of the key fundamentals of Cryptography, especially what has been used in the past. Specifically, it covered the following topics:
- The Caesar Methodology
- The Types of Cryptographic Attacks
- Polyalphabetic Encryption
- Block Ciphers
- Initialization Vectors
- Cipher Block Chaining
In this article, we continue with the theme of Cryptography, with an emphasis on the keys and the Key Distribution Center (also known as the "KDC"). This article covers the following topics:
- The Disadvantages of Symmetric Key Cryptography
- The Key Distribution Center
- The Mathematical Algorithms Associated with Symmetric Cryptography
- Conclusions – The Hashing Function.
For a primer article on Cryptography, click here:
/dna-cryptography-and-information-security/#gref
The disadvantages of symmetric key cryptography
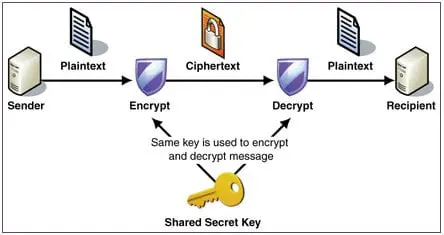
Although Symmetric Key Cryptography does possess its advantages, it also has a set of disadvantages, which are as follows:
- Key Distribution
- Key Storage and Recovery
- Open Systems.
Key distribution
With regards to the first one, Key Distribution, Symmetric Cryptography requires the sharing of secret keys between the two parties (the sending and the receiving ones). This requires that an implicit trust is established so that this key is not shared with any other outside third party. The only way that any type of secrecy can be achieved in this regard would be to establish a secure channel.
Although this works very well in theory, in practice, it is not a feasible solution. For instance, the typical place of business or corporation would not be able to afford to implement or deploy such a secure channel, except the very large business organizations and Federal Government entities. Thus, the only other solution available in this circumstance would be the use of a so-called "Controller."
This third party would have to be very much trusted by both the sending and the receiving parties. However, this methodology of trust to create a secure channel can prove to be a very cumbersome task. For example, suppose that a CEO of a business or a corporation decides to share the private keys with the other employees.
However, rather than trusting the employees explicitly, the CEO could very well decide to utilize the Network/Systems Administrator whom would distribute the private keys so that they can access any resources which they need. In return, the employees would then return the private keys back to this same individual.
Already, one can see that this is a very tedious and time-consuming process. To compound this problem further, the designated controller, in this case the Network/Systems Administrator, cannot be trusted either because he or she could distribute these very same keys to a malicious third party. As a result, when this technique is applied to the world of Cryptography, it does not, by any means, guarantee the secrecy of the private key which is needed to encrypt and decrypt the plain text message.
Key storage and recovery
Regarding Key Storage and Recovery, let us take the example of a very large business or even that of a multinational corporation. The problems of using Symmetric Cryptography become quite evident. First, since there are many more lines of communication between the sending and the receiving parties, the need to implement more controllers becomes a totally unrealistic as well as infeasible goal. Thus, the distribution of the private keys becomes a virtual nightmare.
Second, all of the private keys associated in Symmetric Cryptography have to be securely stored somewhere, primarily in the database which resides on the Central Server. As it is well known, Primary and Central Servers are very much prone to worms, malware, spyware, viruses, etc., as well as other malicious types of software. Compounding this problem, even more, is the fact that if there are many private keys which are stored on this Central Server, the greater are the chances that the Central Server will be a prime target for the Cyber attacker.
For instance, a way that these private keys can be stolen is if a piece of malicious code is injected into the intranet of the corporate network, which in turn, reaches the database. This malicious code can then very covertly hijack and send the private keys to the Cyber attacker.
Third, when companies and organizations get large, the chances that the employees will require remote access to the corporate intranet and network resources become even greater. As a result, the private keys that are used to communicate between the sending and the receiving parties can also be hijacked very quickly and easily by a hacker who has enough experience and knowledge about what they are doing.
Open systems
Finally, with an Open System, private or Symmetric Cryptography works best only when it is used in a very closed, or sterile type of environment, where there are only a handful of sending and receiving parties. However, this is not the case with open or public based environments, such as the example with a very large corporation or business. In these situations, there is simply no way to confirm the authenticity or the integrity of the private keys and their respective Ciphertext messages.
Thus, as one can see, private keys and Symmetric Cryptography simply are inflexible, too costly, and do not scale well for most types of environments. For example, "solutions that are based on private key cryptography are sufficient to deal with the problem of secure communications in open systems where parties cannot physically meet, or where parties have transient interactions." (SOURCE: 1).
Although there will never be a perfect, 100% solution that will correct the flaws of Symmetric Cryptography, there is a partial solution known as "Key Distribution Centers," which is examined in the next section.
The key distribution center
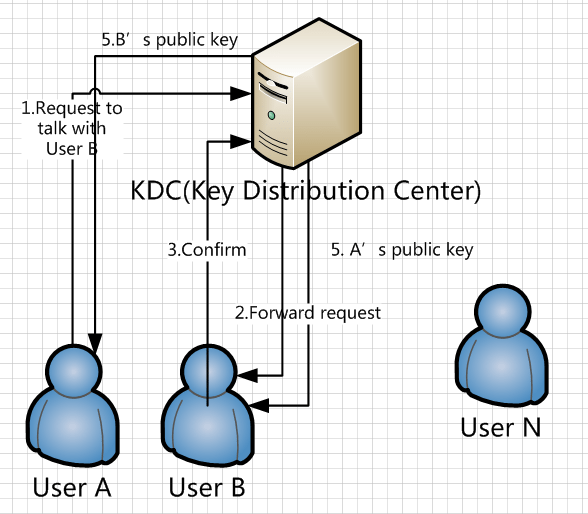
The Key Distribution Center (also known as the "KDC") is primarily a Central Server that is dedicated solely to the KDC network configuration. It merely consists of a database of all of the end users at the place of business or corporation, as well as their respective passwords and other trusted servers and computers along the network.
It should be noted that the passwords which are stored into a KDC are also encrypted. Now, if one end user wishes to communicate with another end user on a different computer system, the sending party enters their password into the KDC, using a specialized software called the "Kerberos." When the KDC receives the password, the Kerberos then uses a special mathematical algorithm that adds the receiving party's information and converts it over to the Cryptographic Key.
Once this Encrypted Key has been established, the KDC then sets up and establishes other keys for the encryption of the communication session between the sending and the receiving parties. These other keys are also referred to as "tickets." These tickets have a time expiration associated with them so that it expires at a predetermined point in time to prevent unauthorized usage.
Although the KDC System just described does provide a partial solution to the shortcomings of Symmetric Key Cryptography, the KDC also by nature has some major security flaws, which are as follows:
- If an attack is successful on the KDC, the entire communications channel from within the place of business or organization will completely break down. Also, personnel with access to the KDC can easily decrypt the Ciphertext messages between the sending and receiving parties.
- The KDC process presents a single point of failure for the organization. For example, if the server containing the KDC crashes, then all types of secure communications becomes impossible to have, at least on a temporary basis. Also, since all of the end users will be hitting the KDC at peak times, the processing demands placed onto the KDC can be very great, thus heightening the chances that very slow communications between the sending and the receiving parties or even a complete breakdown in communications can happen.
The mathematical algorithms associated with symmetric cryptography
There are a number of key mathematical algorithms which are associated with Symmetric Cryptography, and they are as follows:
- The Needham-Schroder Algorithm:
This algorithm was specifically designed for KDC Systems to deal with sending and receiving parties from within the pace of business or corporation, who appear to be offline. For example, if the sending party sends a Ciphertext message to the receiving party and after that goes offline, the KDC System could just literally "hang" and thus maintain an open session indefinitely, until the sending party comes back online once again. With this particular Mathematical Algorithm, this problem is averted by immediately terminating the communications session once either party goes offline.
- The Digital Encryption Standard (DES) Algorithm:
This Mathematical Algorithm was developed in 1975, and by 1981, it became the de facto algorithm, for Symmetric Cryptographic systems. This is a powerful algorithm, as it puts the Ciphertext through at least 16 iterations to ensure full levels of encryption.
- The Triple Digit Encryption Standard Algorithm (3DES):
This Mathematical Algorithm was developed as an upgrade to the previous DES algorithm just described. The primary difference between the two of them is that 3DES puts the Ciphertext through three times as many more iterations than the DES algorithm.
- The International Data Encryption Algorithm (IDEA):
This is a newer Mathematical Algorithm than the 3DES and is constantly shifting the letters of the Ciphertext message around constantly until the receiving party decrypts it. It is three times faster than any of the other DES algorithms just reviewed, and as a result, it does not consume as much processor power as the other DES algorithms do.
- The Advanced Encryption Standard (AES) Algorithm:
This is the latest Symmetric Cryptography algorithm and was developed in 2000. It was designed primarily for use by the Federal Government.
Conclusion – The hashing function
Finally, in Symmetric Cryptography, it should be noted that all of the Ciphertext messages come with what is known as a "Hash." It is a one-way Mathematical Function, meaning, it can be encrypted, but it cannot be decrypted. Its primary purpose is not to encrypt the Ciphertext rather; its primary purpose is to prove that the message in the Ciphertext has not changed in any way, shape, or form. This is also known as "Message Integrity."
For example, if the sending party sends its message to the receiving party, the message (or the Ciphertext) will have a Hash Function with it. The receiving party can then run a Hash Algorithm, and if the Ciphertext message has remained intact, then the receiving party can be assured that the message that they have just received is indeed authentic, and has not been compromised in any way. However, if the Hash Mathematical values are different, then it is quite possible that the message is not authentic and that it has been compromised.
With the principles of Symmetric Cryptography, only one key is used to encrypt and decrypt the Ciphertext between the sending and the receiving parties. In the next article, we look at an entirely different methodology – called "Asymmetric Key Cryptography." With this type of methodology, not just one key is used, but rather, two keys are used.
Sources
- Computer Networking: A Top Down Approach, Kurose, J.F., and Ross, K.W., Pearson Education, 2008.
- http://www4.ncsu.edu/~kksivara/sfwr4c03/lectures/lecture9.pdf
- http://www.cs.umd.edu/~clancy/ents689i/689iwk1.pdf
- http://www.doc.ic.ac.uk/~mrh/430/03.SymmetricKey.ppt.pdf
- http://cs.brown.edu/cgc/net.secbook/se01/handouts/Ch08-CryptoConcepts.pdf
- http://www.ijcaonline.org/journal/number15/pxc387502.pdf
- http://wps.aw.com/wps/media/objects/7134/7305312/previous3e/Key_Distribution.pdf
- http://www.iet.unipi.it/g.dini/Teaching/sanna/lecturenotes/applied-cryptography-key-distribution.pdf
- http://www.ece.mtu.edu/ee/faculty/cchigan/EE5723-Security/lecture5-2-Key-Distribution.pdf
- https://mrajacse.files.wordpress.com/2012/03/chapter-14-key-management-distribution1.pdf
- http://www.computing.dcu.ie/~hamilton/teaching/CA642/notes/KeyDistribution.pdf
- https://people.eecs.berkeley.edu/~daw/teaching/cs261-f08/scribenotes/1108-joshi.pdf
- https://math.berkeley.edu/~kpmann/encryption.pdf
- https://www.esat.kuleuven.be/cosic/publications/thesis-201.pdf
- https://arxiv.org/ftp/math/papers/0510/0510057.pdf
- http://www.cs.princeton.edu/~rs/AlgsDS07/10Hashing.pdf
- http://www.computing.dcu.ie/~hamilton/teaching/CA642/notes/Hash.pdf
- http://csrc.nist.gov/publications/nistbul/March2009_cryptographic-hash-algorithm-family.pdf









